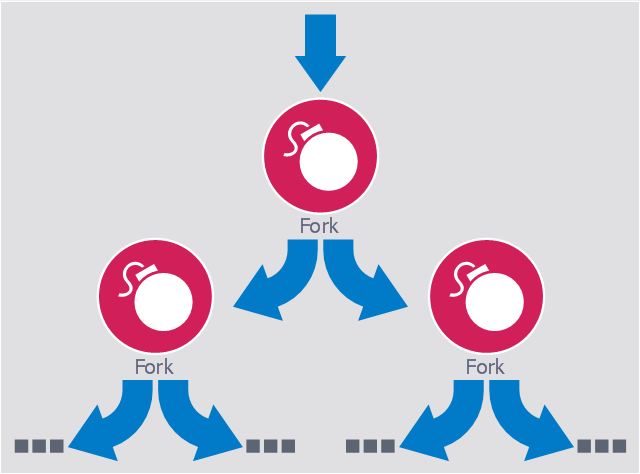
This computer security diagram example was designed on the base of the Wikimedia Commons file: Fork bomb.svg.
"Fork bomb principle. The processes are recursively forked, resulting in a saturation of the available ressources and denial of service." [commons.wikimedia.org/ wiki/ File:Fork_ bomb.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a fork bomb (also called rabbit virus or wabbit) is a denial-of-service attack wherein a process continually replicates itself to deplete available system resources, slowing down or crashing the system due to resource starvation. ...
Fork bombs operate both by consuming CPU time in the process of forking, and by saturating the operating system's process table. A basic implementation of a fork bomb is an infinite loop that repeatedly launches the same process." [Fork bomb. Wikipedia]
The cybersecurity diagram example "Fork bomb" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Fork bomb principle. The processes are recursively forked, resulting in a saturation of the available ressources and denial of service." [commons.wikimedia.org/ wiki/ File:Fork_ bomb.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a fork bomb (also called rabbit virus or wabbit) is a denial-of-service attack wherein a process continually replicates itself to deplete available system resources, slowing down or crashing the system due to resource starvation. ...
Fork bombs operate both by consuming CPU time in the process of forking, and by saturating the operating system's process table. A basic implementation of a fork bomb is an infinite loop that repeatedly launches the same process." [Fork bomb. Wikipedia]
The cybersecurity diagram example "Fork bomb" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
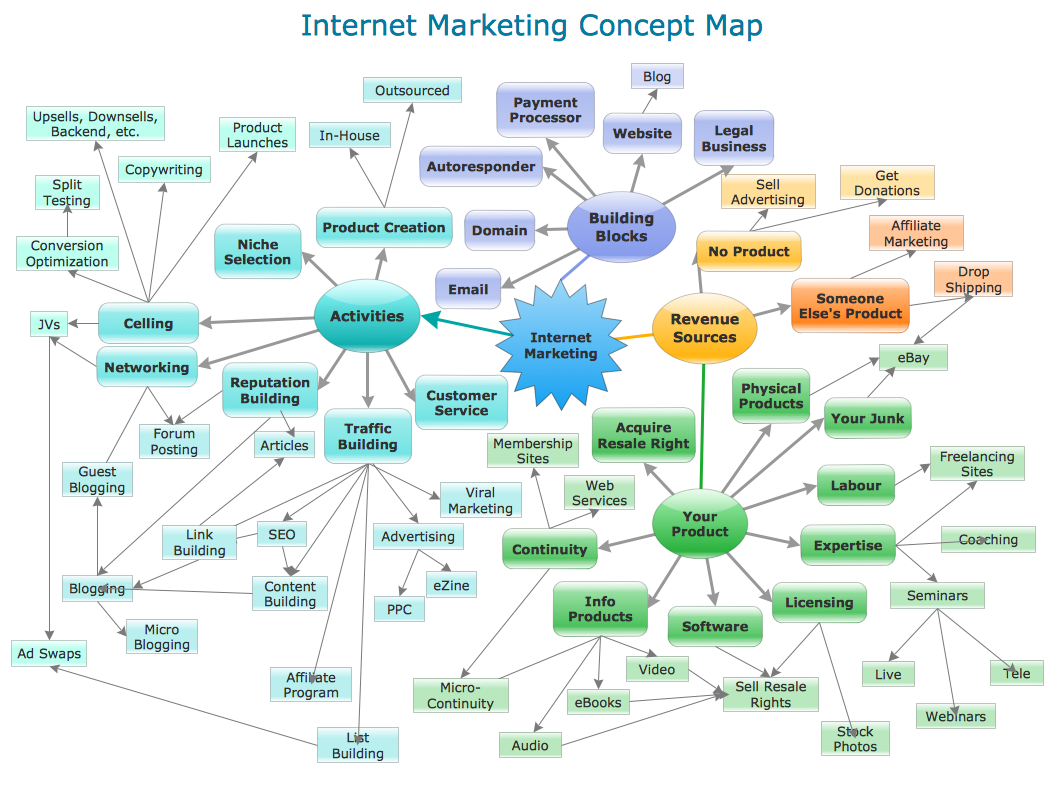
Concept Maps
As concept map consists from conception-blocks and links between them, you can use ConceptDraw library objects and add to a document as much objects as you need. ConceptDraw tools let you to edit, group, move objects, change their appearance and add text signs and raster or vector pictures. ConceptDraw PRO diagramming and vector drawing software extended with Concept Maps Solution from the "What is a Diagram" Area is effective tool for creating professional looking Concept Maps.- How to Draw a Circular Arrows Diagram Using ConceptDraw PRO ...
- Circular diagrams - Vector stencils library | Collaboration life-cycle ...
- How to Draw a Circular Arrows Diagram Using ConceptDraw PRO ...
- Innovation life cycle - Arrow loop diagram | National Preparedness ...
- EU greenhouse gas emissions - Management infogram | Natural ...
- Long Arrow
- Basic Flowchart Symbols and Meaning | Sales arrows - Vector ...
- HR arrows - Vector stencils library | Sales arrows - Vector stencils ...
- Map symbols - Vector stencils library
- Catabolism schematic - Biochemical diagram | Design elements ...
- Buildings and green spaces - Vector stencils library | Buildings and ...
- Flow chart Example. Warehouse Flowchart | Plant Layout Plans ...
- Buildings and green spaces - Vector stencils library | Landmarks ...
- Factory layout floor plan | Buildings and green spaces - Vector ...
- Underground Pict Vector
- Buildings and green spaces - Vector stencils library | Local vehicular ...
- Organizational chart - University leadership | SWOT analysis for a ...
- Flow chart Example. Warehouse Flowchart | Plant Layout Plans ...
- Education pictograms - Vector stencils library | Lifestyle analysis ...
- Transport map - Vector stencils library | Landmarks - Vector stencils ...