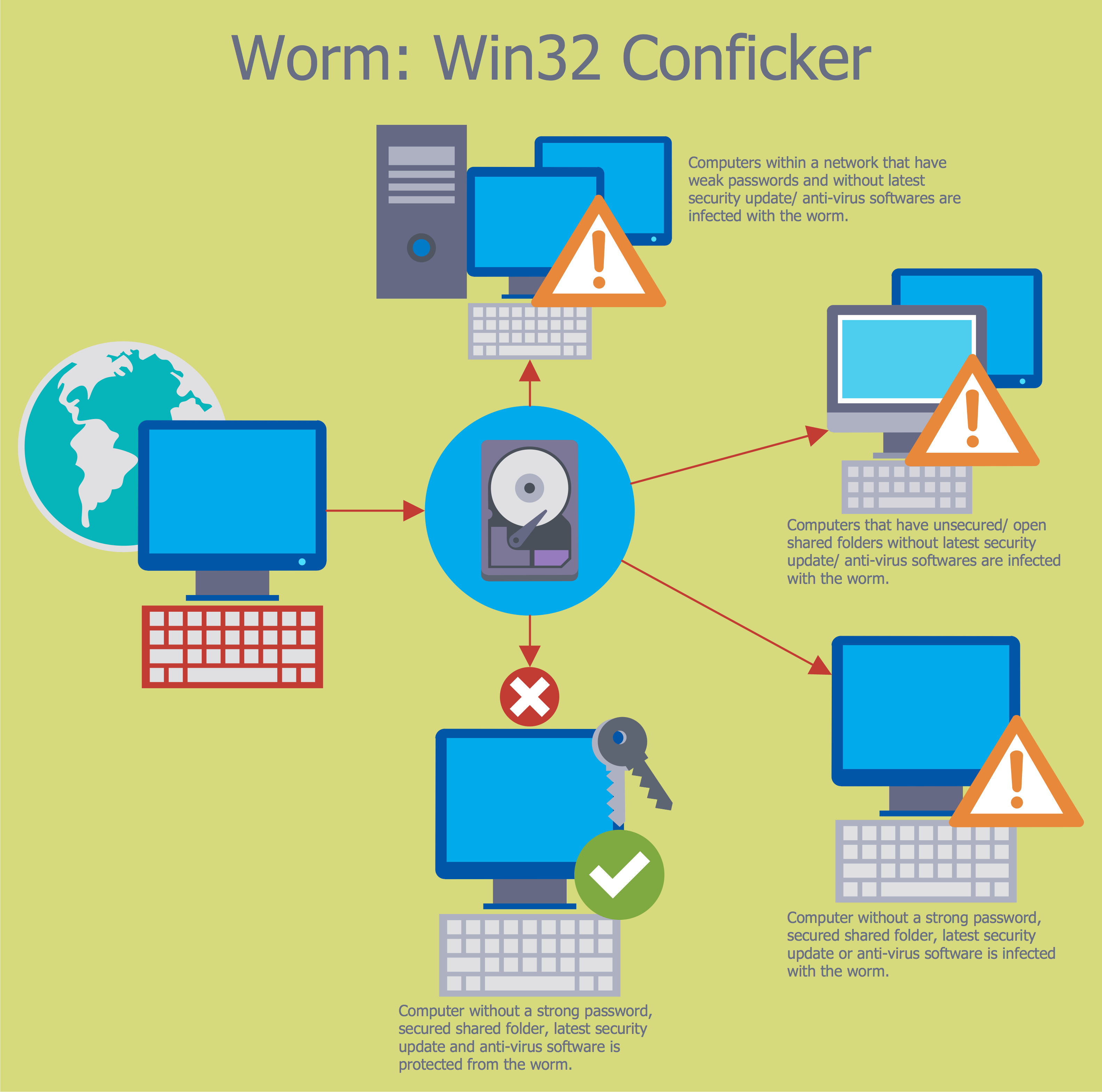
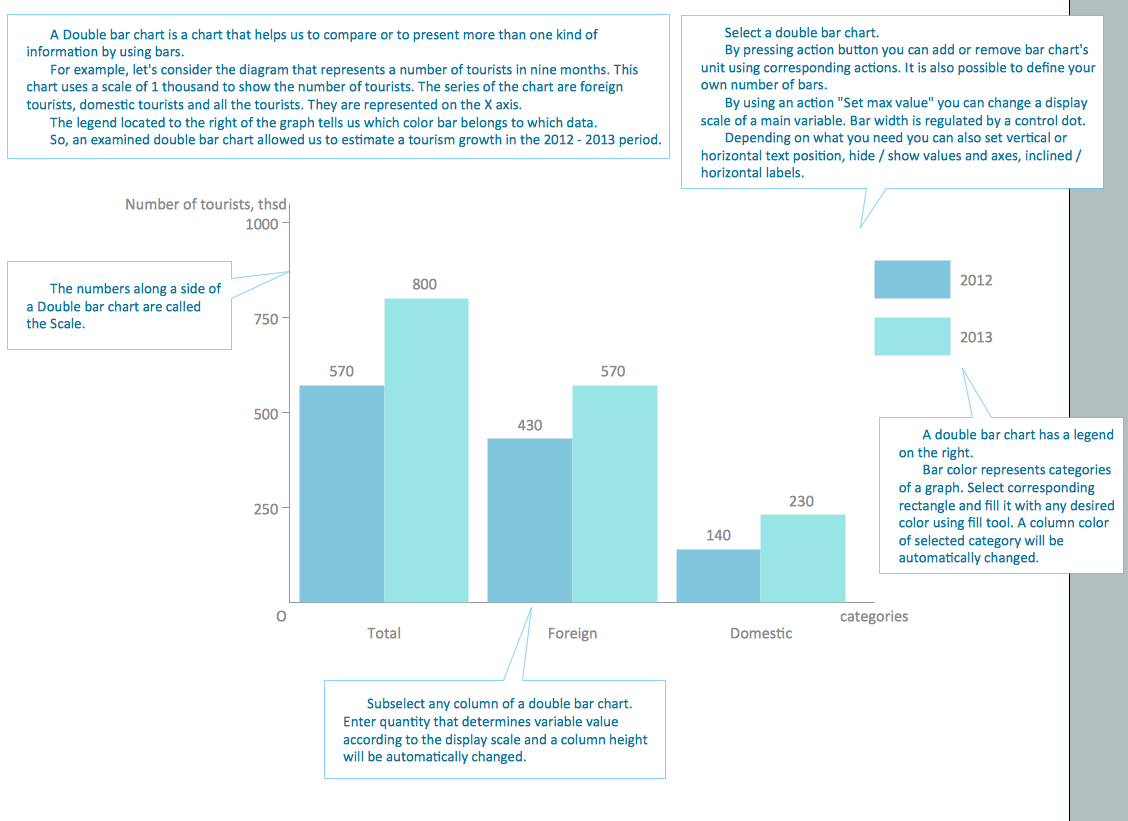
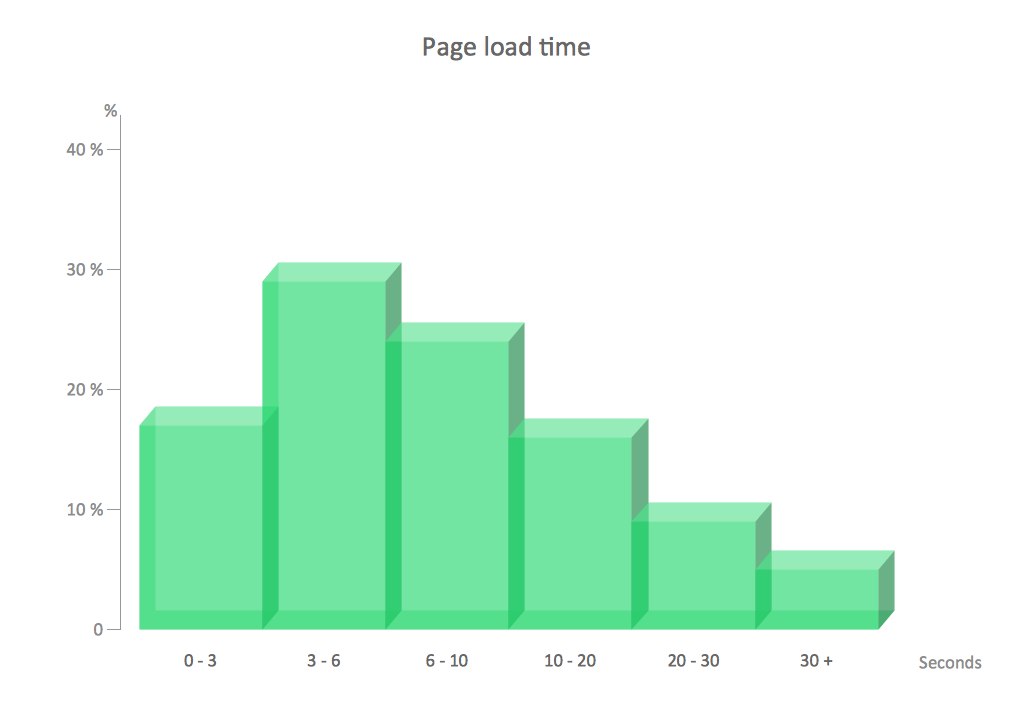
Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.Network Security Tips
The Internet is a huge world with unlimited possibilities. But with all its numerous advantages, the Internet also conceals many dangers and security threats, that's why we advise you to follow simple network security tips. ConceptDraw PRO diagramming and vector drawing software supplied with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is an ideal software for easy designing Network Security Diagrams and attractive illustrations with effective network security tips.Chart Templates
Easy charting software comes with beautiful chart templates and examples. This makes it easy to create professional charts without prior experience.Network Security
The Internet is a giant computer network which connects computers all over the world. It is integral part of human society and business. But the serious question for network engineers, designers, lawmakers and enforcers is the need for protect the Internet networks from the Internet crimes, hacking and attacks. There are quite a number of hardware, software and physical methods of protection against them. The samples you see on this page were created in ConceptDraw PRO using the tools of Network Security Diagrams Solution for ConceptDraw PRO software. They show protection networks with Firewalls and other network security devices.Chart Examples
Easy charting software comes with beautiful chart templates and examples. This makes it easy to create professional charts without prior experience.- Flow Chart Of Computer Security
- Advanced persistent threat lifecycle | Process Flowchart | Basic ...
- Advanced persistent threat lifecycle | Program to Make Flow Chart ...
- Advanced persistent threat lifecycle | Project management life cycle ...
- Advanced persistent threat lifecycle | Pyramid Chart Examples ...
- Program to Make Flow Chart | Advanced persistent threat lifecycle ...
- Basic Flowchart Symbols and Meaning | Process Flowchart | Flow ...
- Serious crime in Cincinnati | How to Create a Column Chart ...
- Basic Flowchart Symbols and Meaning | Flow Chart Symbols ...
- Flowchart design. Flowchart symbols , shapes, stencils and icons | IT ...
- Advanced persistent threat lifecycle | Creatively Draw A Diagram ...
- Process Flowchart | Basic Flowchart Symbols and Meaning ...
- Basic Flowchart Symbols and Meaning | ConceptDraw Arrows10 ...
- Design elements - Cybersecurity shapes | Cyber Security Degrees ...
- Process Flowchart | Basic Flowchart Symbols and Meaning ...
- Process Flowchart | AWS Architecture Diagrams | Workflow ...
- Cyber Security Degrees | Network Security Model | Network Security ...
- Cyber Attack
- Cisco Security. Cisco icons, shapes, stencils and symbols | Network ...
- Basic Flowchart Symbols and Meaning | How to Build Cloud ...