This computer security diagram example was designed on the base of the Wikimedia Commons file: Conficker.svg. [commons.wikimedia.org/ wiki/ File:Conficker.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
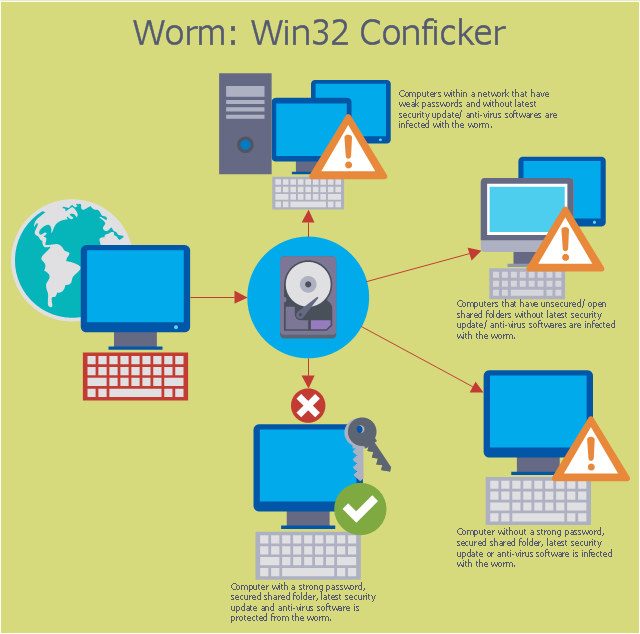
"A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer." [Computer worm. Wikipedia]
The cybersecurity diagram example "Spread of Conficker worm" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer." [Computer worm. Wikipedia]
The cybersecurity diagram example "Spread of Conficker worm" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
 Entity-Relationship Diagram (ERD)
Entity-Relationship Diagram (ERD)
Entity-Relationship Diagram (ERD) solution extends ConceptDraw PRO software with templates, samples and libraries of vector stencils from drawing the ER-diagrams by Chen's and crow’s foot notations.
This computer security diagram example was designed on the base of the Wikimedia Commons file: Firewall.png.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
Fundraising Pyramid
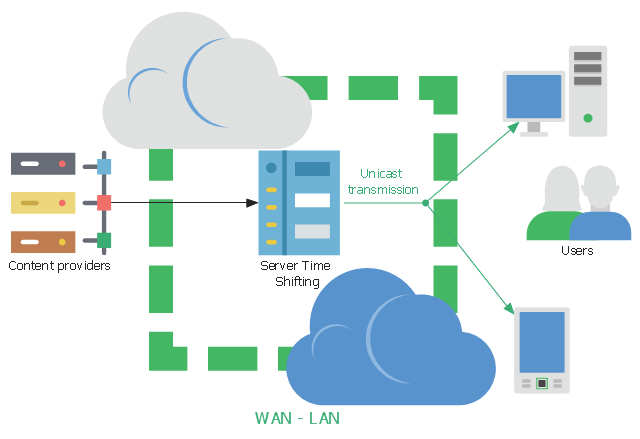
ConceptDraw Pyramid Diagram software allows drawing column charts using predesigned objects or drawing tool.This network diagram sample shows the IPTV network. It was designed on the base of Wikimedia Commons file: RedservidorIPTV.jpg.
[commons.wikimedia.org/ wiki/ File:RedservidorIPTV.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Internet Protocol television (IPTV) is a system through which television services are delivered using the Internet protocol suite over a packet-switched network such as a LAN or the Internet, instead of being delivered through traditional terrestrial, satellite signal, and cable television formats. Unlike downloaded media, IPTV offers the ability to stream the media in smaller batches, directly from the source. As a result, a client media player can begin playing the data (such as a movie) before the entire file has been transmitted. This is known as streaming media." [IPTV. Wikipedia]
The network diagram example "Red IPTV server" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
[commons.wikimedia.org/ wiki/ File:RedservidorIPTV.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Internet Protocol television (IPTV) is a system through which television services are delivered using the Internet protocol suite over a packet-switched network such as a LAN or the Internet, instead of being delivered through traditional terrestrial, satellite signal, and cable television formats. Unlike downloaded media, IPTV offers the ability to stream the media in smaller batches, directly from the source. As a result, a client media player can begin playing the data (such as a movie) before the entire file has been transmitted. This is known as streaming media." [IPTV. Wikipedia]
The network diagram example "Red IPTV server" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
This exaple was resigned from the Wikimedia Commons file: Mobile Cloud Architecture.jpg. [commons.wikimedia.org/ wiki/ File:Mobile_ Cloud_ Architecture.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
This diagram describes general architecture of Mobile Cloud Computing.
Legend.
BTS: Base Transceiver Station.
AAA: Network Authentication, Authorization, and Accounting.
HA: Home Agent.
"Mobile/ cloud computing is the combination of cloud computing and mobile networks to bring benefits for mobile users, network operators, as well as cloud computing providers. The ultimate goal of MCC (mean of MCC is Mobile/ Cloud Computing) is to enable execution of rich mobile applications on a plethora of mobile devices, with a rich user experience. MCC provides business opportunities for mobile network operators as well as cloud providers." [Mobile cloud computing. Wikipedia]
The example "Mobile cloud architecture diagram" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
This diagram describes general architecture of Mobile Cloud Computing.
Legend.
BTS: Base Transceiver Station.
AAA: Network Authentication, Authorization, and Accounting.
HA: Home Agent.
"Mobile/ cloud computing is the combination of cloud computing and mobile networks to bring benefits for mobile users, network operators, as well as cloud computing providers. The ultimate goal of MCC (mean of MCC is Mobile/ Cloud Computing) is to enable execution of rich mobile applications on a plethora of mobile devices, with a rich user experience. MCC provides business opportunities for mobile network operators as well as cloud providers." [Mobile cloud computing. Wikipedia]
The example "Mobile cloud architecture diagram" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
This network diagram sample shows the video on demand (VoD) architecture in a network video recorder (NVR) enviroment. It was designed on the base of Wikimedia Commons file: BaixdemandaArchitecture.png.
[commons.wikimedia.org/ wiki/ File:BaixdemandaArchitecture.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Video on demand (display) (VOD) are systems which allow users to select and watch/ listen to video or audio content when they choose to, rather than having to watch at a specific broadcast time. IPTV technology is often used to bring video on demand to televisions and personal computers." [Video on demand. Wikipedia]
The network diagram example "VoD architecture in a NVR enviroment" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computers and
Communications solution from the Illustration area of ConceptDraw Solution Park.
[commons.wikimedia.org/ wiki/ File:BaixdemandaArchitecture.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Video on demand (display) (VOD) are systems which allow users to select and watch/ listen to video or audio content when they choose to, rather than having to watch at a specific broadcast time. IPTV technology is often used to bring video on demand to televisions and personal computers." [Video on demand. Wikipedia]
The network diagram example "VoD architecture in a NVR enviroment" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computers and
Communications solution from the Illustration area of ConceptDraw Solution Park.
This Active Directory network diagram example depicts types of groups and people assignment rules.
Architecture groups in a Windows Active Directory 2003:
(1) The arrow indicates "may be a member of."
(2) Dotted: Functionality limited to Windows 2003 (without the Windows 2000 compatibility).
(3) Red: Setting possible, but not recommended.
It was drawn on the base of Wikimedia Commons file: AD2003.JPG. [commons.wikimedia.org/ wiki/ File:AD2003.JPG]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
The Active Directory network diagram example "Tree and Forest (Full Trust)" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Architecture groups in a Windows Active Directory 2003:
(1) The arrow indicates "may be a member of."
(2) Dotted: Functionality limited to Windows 2003 (without the Windows 2000 compatibility).
(3) Red: Setting possible, but not recommended.
It was drawn on the base of Wikimedia Commons file: AD2003.JPG. [commons.wikimedia.org/ wiki/ File:AD2003.JPG]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
The Active Directory network diagram example "Tree and Forest (Full Trust)" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
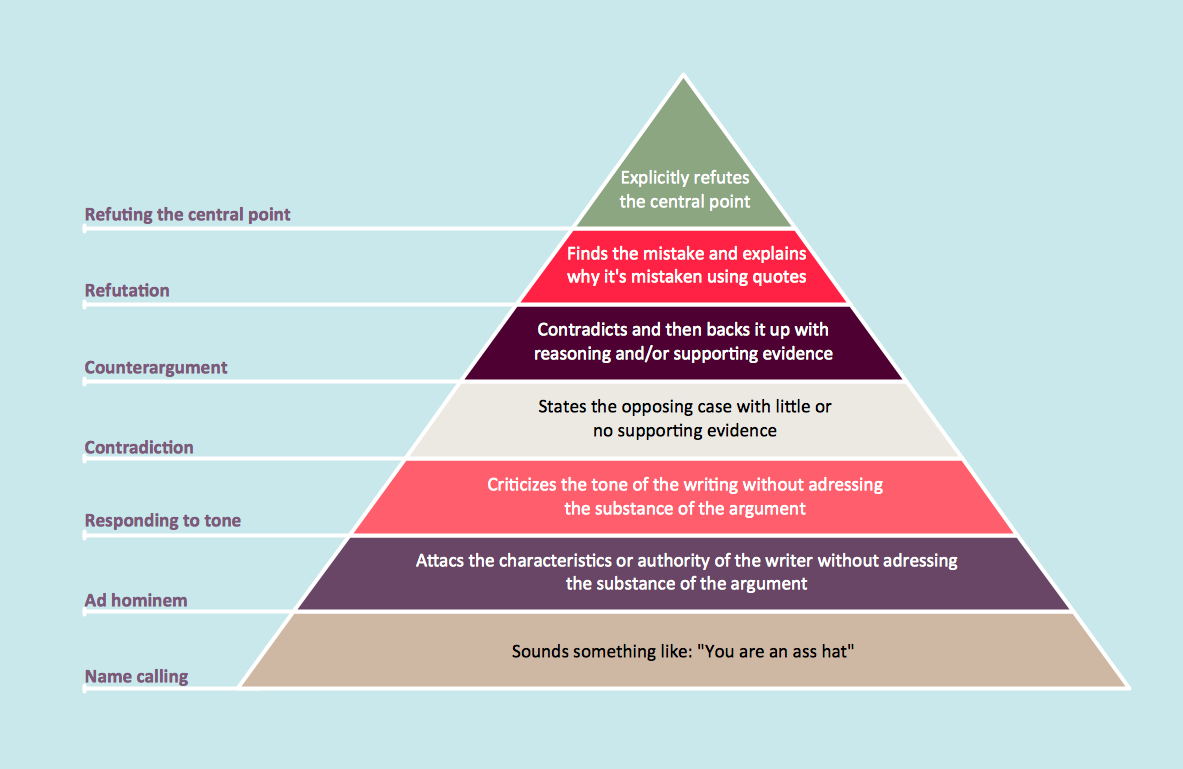
Pyramid Diagram
A triangular graphic representing Graham's "hierarchy of disagreement", based on Paul Graham's March 2008 essay "How to Disagree".This interactive voice response (IVR) diagram sample shows the Voice over IP (VoIP) signalling protocol stack. It was designed on the base of the Wikimedia Commons file: Pvoip.gif. [commons.wikimedia.org/ wiki/ File:Pvoip.gif]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A VoIP phone or IP phone uses Voice over IP technologies for placing and transmitting telephone calls over an IP network, such as the Internet, instead of the traditional public switched telephone network (PSTN).
Digital IP-based telephone service uses control protocols such as the Session Initiation Protocol (SIP), Skinny Client Control Protocol (SCCP) or various other proprietary protocols." [VoIP phone. Wikipedia]
The IVR diagram example "VoIP protocols" was designed using ConceptDraw PRO diagramming and vector drawing software extended with the Interactive Voice Response Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A VoIP phone or IP phone uses Voice over IP technologies for placing and transmitting telephone calls over an IP network, such as the Internet, instead of the traditional public switched telephone network (PSTN).
Digital IP-based telephone service uses control protocols such as the Session Initiation Protocol (SIP), Skinny Client Control Protocol (SCCP) or various other proprietary protocols." [VoIP phone. Wikipedia]
The IVR diagram example "VoIP protocols" was designed using ConceptDraw PRO diagramming and vector drawing software extended with the Interactive Voice Response Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
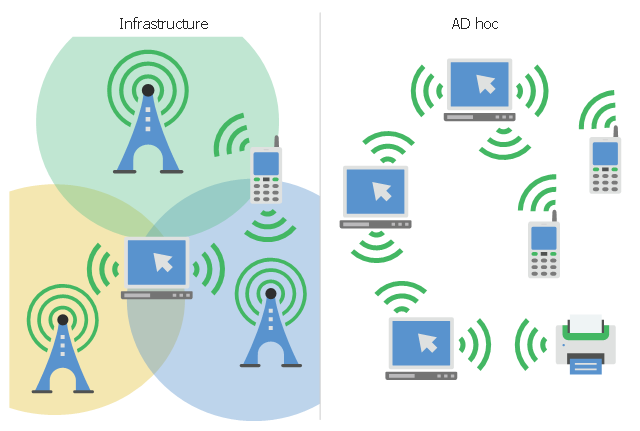
This infographic sample visualizes the Conventional and wireless ad hoc network. It was designed on the base of the Wikimedia Commons file: Běžná bezdrátová síť a ad hoc síť.png.
[commons.wikimedia.org/ wiki/ File:B%C4%9B%C5%BEn%C3%A1_ bezdr%C3%A1tov%C3%A1_ s%C3%AD%C5%A5_ a_ ad_ hoc_ s%C3%AD%C5%A5.png]
This file is licensed under the Creative Commons Attribution-Share Alike 4.0 International license. [creativecommons.org/ licenses/ by-sa/ 4.0/ deed.en]
"A wireless ad hoc network (WANET) is a decentralized type of wireless network. The network is ad hoc because it does not rely on a pre existing infrastructure, such as routers in wired networks or access points in managed (infrastructure) wireless networks. Instead, each node participates in routing by forwarding data for other nodes, so the determination of which nodes forward data is made dynamically on the basis of network connectivity. In addition to the classic routing, ad hoc networks can use flooding for forwarding data.
Wireless mobile ad hoc networks are self-configuring, dynamic networks in which nodes are free to move. Wireless networks lack the complexities of infrastructure setup and administration, enabling devices to create and join networks "on the fly" – anywhere, anytime." [Wireless ad hoc network. Wikipedia]
The infographic example "Conventional and wireless ad hoc network" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
[commons.wikimedia.org/ wiki/ File:B%C4%9B%C5%BEn%C3%A1_ bezdr%C3%A1tov%C3%A1_ s%C3%AD%C5%A5_ a_ ad_ hoc_ s%C3%AD%C5%A5.png]
This file is licensed under the Creative Commons Attribution-Share Alike 4.0 International license. [creativecommons.org/ licenses/ by-sa/ 4.0/ deed.en]
"A wireless ad hoc network (WANET) is a decentralized type of wireless network. The network is ad hoc because it does not rely on a pre existing infrastructure, such as routers in wired networks or access points in managed (infrastructure) wireless networks. Instead, each node participates in routing by forwarding data for other nodes, so the determination of which nodes forward data is made dynamically on the basis of network connectivity. In addition to the classic routing, ad hoc networks can use flooding for forwarding data.
Wireless mobile ad hoc networks are self-configuring, dynamic networks in which nodes are free to move. Wireless networks lack the complexities of infrastructure setup and administration, enabling devices to create and join networks "on the fly" – anywhere, anytime." [Wireless ad hoc network. Wikipedia]
The infographic example "Conventional and wireless ad hoc network" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
This interactive voice response (IVR) diagram sample shows the Scheme of VoIP call with SIM box and gateway. It was designed on the base of the Wikimedia Commons file: Scheme of VoIP call with Sim box.png. [commons.wikimedia.org/ wiki/ File:Scheme_ of_ VoIP_ call_ with_ Sim_ box.png]
This file is licensed under the Creative Commons Attribution-Share Alike 4.0 International license. [creativecommons.org/ licenses/ by-sa/ 4.0/ deed.en]
"A SIM box (also called a SIM bank) is device used as part of a VoIP gateway installation. It contains a number of SIM cards, which are linked to the gateway but housed and stored separately from it. A SIM box can have SIM cards of different mobile operators installed, permitting it to operate with several GSM gateways located in different places." [SIM box. Wikipedia]
The IVR diagram example "VoIP call with SIM box and gateway" was designed using ConceptDraw PRO diagramming and vector drawing software extended with the Interactive Voice Response Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
This file is licensed under the Creative Commons Attribution-Share Alike 4.0 International license. [creativecommons.org/ licenses/ by-sa/ 4.0/ deed.en]
"A SIM box (also called a SIM bank) is device used as part of a VoIP gateway installation. It contains a number of SIM cards, which are linked to the gateway but housed and stored separately from it. A SIM box can have SIM cards of different mobile operators installed, permitting it to operate with several GSM gateways located in different places." [SIM box. Wikipedia]
The IVR diagram example "VoIP call with SIM box and gateway" was designed using ConceptDraw PRO diagramming and vector drawing software extended with the Interactive Voice Response Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
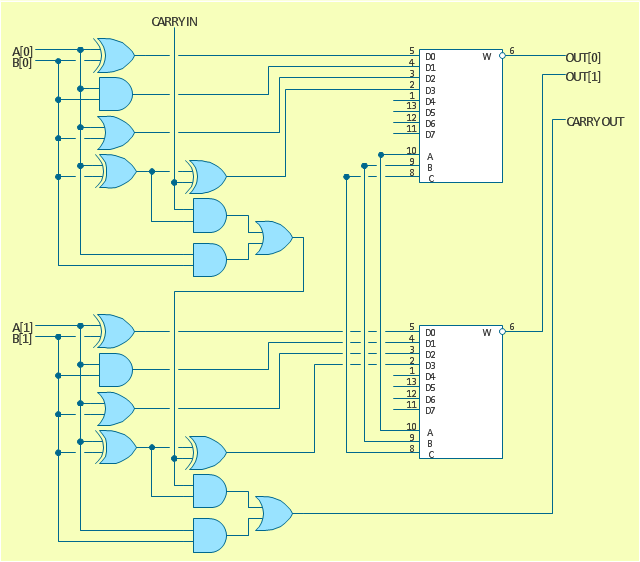
The logic gate diagram example "2-bit ALU" was redesigned from the Wikimedia Commons file: 2-bit ALU.svg.
[commons.wikimedia.org/ wiki/ File:2-bit_ ALU.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In digital electronics, an arithmetic and logic unit (ALU) is a digital circuit that performs integer arithmetic and logical operations. The ALU is a fundamental building block of the central processing unit of a computer, and even the simplest microprocessors contain one for purposes such as maintaining timers. The processors found inside modern CPUs and graphics processing units (GPUs) accommodate very powerful and very complex ALUs; a single component may contain a number of ALUs. ...
Most of a processor's operations are performed by one or more ALUs. An ALU loads data from input registers. Then an external control unit tells the ALU what operation to perform on that data, and then the ALU stores its result into an output register. The control unit is responsible for moving the processed data between these registers, ALU and memory." [Arithmetic logic unit. Wikipedia]
The logic gate diagram example "2-bit ALU" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Electrical Engineering solution from the Engineering area of ConceptDraw Solution Park.
[commons.wikimedia.org/ wiki/ File:2-bit_ ALU.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In digital electronics, an arithmetic and logic unit (ALU) is a digital circuit that performs integer arithmetic and logical operations. The ALU is a fundamental building block of the central processing unit of a computer, and even the simplest microprocessors contain one for purposes such as maintaining timers. The processors found inside modern CPUs and graphics processing units (GPUs) accommodate very powerful and very complex ALUs; a single component may contain a number of ALUs. ...
Most of a processor's operations are performed by one or more ALUs. An ALU loads data from input registers. Then an external control unit tells the ALU what operation to perform on that data, and then the ALU stores its result into an output register. The control unit is responsible for moving the processed data between these registers, ALU and memory." [Arithmetic logic unit. Wikipedia]
The logic gate diagram example "2-bit ALU" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Electrical Engineering solution from the Engineering area of ConceptDraw Solution Park.
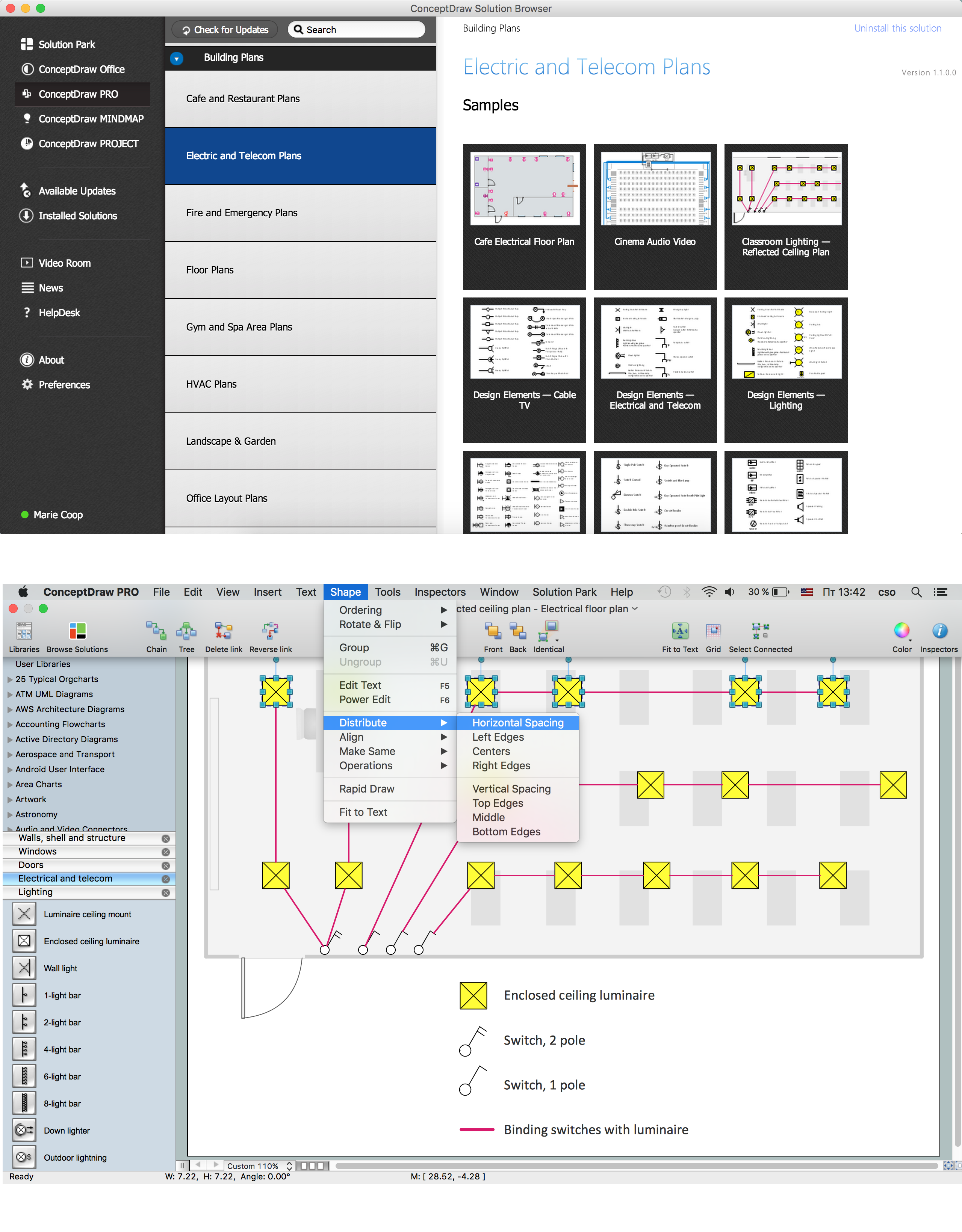
How To use House Electrical Plan Software
How we can conduct the electricity at house correctly without a plan? It is impossible. The House electrical diagram depicts locations of switches, outlets, dimmers and lights, and lets understand how you will connect them. But design of House Electrical Plan looks a complex task at a glance, which requires a lot of tools and special experience. But now all is simple with all-inclusive floor plan software - ConceptDraw PRO. As a house electrical plan software, the ConceptDraw PRO contains libraries with a large range of professional lighting and electrical symbols, ready-to-use electrical plans samples and examples, and built-in templates for creating great-looking Home floor electrical plans. It is a fastest way to draw Electrical circuit diagrams, Electrical wiring and Circuit schematics, Digital circuits, Electrical equipment, House electrical plans, Satellite television, Cable television, Home cinema, Closed-circuit television when are used the tools of Electric and Telecom Plans Solution from ConceptDraw Solution Park. Files created in Visio for Mac app can be easily imported to ConceptDraw PRO. Also you may import stencils and even libraries. Try for free an alternative to Visio that Apple users recommend.
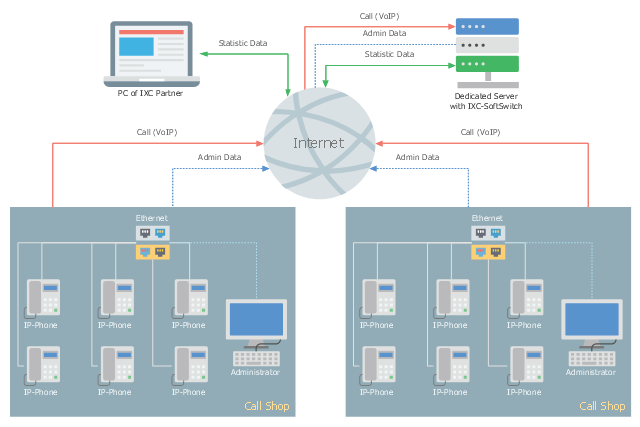
This telecom diagram sample illustrates the call shop solution. It was designed on the base of the Wikimedia Commons file: Call shops.jpg.
[commons.wikimedia.org/ wiki/ File:Call_ shops.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A call shop is a business providing on-site access to telephones for long-distance calling in countries without widespread home long-distance service. Calls may be prepaid or postpaid." [Call shop. Wikipedia]
The telecommunication diagram example "Call shop solution" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
[commons.wikimedia.org/ wiki/ File:Call_ shops.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A call shop is a business providing on-site access to telephones for long-distance calling in countries without widespread home long-distance service. Calls may be prepaid or postpaid." [Call shop. Wikipedia]
The telecommunication diagram example "Call shop solution" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
- Computer Security Program
- Computer Worm Diagram
- Computer Communication Diagram
- Internet Connectivity. Computer and Network Examples | Mobile ...
- Computer Network Diagrams | Telecommunication Network ...
- Example Sa Local Area Nrtwork
- Diagram Of Firewall Computer
- Red IPTV server | Mobile TV Web-based network diagram | Red ...
- Campus Area Networks (CAN). Computer and Network Examples ...
- Home area networks (HAN). Computer and Network Examples ...
- Hierarchical Network Topology | Venn Diagram Examples for ...
- Network Diagram Examples | Network Drawing Software | Tree ...
- EPN Frame-Relay and Dial-up Network. Computer and Network ...
- Cloud Computing diagram | Cloud applications | Mobile cloud ...
- Network Diagram Software Home Area Network | Enterprise private ...
- Mobile cloud architecture diagram | Grid computing system ...
- Computer Security Hardware
- Mobile cloud architecture diagram | Computers and ...
- Computers - Vector stencils library | Rack diagrams - Vector stencils ...
- Network Diagram Software Enterprise Private Network | Enterprise ...



---active-directory-network-diagram.png--diagram-flowchart-example.png)