Cisco Security. Cisco icons, shapes, stencils and symbols
The ConceptDraw vector stencils library "Cisco Security" contains 16 symbols of security devices and equipment for drawing the computer network diagrams using the ConceptDraw DIAGRAM diagramming and vector drawing software.Cisco Network Design. Cisco icons, shapes, stencils, symbols and design elements
Cisco is the largest company, which specializes in the field of high technologies, develops and sells network equipment mainly for the large organizations and telecommunication companies. Cisco produces wide variety of devices and equipment, such as routers, switches, gateways, servers, network security devices (firewalls, VPN, IDs, etc.), ATM switches, cable modems and DSL equipment, access points Wi-Fi, products for IP telephony, etc. The first commercially successful multi-protocol router, which enabled for previously incompatible computers to communicate between themselves, is also developed by Cisco company. Cisco is a generally accepted standard, which uses globally recognized Cisco icons for all produced Cisco equipment. ConceptDraw DIAGRAM software extended with Cisco Network Diagrams solution from Computer and Network area contains a lot of predesigned Cisco network design elements for professional drawing Cisco network diagrams, visualization computer network topologies, equipment connections and arrangement.The vector stencils library "Cybersecurity clipart" contains 197 computer security icons.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide. It includes controlling physical access to the hardware, as well as protecting against harm that may come via network access, data and code injection, and due to malpractice by operators, whether intentional, accidental, or due to them being tricked into deviating from secure procedures." [Computer security. Wikipedia]
The icon set example "Design elements - Cybersecurity clipart" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide. It includes controlling physical access to the hardware, as well as protecting against harm that may come via network access, data and code injection, and due to malpractice by operators, whether intentional, accidental, or due to them being tricked into deviating from secure procedures." [Computer security. Wikipedia]
The icon set example "Design elements - Cybersecurity clipart" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
The vector stencils library "Cybersecurity" contains 24 computer security icons. Use it to design your computer and telecom illustrations and infographics with ConceptDraw PRO diagramming and vector drawing software.
"Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide." [Computer security. Wikipedia]
The IT security icons example "Design elements - Cybersecurity" is included in the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
"Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide." [Computer security. Wikipedia]
The IT security icons example "Design elements - Cybersecurity" is included in the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
The vector stencils library "Cybersecurity" contains 24 computer security icons. Use it to design your computer and telecom illustrations and infographics with ConceptDraw PRO diagramming and vector drawing software.
"Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide." [Computer security. Wikipedia]
The IT security icons example "Design elements - Cybersecurity" is included in the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
"Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide." [Computer security. Wikipedia]
The IT security icons example "Design elements - Cybersecurity" is included in the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
The vector stencils library "Cybersecurity round icons" contains 150 network security diagram icons.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
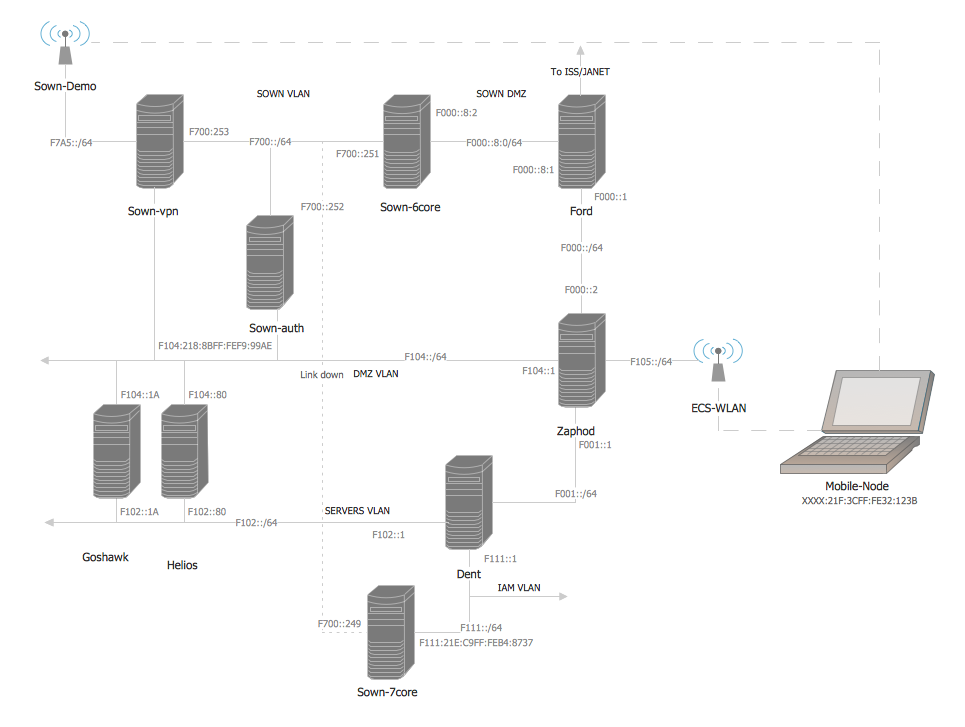
"A computer network diagram is a schematic depicting the nodes and connections amongst nodes in a computer network or, more generally, any telecommunications network. ...
Readily identifiable icons are used to depict common network appliances e.g. Router, and the style of lines between them indicate the type of connection. Clouds are used to represent networks external to the one pictured for the purposes of depicting connections between internal and external devices, without indicating the specifics of the outside network." [Computer network diagram. Wikipedia]
The pictograms example "Design elements - Cybersecurity round icons" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"A computer network diagram is a schematic depicting the nodes and connections amongst nodes in a computer network or, more generally, any telecommunications network. ...
Readily identifiable icons are used to depict common network appliances e.g. Router, and the style of lines between them indicate the type of connection. Clouds are used to represent networks external to the one pictured for the purposes of depicting connections between internal and external devices, without indicating the specifics of the outside network." [Computer network diagram. Wikipedia]
The pictograms example "Design elements - Cybersecurity round icons" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Cyber Security Degrees
For protection various cyber environments are developed and applied large variety of cyber security standards, techniques, security concepts and approaches with different cyber security degrees. The ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park offers the number of useful tools which will help network security engineers, cyber security specialists, network and computer analysts easily and visually depict the knowledge and skills for research and prevention of intrusions, about protection critical information and analysis of cyber incidents, and for how to assess threats and vulnerabilities.Cisco Routers. Cisco icons, shapes, stencils and symbols
Network infrastructure planning is a very important process in the network construction, and the share of time allocated to this within the scope of the entire project may reach 60-80%. A competent and thorough approach to planning contributes to the quick investment return, and also increases the reliability and flexibility of the final system, reducing the probability of additional costs related to the incorrect implementation. Any planning begins with an analysis of the business requirements to the final system. Basic network parameters, which should be assessed are the scalability, accessibility, cost, speed and safety. Speed and cost are often mistaken for the most important parameters, and the rest of the parameters aren't even remembered. This is not entirely correct. Initially, it is necessary to assess the business plans for the future, because sometimes it is more profitable to invest more money in the beginning. If the business is to develop, then, consequently, demands onCisco Telepresence. Cisco icons, shapes, stencils and symbols
The ConceptDraw vector stencils library Cisco Telepresence contains videoconference equipment symbols for drawing the computer network diagrams.Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.- | | Network Security Devices | Cyber Security Icon
- Cyber Icons Diagrams
- Design elements - Cybersecurity round icons | Network Security ...
- Computer Worms Diagram
- Computer security icons
- Network Security Diagrams | Cyber Security Degrees | Network ...
- Network Security Devices | Cyber Security Degrees | Network ...
- Flow Chart Of Computer Security
- Computer security icon set
- Network Security Devices | Network Security Diagrams | Cyber ...