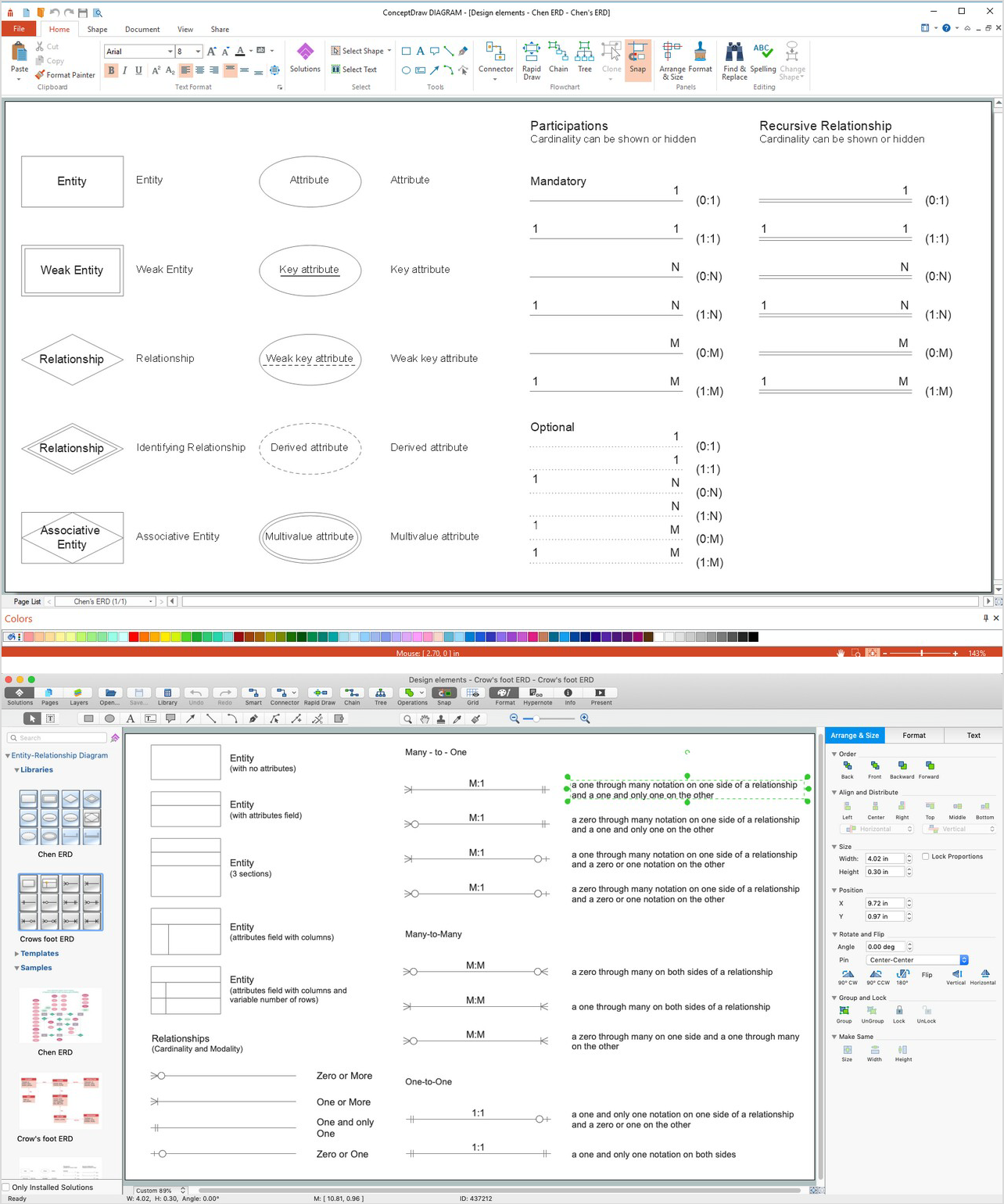
Entity Relationship Diagram Symbols
The semantic modeling method nowadays is successfully applied in database structure design. It is effective method of modeling the data structures, which is based on the meaning of these data. As a tool of semantic modeling, there are used different types of Entity-Relationship Diagrams. Entity Relationship Diagram (ERD) is applied to visually and clearly represent a structure of a business database. The main components of ERDs are: entity, relation and attributes. An entity is a class of similar objects in the model, each entity is depicted in the form of rectangle and has the name expressed by a noun. Relation is shown in the form of non-directional line that connects two entities. There are several notation styles used for ERDs: information engineering style, Chen style, Bachman style, Martin Style. The Entity Relationship Diagram symbols used for professional ERD drawing are predesigned by professionals and collected in the libraries of the Entity-Relationship Diagram (ERD) solution for ConceptDraw PRO software.This AD diagram example was redesigned from the picture "Asymmetric
encryption" from the book "Active Directory for Dummies".
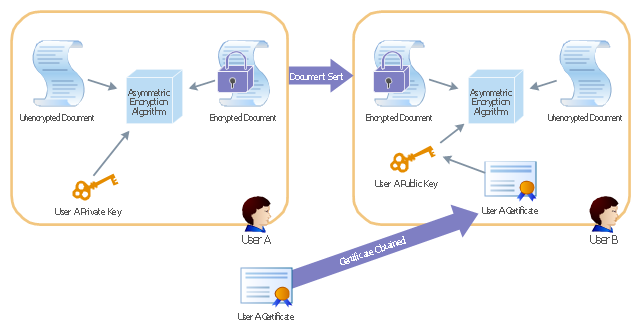
"Asymmetric Encryption:
This scenario uses a public and private key pair that is associated with each other. With this type of encryption, one of the keys is used to encrypt the data in such a way that only the corresponding second key is capable of decrypting the information. ...
In asymmetric encryption, two different keys are involved in the process: one for encrypting the document and a different but related key for decrypting the document. The two keys are generated at the same time so that if a document is encrypted with one of the keys, only the second related key can decrypt the document. ... Typically, these keys are referred to as a private key and a public key. A private key is one that is generated for a particular user and is never shared with any other user or computer. A public key is typically one of the pieces of data that’s stored in a PKI certificate. Although this type of encryption creates a very secure way of sharing data, an added benefit is you knowing that a piece of data decrypted by using a particular user’s public key must have come from that user because no other user would have the private key the document was encrypted with."
[Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Asymmetric encryption" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
encryption" from the book "Active Directory for Dummies".
"Asymmetric Encryption:
This scenario uses a public and private key pair that is associated with each other. With this type of encryption, one of the keys is used to encrypt the data in such a way that only the corresponding second key is capable of decrypting the information. ...
In asymmetric encryption, two different keys are involved in the process: one for encrypting the document and a different but related key for decrypting the document. The two keys are generated at the same time so that if a document is encrypted with one of the keys, only the second related key can decrypt the document. ... Typically, these keys are referred to as a private key and a public key. A private key is one that is generated for a particular user and is never shared with any other user or computer. A public key is typically one of the pieces of data that’s stored in a PKI certificate. Although this type of encryption creates a very secure way of sharing data, an added benefit is you knowing that a piece of data decrypted by using a particular user’s public key must have come from that user because no other user would have the private key the document was encrypted with."
[Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Asymmetric encryption" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
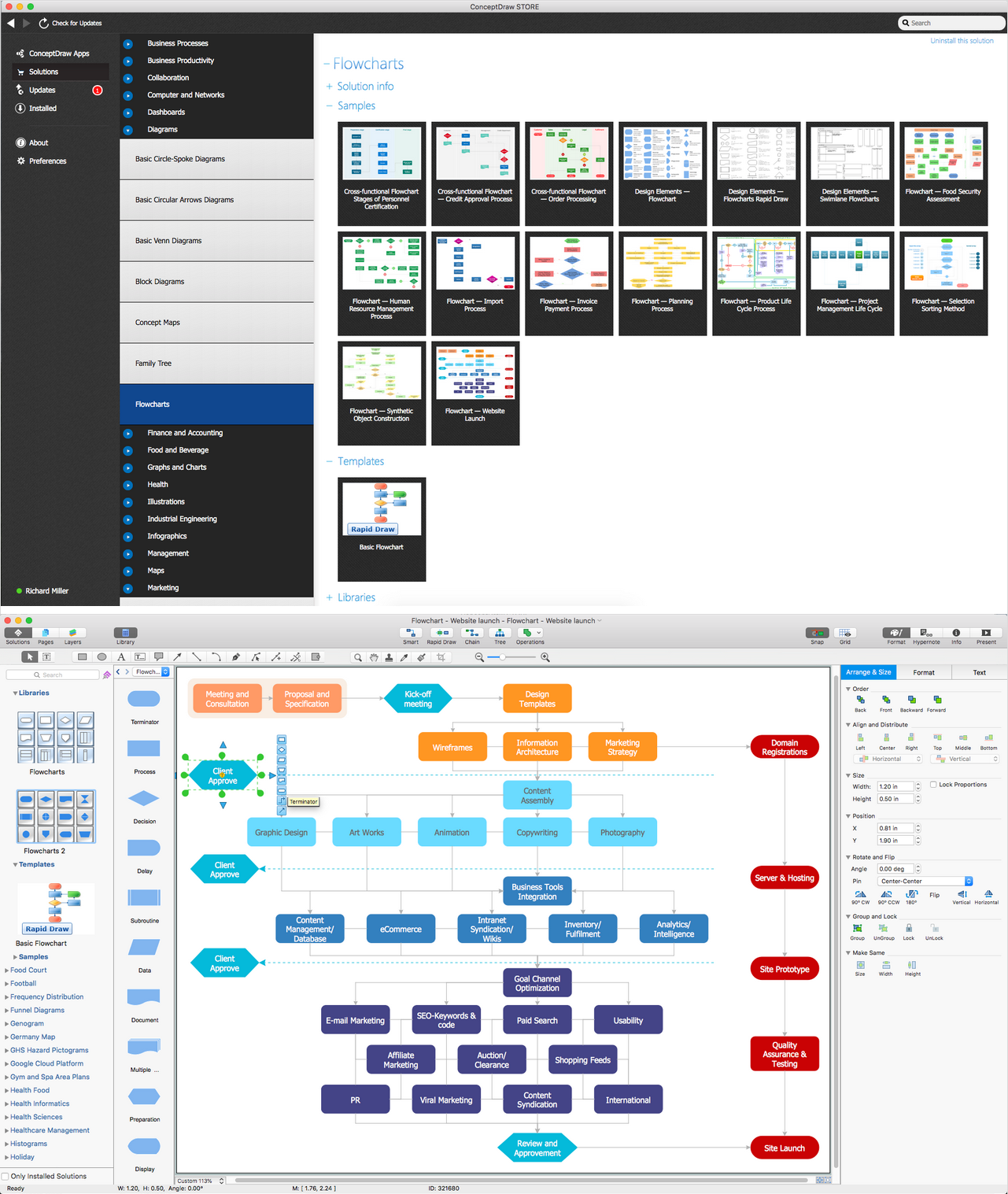
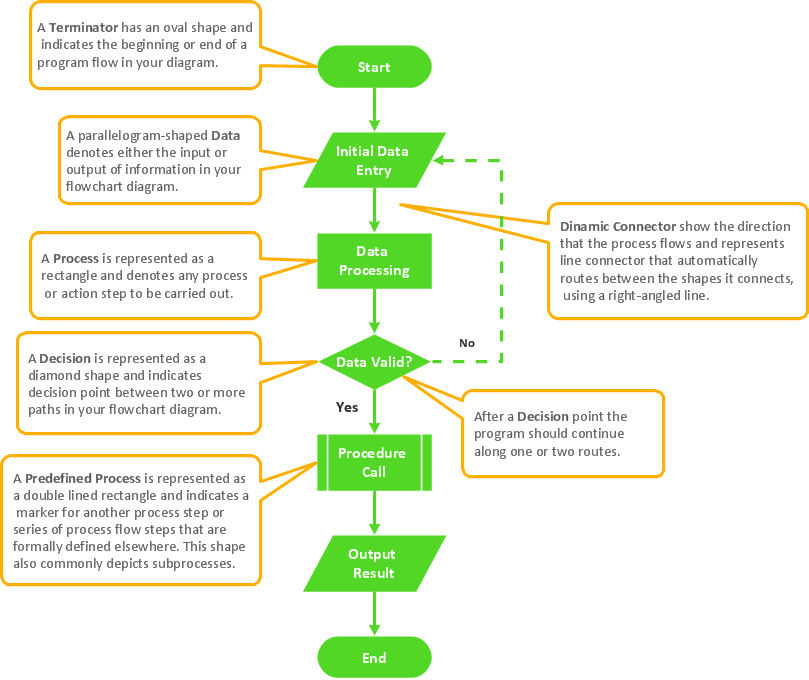
Basic Flowchart Symbols and Meaning
Flowcharts are the best for visually representation the business processes and the flow of a custom-order process through various departments within an organization. ConceptDraw PRO diagramming and vector drawing software extended with Flowcharts solution offers the full set of predesigned basic flowchart symbols which are gathered at two libraries: Flowchart and Flowcharts Rapid Draw. Among them are: process, terminator, decision, data, document, display, manual loop, and many other specific symbols. The meaning for each symbol offered by ConceptDraw gives the presentation about their proposed use in professional Flowcharts for business and technical processes, software algorithms, well-developed structures of web sites, Workflow diagrams, Process flow diagram and correlation in developing on-line instructional projects or business process system. Use of ready flow chart symbols in diagrams is incredibly useful - you need simply drag desired from the libraries to your document and arrange them in required order. There are a few serious alternatives to Visio for Mac, one of them is ConceptDraw PRO. It is one of the main contender with the most similar features and capabilities.
Flowchart Components
The ConceptDraw Flowchart component includes a set of samples and templates. This geathered as flowchart maker toolbox which focused on drawing flowcharts of any industry standards.This Azure cloud architecture pattern diagram template was created on the base of figure in the article "Valet Key Pattern" from the Microsoft Developer Network (MSDN) website.
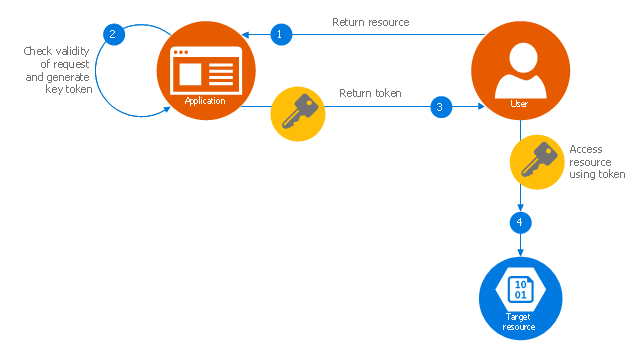
"Valet Key Pattern.
Use a token or key that provides clients with restricted direct access to a specific resource or service in order to offload data transfer operations from the application code. This pattern is particularly useful in applications that use cloud-hosted storage systems or queues, and can minimize cost and maximize scalability and performance. ...
Client programs and web browsers often need to read and write files or data streams to and from an application’s storage. ...
Data stores have the capability to handle upload and download of data directly, without requiring the application to perform any processing to move this data, but this typically requires the client to have access to the security credentials for the store.
... applications must be able to securely control access to data in a granular way, but still reduce the load on the server by setting up this connection and then allowing the client to communicate directly with the data store to perform the required read or write operations. ...
To resolve the problem of controlling access to a data store where the store itself cannot manage authentication and authorization of clients, one typical solution is to restrict access to the data store’s public connection and provide the client with a key or token that the data store itself can validate.
This key or token is usually referred to as a valet key. It provides time-limited access to specific resources and allows only predefined operations such as reading and writing to storage or queues, or uploading and downloading in a web browser. Applications can create and issue valet keys to client devices and web browsers quickly and easily, allowing clients to perform the required operations without requiring the application to directly handle the data transfer. This removes the processing overhead, and the consequent impact on performance and scalability, from the application and the server." [msdn.microsoft.com/ ru-RU/ library/ dn568102.aspx]
The Azure cloud system architecture diagram template "Valet key pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
"Valet Key Pattern.
Use a token or key that provides clients with restricted direct access to a specific resource or service in order to offload data transfer operations from the application code. This pattern is particularly useful in applications that use cloud-hosted storage systems or queues, and can minimize cost and maximize scalability and performance. ...
Client programs and web browsers often need to read and write files or data streams to and from an application’s storage. ...
Data stores have the capability to handle upload and download of data directly, without requiring the application to perform any processing to move this data, but this typically requires the client to have access to the security credentials for the store.
... applications must be able to securely control access to data in a granular way, but still reduce the load on the server by setting up this connection and then allowing the client to communicate directly with the data store to perform the required read or write operations. ...
To resolve the problem of controlling access to a data store where the store itself cannot manage authentication and authorization of clients, one typical solution is to restrict access to the data store’s public connection and provide the client with a key or token that the data store itself can validate.
This key or token is usually referred to as a valet key. It provides time-limited access to specific resources and allows only predefined operations such as reading and writing to storage or queues, or uploading and downloading in a web browser. Applications can create and issue valet keys to client devices and web browsers quickly and easily, allowing clients to perform the required operations without requiring the application to directly handle the data transfer. This removes the processing overhead, and the consequent impact on performance and scalability, from the application and the server." [msdn.microsoft.com/ ru-RU/ library/ dn568102.aspx]
The Azure cloud system architecture diagram template "Valet key pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
ConceptDraw PRO ER Diagram Tool
Entity-relationship model, also called ER-model, is the main tool of domain modeling on the stage of conceptual design. The modeling of domain data structures is based on the use of graphical tools - Entity-Relationship diagrams (ER-diagrams). The core concepts of ER-Diagram are entity, attribute and relationship. ER-diagram lets visually represent the entities, helps effectively document all properties of designed system and to detail the data storages. To represent the elements at ER-model are commonly used Chen’s notation and Crow’s foot notation, each has its pros and cons. The entity on ER-diagram is represented in the form of rectangle, which specifies its name. An attribute is a property of the entity and relationship is an interaction between the entities. The relationship between two entities is called binary, between more than two entities - ternary. Specific software, such as ConceptDraw PRO with Entity-Relationship Diagram (ERD) solution from ConceptDraw Solution Park is helpful for easy creation Entity-Relationship Diagrams."Chen's notation for entity–relationship modeling uses rectangles to represent entity sets, and diamonds to represent relationships appropriate for first-class objects: they can have attributes and relationships of their own. If an entity set participates in a relationship set, they are connected with a line.
Attributes are drawn as ovals and are connected with a line to exactly one entity or relationship set.
Cardinality constraints are expressed as follows:
- a double line indicates a participation constraint, totality or surjectivity: all entities in the entity set must participate in at least one relationship in the relationship set;
- an arrow from entity set to relationship set indicates a key constraint, i.e. injectivity: each entity of the entity set can participate in at most one relationship in the relationship set;
- a thick line indicates both, i.e. bijectivity: each entity in the entity set is involved in exactly one relationship.
- an underlined name of an attribute indicates that it is a key: two different entities or relationships with this attribute always have different values for this attribute.
Attributes are often omitted as they can clutter up a diagram; other diagram techniques often list entity attributes within the rectangles drawn for entity sets." [Entity–relationship model. Wikipedia]
The vector stencils library ERD, Chen's notation contains 13 symbols for drawing entity-relatinship diagrams using the ConceptDraw PRO diagramming and vector drawing software.
The example "Design elements - ER diagram (Chen notation)" is included in the Entity-Relationship Diagram (ERD) solution from the Software Development area of ConceptDraw Solution Park.
Attributes are drawn as ovals and are connected with a line to exactly one entity or relationship set.
Cardinality constraints are expressed as follows:
- a double line indicates a participation constraint, totality or surjectivity: all entities in the entity set must participate in at least one relationship in the relationship set;
- an arrow from entity set to relationship set indicates a key constraint, i.e. injectivity: each entity of the entity set can participate in at most one relationship in the relationship set;
- a thick line indicates both, i.e. bijectivity: each entity in the entity set is involved in exactly one relationship.
- an underlined name of an attribute indicates that it is a key: two different entities or relationships with this attribute always have different values for this attribute.
Attributes are often omitted as they can clutter up a diagram; other diagram techniques often list entity attributes within the rectangles drawn for entity sets." [Entity–relationship model. Wikipedia]
The vector stencils library ERD, Chen's notation contains 13 symbols for drawing entity-relatinship diagrams using the ConceptDraw PRO diagramming and vector drawing software.
The example "Design elements - ER diagram (Chen notation)" is included in the Entity-Relationship Diagram (ERD) solution from the Software Development area of ConceptDraw Solution Park.
ERD Symbols and Meanings
Entity Relationship Diagram (ERD) is a popular software engineering tool for database modeling and illustration the logical structure of databases, which uses one of two notations - Chen's or Crow’s Foot. Crow's foot notation is effective when used in software engineering, information engineering, structured systems analysis and design. Each of these notations applies its own set of ERD symbols. Crow's foot diagrams use boxes to represent entities and lines between these boxes to show relationships. Varied shapes at the ends of lines depict the cardinality of a given relationship. Chen's ERD notation is more detailed way to represent entities and relationships. ConceptDraw PRO application enhanced with all-inclusive Entity-Relationship Diagram (ERD) solution allows design professional ER diagrams with Chen's or Crow’s Foot notation on your choice. It contains the full set of ready-to-use standardized ERD symbols and meanings helpful for quickly drawing, collection of predesigned ERD samples, examples and templates. ConceptDraw Pro is a great alternative to Visio for Mac users as it offers more features and can easily handle the most demanding professional needs.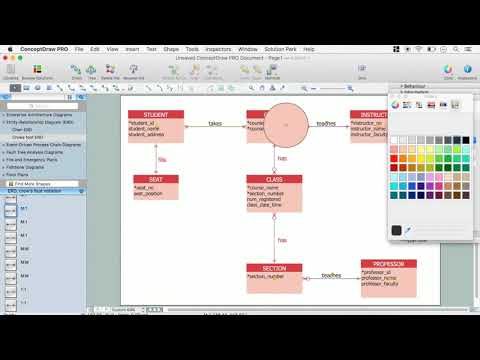
Business Process Modeling Notation
ConceptDraw PRO is a software for simplу depicting the business processes based on BPMN 2.0. Business Process Diagrams Cross-Functional-Flowcharts, Workflows, Process Charts, IDEF0 and IDEF2, Timeline, Calendars, Gantt Charts, Business Process Modeling, Audit and Opportunity Flowcharts and Mind Maps (presentations, meeting agendas).ConceptDraw PRO Network Diagram Tool
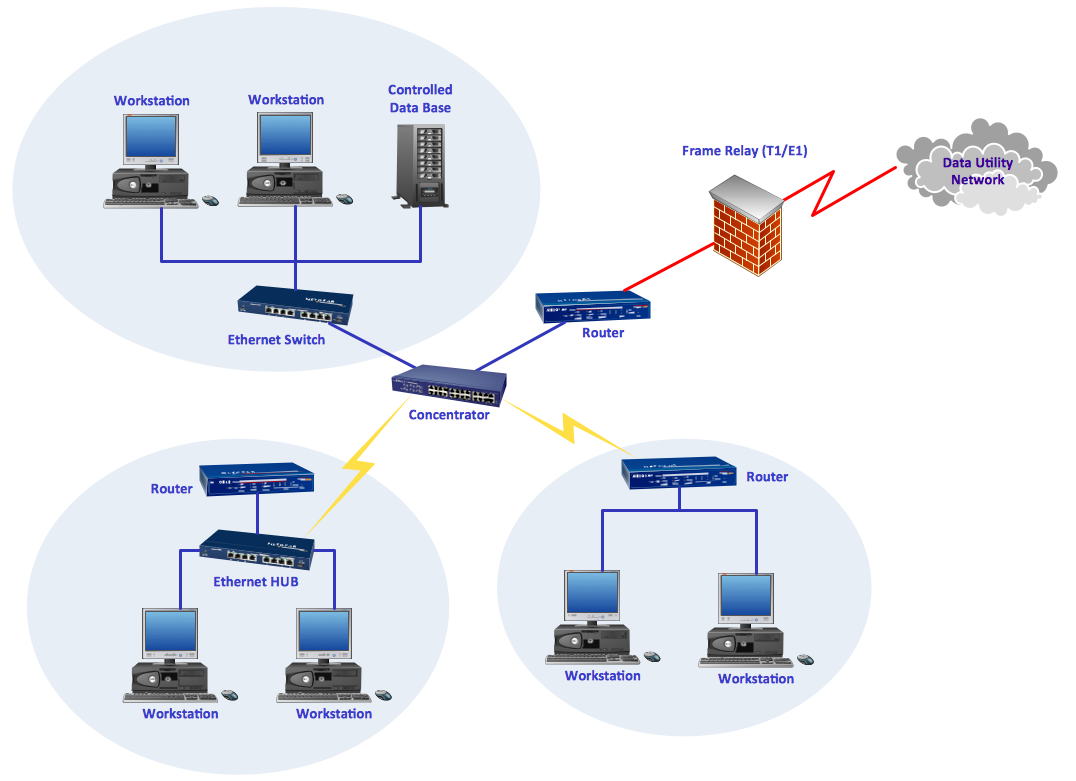
Computer network diagrams visually depict the nodes of computer networks and connections between them. Diversity of Network Diagrams includes Wireless network diagrams, Network wiring diagrams, LAN network diagrams, Network WAN diagrams, Network topology diagrams, Network cable diagrams, Logical network diagrams, Network security diagrams, Diagram home network, Network physical diagrams, Activity network diagrams, and many others. To construct any of them it is useful to apply a special software with effective network diagramming tools. ConceptDraw PRO is ideal and powerful network diagram tool. It helps you diagram a network or create Computer network diagrams of various types using specialized and task-specific libraries of network components such as computers, hubs, switches, servers, routers, smart connectors, printers, mainframes, face plates, etc. that simulate network architectures, network design topologies and devices (all these shapes are parts of network diagram tool ConceptDraw PRO).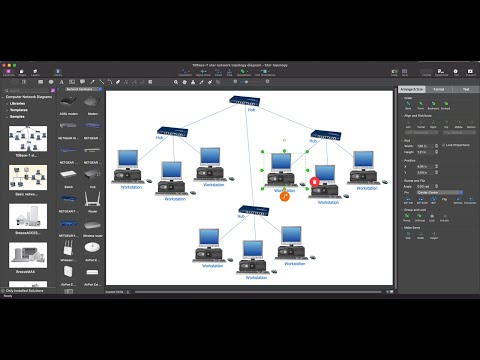
- How To Represent Foreign Key In Er Diagram
- Er Diagram With Unique Key
- Flowcharts | Shape To Represent Foreign Key In Er Diagram
- Design elements - ER diagram (Chen notation) | Flowcharts | Spatial ...
- Foreign Key Representation In Er Diagram
- Timeline Diagrams | Fishbone Diagrams | Draw Timeline And ...
- Key Attribute Er Diagram
- Identify Key Attributes In An Er Diagram
- Diagram Legend Or Key
- Erd Unique Key Represent


.png--diagram-flowchart-example.png)