Network Security
The Internet is a giant computer network which connects computers all over the world. Now the Internet is widely used in all spheres of the life and activity, it is first of all a way to exchange information, without which today is difficult to imagine the life. The Internet is integral part of human society and business. But the serious question for network engineers, designers, lawmakers and enforcers is the need for protect the Internet networks from the Internet crimes, hacking and attacks.
There are many kinds of dangers and ways of attacks, but there are also quite a number of hardware, software and physical methods of protection against them. Such devices as routers, IDS and Firewalls are examples of hardware devices used for network security. Anti-virus software and VPNs are some of the software network security tools.
One of the most effective and easily implemented ways to protect the networks is the use of Firewalls. The Firewall is a first line of defense against the external threats to networks, it can be either software based or hardware based. The main task of firewall is to allow the authorized access to a computer while blocking unauthorized access. The Network layer firewalls makes decisions based on the source address, destination address and ports in individual IP packets. Modern network layer firewalls maintain internal information about states of the connections passing through them.
Depending of the service kind and security you need for your network, you can choose the type of firewall. The most useful types of firewalls are: Screened host firewall, Screened subnet firewall, Packet filer firewall, Stateful inspection firewall, Hybrid firewall, Proxy server firewall, Application level (gateway) firewall.
ConceptDraw DIAGRAM is a powerful diagramming and vector drawing software that allows quick and easy draw the diagrams of your safe networks.
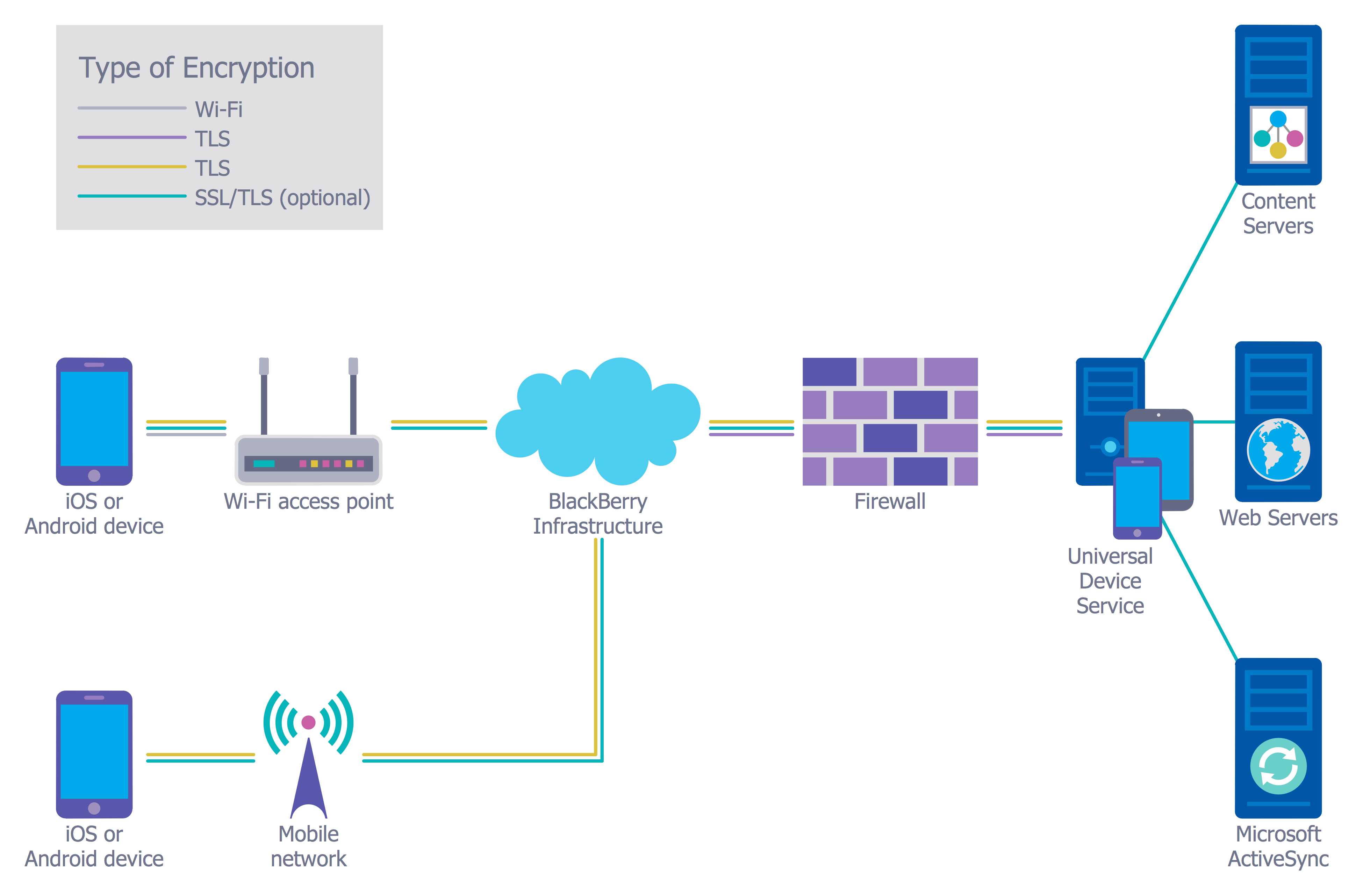
Example 1. Network Security
Computer and Networks Area provides the Network Security Diagrams solution that contains the libraries with a great number of predesigned vector stencils, a set of professional looking examples that you can change for your needs.
All numerous predesigned Network Security Diagram samples are available from ConceptDraw STORE. Use of ready sample is the most simply and quick way of drawing diagrams, you can start with ready sample and change it according to your taste and needs.

Example 2. Network Security Diagram - Access Control and Encryption
The samples you see on this page were created in ConceptDraw DIAGRAM using the tools of Network Security Diagrams Solution for ConceptDraw DIAGRAM software. They show protection networks with Firewalls and other network security devices. An experienced user spent 5-10 minutes creating each of these samples.
Use the Network Security Diagrams Solution for ConceptDraw DIAGRAM to create your own Network Security Diagrams quick, easy and effective.
All source documents are vector graphic documents. They are available for reviewing, modifying, or converting to a variety of formats (PDF file, MS PowerPoint, MS Visio, and many other graphic formats) from the ConceptDraw STORE. The Network Security Diagrams Solution is available for all ConceptDraw DIAGRAM users.
TEN RELATED HOW TO's:
This sample was created in ConceptDraw DIAGRAM diagramming and vector drawing software using the Computer and Networks solution from Computer and Networks area of ConceptDraw Solution Park.
This sample shows the Hierarchical network topology.
A Hierarchical network topology interconnects multiple groups that are located on the separate layers to form a larger network. Each layer concentrates on the specified functions, this allows to choose the right equipment for the layer.
Picture: Hierarchical Network Topology
Related Solution:
A network diagram represents the set of computers and network devices and the connections among them. This scheme can be developed for any institution or establishment. To illustrate this concept let’s take for example, a hotel network topology diagram or a school network diagram. These diagrams depict access points, servers, workstations, firewalls and another equipment needed to provide a network.
On this masterpiece drawing one will see a simple scheme a of connecting computers together. Such form of connecting can be applied for a hotel, guest house, bungalow, hut or something else. This diagram shows the images of the real LAN components. So, it represents a physical category of a network construction. It looks similar to a star - so this network configuration is named a star topology. The typical feature of this construction is a center point - usually it is hub, or router. The rays of this star means network connections. Computers, peripherals and other network details are placed on the ends of the star rays.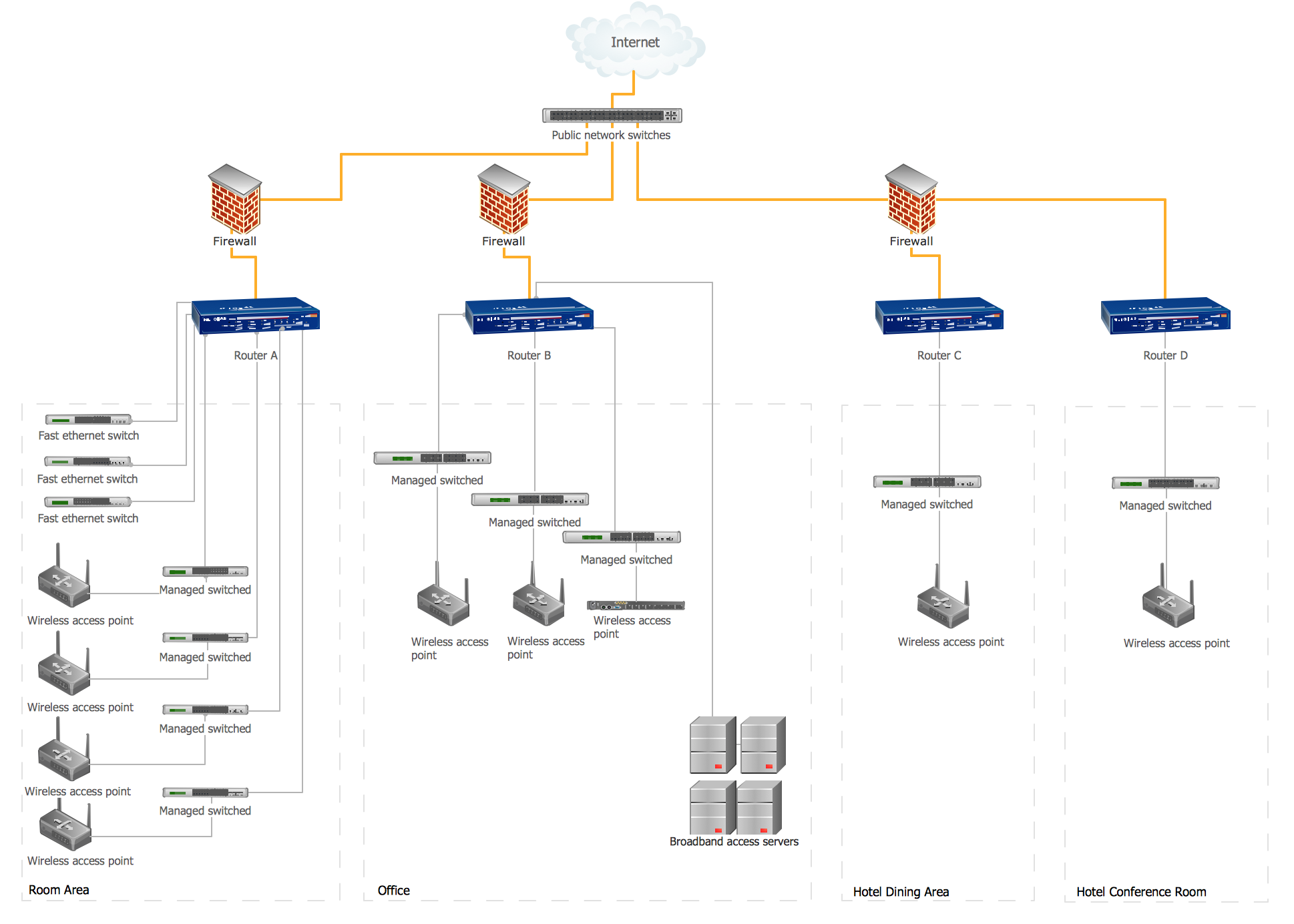
Picture: Hotel Network Topology Diagram
Related Solution:
Indonesia, officially the Republic of Indonesia, is a sovereign state in Southeast Asia and Oceania.
The vector stencils library Indonesia contains contours for ConceptDraw DIAGRAM diagramming and vector drawing software. This library is contained in the Continent Maps solution from Maps area of ConceptDraw Solution Park.
Picture: Geo Map — Asia — Indonesia
Related Solution:
Electrical plan is a document that is developed during the first stage of the building design. This scheme is composed of conventional images or symbols of components that operate by means of electric energy. To simplify the creation of these schemes you can use house electrical plan software, which will not require a long additional training to understand how to use it. You only need to install the necessary software ant it’s libraries and you’ll have one less problem during the building projection.
Any building contains a number of electrical systems, including switches, fixtures, outlets and other lightening equipment. All these should be depicted in a building electrical plans and included to general building documentation. This home electrical plan displays electrical and telecommunication devices placed to a home floor plan. On the plan, each electrical device is referenced with the proper symbol. Electrical symbols are used for universal recognition of the building plan by different persons who will be working on the construction. Not all possible electric symbols used on a certain plan, so the symbols used in the current home plan are included to a legend. The electrical home plan may be added as a separate document to a complete set of building plans.
Picture: How To use House Electrical Plan Software
Related Solution:
All computer networks differ by various params, and their size is one of them. As global area networks are the biggest, personal area (PAN) networks are the smallest. Personal computers, smartphones and other devices that have possibility to connect to Internet form a personal network.
This diagram was created using ConceptDraw Computer Network Diagrams to represent a typical components of Personal area network. A personal area network (PAN) is the connection of IT devices around an individual person. This sample of personal area network involves a notebook, a personal digital assistant (PDA), and a portable printer. Commonly a PAN contains such wireless devices as mouse, keyboard, smartphone and tablet. A wireless connection is typical for a PAN.
Picture: Personal area (PAN) networks. Computer and Network Examples
Related Solution:
Network infrastructure planning is a very important process in the network construction, and the share of time allocated to this within the scope of the entire project may reach 60-80%. A competent and thorough approach to planning contributes to the quick investment return, and also increases the reliability and flexibility of the final system, reducing the probability of additional costs related to the incorrect implementation.
Any planning begins with an analysis of the business requirements to the final system. Basic network parameters, which should be assessed are the scalability, accessibility, cost, speed and safety.
Speed and cost are often mistaken for the most important parameters, and the rest of the parameters aren't even remembered. This is not entirely correct. Initially, it is necessary to assess the business plans for the future, because sometimes it is more profitable to invest more money in the beginning. If the business is to develop, then, consequently, demands on
Picture: Cisco Routers. Cisco icons, shapes, stencils and symbols
Related Solution:
Dynamic of development computer and network technologies increases the need in modern cyber security strategies and IT security solutions to support security of your data, to ensure data privacy, and to protect your operations from the cyber threats. Thanks to the Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park, the ConceptDraw DIAGRAM diagramming and vector drawing software is one of the unique IT security solutions for professional designing Network Security Diagrams.
Picture: IT Security Solutions
Related Solution:
The ConceptDraw vector stencils library Cisco Security contains 16 symbols of security devices and equipment for drawing the computer network diagrams using the ConceptDraw DIAGRAM diagramming and vector drawing software.
Picture: Cisco Security. Cisco icons, shapes, stencils and symbols
Related Solution:
Local area network connects computers and other network appliances within an area, such as office building or a campus. It can be difficult to provide such network without a predesigned plan. For these purposes you can use network diagram software, which helps you to create LAN network diagrams and office network diagrams quickly and effortless. This will speed up your work and you can save the diagram for the future network improvements.
The following diagram illustrates a network topology of the small office. LAN configuration has a star topology. The local network joins 8 computers among which are several desktop PCs, laptop, two iMacs and iBook. The end-point devices are divided into three groups. Each group is connected to its hub. There is a network printer and a modem, which are interconnected with other devices through a network server. Each computer on the LAN can access the server through a corresponding hub.
Picture: Network Diagram Software. LAN Network Diagrams. Physical Office Network Diagrams
Related Solution:













