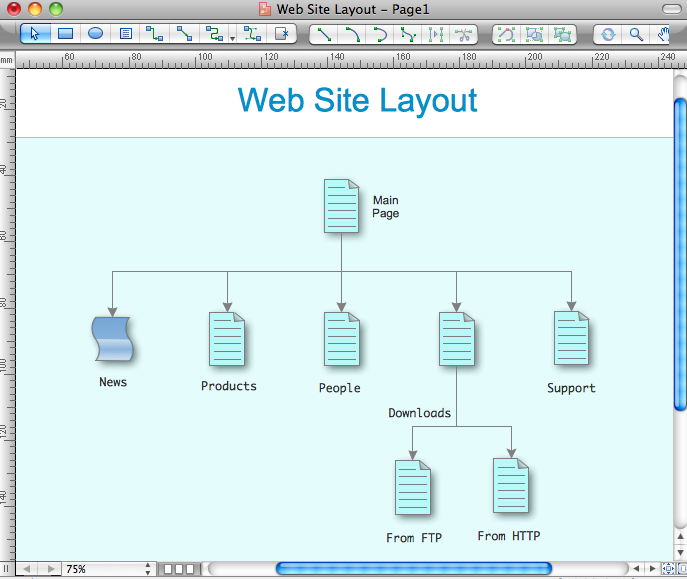
Personal area (PAN) networks. Computer and Network Examples
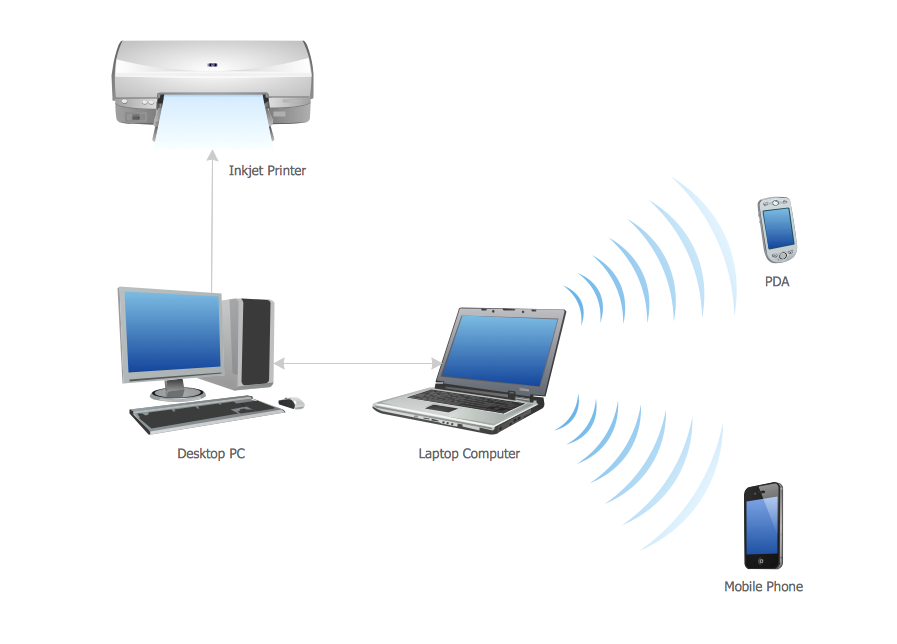
Personal area network (PAN) is a network organized on a limited area and used for data transmission between various personal devices, such as computers, tablets, laptops, telephones, different digital and mobile devices, etc. and also for connecting to higher level network and Internet. PAN is used to manage the interconnections of IT devices which surround a single user and generally contains such appliances, as cordless mice, keyboard, phone, and Bluetooth handsets. PANs can be wired with computer buses, or wirelessly connected to the Internet using such network technologies as Bluetooth, Z-Wave, ZigBee, IrDa, UWB, Body Area Network. PANs have a lot of pros and cons, they are expedient, lucrative and handy, but sometimes have bad connection with other networks on the same radio bands, Bluetooth has distance limits and slow data transfer speed, but is comparatively safe. ConceptDraw DIAGRAM diagramming software supplied with numerous solutions of Computer and Networks Area included to ConceptDraw Solution Park perfectly suits for designing the Personal Area Networks.
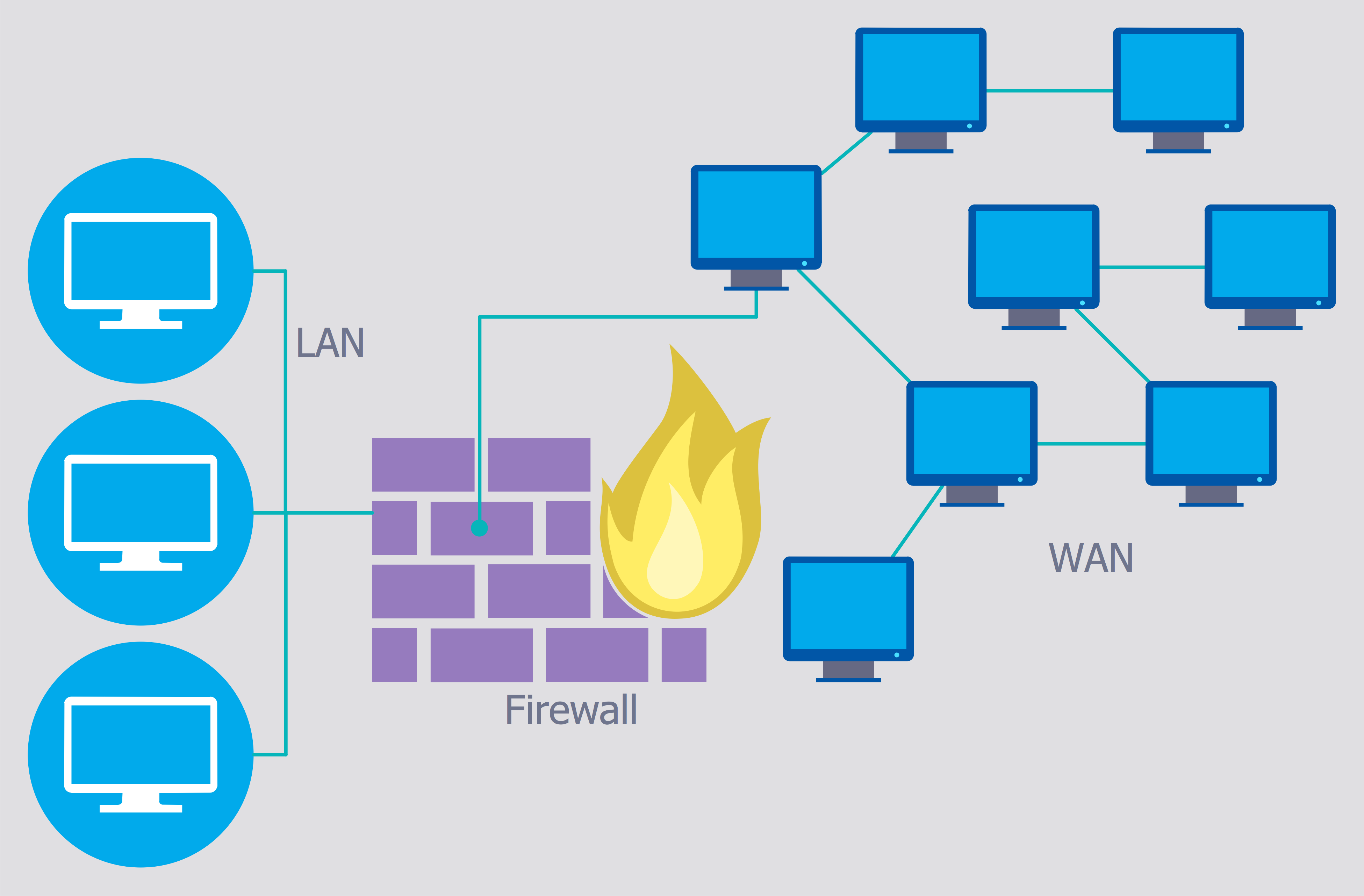
Network Security Tips
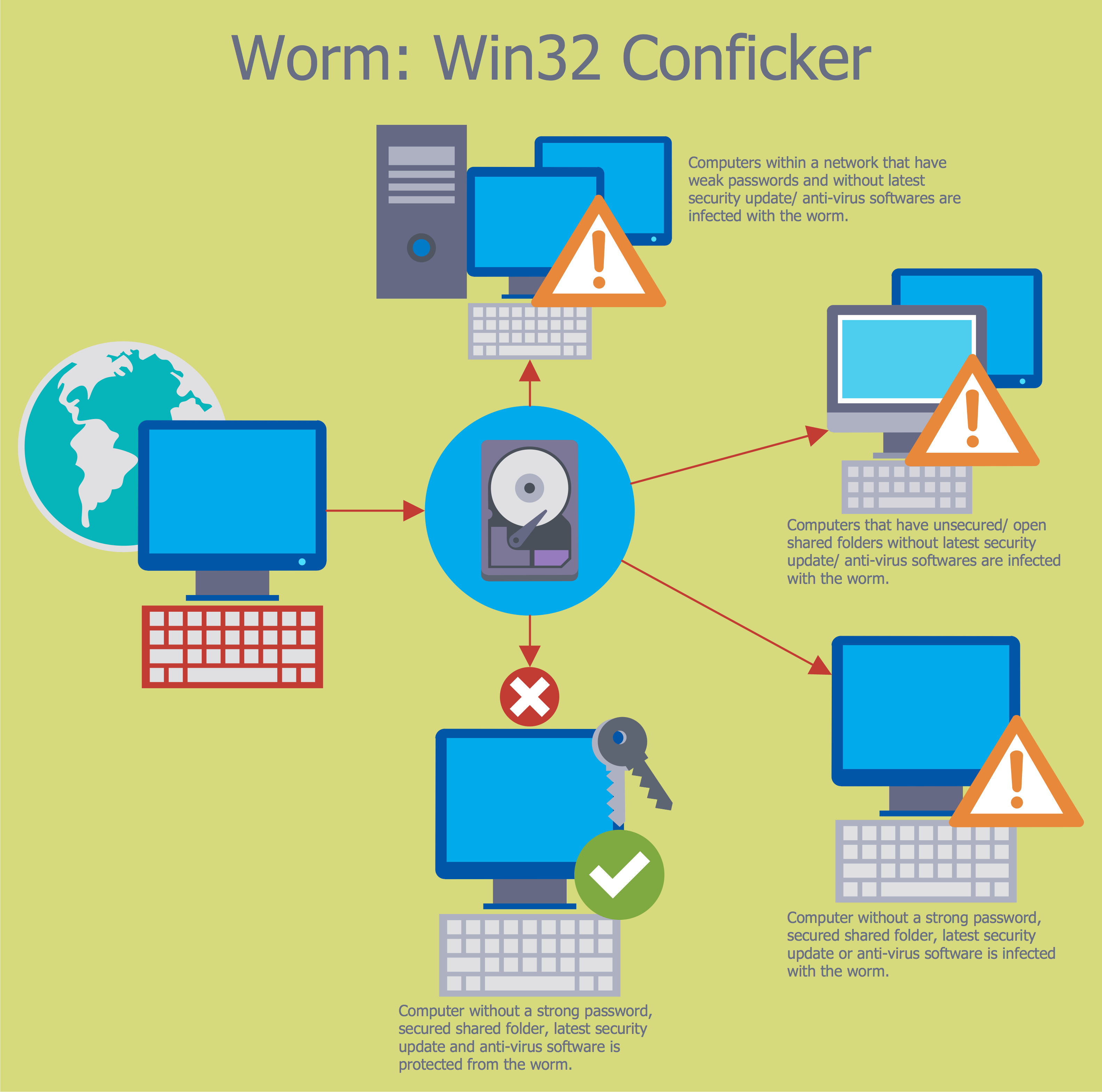
The Internet is a huge world with unlimited possibilities. But with all its numerous advantages, the Internet also conceals many dangers and security threats, that's why we advise you to follow simple network security tips. ConceptDraw DIAGRAM diagramming and vector drawing software supplied with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is an ideal software for easy designing Network Security Diagrams and attractive illustrations with effective network security tips.Quality Mind Maps - samples and templates
Use samples and templates to describe your own quality processes, brainstorm, and structure quality issues.Hotel Network Topology Diagram
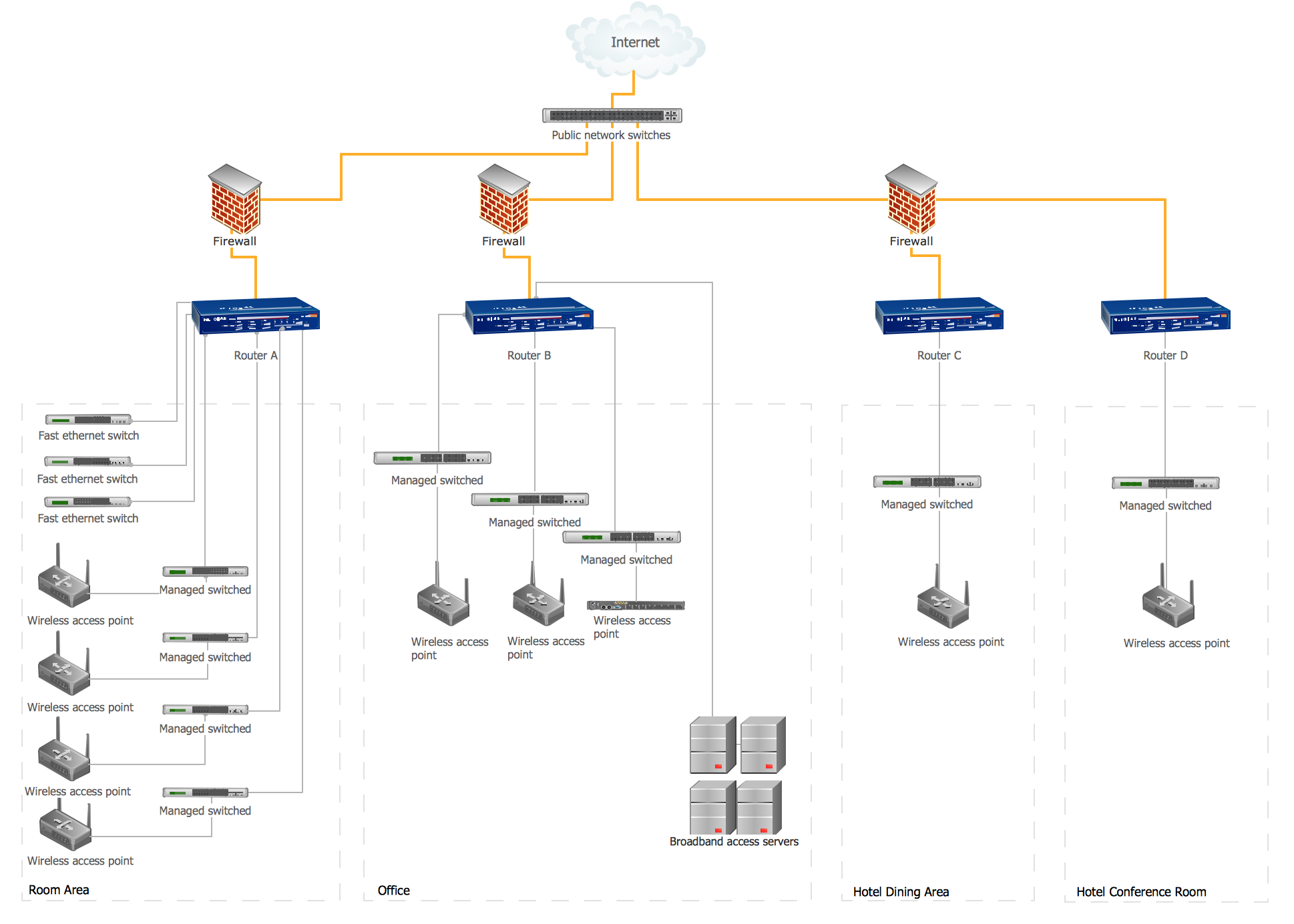
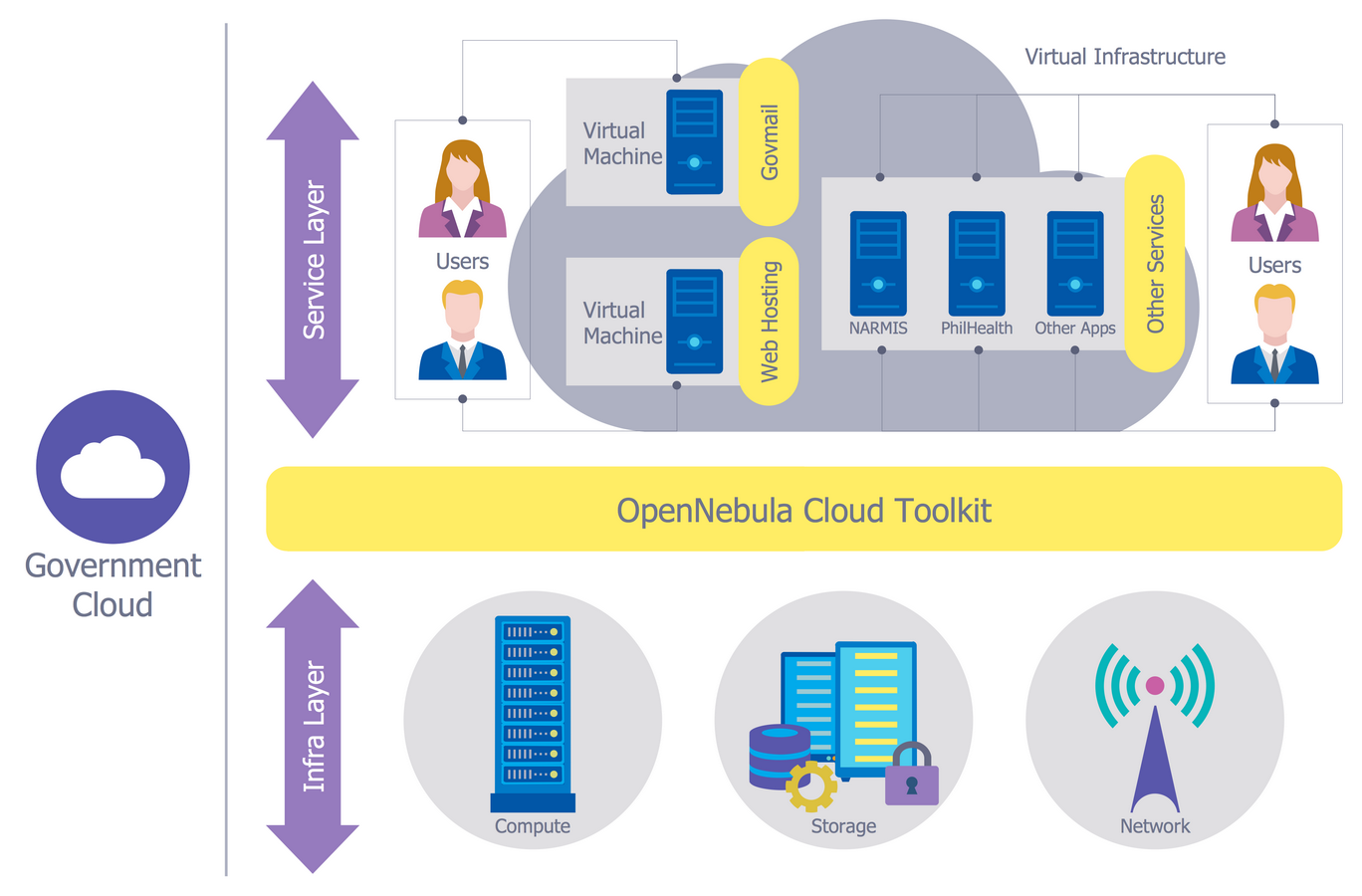
Network topology is a layout of various elements of computer network, such as nodes, links, routers, etc. It is a network topological structure which can be depicted logically or physically. Physical topology shows the physical location of network's components and cable connections between network nodes. Logical topology describes the data flows, the circulation of signals in physical topology. The physical and logical topologies for two networks can be identical, while their physical interconnections, the distances between nodes, transmission rates, and/or signal types may be differ. ConceptDraw DIAGRAM with Computer and Networks solution from Computer and Networks area of ConceptDraw Solution Park lets you design physical and logical network topology diagrams for wireless and wired computer communication networks located in various premises, including the hotels. You can easy design Hotel Network Topology Diagram, diagrams depicted LANs and WLANs, and also any of eight basic topologies (Point-to-point, Star, Bus, Mesh, Ring, Tree, Hybrid, Daisy chain).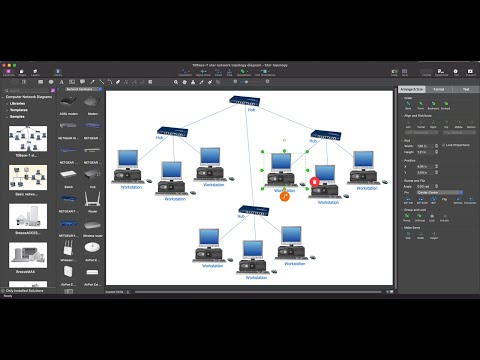
IT Security Solutions
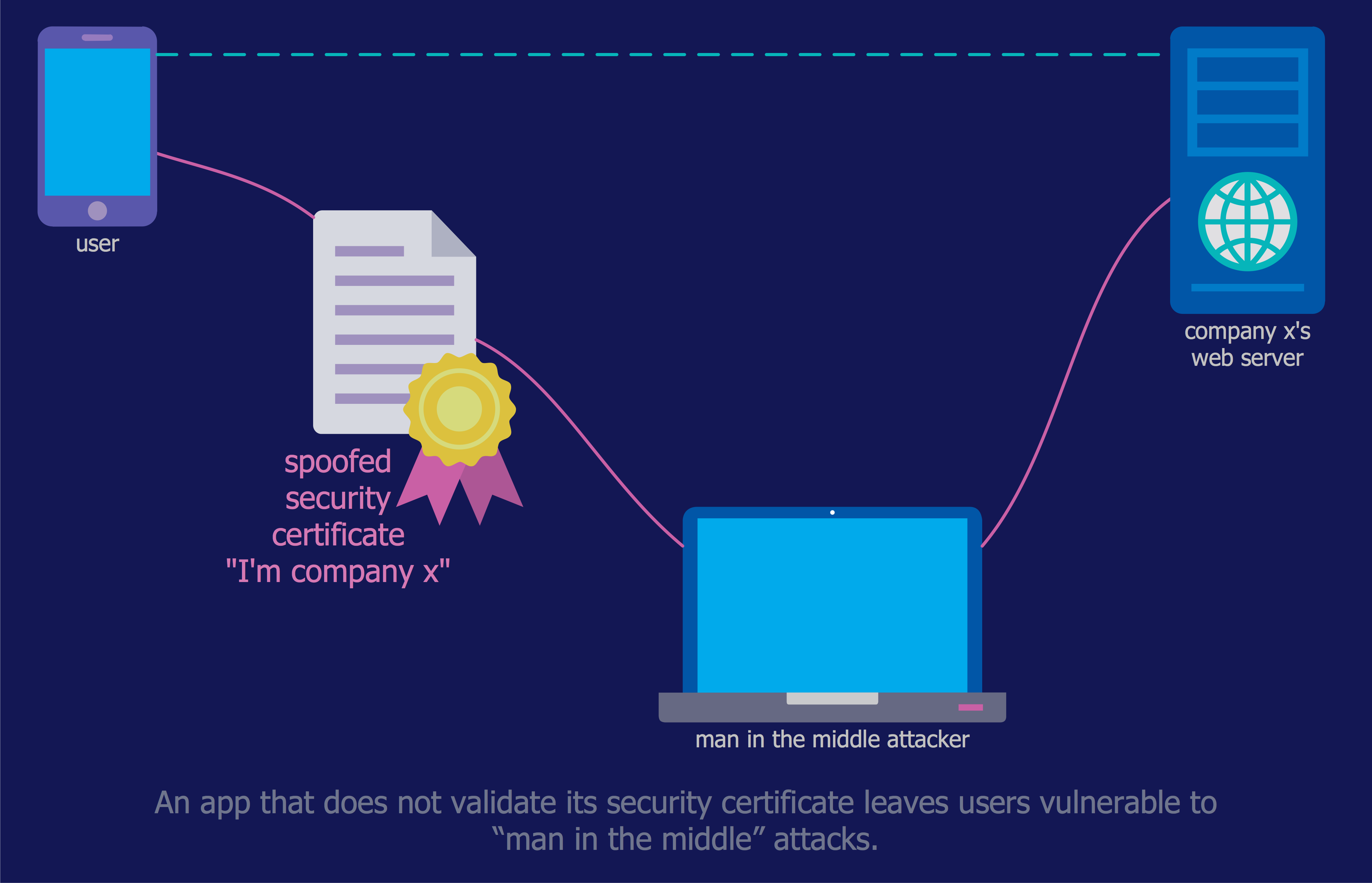
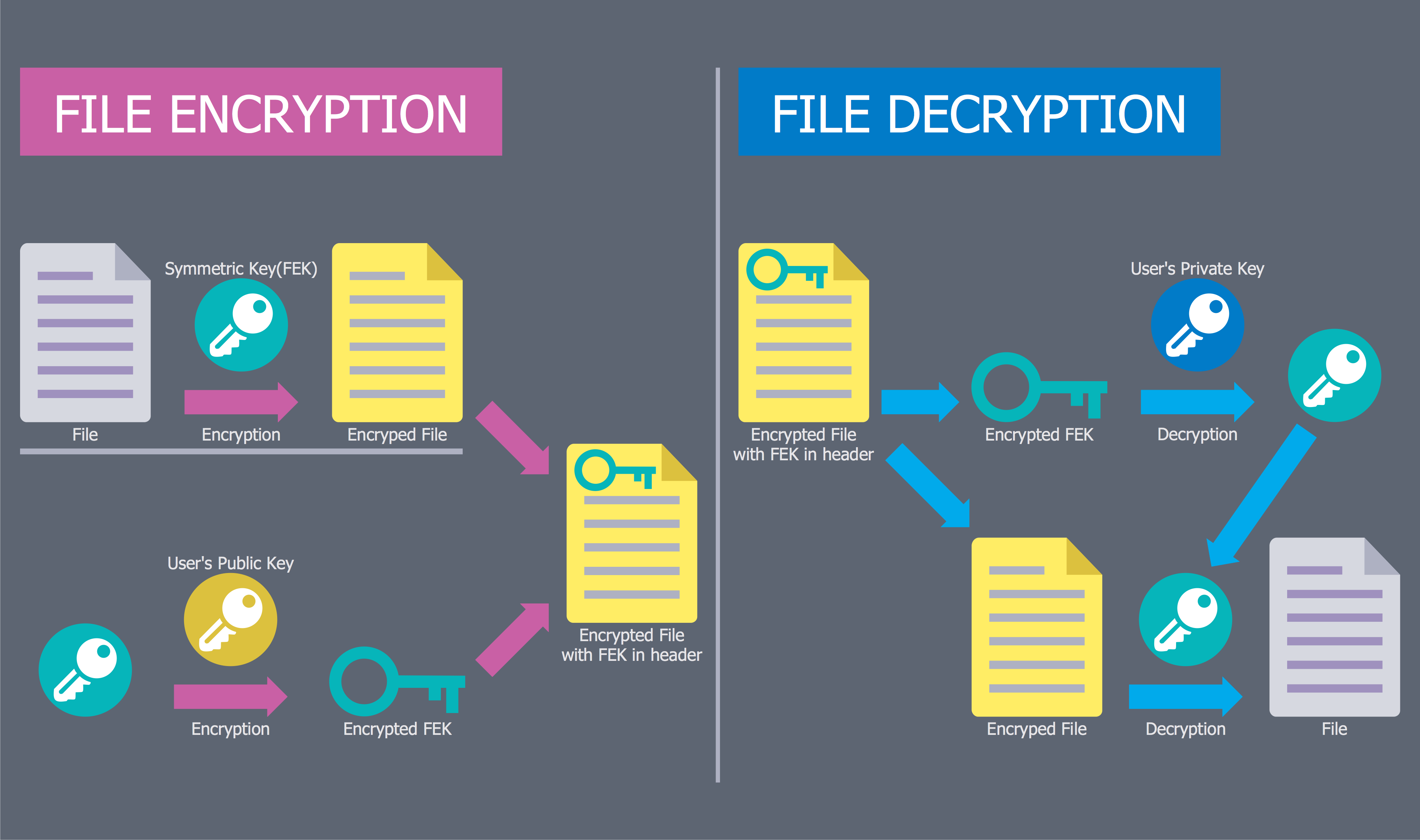
Dynamic of development computer and network technologies increases the need in modern cyber security strategies and IT security solutions to support security of your data, to ensure data privacy, and to protect your operations from the cyber threats. Thanks to the Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park, the ConceptDraw DIAGRAM diagramming and vector drawing software is one of the unique IT security solutions for professional designing Network Security Diagrams.Network Security Diagram
ConceptDraw DIAGRAM diagramming and vector drawing software enhanced with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is the best for effective design professional, colorful and attractive Network Security Diagram of any complexity and degree of detailing.Dealing with Difficult People
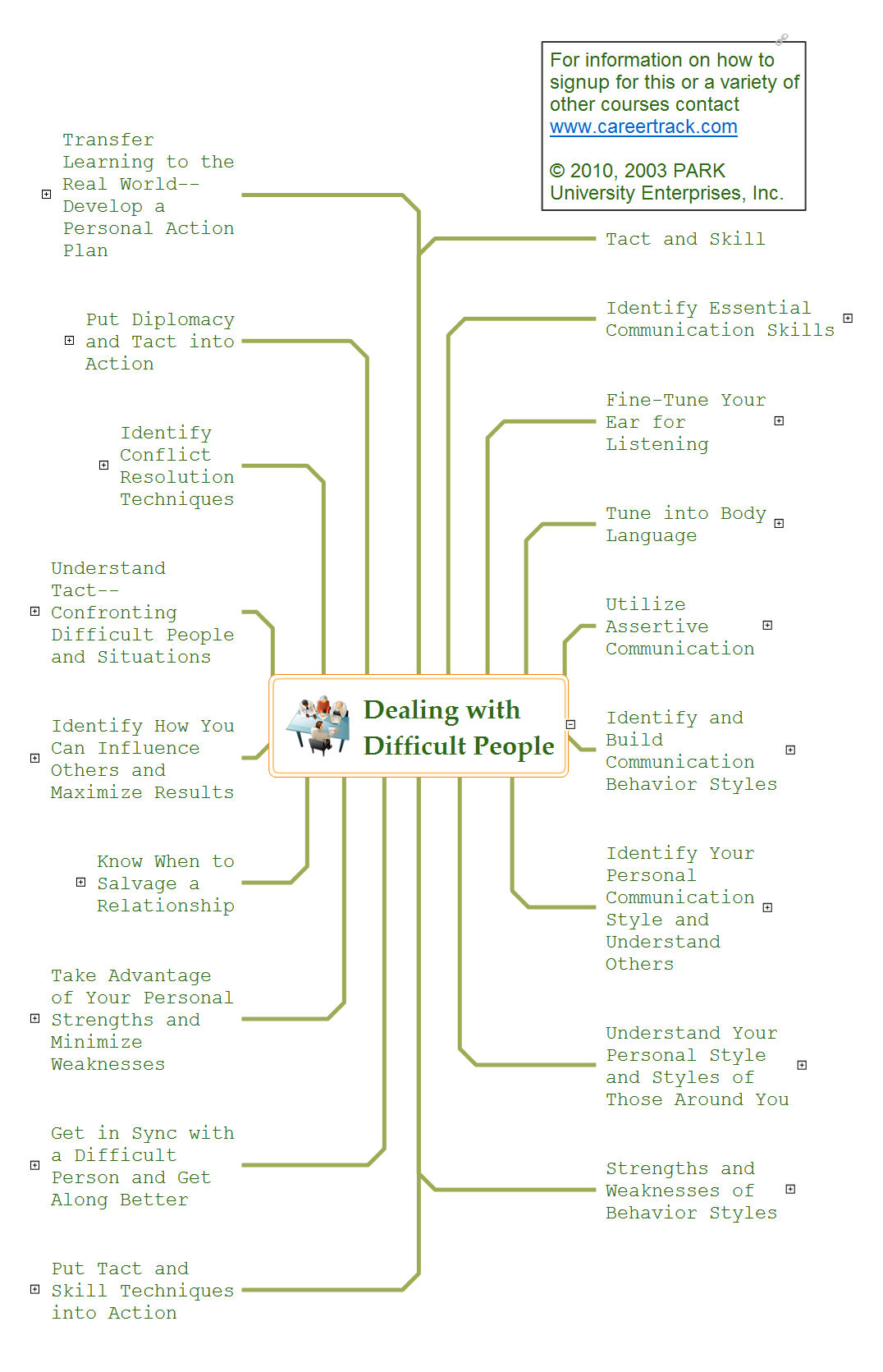
Every day we communicate with many people, but sometimes we meet the people with a complex character that do not go towards, in spite of all our efforts. There are about twelve types of people that are recognized as difficult. What we need to do when dealing with a difficult person? Anyway you must realize that you can not avoid the meeting with people, who consciously or unconsciously, will complicate your life. No matter where you are faced with a difficult person - at work, study, or in other occasions, it is needed try to find a compromise, you can use special approaches to dealing with difficult people. The key point in detecting the approach to difficult people is to realize that the person is difficult to communicate, to stay flexible and calm, retain neutrality, to apply to a specific person an individual approach, given its features, hidden needs and interests, and also your own priorities in this situation. Mind Map is a useful way to describe various approaches that you need to take when dealing with difficult people. Make it easy in ConceptDraw MINDMAP software.Network Security Model
Creation of well thought-out network security model will effectively help you in realization your network's security. ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park lets fast and easy design all variety of network security models: Open network security model, Closed network security model, Restrictive network access model.Internet solutions with ConceptDraw DIAGRAM
ConceptDraw is a good means of visualization of information of any kind as it features powerful graphic capabilities. The conception of using ConceptDraw and open formats by the programs that work with Internet can be used for displaying any data and any structure in Internet.Secure Wireless Network
Use the ConceptDraw DIAGRAM diagramming and vector drawing software enhanced with powerful tools of Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park to effectively visualize the importance of network security and wireless network security, and ways to ensure them, to easily design Network Security Diagrams and Maps, Network Security Model, Secure Wireless Network and Network Security Architecture diagrams.- Internet Security Diagram
- Make Chart On Computer Security
- Advantage And Disadvantage Of Personal Area Network
- Network Security Architecture Diagram | Design elements - AWS ...
- 10 Steps to Cyber Security | Network Security Diagrams | Network ...
- Pan Network Advantages And Disadvantages
- Why People Select ConceptDraw MINDMAP | Internet solutions with ...
- Personal area (PAN) networks. Computer and Network Examples ...
- Extended Star Topology Advantages And Disadvantages
- Data Flow Diagram | Flowcharts | Target and Circular Diagrams | Dfd ...