The vector stencils library "Active Directory" contains 20 symbols of Active Directory elements for drawing AD network diagrams. It helps network and system administrators to visualize Microsoft Windows Active Directory structures for network design, installation and maintainance.
"An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The AD symbols example "Active Directory - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
"An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The AD symbols example "Active Directory - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
The vector stencils library "Active Directory" contains 20 symbols of Active Directory elements for drawing AD network diagrams. It helps network and system administrators to visualize Microsoft Windows Active Directory structures for network design, installation and maintainance.
"An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The AD symbols example "Active Directory - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
"An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The AD symbols example "Active Directory - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
The vector stencils library "Active Directory" contains 20 symbols of Active Directory elements for drawing AD network diagrams. It helps network and system administrators to visualize Microsoft Windows Active Directory structures for network design, installation and maintainance.
"An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The AD symbols example "Active Directory - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
"An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The AD symbols example "Active Directory - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
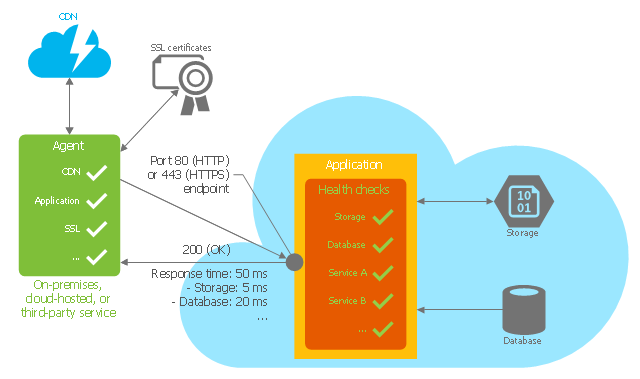
This Azure cloud architecture pattern diagram template was created on the base of figure in the article "Health Endpoint Monitoring Pattern" from the Microsoft Developer Network (MSDN) website.
"Health Endpoint Monitoring Pattern.
Implement functional checks within an application that external tools can access through exposed endpoints at regular intervals. This pattern can help to verify that applications and services are performing correctly. ...
It is good practice—and often a business requirement—to monitor web applications, and middle-tier and shared services, to ensure that they are available and performing correctly. However, it is more difficult to monitor services running in the cloud than it is to monitor on-premises services. ...
Implement health monitoring by sending requests to an endpoint on the application. The application should perform the necessary checks, and return an indication of its status.
A health monitoring check typically combines two factors: the checks (if any) performed by the application or service in response to the request to the health verification endpoint, and analysis of the result by the tool or framework that is performing the health verification check. The response code indicates the status of the application and, optionally, any components or services it uses. The latency or response time check is performed by the monitoring tool or framework." [msdn.microsoft.com/ ru-RU/ library/ dn589789.aspx]
The Azure cloud system architecture diagram template "Health endpoint monitoring pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
"Health Endpoint Monitoring Pattern.
Implement functional checks within an application that external tools can access through exposed endpoints at regular intervals. This pattern can help to verify that applications and services are performing correctly. ...
It is good practice—and often a business requirement—to monitor web applications, and middle-tier and shared services, to ensure that they are available and performing correctly. However, it is more difficult to monitor services running in the cloud than it is to monitor on-premises services. ...
Implement health monitoring by sending requests to an endpoint on the application. The application should perform the necessary checks, and return an indication of its status.
A health monitoring check typically combines two factors: the checks (if any) performed by the application or service in response to the request to the health verification endpoint, and analysis of the result by the tool or framework that is performing the health verification check. The response code indicates the status of the application and, optionally, any components or services it uses. The latency or response time check is performed by the monitoring tool or framework." [msdn.microsoft.com/ ru-RU/ library/ dn589789.aspx]
The Azure cloud system architecture diagram template "Health endpoint monitoring pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
- Certificate template
- Certificate Templates
- | Active Directory - Vector stencils library | | Network Security Certificate
- Certificate Design
- Sign Making Software | Create Flow Chart on Mac | Certificate Maker ...
- Certificate Software
- Certificate Design Software
- Active Directory - Vector stencils library | Network Glossary Definition ...
- Certificates Design
- Active Directory Domain Services | Active Directory Diagram | Single ...
- Active Directory Diagram | Active Directory structure diagram | How ...
- Active Directory Domain Services | Active Directory Diagram | Active ...
- IP Subnet mask calculator - Template | Cisco products additional ...
- Active Directory Diagram | Network Diagramming Software for ...
- Active Directory Diagram | Active Directory structure diagram | Active ...
- ConceptDraw PRO Network Diagram Tool | Network Security Tips ...
- Network Security Model | Network Security Diagrams | Network ...
- Active Directory Windows
- Tree Network Topology Diagram | Network Glossary Definition ...