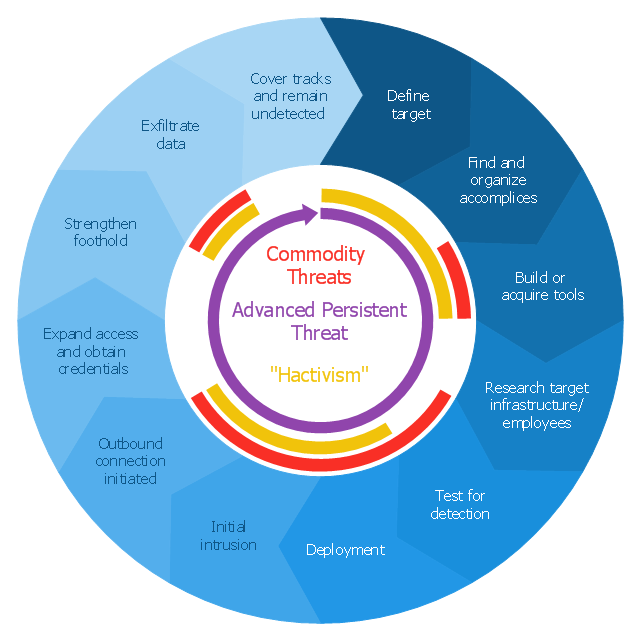
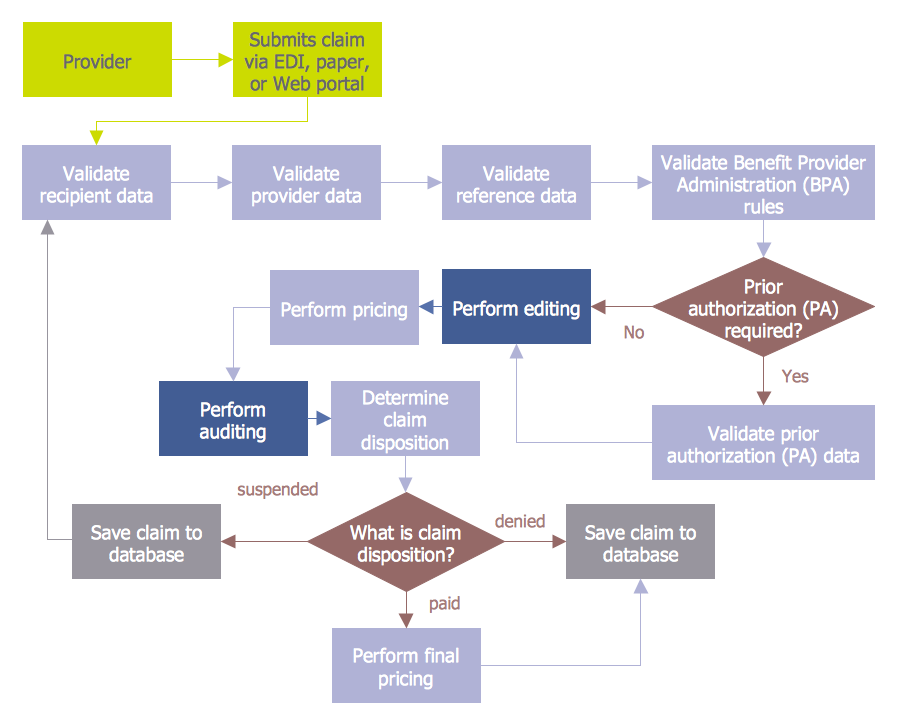
This circular arrows diagram sample shows advanced persistent threat lifecycle.
It was designed on the base of the Wikimedia Commons file: Advanced persistent threat lifecycle.jpg.
[commons.wikimedia.org/ wiki/ File:Advanced_ persistent_ threat_ lifecycle.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Advanced Persistent Threat (APT) APT is a set of stealthy and continuous hacking processes often orchestrated by human targeting a specific entity. APT usually targets organizations and or nations for business or political motives. APT processes require high degree of covertness over a long period of time. As the name implies, APT consists of three major components/ processes: advanced, persistent, and threat. The advanced process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The persistent process suggests that an external command and control is continuously monitoring and extracting data off a specific target. The threat process indicates human involvement in orchestrating the attack.
APT usually refers to a group, such as a government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack. Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target." [Advanced persistent threat. Wikipedia]
The arrow donut chart example
"Advanced persistent threat lifecycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
It was designed on the base of the Wikimedia Commons file: Advanced persistent threat lifecycle.jpg.
[commons.wikimedia.org/ wiki/ File:Advanced_ persistent_ threat_ lifecycle.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Advanced Persistent Threat (APT) APT is a set of stealthy and continuous hacking processes often orchestrated by human targeting a specific entity. APT usually targets organizations and or nations for business or political motives. APT processes require high degree of covertness over a long period of time. As the name implies, APT consists of three major components/ processes: advanced, persistent, and threat. The advanced process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The persistent process suggests that an external command and control is continuously monitoring and extracting data off a specific target. The threat process indicates human involvement in orchestrating the attack.
APT usually refers to a group, such as a government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack. Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target." [Advanced persistent threat. Wikipedia]
The arrow donut chart example
"Advanced persistent threat lifecycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
Flowchart design. Flowchart symbols, shapes, stencils and icons
A flowchart is a type of diagram which represents an algorithm, process or workflow, displays the steps as boxes of various kinds and depicts their order by connecting them with arrows. Any business graphic document will be more colorful and understandable if will use professional-looking and visual diagrams and flowcharts. Flowchart design gives versatile presenting and explaining of the process. ConceptDraw DIAGRAM flowchart software enhanced with Flowcharts solution helps effectively make Flowchart Design. Use of predesigned flowchart symbols and bright color palette offers a fresh view and favorably distinguishes the flowcharts designed in ConceptDraw DIAGRAM from the black and white flowcharts on a paper. Preferably to use no more than three or four colors and apply identical for the same shape types. The best flowchart design can be achieved by starting with Flowchart template, or any of suitable ready examples or samples offered in ConceptDraw STORE, open one of them and enter the proper text into each Flowchart shape. Each symbol of the flowchart has a definition that can't be changed. This means that all flowcharts shapes can be grouped in according to their meaning. Users with ConceptDraw DIAGRAM flowchart software can style groups of symbols with close definitions by color sets chosen from complementary palette. Almost all workflows can be depicted as a flowchart. Colored diagrams are more light for perception of the certain information, this is part of flowchart design. Bright colors need to be used in the key points of Decision symbols, to focus attention on their importance for whole process flow.
Block Diagram Software
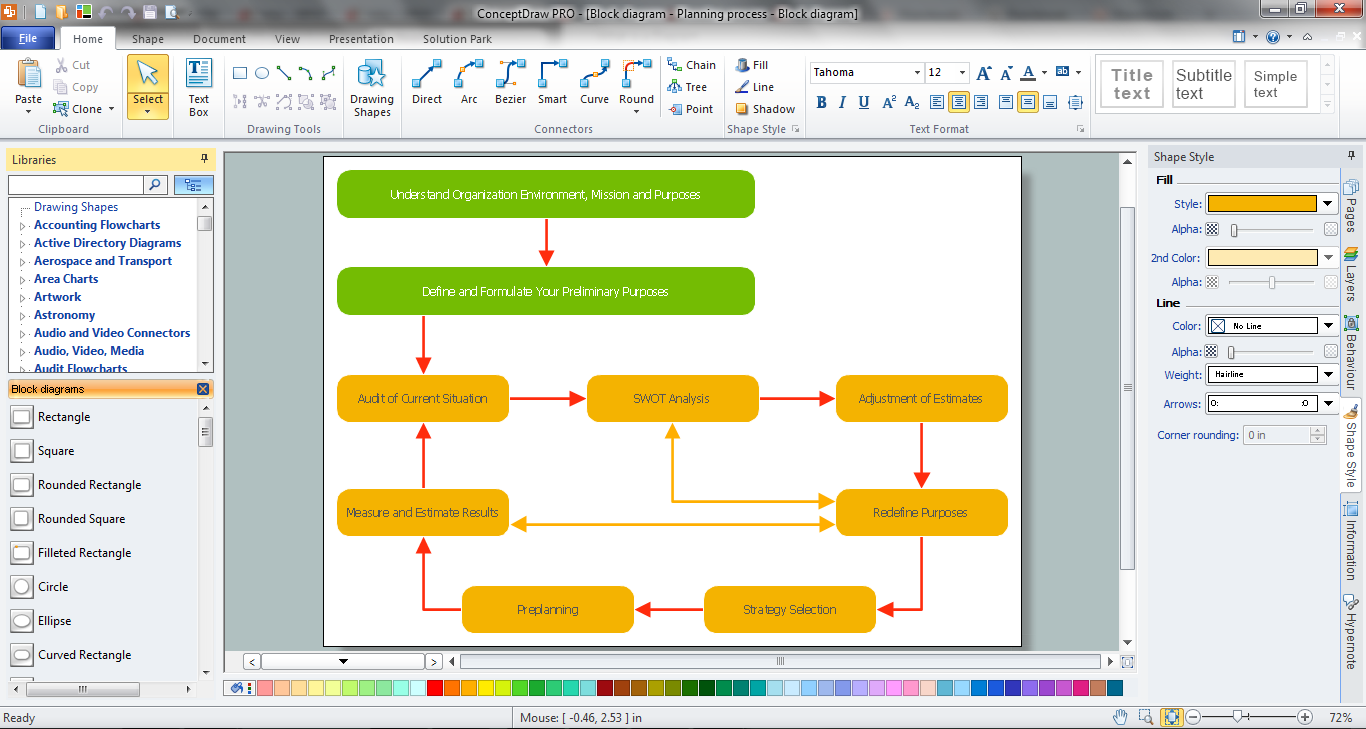
The popularity of Block Diagrams grows day by day. The existence of powerful software for their design is an excellent news! ConceptDraw DIAGRAM Block Diagram Software offers the Block Diagrams Solution from the "Diagrams" Area.Think and act effectively
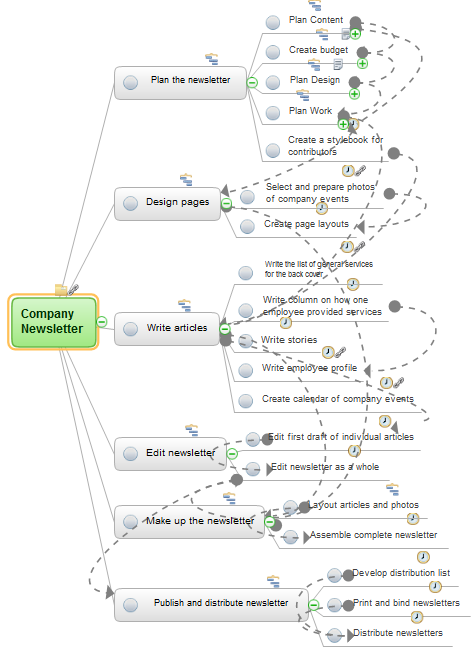
Many people who use mind mapping software for personal organizing find ConceptDraw MINDMAP sufficiently useful mind mapping tool in their business and daily life. Especially many positive responses receive ConceptDraw MINDMAP as cross platform tool to mind maps for Macintosh and Windows.Audit Procedures
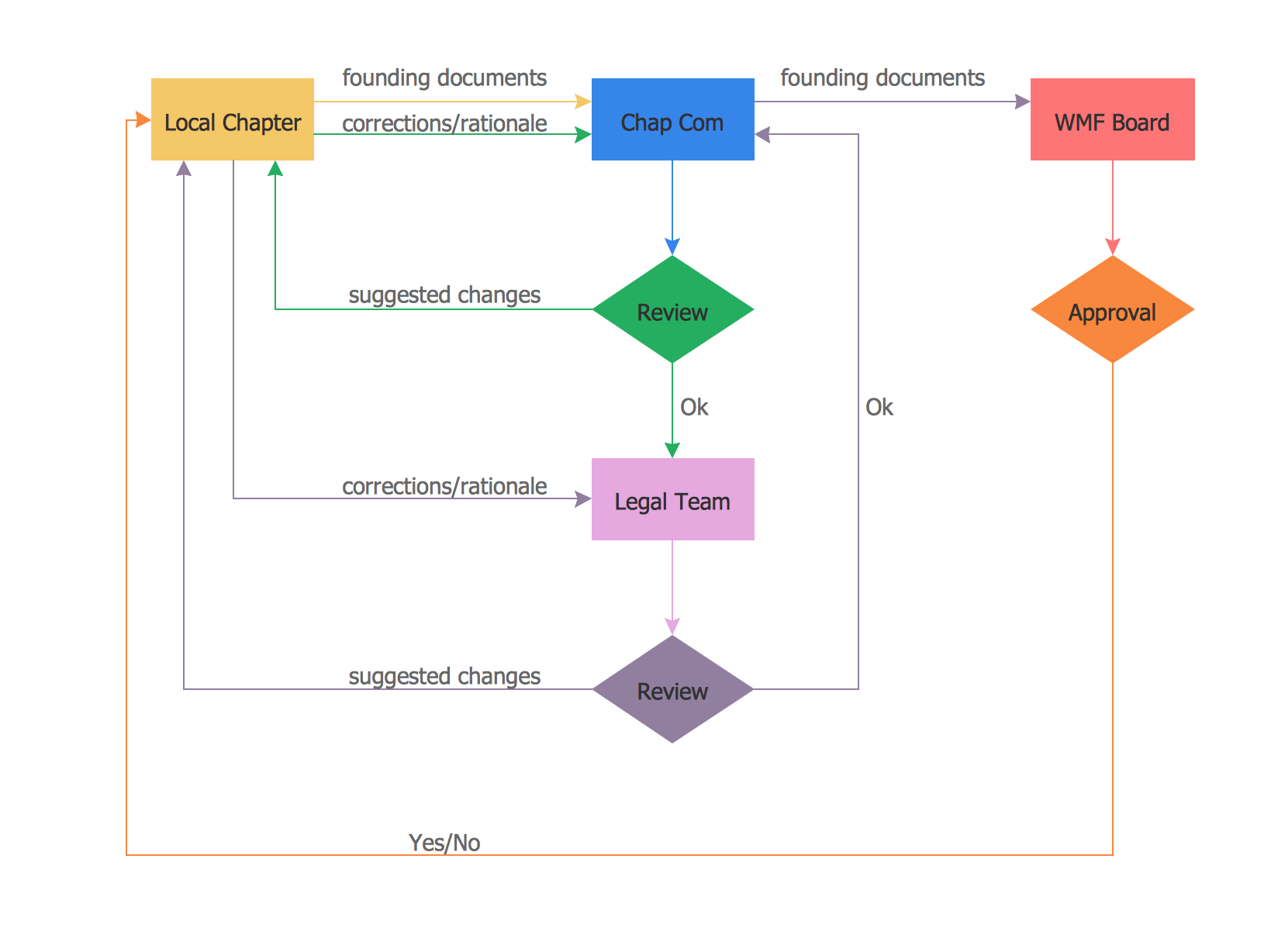
Audit procedures are the specific tests and methods that auditor executes when gathering the evidence which are necessary for making an opinion on the financial statements of the firm. There are three types of audit procedures: data selection, reliability validation, relevance confirmation. Thanks to the extensive drawing tools which provides the Audit Flowcharts solution from the Finance and Accounting area of ConceptDraw Solution Park, you can easy and effectively develop and realize various audit procedures.Sales Process Management
Sales process management is a business discipline which focuses on the development and practical application of various sales techniques, and on the management of sales operations of the company.It is effective to use professional software for the sales process management. ConceptDraw DIAGRAM diagramming and vector drawing software extended with Sales Flowcharts solution from the Marketing area of ConceptDraw Solution Park is the best choice.
Collaboration in a Project Team
Create with our data flow diagram software perfect data flow diagrams. Download data flow diagram software for FREE. Use hundreds of data flow diagram examples.Account Flowchart Stockbridge System. Flowchart Examples
Create your own flow charts of data processing systems using the ConceptDraw DIAGRAM diagramming and vector drawing software extended with the Cross-Functional Flowcharts solution from the Business Processes area of ConceptDraw Solution Park. This is a flowchart of a data processing system combining manual and computerized processing to handle accounts receivable, billing, and general ledger.Network Security Tips
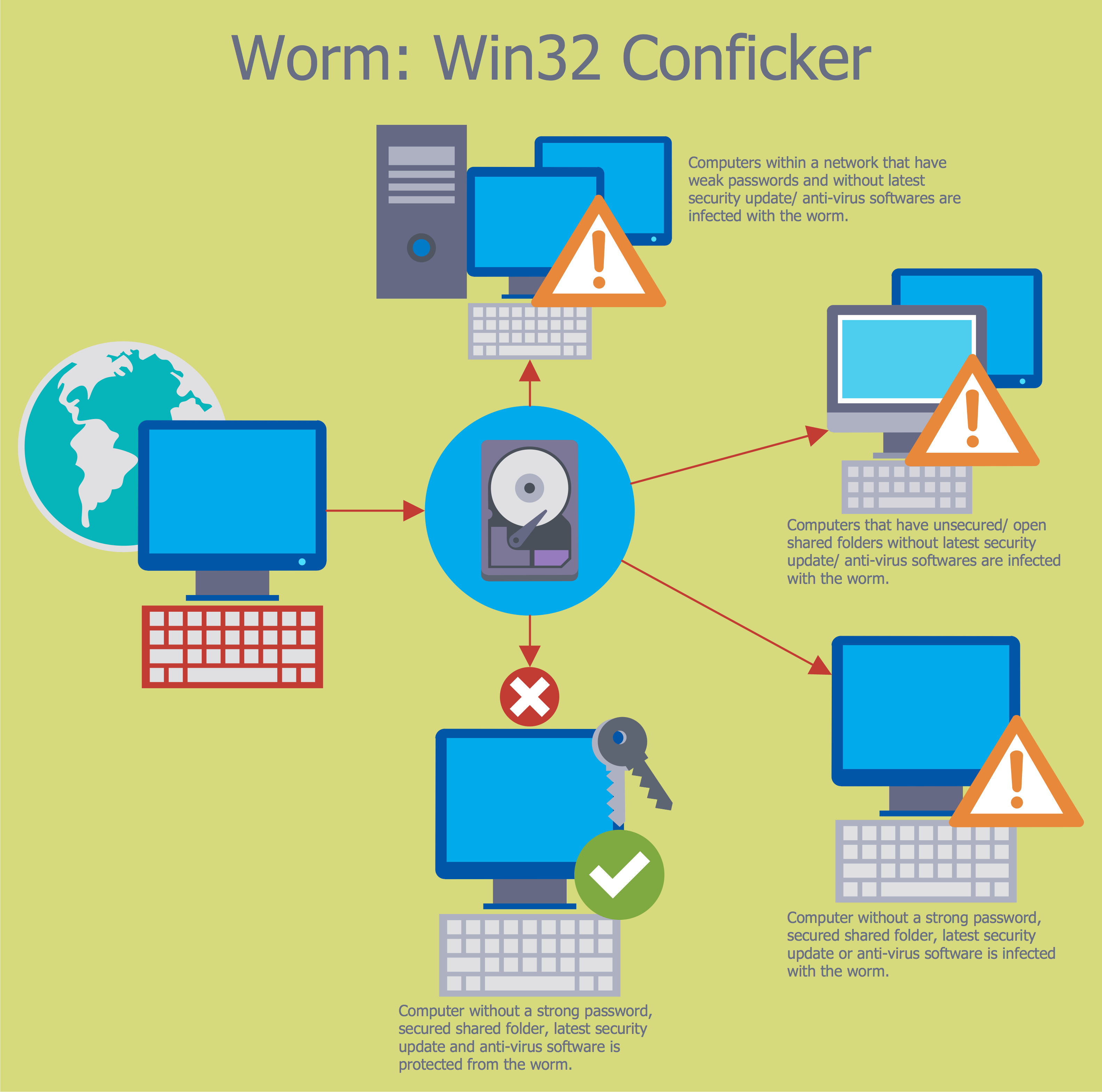
The Internet is a huge world with unlimited possibilities. But with all its numerous advantages, the Internet also conceals many dangers and security threats, that's why we advise you to follow simple network security tips. ConceptDraw DIAGRAM diagramming and vector drawing software supplied with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is an ideal software for easy designing Network Security Diagrams and attractive illustrations with effective network security tips.- Diagramthat Indicates Human Life Cycle
- Diagram That Indicates Human Life Cycle
- Human Life Cycle Chart
- Draw A Diagram About Lifecycles
- Daigram For Chart On Human Life Cycle
- Is There A Flow Diagram Of The Human Life Cycle
- Human Life Cycle Diagram
- Project management life cycle - Flowchart | Flowcharts | Draw ...
- Human Life Cycle Stages In Flow Diagram
- Flow Chart Of Human Life Cycle
- Intelligence analyst cycle - Arrow loop diagram | Target and Circular ...
- Flow Chart Of Life Cycle Of Humans
- Life Flow Chart Of Human
- Flow Chart Diagram Of Human Life
- Advanced persistent threat lifecycle | Circular Arrows | Circular ...
- Stages Of Human Life Cycle Flow Chart
- Advanced persistent threat lifecycle | Circular Arrows Diagrams | Apt ...
- Advanced persistent threat lifecycle | Roaming wireless local area ...
- Program to Make Flow Chart | Advanced persistent threat lifecycle ...