DES Network. Computer and Network Examples
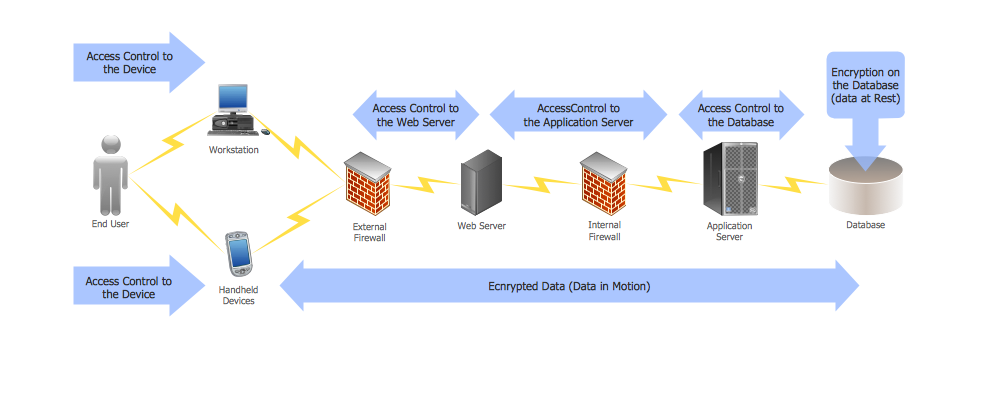
29095The Data Encryption Standard (DES) is a symmetric-key algorithm for the encryption of the electronic data. This diagram was created in ConceptDraw PRO using the Computer and Networks Area of ConceptDraw Solution Park and shows how the encryption and access control work together to secure data.
Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.Virtual private networks (VPN). Computer and Network Examples
A Virtual Private Network (VPN) is a network that allows the private networks at a remote location securely connect to the public Internet and provide access only to the intended recipients for transmitting data. VPN is built by creating the virtual point-to-point connection using the dedicated connections, traffic encryption or virtual tunneling protocols. This example was created in ConceptDraw PRO using the Computer and Networks Area of ConceptDraw Solution Park and shows the Virtual Private Network (VPN) diagram.
 Active Directory Diagrams
Active Directory Diagrams
Active Directory Diagrams solution significantly extends the capabilities of ConceptDraw PRO software with special Active Directory samples, convenient template and libraries of Active Directory vector stencils, common icons of sites and services, icons of LDPA elements, which were developed to help you in planning and modelling network structures and network topologies, in designing excellently looking Active Directory diagrams, Active Directory Structure diagrams, and Active Directory Services diagram, which are perfect way to visualize detailed structures of Microsoft Windows networks, Active Directory Domain topology, Active Directory Site topology, Organizational Units (OU), and Exchange Server organization.
Using Remote Networking Diagrams
Remote Networking - We explain the method most people use to connect to the Internet.
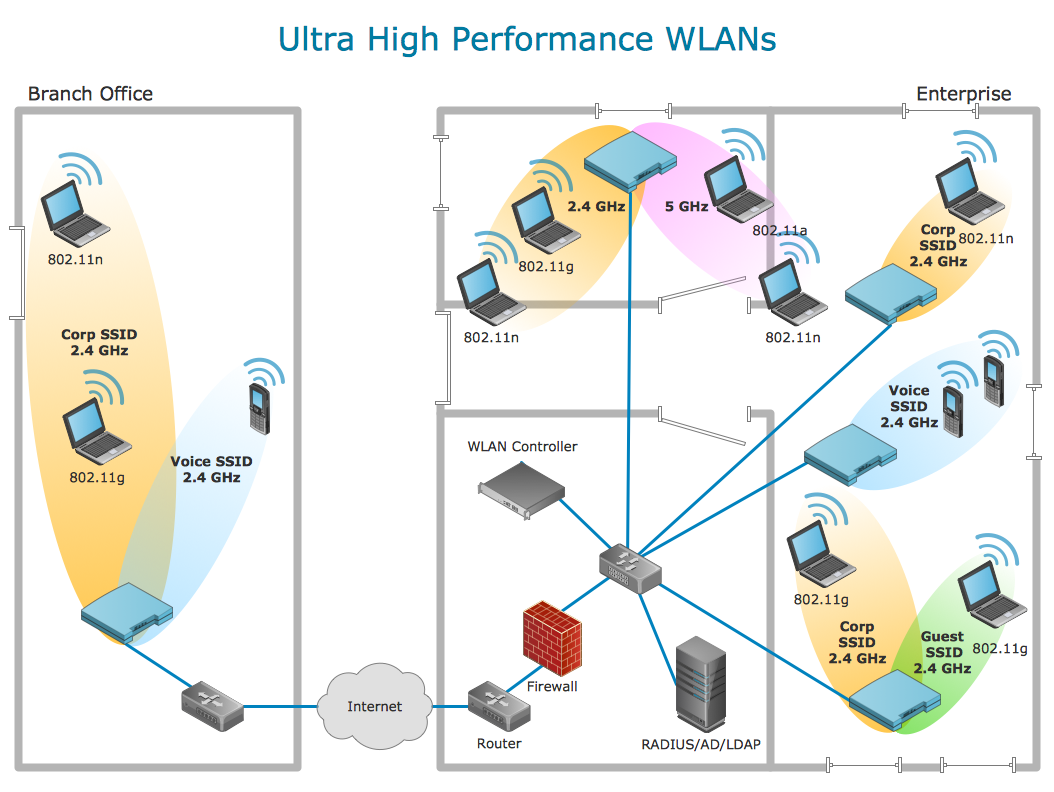
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw PRO software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
This computer security diagram example was designed on the base of the diagram from the website of the Centers for Disease Control and Prevention (CDC).
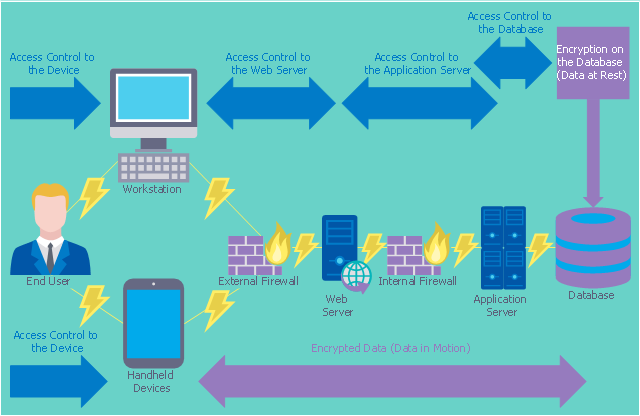
"Encryption and Cryptography
Encryption converts plain text into ciphertext, and decryption converts ciphertext back into plain text. Ciphertext looks like random characters, but is actually the result of the application of a key to the plain text. A key is usually a mathematical algorithm known only to the sender and the intended recipient of the message.
A cryptosystem is a system for encrypting and decrypting data. A strong cryptosystem has many possible keys, so a third party would be unlikely to find the correct key by trying all possible keys. A strong cryptosystem also produces ciphertext that appears random to all standard statistical tests and resists all known methods for breaking codes.
Access Control
Before implementing encryption, an organization needs to ensure access to the database is limited to authorized users. Access controls that should be addressed include rules for creating users, users’ privileges to access objects, and users’ permissions to perform commands and various tasks.
The following diagram illustrates how access control and encryption work together to secure data" [cdc.gov/ cancer/ npcr/ tools/ security/ encryption2.htm]
The cybersecurity diagram example "Access control and encryption " was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Encryption and Cryptography
Encryption converts plain text into ciphertext, and decryption converts ciphertext back into plain text. Ciphertext looks like random characters, but is actually the result of the application of a key to the plain text. A key is usually a mathematical algorithm known only to the sender and the intended recipient of the message.
A cryptosystem is a system for encrypting and decrypting data. A strong cryptosystem has many possible keys, so a third party would be unlikely to find the correct key by trying all possible keys. A strong cryptosystem also produces ciphertext that appears random to all standard statistical tests and resists all known methods for breaking codes.
Access Control
Before implementing encryption, an organization needs to ensure access to the database is limited to authorized users. Access controls that should be addressed include rules for creating users, users’ privileges to access objects, and users’ permissions to perform commands and various tasks.
The following diagram illustrates how access control and encryption work together to secure data" [cdc.gov/ cancer/ npcr/ tools/ security/ encryption2.htm]
The cybersecurity diagram example "Access control and encryption " was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
Network Security
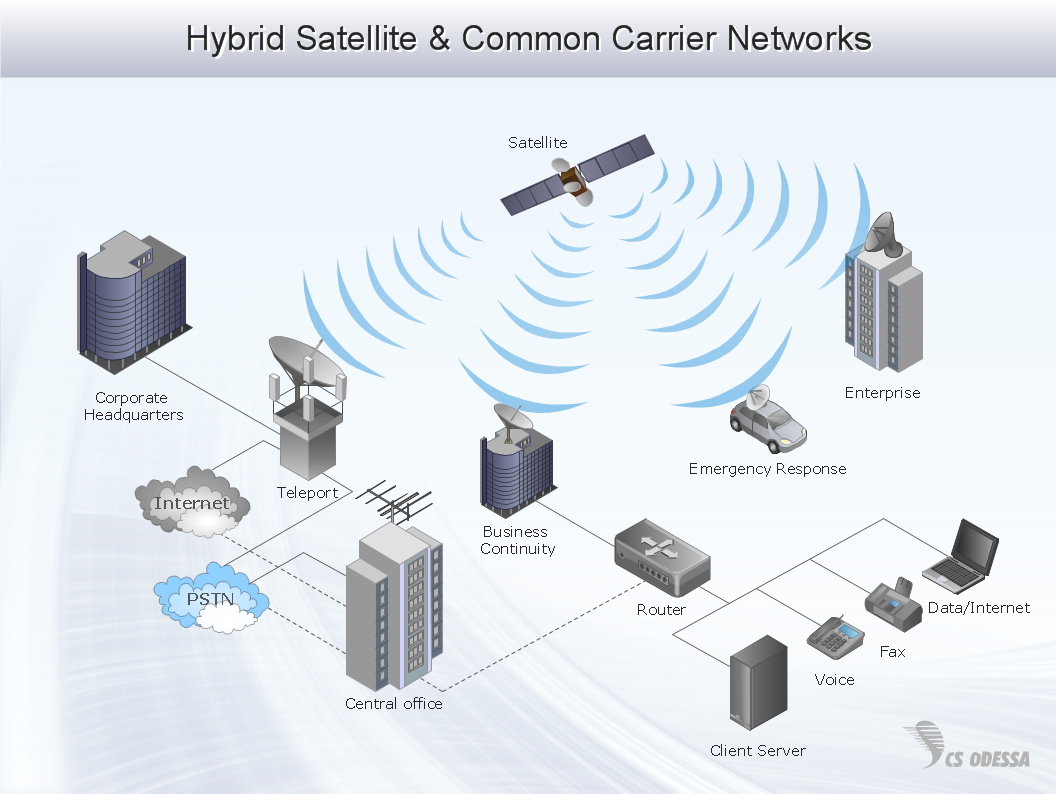
The Internet is a giant computer network which connects computers all over the world. It is integral part of human society and business. But the serious question for network engineers, designers, lawmakers and enforcers is the need for protect the Internet networks from the Internet crimes, hacking and attacks. There are quite a number of hardware, software and physical methods of protection against them. The samples you see on this page were created in ConceptDraw PRO using the tools of Network Security Diagrams Solution for ConceptDraw PRO software. They show protection networks with Firewalls and other network security devices.Network Diagram Software Enterprise Private Network
ConceptDraw - Perfect Network Diagramming Software with abundant examples and templates. ConceptDraw Network Diagram is ideal for network engineers and network designers who need to draw Enterprise Private Network diagrams.
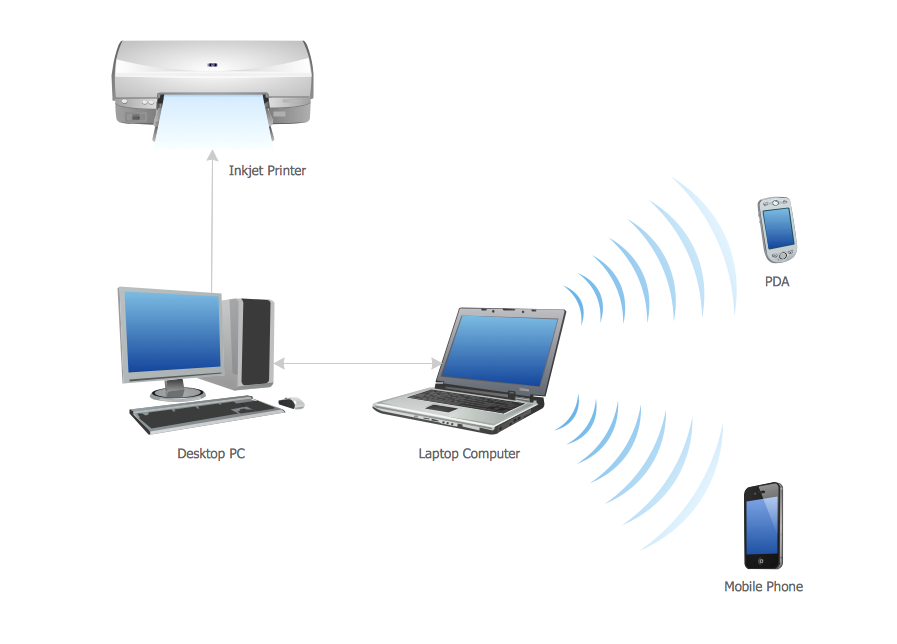
Personal area (PAN) networks. Computer and Network Examples
Personal area network (PAN) is a network organized on a limited area and used for data transmission between various personal devices, such as computers, tablets, laptops, telephones, different digital and mobile devices, etc. and also for connecting to higher level network and Internet. PAN is used to manage the interconnections of IT devices which surround a single user and generally contains such appliances, as cordless mice, keyboard, phone, and Bluetooth handsets. PANs can be wired with computer buses, or wirelessly connected to the Internet using such network technologies as Bluetooth, Z-Wave, ZigBee, IrDa, UWB, Body Area Network. PANs have a lot of pros and cons, they are expedient, lucrative and handy, but sometimes have bad connection with other networks on the same radio bands, Bluetooth has distance limits and slow data transfer speed, but is comparatively safe. ConceptDraw PRO diagramming software supplied with numerous solutions of Computer and Networks Area included to ConceptDraw Solution Park perfectly suits for designing the Personal Area Networks.
- Er Diagram For Image Encryption
- Active Directory diagram - Asymmetric encryption | Active Directory ...
- Network Diagram For Network Access Storage And Encryption
- UML Class Diagram Generalization Example UML Diagrams ...
- Examples Of Enterprise Private Network
- Access Control And Encryption
- Recommended network architecture for BlackBerry SWS | Firewall ...
- Computer Security Applications
- DES Network. Computer and Network Examples | Network ...
- How to Build Cloud Computing Diagram Principal Cloud ...