The vector stencils library "Cybersecurity round icons" contains 150 network security diagram icons.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"A computer network diagram is a schematic depicting the nodes and connections amongst nodes in a computer network or, more generally, any telecommunications network. ...
Readily identifiable icons are used to depict common network appliances e.g. Router, and the style of lines between them indicate the type of connection. Clouds are used to represent networks external to the one pictured for the purposes of depicting connections between internal and external devices, without indicating the specifics of the outside network." [Computer network diagram. Wikipedia]
The pictograms example "Design elements - Cybersecurity round icons" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"A computer network diagram is a schematic depicting the nodes and connections amongst nodes in a computer network or, more generally, any telecommunications network. ...
Readily identifiable icons are used to depict common network appliances e.g. Router, and the style of lines between them indicate the type of connection. Clouds are used to represent networks external to the one pictured for the purposes of depicting connections between internal and external devices, without indicating the specifics of the outside network." [Computer network diagram. Wikipedia]
The pictograms example "Design elements - Cybersecurity round icons" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
The vector stencils library "Cloud round icons" contains 184 cloud computing pictograms.
Use it to design your cloud computing diagrams and infographics with ConceptDraw PRO software.
"Graphically, the icon is a stylized picture of objects that users are familiar with from office environment or from other professional arenas. ...
The design of all computer icons is constricted by the limitations of the device display. ... They are frequently scalable, as they are displayed in different positions in the software. The colors used, of both the image and the icon background, should stand out on different system backgrounds. The detailing of the icon image needs to be simple, remaining recognizable in varying graphical resolutions and screen sizes. Computer icons are by definition language-independent; they do not rely on letters or words to convey their meaning." [Icon (computing). Wikipedia]
The icon set example "Design elements - Cloud round icons" is included in the Cloud Computing Diagrams solution from the Computer and Networks area from ConceptDraw Solution Park.
Use it to design your cloud computing diagrams and infographics with ConceptDraw PRO software.
"Graphically, the icon is a stylized picture of objects that users are familiar with from office environment or from other professional arenas. ...
The design of all computer icons is constricted by the limitations of the device display. ... They are frequently scalable, as they are displayed in different positions in the software. The colors used, of both the image and the icon background, should stand out on different system backgrounds. The detailing of the icon image needs to be simple, remaining recognizable in varying graphical resolutions and screen sizes. Computer icons are by definition language-independent; they do not rely on letters or words to convey their meaning." [Icon (computing). Wikipedia]
The icon set example "Design elements - Cloud round icons" is included in the Cloud Computing Diagrams solution from the Computer and Networks area from ConceptDraw Solution Park.
Network Security Devices
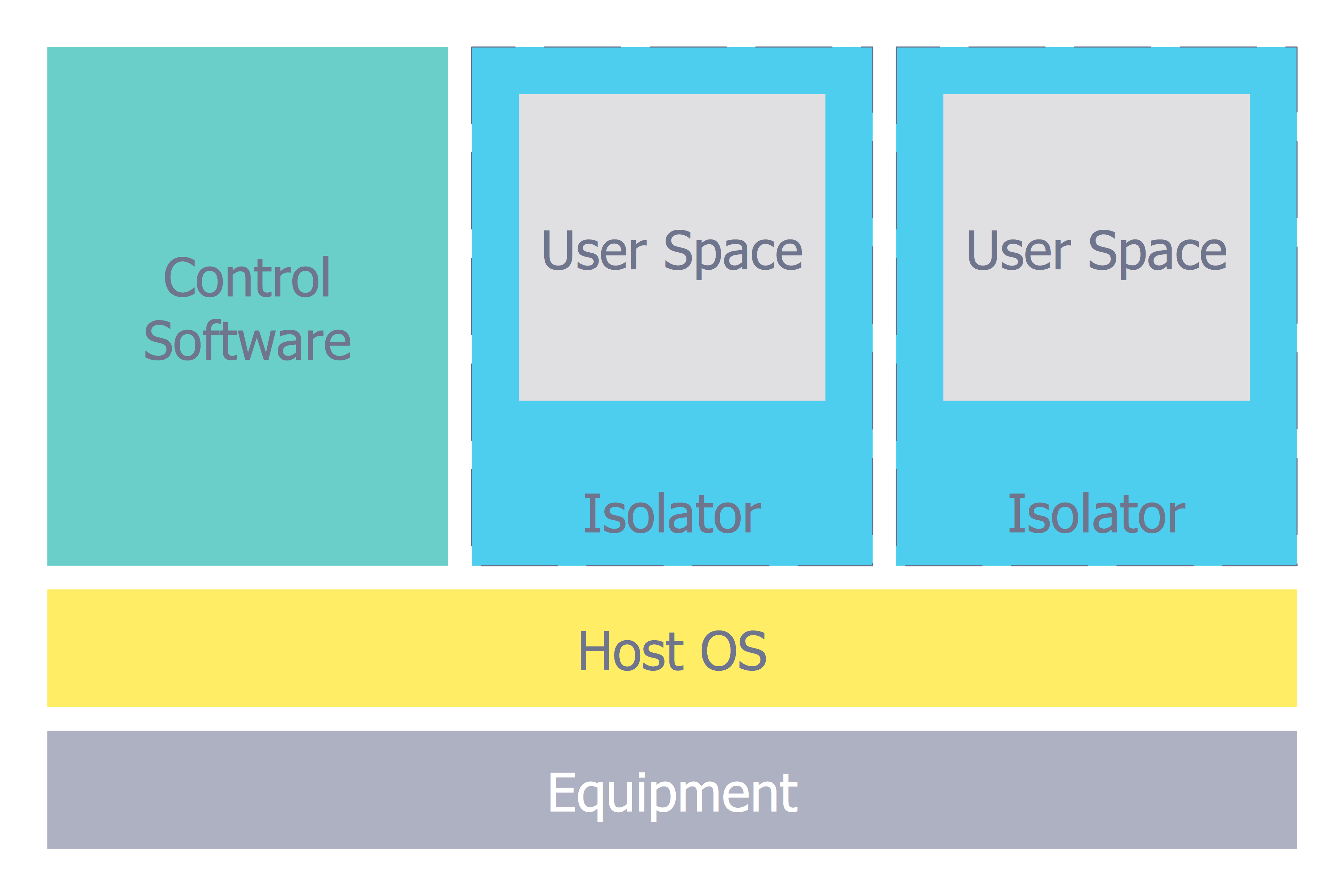
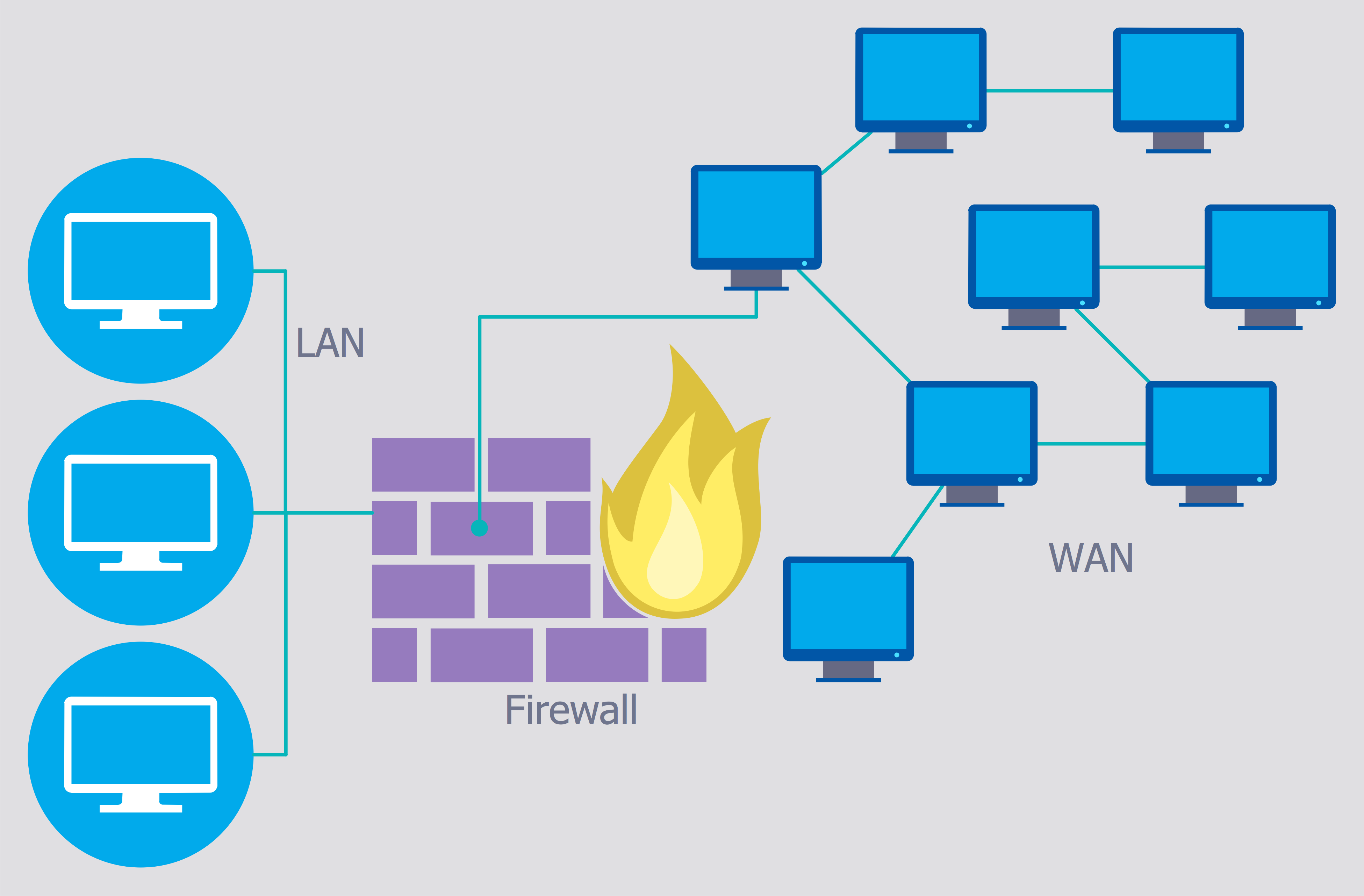
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.Network Security
The Internet is a giant computer network which connects computers all over the world. It is integral part of human society and business. But the serious question for network engineers, designers, lawmakers and enforcers is the need for protect the Internet networks from the Internet crimes, hacking and attacks. There are quite a number of hardware, software and physical methods of protection against them. The samples you see on this page were created in ConceptDraw PRO using the tools of Network Security Diagrams Solution for ConceptDraw PRO software. They show protection networks with Firewalls and other network security devices.This vector stencils library contains 184 round icons.
Use it to design cloud computing infographics and diagrams with ConceptDraw PRO software.
"Though service-oriented architecture advocates "everything as a service" (with the acronyms EaaS or XaaS or simply aas), cloud-computing providers offer their "services" according to different models, which happen to form a stack: infrastructure-, platform- and software-as-a-service.
Infrastructure as a service (IaaS)
In the most basic cloud-service model ... providers of IaaS offer computers — physical or (more often) virtual machines — and other resources. IaaS refers to online services that abstract the user from the details of infrastructure like physical computing resources, location, data partitioning, scaling, security, backup etc.
Platform as a service (PaaS)
PaaS vendors offer a development environment to application developers. The provider typically develops toolkit and standards for development and channels for distribution and payment. In the PaaS models, cloud providers deliver a computing platform, typically including operating system, programming-language execution environment, database, and web server. Application developers can develop and run their software solutions on a cloud platform without the cost and complexity of buying and managing the underlying hardware and software layers.
Software as a service (SaaS)
In the software as a service (SaaS) model, users gain access to application software and databases. Cloud providers manage the infrastructure and platforms that run the applications. SaaS is sometimes referred to as "on-demand software" and is usually priced on a pay-per-use basis or using a subscription fee.
In the SaaS model, cloud providers install and operate application software in the cloud and cloud users access the software from cloud clients. Cloud users do not manage the cloud infrastructure and platform where the application runs. This eliminates the need to install and run the application on the cloud user's own computers, which simplifies maintenance and support. Cloud applications differ from other applications in their scalability — which can be achieved by cloning tasks onto multiple virtual machines at run-time to meet changing work demand." [Cloud computing. Wikipedia]
The vector stencils library "Cloud round icons" is included in the Cloud Computing Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design cloud computing infographics and diagrams with ConceptDraw PRO software.
"Though service-oriented architecture advocates "everything as a service" (with the acronyms EaaS or XaaS or simply aas), cloud-computing providers offer their "services" according to different models, which happen to form a stack: infrastructure-, platform- and software-as-a-service.
Infrastructure as a service (IaaS)
In the most basic cloud-service model ... providers of IaaS offer computers — physical or (more often) virtual machines — and other resources. IaaS refers to online services that abstract the user from the details of infrastructure like physical computing resources, location, data partitioning, scaling, security, backup etc.
Platform as a service (PaaS)
PaaS vendors offer a development environment to application developers. The provider typically develops toolkit and standards for development and channels for distribution and payment. In the PaaS models, cloud providers deliver a computing platform, typically including operating system, programming-language execution environment, database, and web server. Application developers can develop and run their software solutions on a cloud platform without the cost and complexity of buying and managing the underlying hardware and software layers.
Software as a service (SaaS)
In the software as a service (SaaS) model, users gain access to application software and databases. Cloud providers manage the infrastructure and platforms that run the applications. SaaS is sometimes referred to as "on-demand software" and is usually priced on a pay-per-use basis or using a subscription fee.
In the SaaS model, cloud providers install and operate application software in the cloud and cloud users access the software from cloud clients. Cloud users do not manage the cloud infrastructure and platform where the application runs. This eliminates the need to install and run the application on the cloud user's own computers, which simplifies maintenance and support. Cloud applications differ from other applications in their scalability — which can be achieved by cloning tasks onto multiple virtual machines at run-time to meet changing work demand." [Cloud computing. Wikipedia]
The vector stencils library "Cloud round icons" is included in the Cloud Computing Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
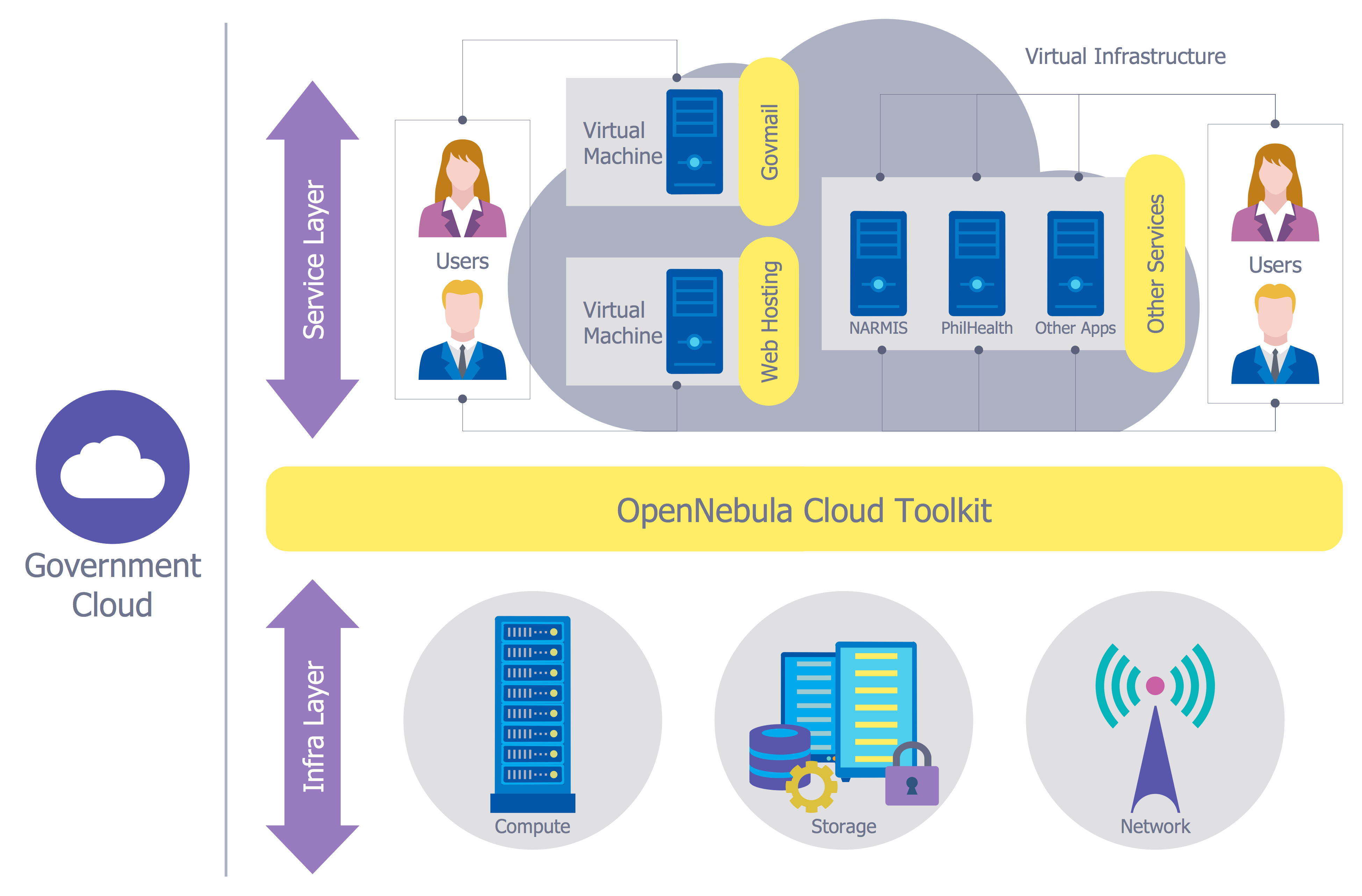
 Computer and Network Package
Computer and Network Package
Computer and Network Package is a large set of valuable graphical solutions from ConceptDraw Solution Park, developed and specially selected to help computer network specialists and IT professionals to realize their daily work the most efficiently and quickly. This package contains extensive set of graphic design tools, ready-to-use vector elements, built-in templates and samples for designing professional-looking diagrams, charts, schematics and infographics in a field of computer network technologies, cloud computing, vehicular networking, wireless networking, ensuring networks security and networks protection. It is useful for designing different floor plans and layout plans for homes, offices, hotels and instantly construction detailed schemes of computer networks and wireless networks on them, for making professional-looking and colorful Pie Charts, Bar Graphs and Line Charts visualizing the relevant information and data.
Basic Flowchart Symbols and Meaning
Flowcharts are the best for visually representation the business processes and the flow of a custom-order process through various departments within an organization. ConceptDraw PRO diagramming and vector drawing software extended with Flowcharts solution offers the full set of predesigned basic flowchart symbols which are gathered at two libraries: Flowchart and Flowcharts Rapid Draw. Among them are: process, terminator, decision, data, document, display, manual loop, and many other specific symbols. The meaning for each symbol offered by ConceptDraw gives the presentation about their proposed use in professional Flowcharts for business and technical processes, software algorithms, well-developed structures of web sites, Workflow diagrams, Process flow diagram and correlation in developing on-line instructional projects or business process system. Use of ready flow chart symbols in diagrams is incredibly useful - you need simply drag desired from the libraries to your document and arrange them in required order. There are a few serious alternatives to Visio for Mac, one of them is ConceptDraw PRO. It is one of the main contender with the most similar features and capabilities.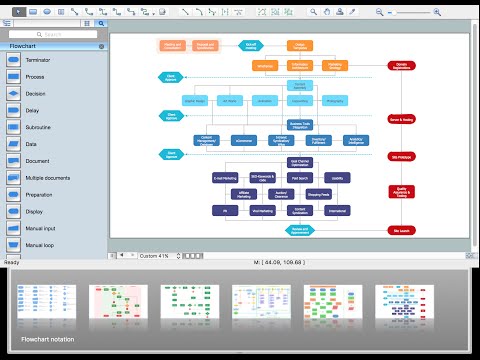
Network Security Architecture Diagram
Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram? We recommend to use ConceptDraw PRO extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.Secure Wireless Network
Use the ConceptDraw PRO diagramming and vector drawing software enhanced with powerful tools of Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park to effectively visualize the importance of network security and wireless network security, and ways to ensure them, to easily design Network Security Diagrams and Maps, Network Security Model, Secure Wireless Network and Network Security Architecture diagrams.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution enhances the ConceptDraw PRO v10 functionality with large collection of predesigned vector stencils of cybersecurity clipart, shapes, icons and connectors to help you succeed in designing professional and accurate Ne
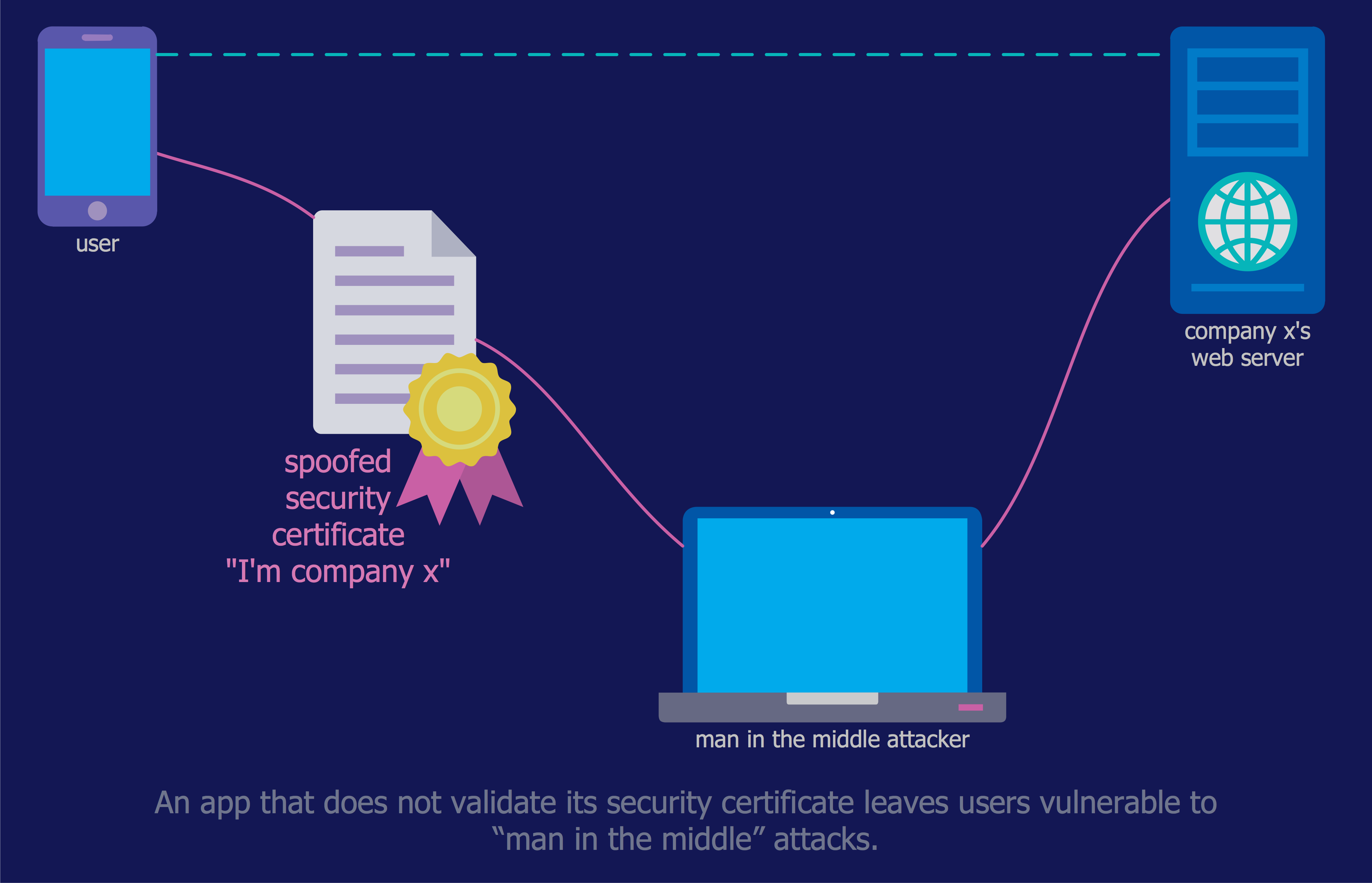
Cyber Security Degrees
For protection various cyber environments are developed and applied large variety of cyber security standards, techniques, security concepts and approaches with different cyber security degrees. The ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park offers the number of useful tools which will help network security engineers, cyber security specialists, network and computer analysts easily and visually depict the knowledge and skills for research and prevention of intrusions, about protection critical information and analysis of cyber incidents, and for how to assess threats and vulnerabilities.
 Computer Network Diagrams
Computer Network Diagrams
Computer Network Diagrams solution extends ConceptDraw PRO software with samples, templates and libraries of vector stencils for drawing the computer network topology diagrams.
 Cloud Computing Diagrams
Cloud Computing Diagrams
The Cloud Computing Diagrams solution extends the functionality of the ConceptDraw PRO software with comprehensive collection of libraries of cloud computing vector stencils to help you get started design of Cloud Computing Diagrams and Architecture D
IT Security Solutions
Dynamic of development computer and network technologies increases the need in modern cyber security strategies and IT security solutions to support security of your data, to ensure data privacy, and to protect your operations from the cyber threats. Thanks to the Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park, the ConceptDraw PRO diagramming and vector drawing software is one of the unique IT security solutions for professional designing Network Security Diagrams.Network Security Model
Creation of well thought-out network security model will effectively help you in realization your network's security. ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park lets fast and easy design all variety of network security models: Open network security model, Closed network security model, Restrictive network access model.- Cloud round icons
- Document Icon Png Round Blue Grey
- ConceptDraw Arrows10 Technology | Routing Blue Round Icon
- Database Icon Circle White Blue
- Examples Of Computer Icon And Their Meaning
- Cloud round icons - Vector stencils library | Education pictograms ...
- Location Icons Png Round Blue
- Design elements - Windows 8 round icons | Design elements ...
- Design elements - Cybersecurity round icons | Network Security ...
- Cloud Computing Architecture Diagrams | Design elements - Cloud ...
- DroidDia PRO unlocker | Cloud round icons - Vector stencils library ...
- Design elements - Cloud round icons | Glyph icons - Vector stencils ...
- Spread of Conficker worm | Network Security Diagrams | Design ...
- Computer Icons
- Desktop Vector Icon Png
- Cloud Computing Architecture Diagrams | Cloud round icons ...
- Cisco Network Topology. Cisco icons , shapes, stencils and symbols ...
- Cloud round icons - Vector stencils library | Cisco LAN - Vector ...
- Cloud Computing Architecture Diagrams | Design elements - Cloud ...
- Cloud round icons - Vector stencils library | Microsoft Azure ...