ConceptDraw Arrows10 Technology
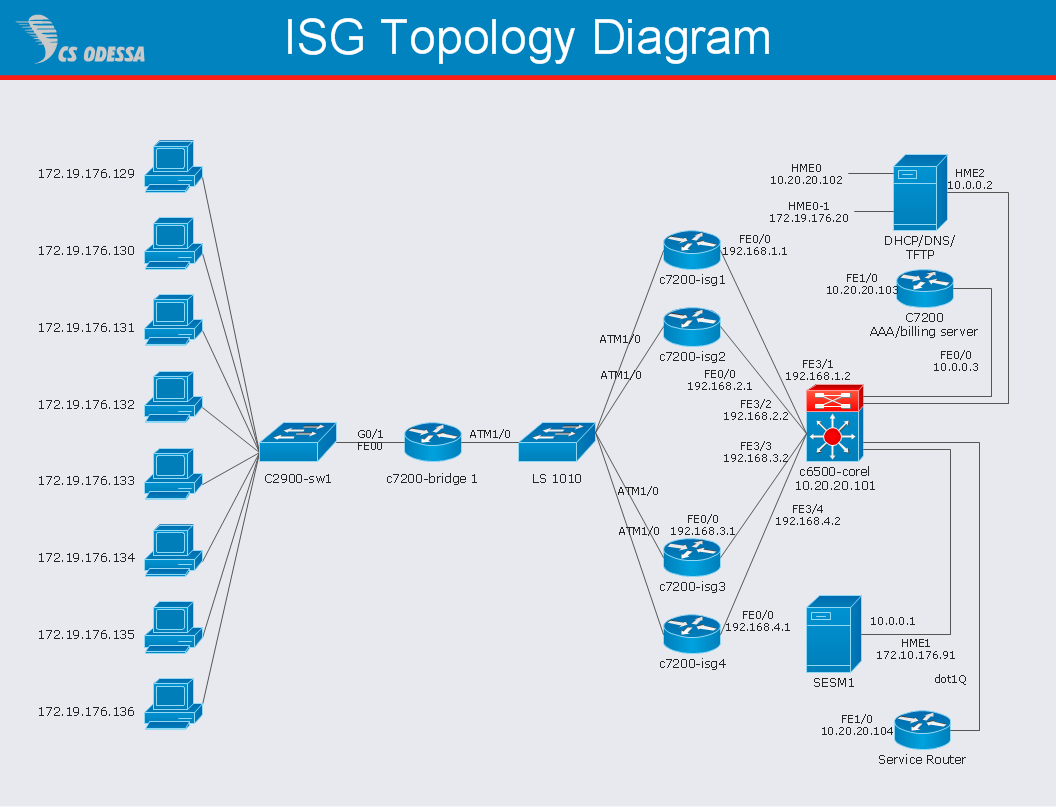
When you are connecting existing objects you can control the diagram structure by changing selection order. This is how diagramming software should work. You are able to draw a diagram as quickly as the ideas come to you.Network Diagram Software ISG Network Diagram
Drawing ISG Network Diagram using ConceptDraw PRO stencils
 Bubble Diagrams
Bubble Diagrams
Bubble diagrams have enjoyed great success in software engineering, architecture, economics, medicine, landscape design, scientific and educational process, for ideas organization during brainstorming, for making business illustrations, presentations, planning, design, and strategy development. They are popular because of their simplicity and their powerful visual communication attributes.
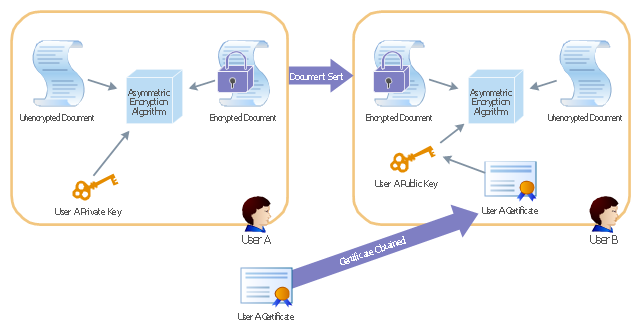
This AD diagram example was redesigned from the picture "Asymmetric
encryption" from the book "Active Directory for Dummies".
"Asymmetric Encryption:
This scenario uses a public and private key pair that is associated with each other. With this type of encryption, one of the keys is used to encrypt the data in such a way that only the corresponding second key is capable of decrypting the information. ...
In asymmetric encryption, two different keys are involved in the process: one for encrypting the document and a different but related key for decrypting the document. The two keys are generated at the same time so that if a document is encrypted with one of the keys, only the second related key can decrypt the document. ... Typically, these keys are referred to as a private key and a public key. A private key is one that is generated for a particular user and is never shared with any other user or computer. A public key is typically one of the pieces of data that’s stored in a PKI certificate. Although this type of encryption creates a very secure way of sharing data, an added benefit is you knowing that a piece of data decrypted by using a particular user’s public key must have come from that user because no other user would have the private key the document was encrypted with."
[Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Asymmetric encryption" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
encryption" from the book "Active Directory for Dummies".
"Asymmetric Encryption:
This scenario uses a public and private key pair that is associated with each other. With this type of encryption, one of the keys is used to encrypt the data in such a way that only the corresponding second key is capable of decrypting the information. ...
In asymmetric encryption, two different keys are involved in the process: one for encrypting the document and a different but related key for decrypting the document. The two keys are generated at the same time so that if a document is encrypted with one of the keys, only the second related key can decrypt the document. ... Typically, these keys are referred to as a private key and a public key. A private key is one that is generated for a particular user and is never shared with any other user or computer. A public key is typically one of the pieces of data that’s stored in a PKI certificate. Although this type of encryption creates a very secure way of sharing data, an added benefit is you knowing that a piece of data decrypted by using a particular user’s public key must have come from that user because no other user would have the private key the document was encrypted with."
[Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Asymmetric encryption" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
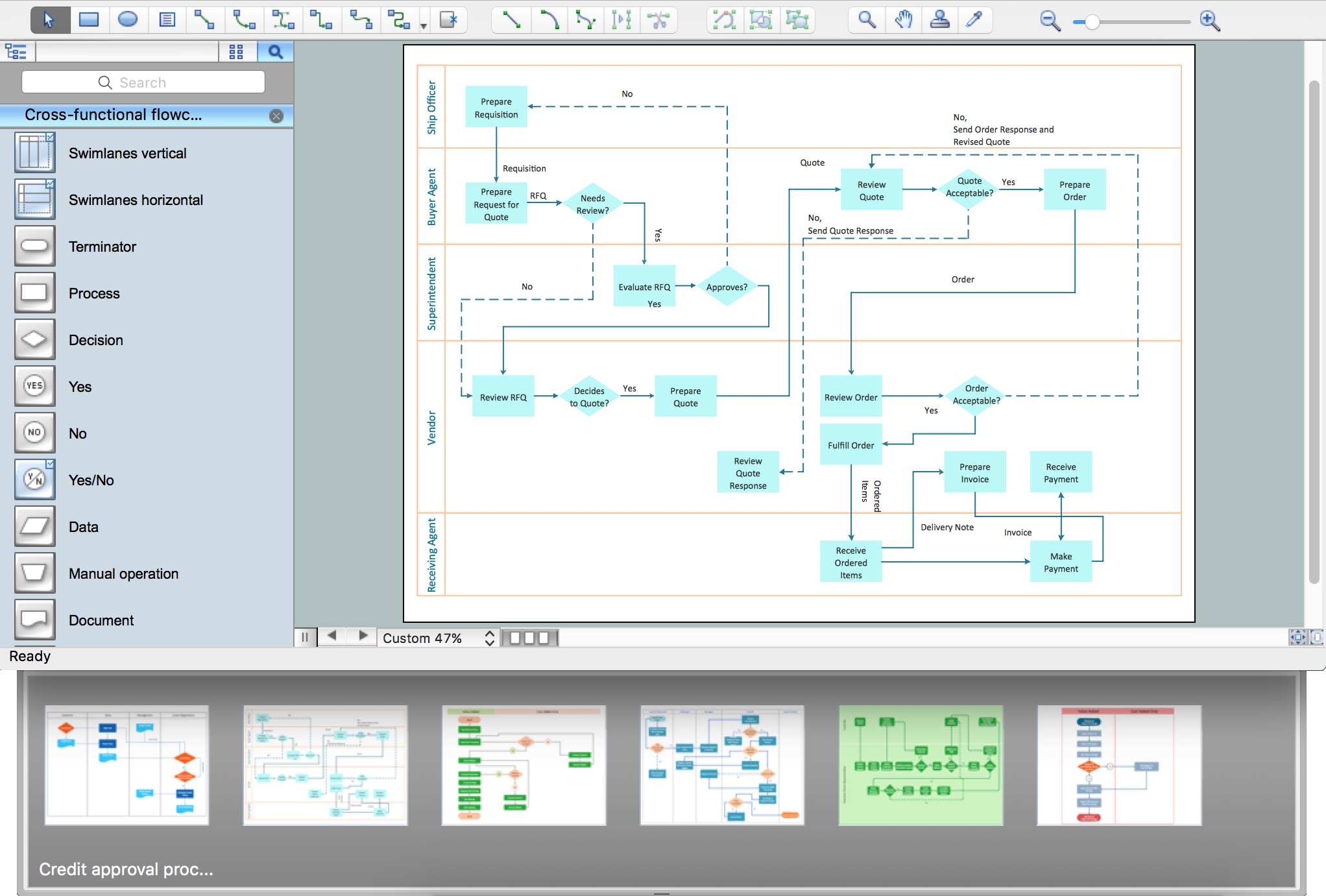
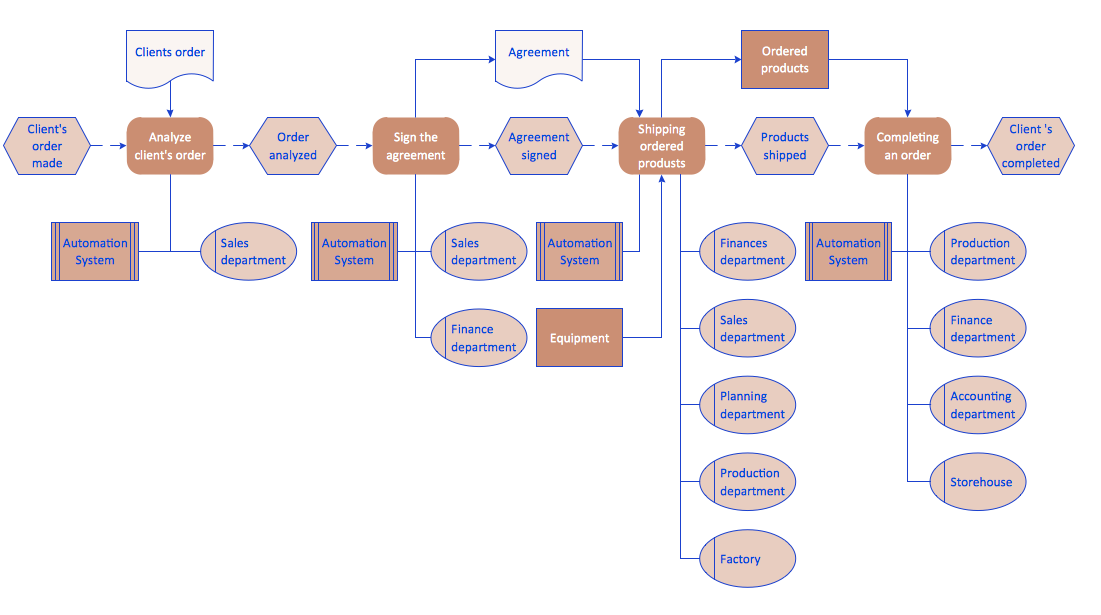
Process Flowchart
The main reason of using Process Flowchart or PFD is to show relations between major parts of the system. Process Flowcharts are used in process engineering and chemical industry where there is a requirement of depicting relationships between major components only and not include minor parts. Process Flowcharts for single unit or multiple units differ in their structure and implementation. ConceptDraw PRO is Professional business process mapping software for making Process flowcharts, Process flow diagram, Workflow diagram, flowcharts and technical illustrations for business documents and also comprehensive visio for mac application. Easier define and document basic work and data flows, financial, production and quality management processes to increase efficiency of your business with ConcepDraw PRO. Business process mapping software with Flowchart Maker ConceptDraw PRO includes extensive drawing tools, rich examples and templates, process flowchart symbols and shape libraries, smart connectors that allow you create the flowcharts of complex processes, process flow diagrams, procedures and information exchange. Process Flowchart Solution is project management workflow tools which is part ConceptDraw Project marketing project management software. Drawing charts, diagrams, and network layouts has long been the monopoly of Microsoft Visio, making Mac users to struggle when needing such visio alternative like visio for mac, it requires only to view features, make a minor edit to, or print a diagram or chart. Thankfully to MS Visio alternative like ConceptDraw PRO software, this is cross-platform charting and business process management tool, now visio alternative for making sort of visio diagram is not a problem anymore however many people still name it business process visio tools.
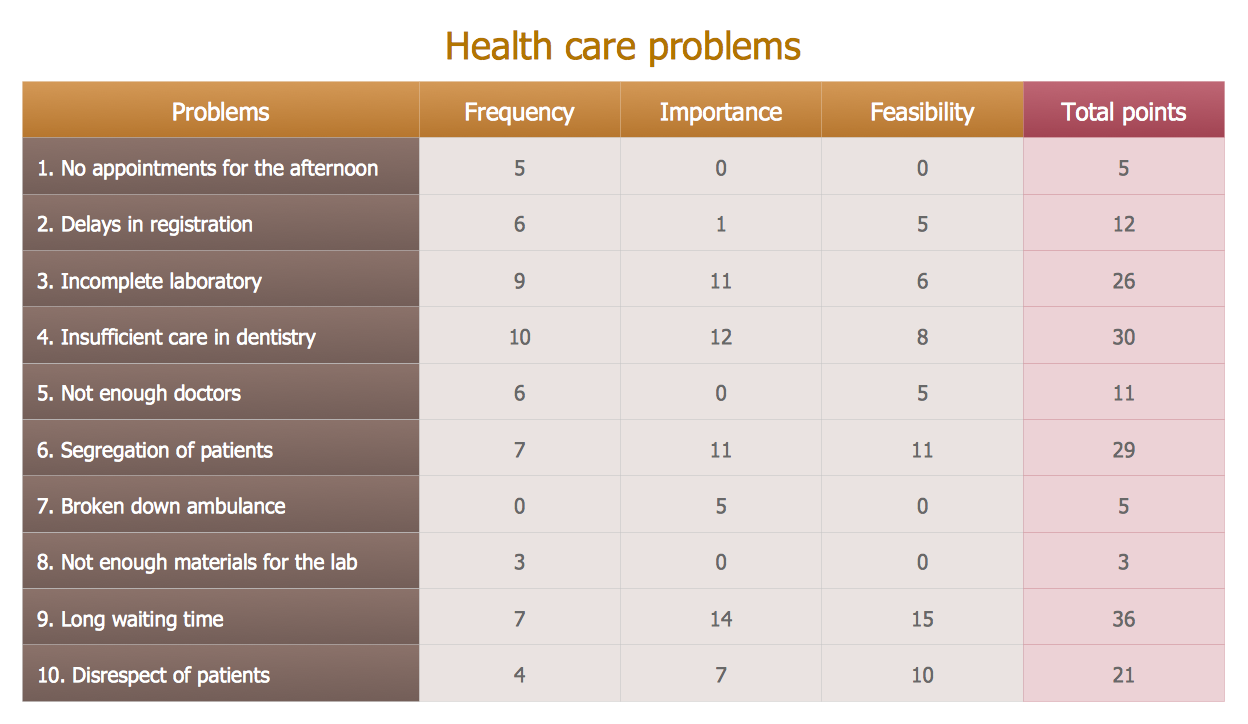
Prioritization Matrix
You can design the Prioritization Matrix by hand on the paper, but we offer you the most easier way - to use the ConceptDraw PRO diagramming and vector drawing software extended with Seven Management and Planning Tools Solution from the Management Area.This example was drawn on the base of the Figure 2 illustrating the "Active Directory FAQ" from the website "Information Management Systems & Services" (IMSS) of the California Institute of Technology (Caltech) campus. [imss.caltech.edu/ node/ 412]
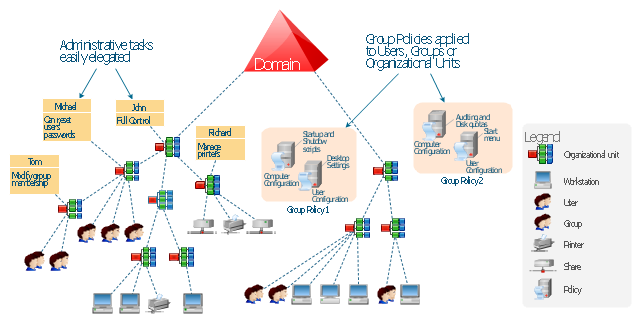
"By using the Active Directory® Domain Services (AD DS) server role, you can create a scalable, secure, and manageable infrastructure for user and resource management, and you can provide support for directory-enabled applications, such as Microsoft® Exchange Server. ...
AD DS provides a distributed database that stores and manages information about network resources and application-specific data from directory-enabled applications. Administrators can use AD DS to organize elements of a network, such as users, computers, and other devices, into a hierarchical containment structure. The hierarchical containment structure includes the Active Directory forest, domains in the forest, and organizational units (OUs) in each domain. A server that is running AD DS is called a domain controller." [technet.microsoft.com/ en-us/ library/ 9a5cba91-7153-4265-adda-c70df2321982]
The Active Directory Domain Services diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"By using the Active Directory® Domain Services (AD DS) server role, you can create a scalable, secure, and manageable infrastructure for user and resource management, and you can provide support for directory-enabled applications, such as Microsoft® Exchange Server. ...
AD DS provides a distributed database that stores and manages information about network resources and application-specific data from directory-enabled applications. Administrators can use AD DS to organize elements of a network, such as users, computers, and other devices, into a hierarchical containment structure. The hierarchical containment structure includes the Active Directory forest, domains in the forest, and organizational units (OUs) in each domain. A server that is running AD DS is called a domain controller." [technet.microsoft.com/ en-us/ library/ 9a5cba91-7153-4265-adda-c70df2321982]
The Active Directory Domain Services diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
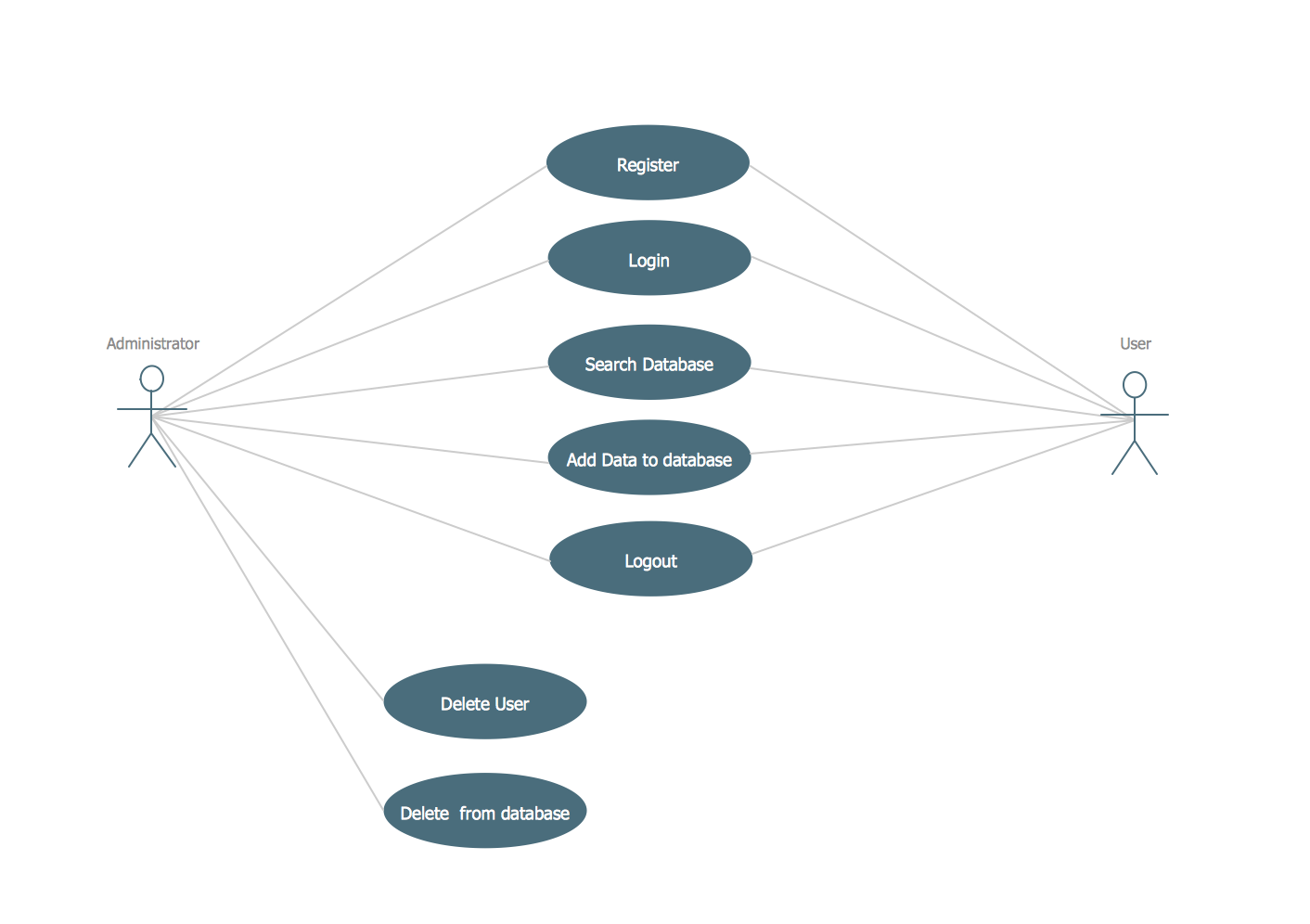
UML Use Case Diagram Example Registration System
This sample was created in ConceptDraw PRO diagramming and vector drawing software using the UML Use Case Diagram library of the Rapid UML Solution from the Software Development area of ConceptDraw Solution Park. This sample shows the types of user’s interactions with the system and is used at the registration and working with the database system.Best Diagramming
Need to draw a diagram, process chart, flowchart, organizational chart, graphic design? ConceptDraw can help you to make professional graphic documents quickly.
EPC Diagrams Illustrate Business Process Work Flows
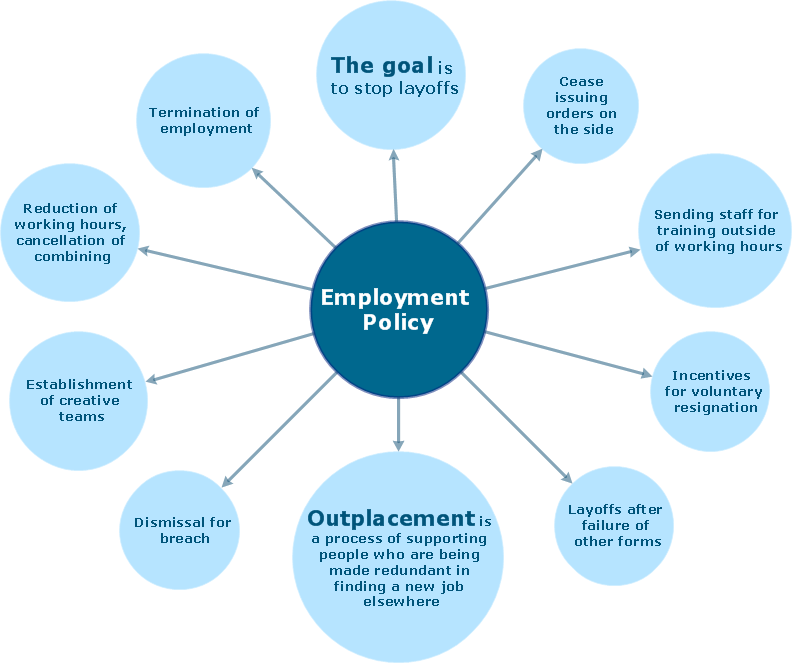
The Event-driven Process Chain ( EPC ) Diagrams allows users present business process models in terms of work flows. The EPC diagram can show various ways for improvement throughout an organisation.- Employment Form Software | Employment policy direction ...
- Examples Of Diagram Of Business Policy
- Process Of Business Policy Through Diagram
- Group Policy Diagram Windows
- Diagram On Business Policy Objective
- Concept Mapping In Business Policy
- Business Policy Diagram
- Business Policy Concept Map
- Active Directory Domain Services diagram | Active Directory ...