Cyber Security Degrees
Cyber security is the defense of information and computer systems from various attacks and threats, from the damage the hardware and software, from the theft of the information stored on them, and from the disruption and misdirection of services which they provide. The reliance on various computer and networked systems increases day by day, but all them are sufficiently vulnerable and so the need for cyber security acquires more and more importance, it includes protection from the damages due to the network access, the control of physical access to the hardware, the control of intentional and accidental malpractice by operators.
Increase of variety and quantity of cyber threats is lead to the active development of cyber security field today. For protection various cyber environments are developed and applied large variety of cyber security standards, techniques, security concepts and approaches with different cyber security degrees. But the main common objective of all them is reduce the risks, increase privacy and security, provide a reliable protection of computers, programs, networks and data from damages and unauthorized access, and effectively prevent the cyber attacks and cyber threats.
The ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park offers the number of useful tools which will help network security engineers, cyber security specialists, network and computer analysts easily and visually depict the knowledge and skills for research and prevention of intrusions, about maintenance of security protocols on computer networks of various sizes, about protection critical information and analysis of cyber incidents, and for how to assess threats and vulnerabilities.

Example 1. Cyber Security Degrees
Network Security Diagrams Solution for ConceptDraw DIAGRAM is incredibly useful for effective network security schemes design with different cyber security degrees thanks primarily to 4 libraries with numerous quantity of predesigned vector objects:
- Cybersecurity Clipart
- Cybersecurity Round Icons
- Cybersecurity Shapes
- Cybersecurity Connectors
Start create your diagram by dragging the objects from these libraries to your ConceptDraw document and evaluate the usability of using fully ready-to-use objects.

Example 2. Network Security Diagrams Solution in ConceptDraw STORE
Network Security Diagrams solution provides also wide collection of predesigned network security samples which are available from ConceptDraw STORE. Each of offered samples is carefully thought-out by experts and can be used as easy start for your own diagrams. Pay attention for them and get excellent result in a few minutes!

Example 3. Network Security Diagram - Recommended Network Architecture
The samples you see on this page were created in ConceptDraw DIAGRAM using the predesigned vector objects from the libraries of Network Security Diagrams Solution. An experienced user spent 10-15 minutes creating each of these samples.
Use the Network Security Diagrams Solution for ConceptDraw DIAGRAM to create your own Network Security Diagrams of any cyber security degrees fast, easy and effective.
All source documents are vector graphic documents. They are available for reviewing, modifying, or converting to a variety of formats (PDF file, MS PowerPoint, MS Visio, and many other graphic formats) from the ConceptDraw STORE. The Network Security Diagrams Solution is available for all ConceptDraw DIAGRAM users.
SEVEN RELATED HOW TO's:
If we divide computer networks by scale, we get several main categories. The smallest network is PAN, as it connects personal devices themselves, and as the number of users grows, a local area network can be recognized, and campus area networks (CAN) connects several local networks located within some area like a university or a corporation. Computers connected to CAN share public educational materials and list of CAN network examples includes such prestigious universities like Stanford and Carnegie Mellon.
This is an example of a computer network diagram created for a campus area network. It was created using using ConceptDraw solution for the Computer and Network diagramming. The specific of this sample campus network is its distribution. It is rather broad to embrace a big campus territory. This diagram can be applied as a template for designing custom area network topology diagram for a particular educational institution.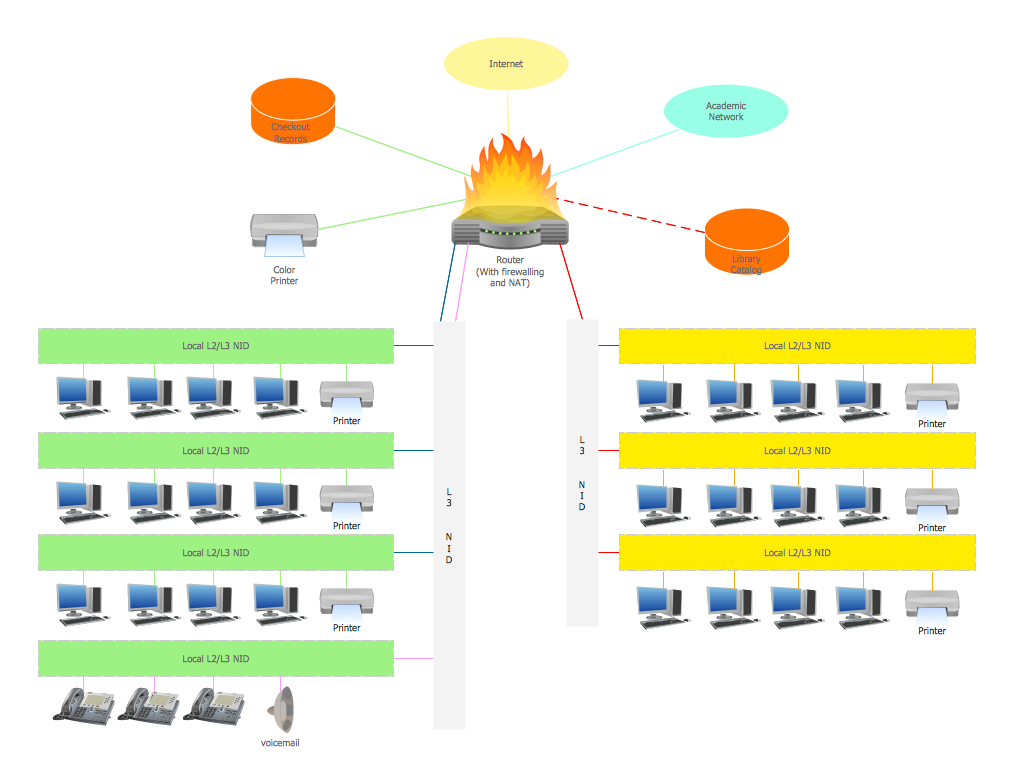
Picture: Campus Area Networks (CAN). Computer and Network Examples
Related Solution:
ConceptDraw DIAGRAM diagramming and vector drawing software offers the Vehicular Networking Solution from the Computer and Networks Area of ConceptDraw Solution Park which makes it the best for designing professional looking vehicular network diagrams.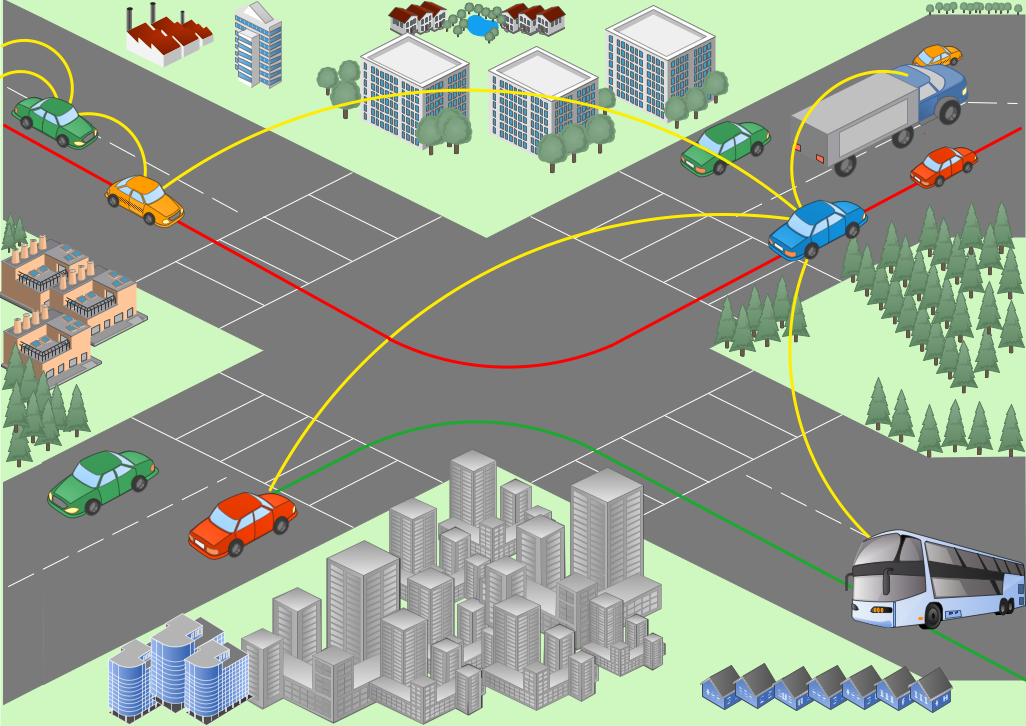
Picture: Vehicular Network
Related Solution:
ConceptDraw DIAGRAM diagramming and vector drawing software extended with Security and Access Plans Solution from the Building Plans Area of ConceptDraw Solution Park is a powerful software for fast and easy drawing professional looking Physical Security Plan.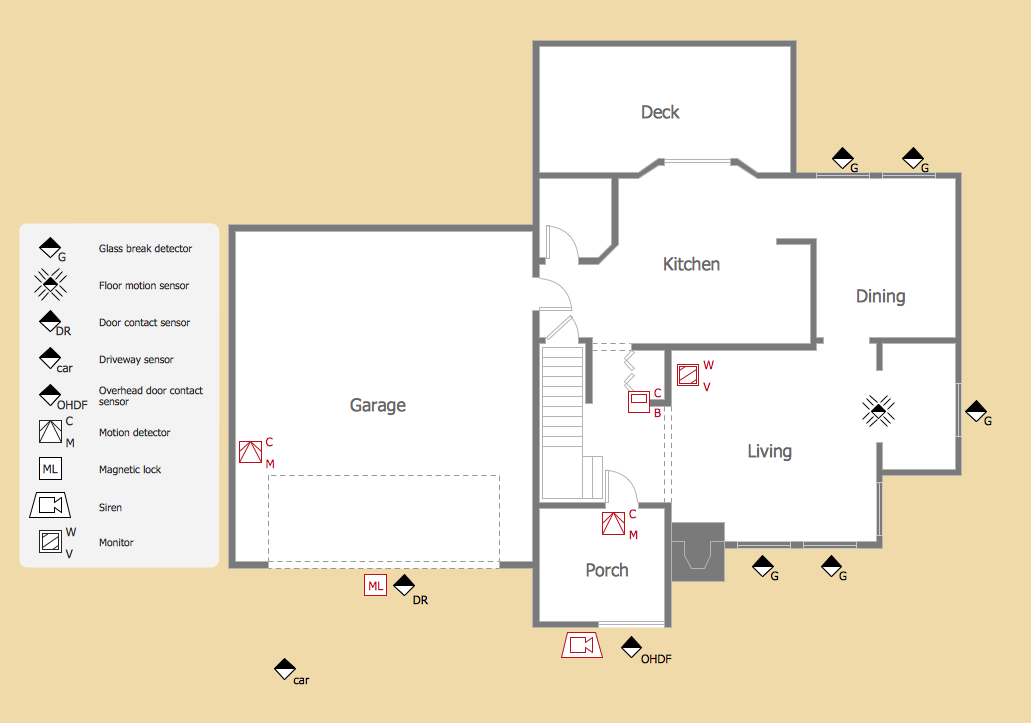
Picture: Physical Security Plan
Related Solution:
ConceptDraw DIAGRAM software extended with Fishbone Diagrams solution from the Management area of ConceptDraw Solution Park is perfect for Cause and Effect Diagram creating. It gives the ability to draw fishbone diagram that identifies many possible causes for an effect or a problem. Causes and Effects are usually grouped into major categories to identify these sources of variation. Causes and Effects in the diagram show relationships among various factor. Fishbone diagram shows factors of Equipment, Process, People, Materials, Environment and Management, all affecting the overall problem.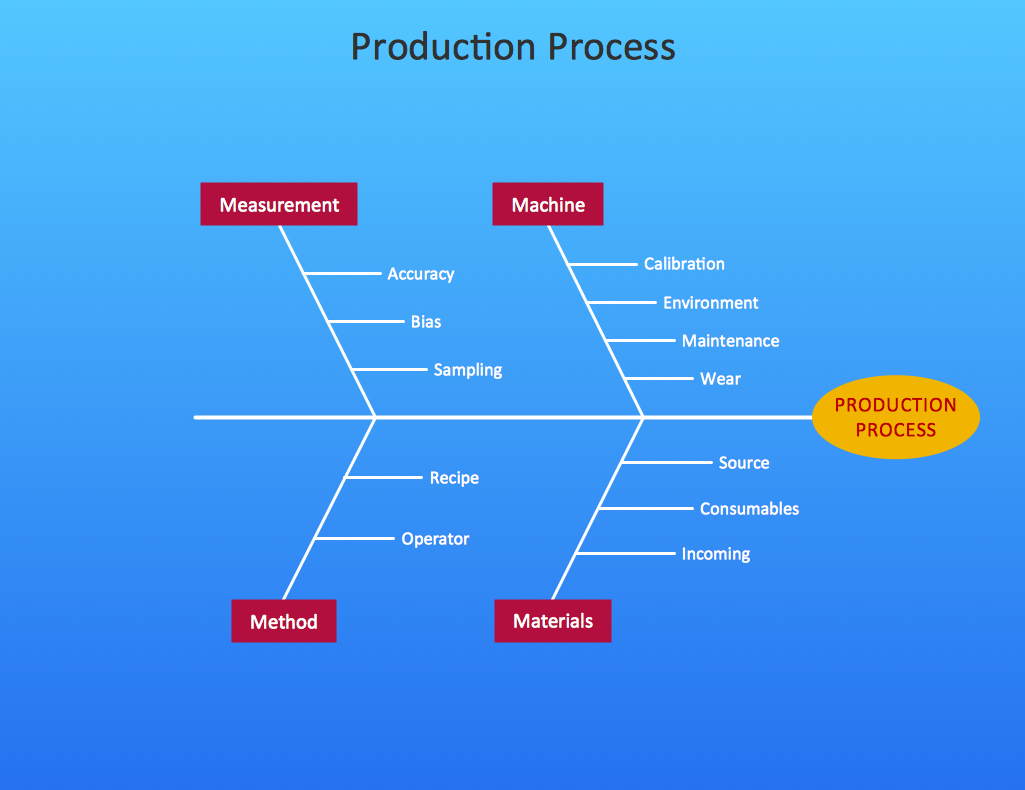
Picture: Cause and Effect Diagram
Related Solution:
There are numerous articles about the advantages of flowcharting, creating business graphics and developing different charts. Nevertheless, these articles are almost useless without the main component - the examples of flowcharts, org charts and without a fine example, it is difficult to get all the conveniences of creating diagrams. You can find tons of templates and vivid examples on Solution Park.
This illustration shows a variety of business diagrams that can be created using ConceptDraw DIAGRAM. It comprises a different fields of business activities: management, marketing, networking, software and database development along with design of infographics and business illustrations. ConceptDraw DIAGRAM provides a huge set of sample drawings including business process modeling diagrams,, network diagrams, UML diagrams, orgcharts, DFD, flowcharts, ERD, geographical maps and more.
Picture: Examples of Flowcharts, Org Charts and More
Related Solution:
A list of parameters on which networks differ is very long. A large network with a range up to 50 kilometers is called metropolitan area network (MAN), and this type of network can include several local area networks. Metropolitan networks in their turn connect into global area networks.
Here you will see a Metropolitan Area Network (MAN). This is an extensive network which occupies a large territory including a few buildings or even the whole city. The space of the MAN is bigger than LAN, but lower than WAN. MAN comprise a lot of communication equipment and delivers the Internet connection to the LANs in the city area. Computer and Networks solution for ConceptDraw DIAGRAM provides a set of libraries with ready-to-use vector objects to design various kinds of computer networks.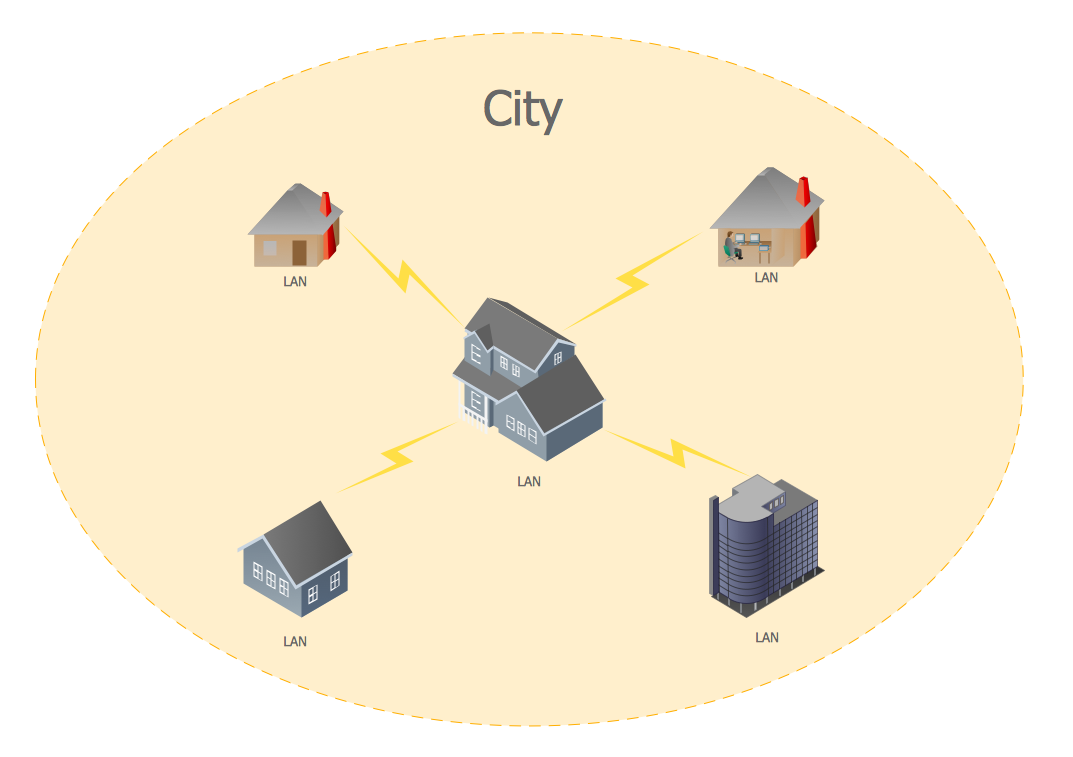
Picture: Metropolitan area networks (MAN). Computer and Network Examples
Related Solution:








