Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw PRO software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
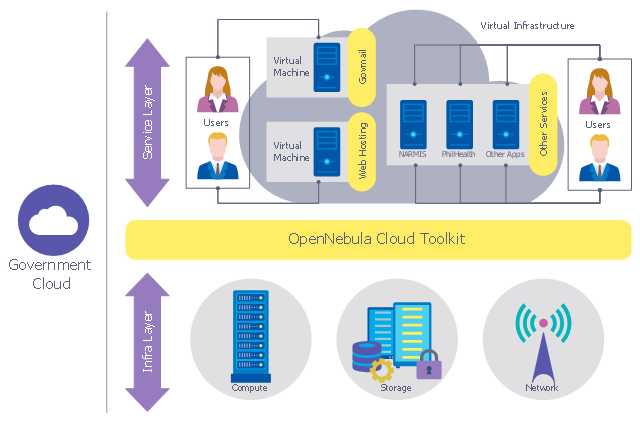
This example was designed on the base of the computer security diagram from the website of the Integrated Government Philippines (iGovPhil) Project.
"Department of Science and Technology (DOST) agencies, the Information and Communications Technology Office (DOST-ICTO) and the Advanced Science and Technology Institute (DOST-ASTI) are encouraging government institutions to adopt the use of cloud applications over traditional IT systems, as it unveiled a new online service called GovCloud or Government Cloud, which will enable government agencies to use secure online applications for their various computing requirements.
GovCloud was unveiled by Integrated Government Philippines (iGovPhil) Project at the start of a four-day celebration for Information and Communications Technology (ICT) Month 2013." [i.gov.ph/ govt-pushes-for-cloud-use-launches-govcloud/ ]
The cybersecurity diagram example "Government Cloud" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Department of Science and Technology (DOST) agencies, the Information and Communications Technology Office (DOST-ICTO) and the Advanced Science and Technology Institute (DOST-ASTI) are encouraging government institutions to adopt the use of cloud applications over traditional IT systems, as it unveiled a new online service called GovCloud or Government Cloud, which will enable government agencies to use secure online applications for their various computing requirements.
GovCloud was unveiled by Integrated Government Philippines (iGovPhil) Project at the start of a four-day celebration for Information and Communications Technology (ICT) Month 2013." [i.gov.ph/ govt-pushes-for-cloud-use-launches-govcloud/ ]
The cybersecurity diagram example "Government Cloud" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
 ConceptDraw Solution Park
ConceptDraw Solution Park
ConceptDraw Solution Park collects graphic extensions, examples and learning materials
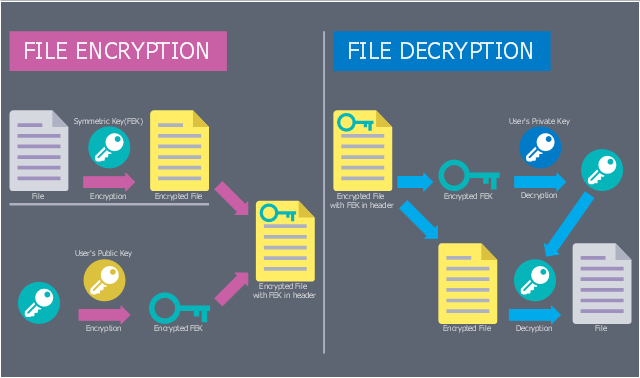
This computer security diagram example was designed on the base of Wikimedia Commons file: EFSOperation.svg.
"Flowchart for the operation of Encrypting File System (EFS)" [commons.wikimedia.org/ wiki/ File:EFSOperation.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"The Encrypting File System (EFS) on Microsoft Windows is a feature introduced in version 3.0 of NTFS that provides filesystem-level encryption. The technology enables files to be transparently encrypted to protect confidential data from attackers with physical access to the computer.
EFS is available in all versions of Windows developed for business environments from Windows 2000 onwards. By default, no files are encrypted, but encryption can be enabled by users on a per-file, per-directory, or per-drive basis. Some EFS settings can also be mandated via Group Policy in Windows domain environments." [Encrypting File System. Wikipedia]
The cybersecurity diagram example "EFS Operation" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Flowchart for the operation of Encrypting File System (EFS)" [commons.wikimedia.org/ wiki/ File:EFSOperation.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"The Encrypting File System (EFS) on Microsoft Windows is a feature introduced in version 3.0 of NTFS that provides filesystem-level encryption. The technology enables files to be transparently encrypted to protect confidential data from attackers with physical access to the computer.
EFS is available in all versions of Windows developed for business environments from Windows 2000 onwards. By default, no files are encrypted, but encryption can be enabled by users on a per-file, per-directory, or per-drive basis. Some EFS settings can also be mandated via Group Policy in Windows domain environments." [Encrypting File System. Wikipedia]
The cybersecurity diagram example "EFS Operation" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
 Computer and Networks Area
Computer and Networks Area
The solutions from Computer and Networks Area of ConceptDraw Solution Park collect samples, templates and vector stencils libraries for drawing computer and network diagrams, schemes and technical drawings.
 Cisco Network Diagrams
Cisco Network Diagrams
Cisco Network Diagrams solution extends ConceptDraw PRO with the best characteristics of network diagramming software. Included samples, templates and libraries of built-in standardized vector Cisco network icons and Cisco symbols of computers, network devices, network appliances and other Cisco network equipment will help network engineers, network designers, network and system administrators, as well as other IT professionals and corporate IT departments to diagram efficiently the network infrastructure, to visualize computer networks topologies, to design Cisco computer networks, and to create professional-looking Cisco Computer network diagrams, Cisco network designs and schematics, Network maps, and Network topology diagrams in minutes.
 Computers and Communications
Computers and Communications
Computers and communications solution extends ConceptDraw PRO software with illustration samples, templates and vector stencils libraries with clip art of computers, control devices, communications, technology, Apple machines.
 Project Exchange
Project Exchange
This solution extends ConceptDraw PROJECT and ConceptDraw MINDMAP software with the ability to import and export project data.
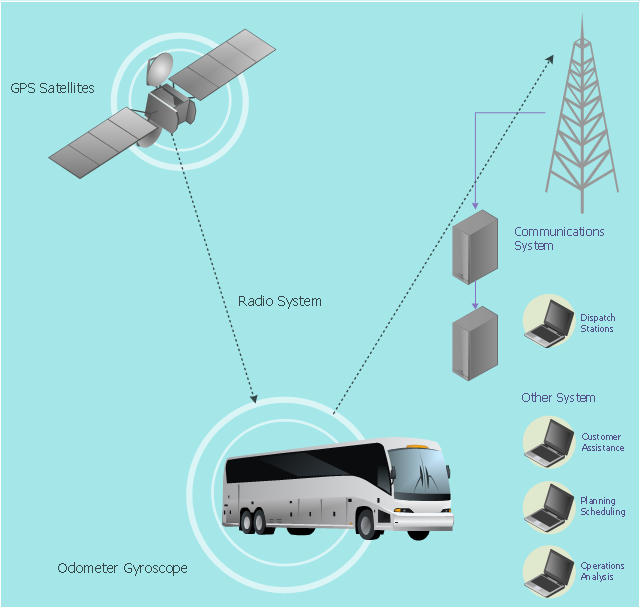
This vehicular network diagram example was drawn on the base of picture illustrating the article "Automatic Vehicle Location: Rural Transit" from the website of the Research and Innovative Technology Administration (RITA), U.S. Department of Transportation (US DOT).
"Automatic Vehicle Location (AVL) systems calculate the real-time location of any vehicle equipped with a Global Positioning Satellite (GPS) receiver. Data are then transmitted to the transit center with use of radio or cellular communications and can be used immediately for daily operations as well as archived for further analysis.
As a stand-alone technology, an AVL system can be used to monitor on-time performance. When combined with other technologies, AVL can deliver many benefits in the areas of fleet management, service planning, safety and security, traveler information, fare payment, vehicle component monitoring, and data collection. Since the greatest benefits from AVL are achieved by combining it with other Intelligent Transportation System (ITS) technologies, AVL is most appropriate for large rural agencies with more than 30 vehicles that plan to implement a comprehensive ITS."
[pcb.its.dot.gov/ factsheets/ avl/ avlRural_ overview.asp]
The vehicular network diagram example "Automatic vehicle location" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Vehicular Networking solution from the Computer and Networks area of ConceptDraw Solution Park.
"Automatic Vehicle Location (AVL) systems calculate the real-time location of any vehicle equipped with a Global Positioning Satellite (GPS) receiver. Data are then transmitted to the transit center with use of radio or cellular communications and can be used immediately for daily operations as well as archived for further analysis.
As a stand-alone technology, an AVL system can be used to monitor on-time performance. When combined with other technologies, AVL can deliver many benefits in the areas of fleet management, service planning, safety and security, traveler information, fare payment, vehicle component monitoring, and data collection. Since the greatest benefits from AVL are achieved by combining it with other Intelligent Transportation System (ITS) technologies, AVL is most appropriate for large rural agencies with more than 30 vehicles that plan to implement a comprehensive ITS."
[pcb.its.dot.gov/ factsheets/ avl/ avlRural_ overview.asp]
The vehicular network diagram example "Automatic vehicle location" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Vehicular Networking solution from the Computer and Networks area of ConceptDraw Solution Park.
Used Solutions
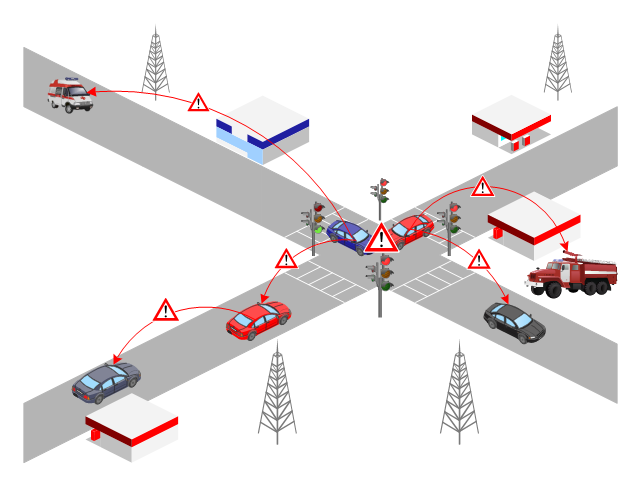
This VANET diagram example was drawn on the base of picture from the webpage "Security and Privacy in Location-based MANETs/ VANETs" from the Donald Bren School of Information and Computer Sciences, the University of California, Irvine. [ics.uci.edu/ ~keldefra/ manet.htm]
"A vehicular ad hoc network (VANET) uses cars as mobile nodes in a MANET to create a mobile network. A VANET turns every participating car into a wireless router or node, allowing cars approximately 100 to 300 metres of each other to connect and, in turn, create a network with a wide range. As cars fall out of the signal range and drop out of the network, other cars can join in, connecting vehicles to one another so that a mobile Internet is created. It is estimated that the first systems that will integrate this technology are police and fire vehicles to communicate with each other for safety purposes. Automotive companies like General Motors, Toyota, Nissan, DaimlerChrysler, BMW and Ford promote this term." [Vehicular ad hoc network. Wikipedia]
The VANET diagram example "Vehicular ad-hoc network" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Vehicular Networking solution from the Computer and Networks area of ConceptDraw Solution Park.
"A vehicular ad hoc network (VANET) uses cars as mobile nodes in a MANET to create a mobile network. A VANET turns every participating car into a wireless router or node, allowing cars approximately 100 to 300 metres of each other to connect and, in turn, create a network with a wide range. As cars fall out of the signal range and drop out of the network, other cars can join in, connecting vehicles to one another so that a mobile Internet is created. It is estimated that the first systems that will integrate this technology are police and fire vehicles to communicate with each other for safety purposes. Automotive companies like General Motors, Toyota, Nissan, DaimlerChrysler, BMW and Ford promote this term." [Vehicular ad hoc network. Wikipedia]
The VANET diagram example "Vehicular ad-hoc network" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Vehicular Networking solution from the Computer and Networks area of ConceptDraw Solution Park.
Used Solutions
Maps
>
- Camera layout schematic | Marketing Diagrams | Computers and ...
- Cyber Security Degrees | Network Security Devices | IT Security ...
- Conceptdraw.com: Mind Map Software, Drawing Tools | Project ...
- Technology - Vector stencils library | Telecommunication networks ...
- Government Cloud | Network Security Diagrams | Network Security ...
- Design elements - Office | Office - Design Elements | Cisco Security ...
- Network Security Diagrams | Network Security Devices ...
- Personal area (PAN) networks. Computer and Network Examples ...
- ATM UML Diagrams | Security and Access Plans | Computer ...
- Apple machines - Vector stencils library | Computers - Vector ...
- Information Technology Architecture | Manufacturing 8 Ms fishbone ...
- Internet symbols - Vector stencils library | Access and security ...
- EFS Operation | Network Security Diagrams | Network Security ...
- Cyber Security Degrees | | Network Security Devices | Cyber ...
- Health IT dashboard | EPC IT Solutions | NIH IT enterprise ...
- Internet symbols - Vector stencils library | | Network Security ...
- ConceptDraw Arrows10 Technology | Flow chart Example ...
- Cloud Solutions Technology
- Camera layout schematic | Security and Access Plans | Security ...
- Fishbone Diagrams | Safety and Security | Seven Basic Tools of ...