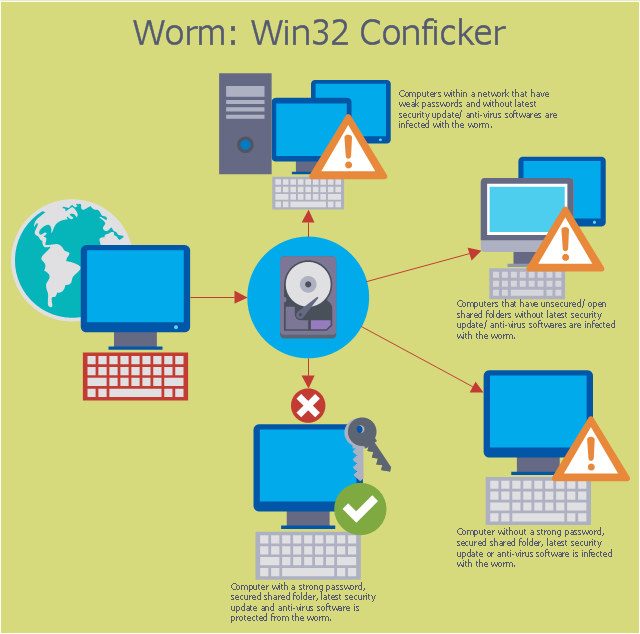
This computer security diagram example was designed on the base of the Wikimedia Commons file: Conficker.svg. [commons.wikimedia.org/ wiki/ File:Conficker.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer." [Computer worm. Wikipedia]
The cybersecurity diagram example "Spread of Conficker worm" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer." [Computer worm. Wikipedia]
The cybersecurity diagram example "Spread of Conficker worm" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
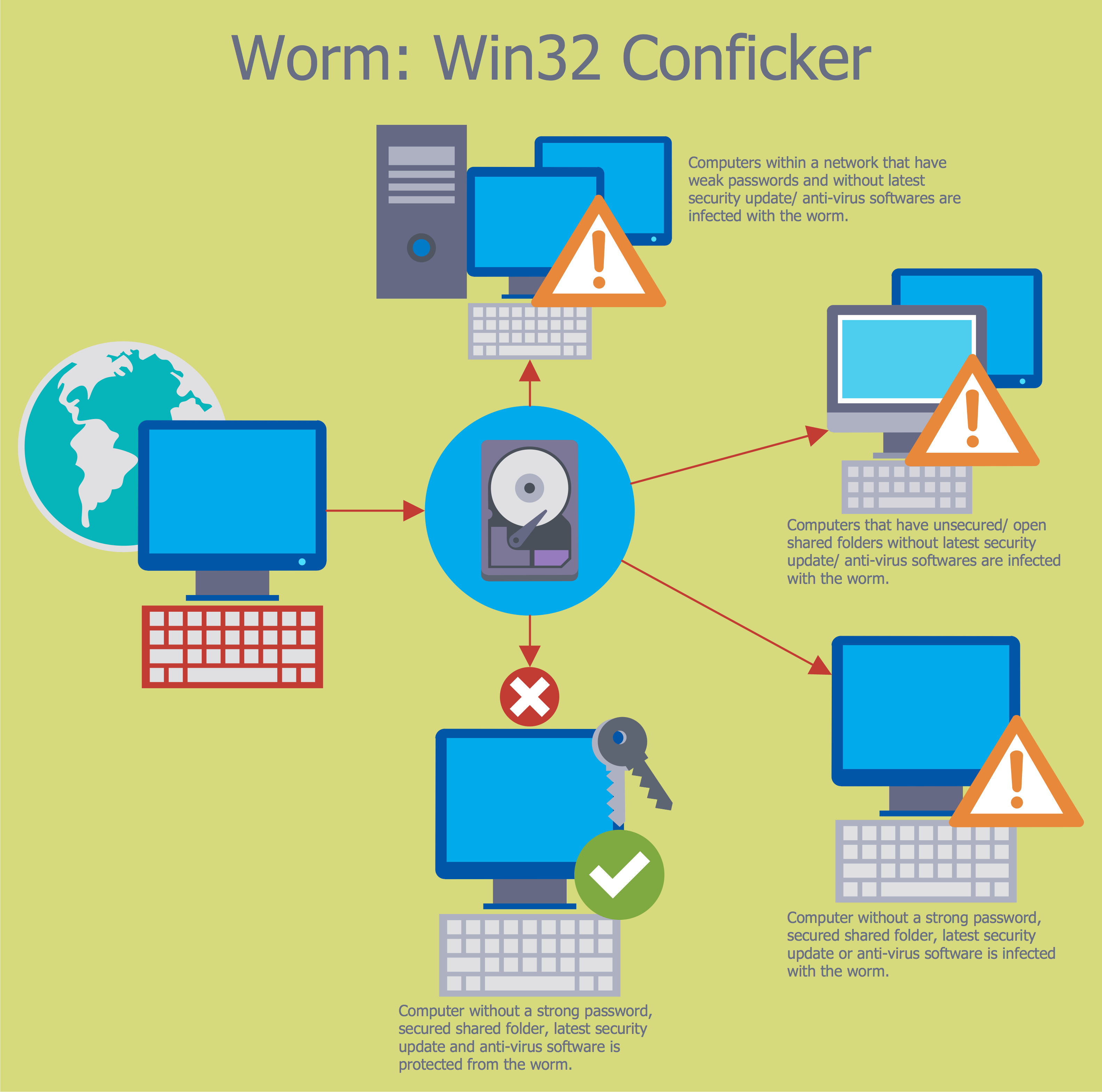
This computer security diagram example was designed on the base of the Wikimedia Commons file: Conficker.svg. [commons.wikimedia.org/ wiki/ File:Conficker.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer." [Computer worm. Wikipedia]
The cybersecurity diagram example "Spread of Conficker worm" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer." [Computer worm. Wikipedia]
The cybersecurity diagram example "Spread of Conficker worm" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
The vector stencils library "Cybersecurity round icons" contains 150 network security diagram icons.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"A computer network diagram is a schematic depicting the nodes and connections amongst nodes in a computer network or, more generally, any telecommunications network. ...
Readily identifiable icons are used to depict common network appliances e.g. Router, and the style of lines between them indicate the type of connection. Clouds are used to represent networks external to the one pictured for the purposes of depicting connections between internal and external devices, without indicating the specifics of the outside network." [Computer network diagram. Wikipedia]
The pictograms example "Design elements - Cybersecurity round icons" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"A computer network diagram is a schematic depicting the nodes and connections amongst nodes in a computer network or, more generally, any telecommunications network. ...
Readily identifiable icons are used to depict common network appliances e.g. Router, and the style of lines between them indicate the type of connection. Clouds are used to represent networks external to the one pictured for the purposes of depicting connections between internal and external devices, without indicating the specifics of the outside network." [Computer network diagram. Wikipedia]
The pictograms example "Design elements - Cybersecurity round icons" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
The vector stencils library "Cybersecurity clipart" contains 197 computer security icons.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide. It includes controlling physical access to the hardware, as well as protecting against harm that may come via network access, data and code injection, and due to malpractice by operators, whether intentional, accidental, or due to them being tricked into deviating from secure procedures." [Computer security. Wikipedia]
The icon set example "Design elements - Cybersecurity clipart" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide. It includes controlling physical access to the hardware, as well as protecting against harm that may come via network access, data and code injection, and due to malpractice by operators, whether intentional, accidental, or due to them being tricked into deviating from secure procedures." [Computer security. Wikipedia]
The icon set example "Design elements - Cybersecurity clipart" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Network Security Tips
The Internet is a huge world with unlimited possibilities. But with all its numerous advantages, the Internet also conceals many dangers and security threats, that's why we advise you to follow simple network security tips. ConceptDraw PRO diagramming and vector drawing software supplied with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is an ideal software for easy designing Network Security Diagrams and attractive illustrations with effective network security tips.- Spread of Conficker worm | Network Security Diagrams | Spread Of ...
- Diagrams Of Computer Monitor
- Computer Security Diagrams
- Basic computer network diagram
- Network Security Diagrams | Network Security | How to Create a ...
- Cyber Security Degrees | Design elements - Cybersecurity clipart ...
- What Are Diagrams Used For In Cyber Security
- Diagram Of A Desk Top Computer
- Network Security Diagrams | Cyber Security Degrees | Network ...
- Network Diagrams for Bandwidth Management | UML Class ...
- Network Diagrams for Bandwidth Management | Cisco Intelligent ...
- In searching of alternative to MS Visio for MAC and PC with ...
- Computer security diagram
- Network Security Diagram | Recommended network architecture for ...
- Computer network - Vector stencils library | In searching of ...
- Computer network - Vector stencils library | Computer network ...
- Firewall between LAN and WAN | Australia Map | Tree and Forest ...
- Design elements - Cybersecurity round icons | Cyber Security ...
- Pc Monitor
- Monitor Diagram