Cyber Security Degrees
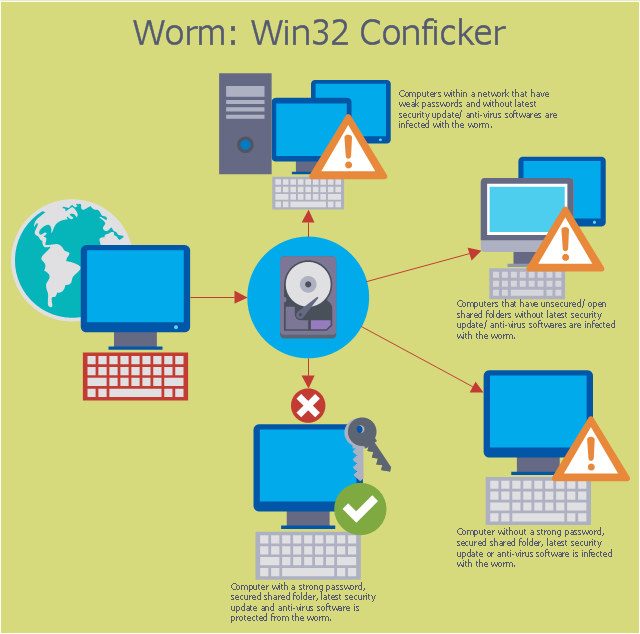
For protection various cyber environments are developed and applied large variety of cyber security standards, techniques, security concepts and approaches with different cyber security degrees. The ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park offers the number of useful tools which will help network security engineers, cyber security specialists, network and computer analysts easily and visually depict the knowledge and skills for research and prevention of intrusions, about protection critical information and analysis of cyber incidents, and for how to assess threats and vulnerabilities.This computer security diagram example was designed on the base of the Wikimedia Commons file: Conficker.svg. [commons.wikimedia.org/ wiki/ File:Conficker.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer." [Computer worm. Wikipedia]
The cybersecurity diagram example "Spread of Conficker worm" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer." [Computer worm. Wikipedia]
The cybersecurity diagram example "Spread of Conficker worm" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
Network Security Diagram
ConceptDraw DIAGRAM diagramming and vector drawing software enhanced with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is the best for effective design professional, colorful and attractive Network Security Diagram of any complexity and degree of detailing.
 Computer and Networks Area
Computer and Networks Area
The solutions from Computer and Networks Area of ConceptDraw Solution Park collect samples, templates and vector stencils libraries for drawing computer and network diagrams, schemes and technical drawings.
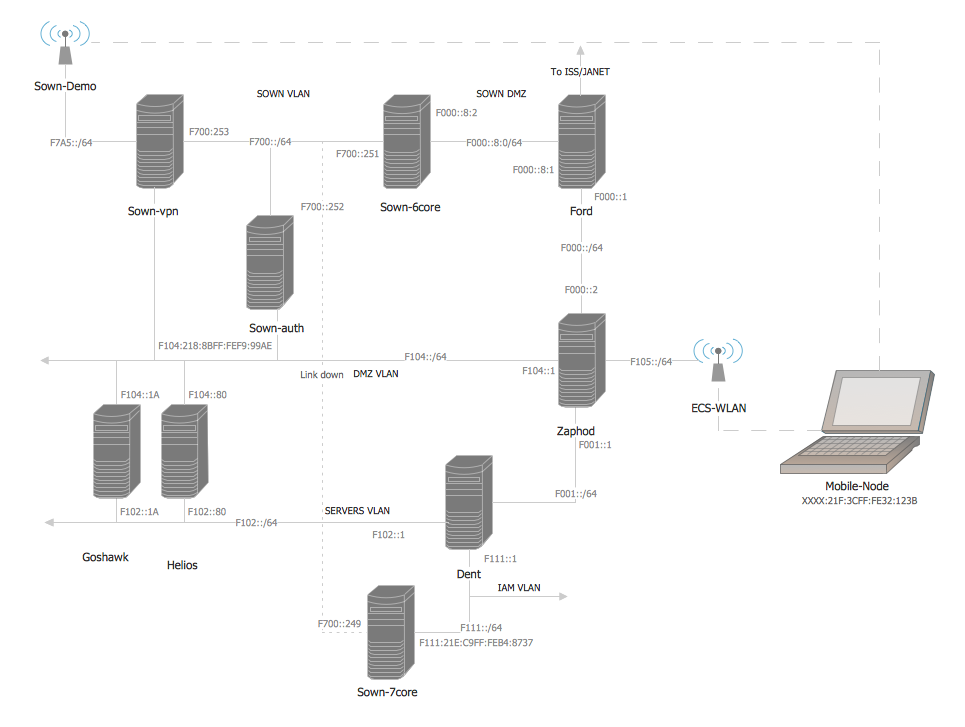
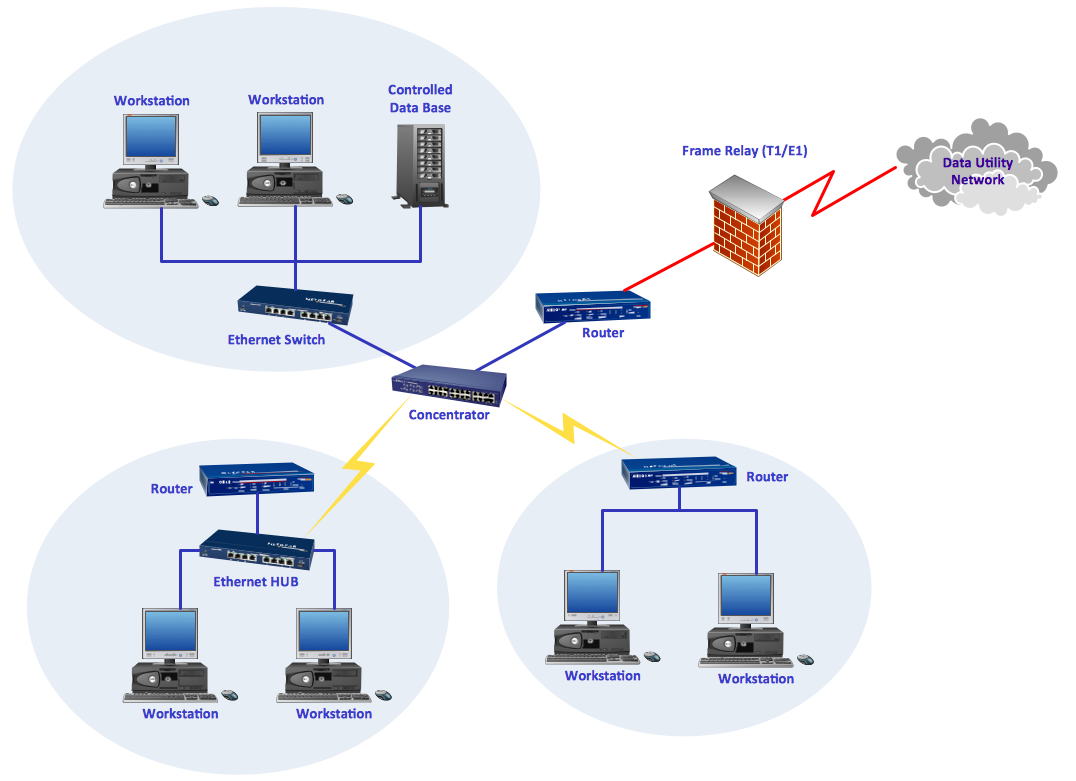
Network Security Architecture Diagram
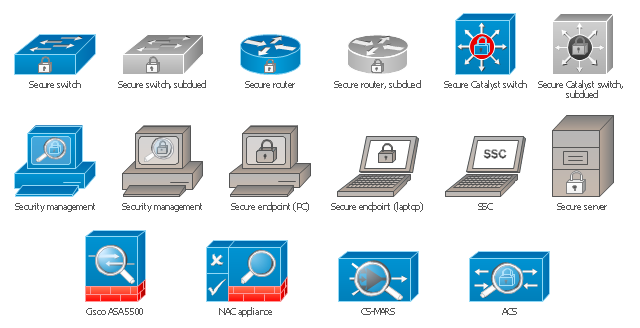
Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram? We recommend to use ConceptDraw DIAGRAM extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
Cisco Network Design. Cisco icons, shapes, stencils, symbols and design elements
Cisco is the largest company, which specializes in the field of high technologies, develops and sells network equipment mainly for the large organizations and telecommunication companies. Cisco produces wide variety of devices and equipment, such as routers, switches, gateways, servers, network security devices (firewalls, VPN, IDs, etc.), ATM switches, cable modems and DSL equipment, access points Wi-Fi, products for IP telephony, etc. The first commercially successful multi-protocol router, which enabled for previously incompatible computers to communicate between themselves, is also developed by Cisco company. Cisco is a generally accepted standard, which uses globally recognized Cisco icons for all produced Cisco equipment. ConceptDraw DIAGRAM software extended with Cisco Network Diagrams solution from Computer and Network area contains a lot of predesigned Cisco network design elements for professional drawing Cisco network diagrams, visualization computer network topologies, equipment connections and arrangement.The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
 ConceptDraw Solution Park
ConceptDraw Solution Park
ConceptDraw Solution Park collects graphic extensions, examples and learning materials
Cisco Switches and Hubs. Cisco icons, shapes, stencils and symbols
Cisco switches and hubs deliver the best performance, and often used as network solutions for small businesses, enterprises, data centers. Cisco switches are the core interconnect devices of each computer network. The numerous Cisco switches specifically designed for various applications. Network switches are separated for two types: fixed configuration and modular switches. The fixed configuration switches deprecate swapping or adding another module, and vice versa for modular switch.Network Topologies
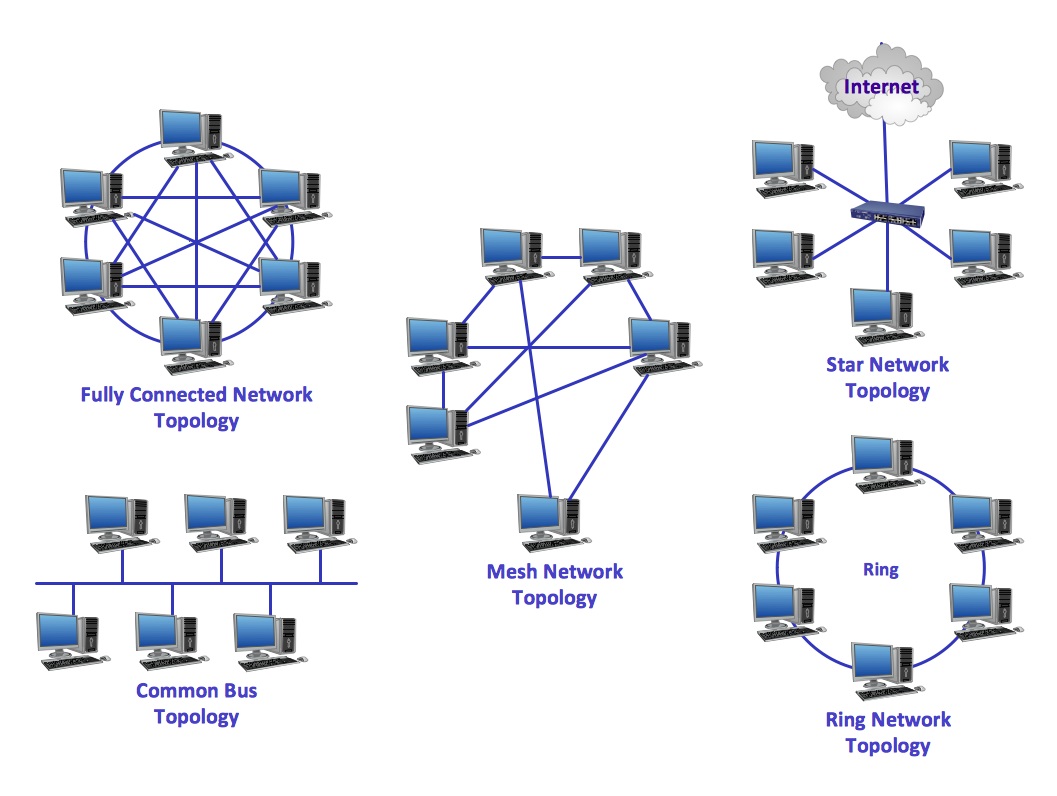
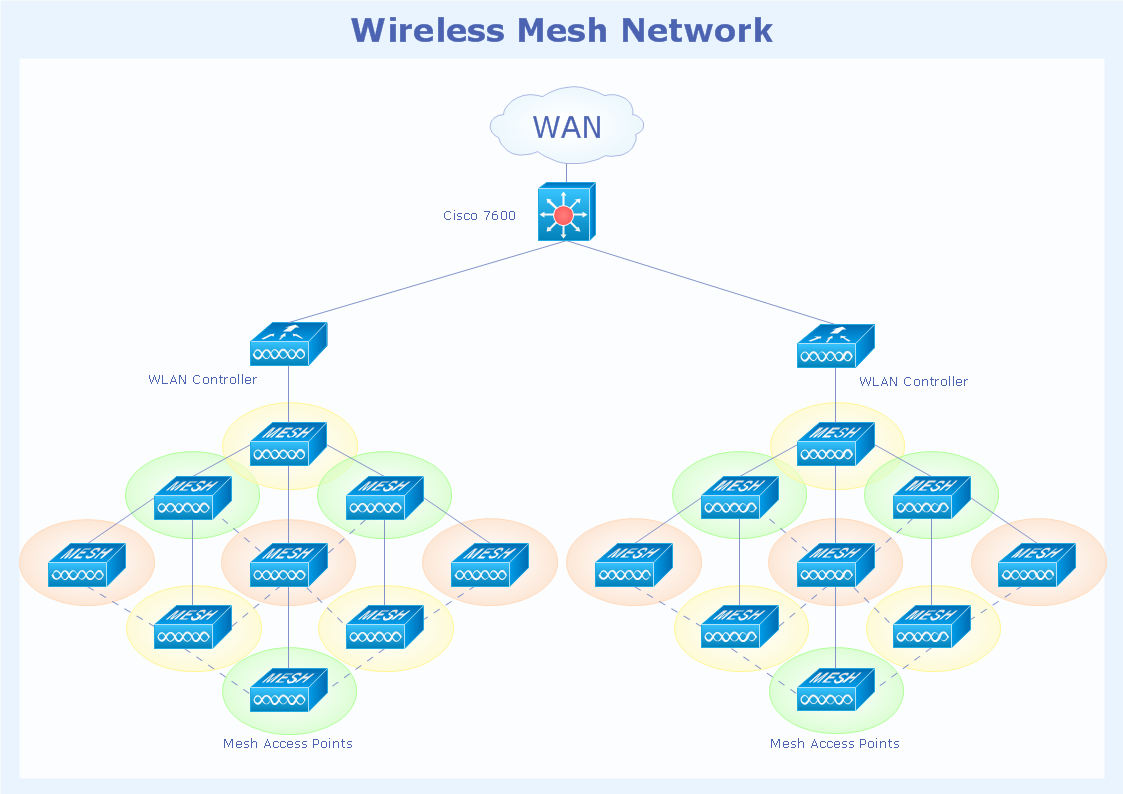
Network topology is a topological structure of computer network, which can be physical or logical. The physical topology depicts location of different computer network elements such as computers, cables and other devices. The logical topology visually displays network dataflows from one device to another. Sometimes network logical and physical topologies can be the same. ConceptDraw DIAGRAM diagramming and vector drawing software is powerful for drawing network maps and network topologies diagrams of any kinds and complexity thanks to the Computer Network Diagrams solution from the Computer and Networks area. ConceptDraw STORE proposes collection of network icons libraries and a lot of Network Topology Diagram examples, samples and templates which were created at ConceptDraw DIAGRAM software specially for Computer Network Diagrams solution. There are six basic types of the network topologies: Bus, Star, Ring, Mesh, Tree, Fully Connected. You can fast and easy design professional-looking diagram for each of them using the ConceptDraw DIAGRAM tools. There are plenty of web Visio-like diagramming software available. Web based diagrams software can be powerful, but sometimes it is essential to have desktop software. One of the most advanced diagrams tools like Visio for Mac OS is ConceptDraw DIAGRAM app.
ConceptDraw DIAGRAM Network Diagram Tool
Computer network diagrams visually depict the nodes of computer networks and connections between them. Diversity of Network Diagrams includes Wireless network diagrams, Network wiring diagrams, LAN network diagrams, Network WAN diagrams, Network topology diagrams, Network cable diagrams, Logical network diagrams, Network security diagrams, Diagram home network, Network physical diagrams, Activity network diagrams, and many others. To construct any of them it is useful to apply a special software with effective network diagramming tools. ConceptDraw DIAGRAM is ideal and powerful network diagram tool. It helps you diagram a network or create Computer network diagrams of various types using specialized and task-specific libraries of network components such as computers, hubs, switches, servers, routers, smart connectors, printers, mainframes, face plates, etc. that simulate network architectures, network design topologies and devices (all these shapes are parts of network diagram tool ConceptDraw DIAGRAM ).
Cisco Network Topology
Draw Cisco Network Topology and Cisco Computer Network Diagrams, Designs, Schematics, and Network Maps using ConceptDraw in no Time! Cisco Network Diagrams solution also provides 15 libraries of 508 Cisco symbols for network components and points, LAN and WAN, schematic and wiring drawings.Cloud Computing
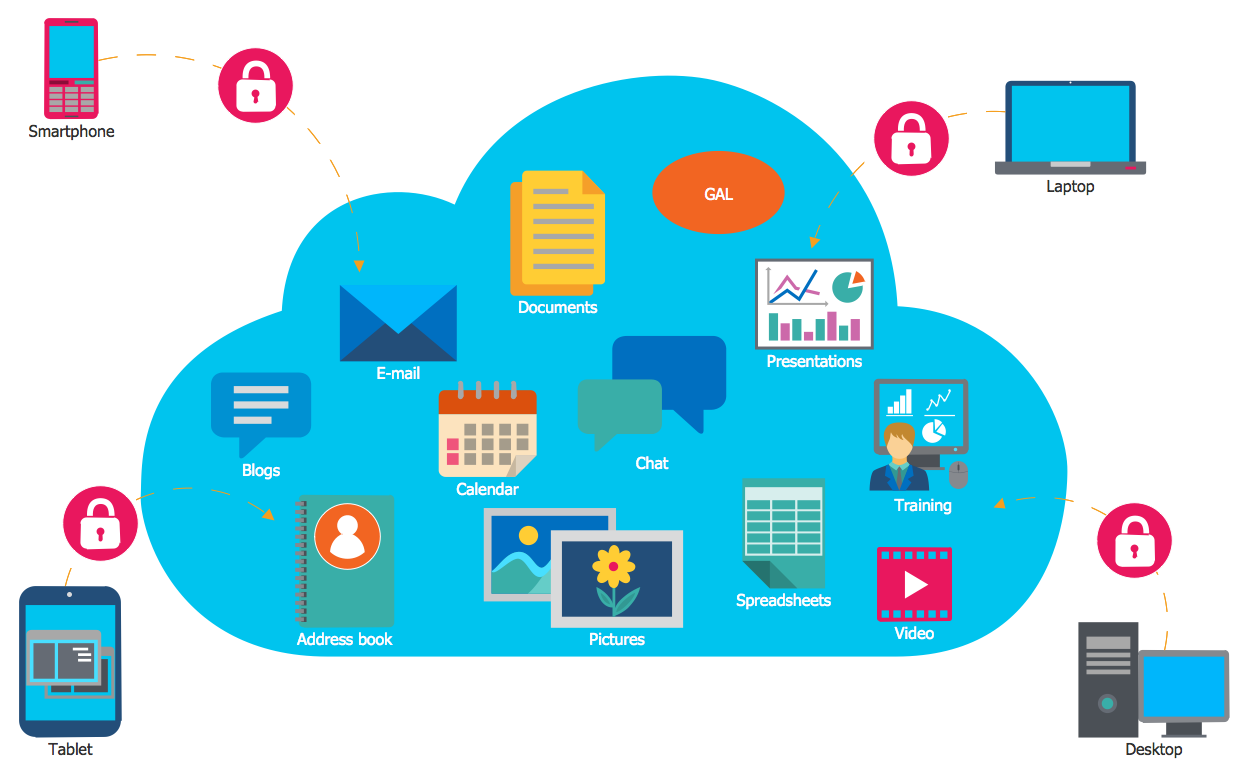
The Cloud Computing is the use of the software and hardware that includes the great number of computers connected over the communication network such as the Internet. The Cloud name comes from the usage the cloud symbol on the system diagrams as the abstraction for the complex network infrastructure. This term is used as a marketing metaphor for the Internet. This example was created in ConceptDraw DIAGRAM using the Computer and Networks Area of ConceptDraw Solution Park and shows the Cloud Computing.- Conceptdraw.com: Mind Map Software , Drawing Tools | Project ...
- Cyber Security Degrees | Network Security Devices | IT Security ...
- ConceptDraw PRO Network Diagram Tool | Network Security ...
- Network Security . Computer and Network Examples | Cisco security ...
- Security and Access Plans | How to Draw a Security and Access ...
- Spread of Conficker worm | Network Security Diagrams | Spread Of ...
- Security For Computer
- Project — Assigning Resources | Advanced Resource Assignment ...
- Cisco Security . Cisco icons, shapes, stencils and symbols | Cisco ...
- Security and Access Plans | Camera layout schematic | Camera ...
- Cisco Switches and Hubs. Cisco icons, shapes, stencils and ...
- Camera layout schematic | Marketing Diagrams | Computers and ...
- Network Security Devices | Cyber Security Degrees | Security and ...
- Cisco security - Vector stencils library
- Computer Hardware And Software Examples
- Network Diagramming Software for Design Cisco Network Diagrams ...
- Camera layout schematic | Security and Access Plans | Security ...
- Design elements - Office | Office - Design Elements | Cisco Security ...
- Cisco security - Vector stencils library | Cisco Security . Cisco icons ...
- Account Flowchart. Flowchart Examples | Budgeted appropriations ...






-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)