Sign Making Software
ConceptDraw DIAGRAM is a powerful sign making software thanks to the vector stencils library "Recreation signs". This library is included in the Directional Maps solution from the Maps area of ConceptDraw Solution Park. Sign making software is very useful tool for professional sign-making business. Use ConceptDraw DIAGRAM and make sure that now sign making is easier and timesaving than ever!Entity Relationship Software
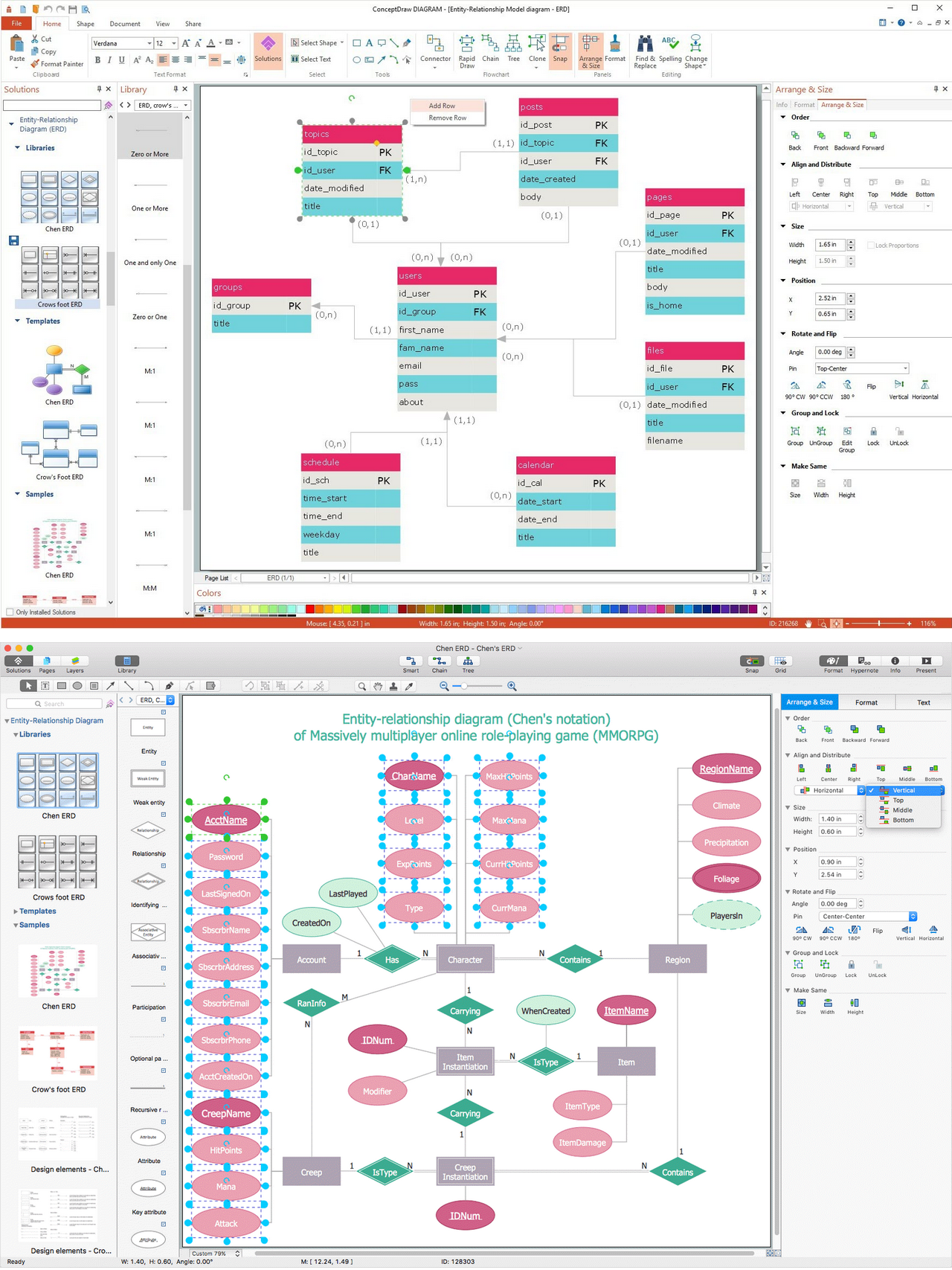
Entity Relationship Diagram (ERD) is a leading data modeling tool that is used to illustrate the logical structure of database, helps to organize and represent your project's data in terms of entities, attributes and relationships. To describe the database structure usually is used the ERD Chen's or Crow's Foot notation. Chen's notation supposes the representation of entities by rectangles with the entities names inside, relationships by diamonds and attributes by ovals connected with a line to exactly one entity. In Crow's Foot notation the boxes are used to depict the entities and their attributes, the lines between them - to depict relationships. ConceptDraw DIAGRAM software extended with Entity-Relationship Diagram (ERD) Solution is convenient and useful for designing the ER Diagrams, and supports the use of Chen's or Crow’s Foot notation according to your needs and desires. The ERD diagrams produced with ConceptDraw DIAGRAM Entity Relationship Diagram software can be successfully used in whitepapers, presentations, posters, datasheets, technical materials, etc.Quality Control Chart Software — ISO Flowcharting
Quality Control Chart Software (ISO Flowcharting) - ConceptDraw DIAGRAM extended with Total Quality Management TQM Diagrams Solution from the Quality Management Area is the best diagramming and vector drawing software that allows you to draw the quality control charts quick and easy. The quality control chart is a graphic that illustrates the accordance of processes or products to the intended specifications and degree of differences from them. Depending on what type of data you need analyze, there are used different types of quality control charts: X-bar charts, S charts, Np charts.Entity Relationship Diagram Examples
Creation of Entity-Relationship (ER) model is a visual representation the structure of a business database, where data equates to entities or objects, which are linked by defined relationships expressing dependencies and requirements. By the nature, the ER model is an abstract visualization, a first step in design process towards creating a logical and functional database. ConceptDraw DIAGRAM professional software gives the ability to effectively describe a database using the Entity-Relationship model. Included to ConceptDraw Solution Park, the Entity-Relationship Diagram (ERD) solution contains the set of predesigned vector icons advocated by Chen's and Crow’s Foot notations that both can be used for data modeling and describing a database. Entity-Relationship Diagram (ERD) solution includes also helpful templates and incredibly large collection of varied Entity Relationship Diagram examples and samples offered at ConceptDraw STORE. Each of them can be used to develop your own model of a database of arbitrary complexity.
Network Diagramming Software for Design Network Layout Diagrams
ConceptDraw DIAGRAM is perfect for software designers and software developers who need to draw Network Layout Diagrams.
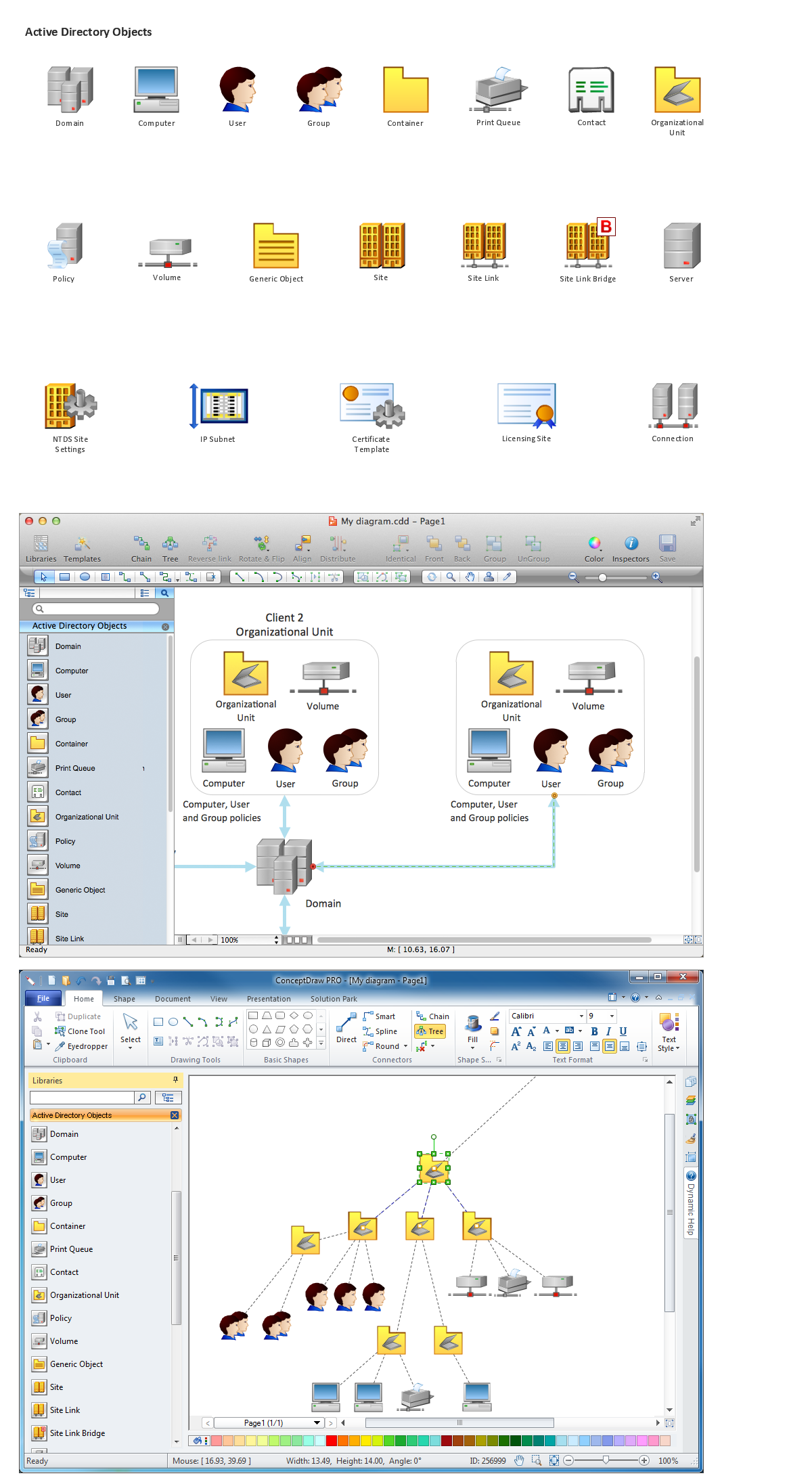
Network Diagramming Software for Network Active Directory Diagrams
ConceptDraw DIAGRAM is perfect for software designers and software developers who need to draw Network Active Directory Diagrams.
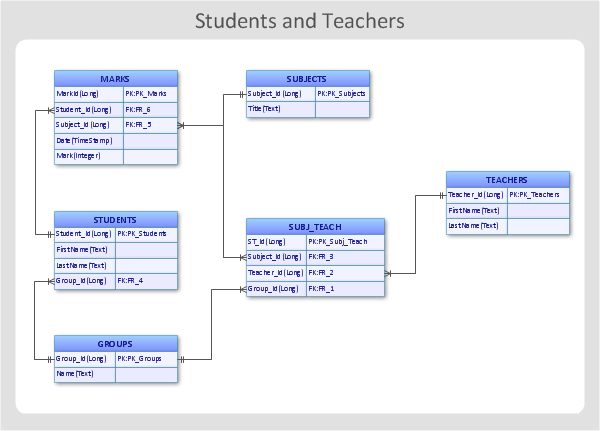
Entity-Relationship Diagram
Entity Relationship Diagram (ERD) is the world-known way to show the logical structure of databases in visual manner. The best software tool for drawing Entity-Relationship Diagram is ConceptDraw DIAGRAM ector graphics software with Entity-Relationship Diagram (ERD) solution from Software Development area which gives the ability to describe a database using the Entity-Relationship model. The vector graphic diagrams produced using this solution can be successfully used in whitepapers, presentations, datasheets, posters, or any technical materials.UML Use Case Diagram Example. Registration System
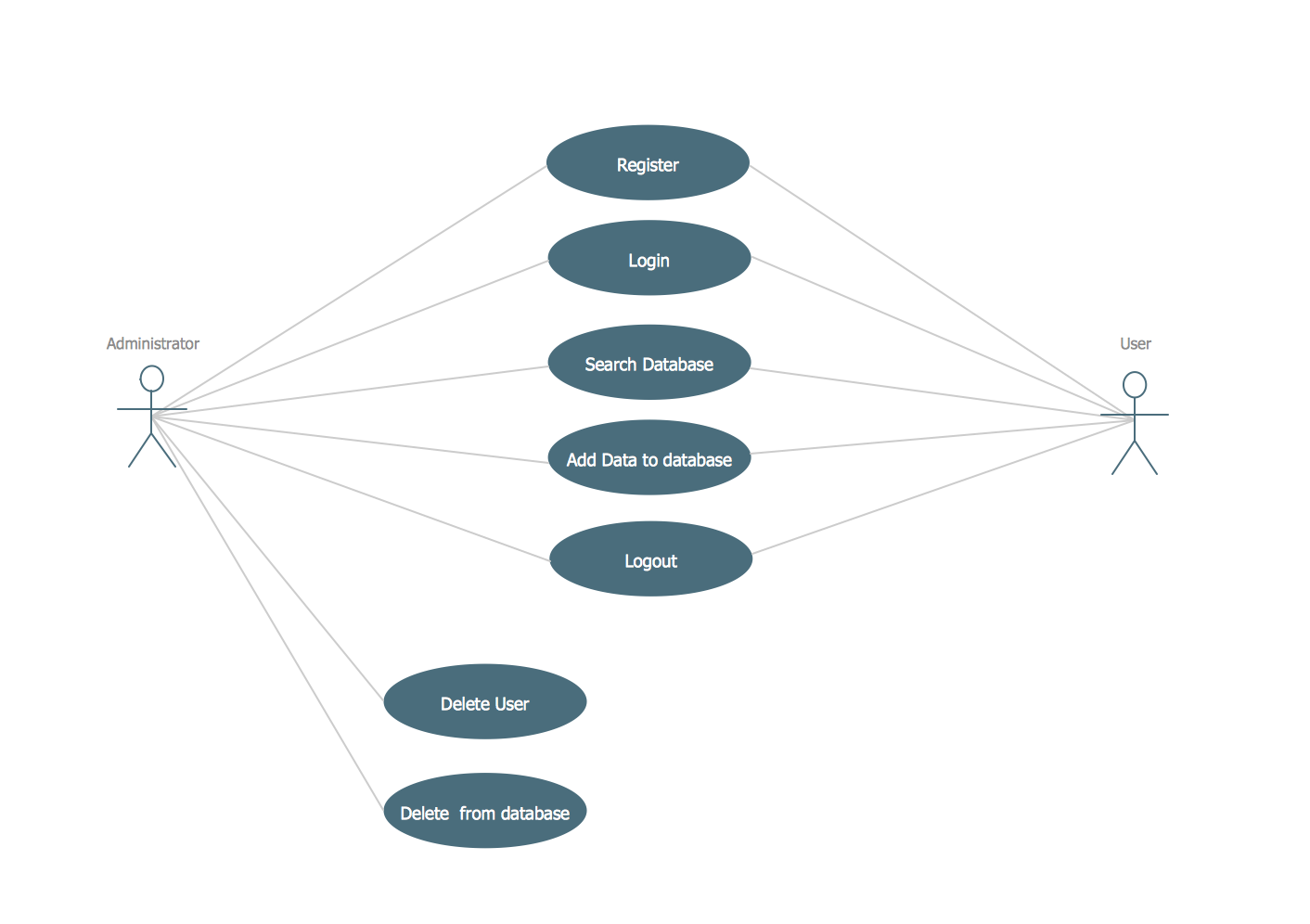
This sample was created in ConceptDraw DIAGRAM diagramming and vector drawing software using the UML Use Case Diagram library of the Rapid UML Solution from the Software Development area of ConceptDraw Solution Park. This sample shows the types of user’s interactions with the system and is used at the registration and working with the database system.Telecommunication networks. Computer and Network Examples
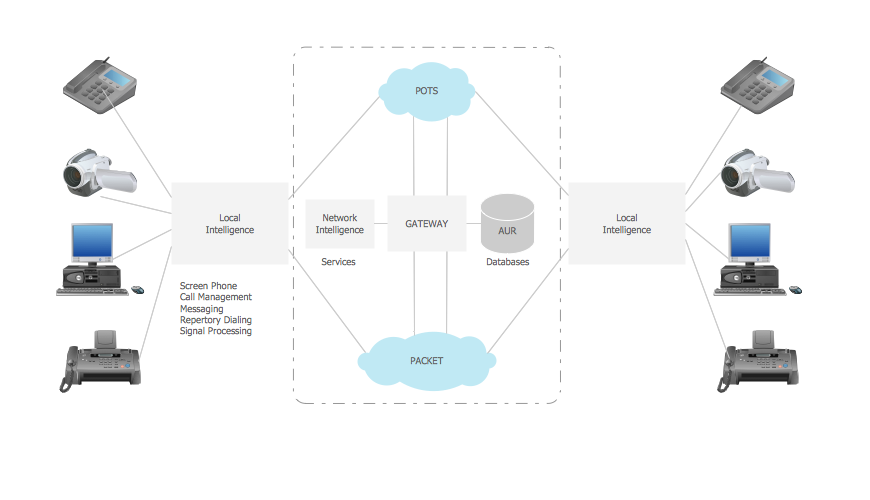
A Telecommunications network is a network of nodes, links, trunks and telephone switches that are connected, operated by telephone companies and realize telephone, audio, visual and data communications among the users. The telecommunications network can also include Internet, microwave, wireless equipment. This example was created in ConceptDraw DIAGRAM using the Computer and Networks Area of ConceptDraw Solution Park and shows the Telecommunications network.
This vector stencils library contains 184 round icons.
Use it to design cloud computing infographics and diagrams with ConceptDraw PRO software.
"Though service-oriented architecture advocates "everything as a service" (with the acronyms EaaS or XaaS or simply aas), cloud-computing providers offer their "services" according to different models, which happen to form a stack: infrastructure-, platform- and software-as-a-service.
Infrastructure as a service (IaaS)
In the most basic cloud-service model ... providers of IaaS offer computers — physical or (more often) virtual machines — and other resources. IaaS refers to online services that abstract the user from the details of infrastructure like physical computing resources, location, data partitioning, scaling, security, backup etc.
Platform as a service (PaaS)
PaaS vendors offer a development environment to application developers. The provider typically develops toolkit and standards for development and channels for distribution and payment. In the PaaS models, cloud providers deliver a computing platform, typically including operating system, programming-language execution environment, database, and web server. Application developers can develop and run their software solutions on a cloud platform without the cost and complexity of buying and managing the underlying hardware and software layers.
Software as a service (SaaS)
In the software as a service (SaaS) model, users gain access to application software and databases. Cloud providers manage the infrastructure and platforms that run the applications. SaaS is sometimes referred to as "on-demand software" and is usually priced on a pay-per-use basis or using a subscription fee.
In the SaaS model, cloud providers install and operate application software in the cloud and cloud users access the software from cloud clients. Cloud users do not manage the cloud infrastructure and platform where the application runs. This eliminates the need to install and run the application on the cloud user's own computers, which simplifies maintenance and support. Cloud applications differ from other applications in their scalability — which can be achieved by cloning tasks onto multiple virtual machines at run-time to meet changing work demand." [Cloud computing. Wikipedia]
The vector stencils library "Cloud round icons" is included in the Cloud Computing Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design cloud computing infographics and diagrams with ConceptDraw PRO software.
"Though service-oriented architecture advocates "everything as a service" (with the acronyms EaaS or XaaS or simply aas), cloud-computing providers offer their "services" according to different models, which happen to form a stack: infrastructure-, platform- and software-as-a-service.
Infrastructure as a service (IaaS)
In the most basic cloud-service model ... providers of IaaS offer computers — physical or (more often) virtual machines — and other resources. IaaS refers to online services that abstract the user from the details of infrastructure like physical computing resources, location, data partitioning, scaling, security, backup etc.
Platform as a service (PaaS)
PaaS vendors offer a development environment to application developers. The provider typically develops toolkit and standards for development and channels for distribution and payment. In the PaaS models, cloud providers deliver a computing platform, typically including operating system, programming-language execution environment, database, and web server. Application developers can develop and run their software solutions on a cloud platform without the cost and complexity of buying and managing the underlying hardware and software layers.
Software as a service (SaaS)
In the software as a service (SaaS) model, users gain access to application software and databases. Cloud providers manage the infrastructure and platforms that run the applications. SaaS is sometimes referred to as "on-demand software" and is usually priced on a pay-per-use basis or using a subscription fee.
In the SaaS model, cloud providers install and operate application software in the cloud and cloud users access the software from cloud clients. Cloud users do not manage the cloud infrastructure and platform where the application runs. This eliminates the need to install and run the application on the cloud user's own computers, which simplifies maintenance and support. Cloud applications differ from other applications in their scalability — which can be achieved by cloning tasks onto multiple virtual machines at run-time to meet changing work demand." [Cloud computing. Wikipedia]
The vector stencils library "Cloud round icons" is included in the Cloud Computing Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
- Printing Certificates Software
- Certificates Design
- Sign Making Software | Professional Looking Certificate Format
- Professional Certificate Maker
- Certificate Courses Templates For Students
- Personnel Software Free
- Software Certificate Sample
- AWS Architecture Diagrams | Funnel Chart | Marketing Diagrams ...
- Modern Training Certificates Templates
- Certificate Maker Free Download

_Win_Mac.png)