Network Security
The Internet is a giant computer network which connects computers all over the world. It is integral part of human society and business. But the serious question for network engineers, designers, lawmakers and enforcers is the need for protect the Internet networks from the Internet crimes, hacking and attacks. There are quite a number of hardware, software and physical methods of protection against them. The samples you see on this page were created in ConceptDraw DIAGRAM using the tools of Network Security Diagrams Solution for ConceptDraw DIAGRAM software. They show protection networks with Firewalls and other network security devices.Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw DIAGRAM software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
Cyber Security Degrees
For protection various cyber environments are developed and applied large variety of cyber security standards, techniques, security concepts and approaches with different cyber security degrees. The ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park offers the number of useful tools which will help network security engineers, cyber security specialists, network and computer analysts easily and visually depict the knowledge and skills for research and prevention of intrusions, about protection critical information and analysis of cyber incidents, and for how to assess threats and vulnerabilities.
 Computer and Networks Area
Computer and Networks Area
The solutions from Computer and Networks Area of ConceptDraw Solution Park collect samples, templates and vector stencils libraries for drawing computer and network diagrams, schemes and technical drawings.
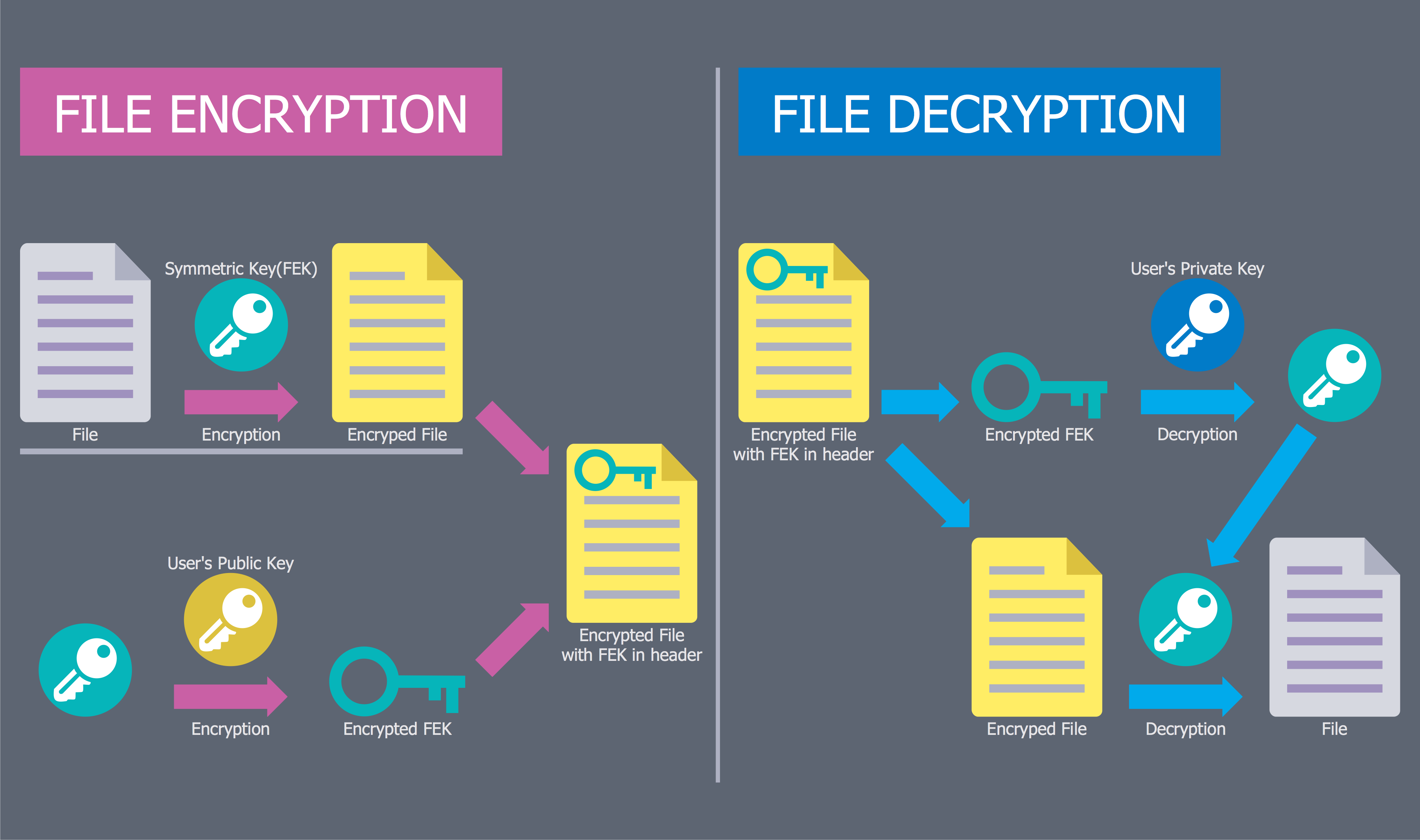
This computer security diagram example was designed on the base of the Wikimedia Commons file: Firewall.png.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
 Computer Network Diagrams
Computer Network Diagrams
Computer Network Diagrams solution extends ConceptDraw DIAGRAM software with samples, templates and libraries of vector icons and objects of computer network devices and network components to help you create professional-looking Computer Network Diagrams, to plan simple home networks and complex computer network configurations for large buildings, to represent their schemes in a comprehensible graphical view, to document computer networks configurations, to depict the interactions between network's components, the used protocols and topologies, to represent physical and logical network structures, to compare visually different topologies and to depict their combinations, to represent in details the network structure with help of schemes, to study and analyze the network configurations, to communicate effectively to engineers, stakeholders and end-users, to track network working and troubleshoot, if necessary.
The vector stencils library "Cybersecurity clipart" contains 197 computer security icons.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide. It includes controlling physical access to the hardware, as well as protecting against harm that may come via network access, data and code injection, and due to malpractice by operators, whether intentional, accidental, or due to them being tricked into deviating from secure procedures." [Computer security. Wikipedia]
The icon set example "Design elements - Cybersecurity clipart" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide. It includes controlling physical access to the hardware, as well as protecting against harm that may come via network access, data and code injection, and due to malpractice by operators, whether intentional, accidental, or due to them being tricked into deviating from secure procedures." [Computer security. Wikipedia]
The icon set example "Design elements - Cybersecurity clipart" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Network Security Diagram
ConceptDraw DIAGRAM diagramming and vector drawing software enhanced with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is the best for effective design professional, colorful and attractive Network Security Diagram of any complexity and degree of detailing.Network Glossary Definition
The network glossary contains a complete list of network, computer-related and technical terms in alphabetic order, explanations and definitions for them, among them there are words well known for you and also specific, rare-used, uncommon or newly introduced terms. This specialized glossary, also known as a vocabulary, is the best in its field and covers in details the various aspects of computer network technologies. This glossary was developed by specialists using the practical experience and many useful sources to help the ConceptDraw users in their work, you can read and learn it from the screen on-line or print, it can be also used as a perfect educational guide or tutorial. ConceptDraw DIAGRAM software extended with Computer and Networks solution is easy to draw various types of Network diagrams, Network topology diagrams, Computer networking schematics, Network maps, Cisco network topology, Computer network architecture, Wireless networks, Vehicular networks, Rack diagrams, Logical, Physical, Cable networks, etc. Desktop ConceptDraw DIAGRAM Software is a good Visio for Mac Os X replacement. It gives you rich productivity and quality of the produced diagrams.
Network Security Architecture Diagram
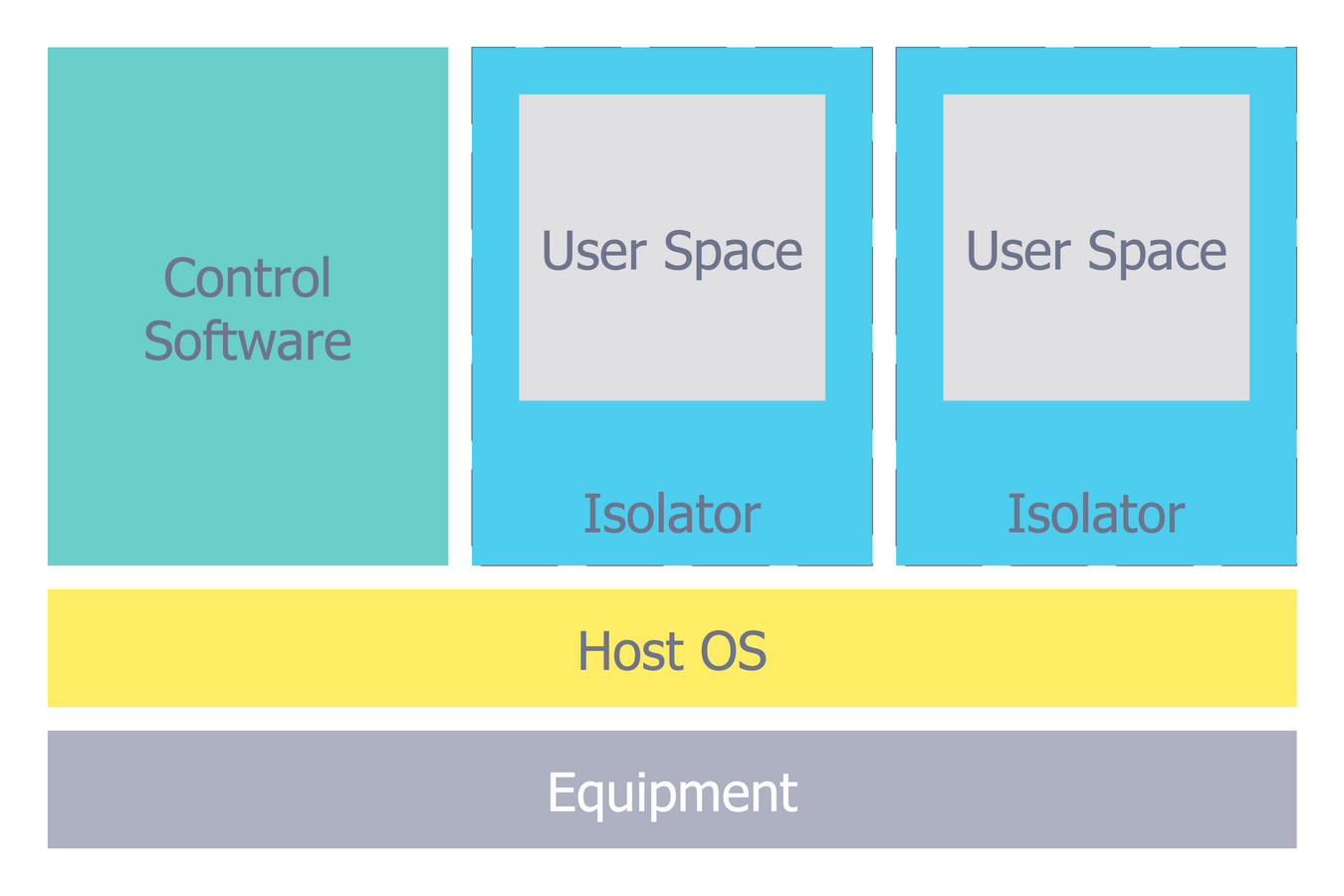
Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram? We recommend to use ConceptDraw DIAGRAM extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.This computer security diagram example was designed on the base of the Wikimedia Commons file: Diagramme ArchiIsolateur.png.
"Virtualization, architecture of an isolator."
[commons.wikimedia.org/ wiki/ File:Diagramme_ ArchiIsolateur.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, virtualization refers to the act of creating a virtual (rather than actual) version of something, including virtual computer hardware platforms, operating systems, storage devices, and computer network resources." [Virtualization. Wikipedia]
The cybersecurity diagram example "Isolator architecture" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
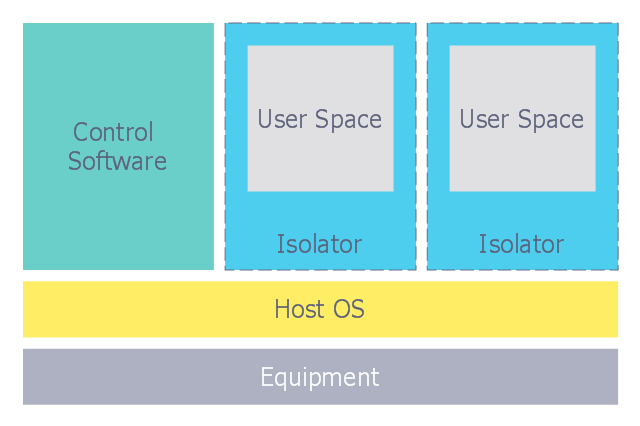
"Virtualization, architecture of an isolator."
[commons.wikimedia.org/ wiki/ File:Diagramme_ ArchiIsolateur.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, virtualization refers to the act of creating a virtual (rather than actual) version of something, including virtual computer hardware platforms, operating systems, storage devices, and computer network resources." [Virtualization. Wikipedia]
The cybersecurity diagram example "Isolator architecture" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
HelpDesk
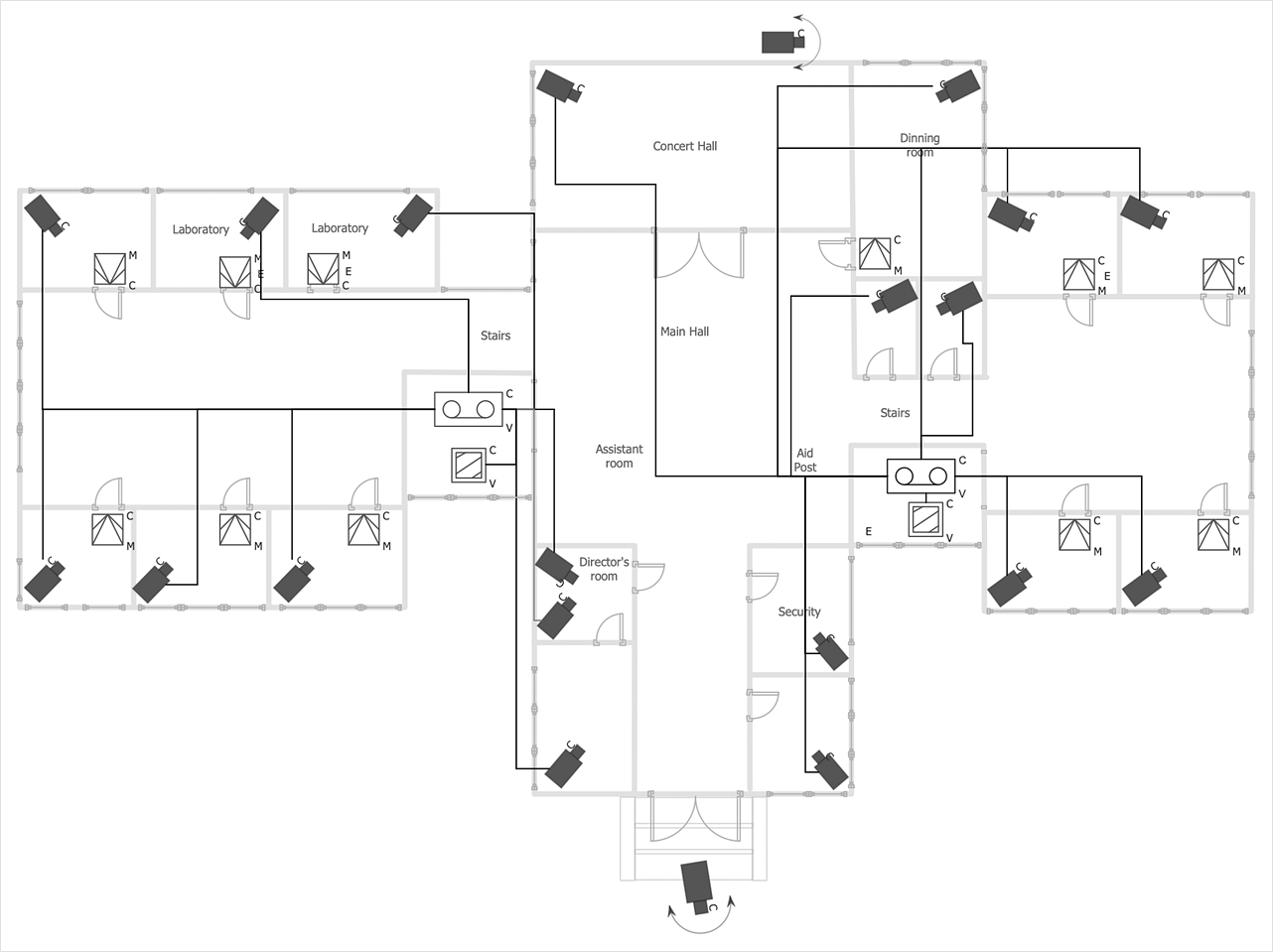
How to Create a CCTV Diagram
CCTV (Closed-circuit television) diagram is used to depict a system of video monitoring. The CCTV diagram provides video cameras placement strategy. CCTV diagram should include the scheme of strategic placement of video cameras, which capture and transmit videos to either a private network of monitors for real-time viewing or to a video recorder for later reference. CCTV is commonly used for surveillance and security purposes. Using ConceptDraw DIAGRAM with the Security and Access Plans Solution lets you create professional looking video surveillance CCTV system plans, security plans, and access schemes.- Internet symbols - Vector stencils library | | Network Security ...
- Security and Access Plans | How to Draw a Security and Access ...
- Computer Hardware And Software Examples
- Layout Of Network Hardware
- Design elements - Cybersecurity clipart | Cyber Security Degrees ...
- Cyber Security Degrees | 10 Steps to Cyber Security | Network ...
- Isolator architecture | Network Security Diagrams | Network Security ...
- Design elements - Cybersecurity connectors | Cyber Security ...
- How to Create a Network Security Diagram Using ConceptDraw PRO
- How to Draw a Computer Network Diagrams | Computer Network ...
- Diagram Of Firewall Computer
- Firewall between LAN and WAN | Network Security Diagrams ...
- Design elements - Cybersecurity round icons | Cyber Security ...
- Design elements - Cybersecurity shapes | Cyber Security Degrees ...
- How To Create Emergency Plans and Fire Evacuation | Design ...
- Security system plan
- Design elements - Initiation and annunciation | Network hardware ...
- Computer Network Diagrams | Network hardware - Vector stencils ...
- Hardware And Networking In Diagrams Format Pdf
- How to Create a Network Security Diagram Using ConceptDraw ...