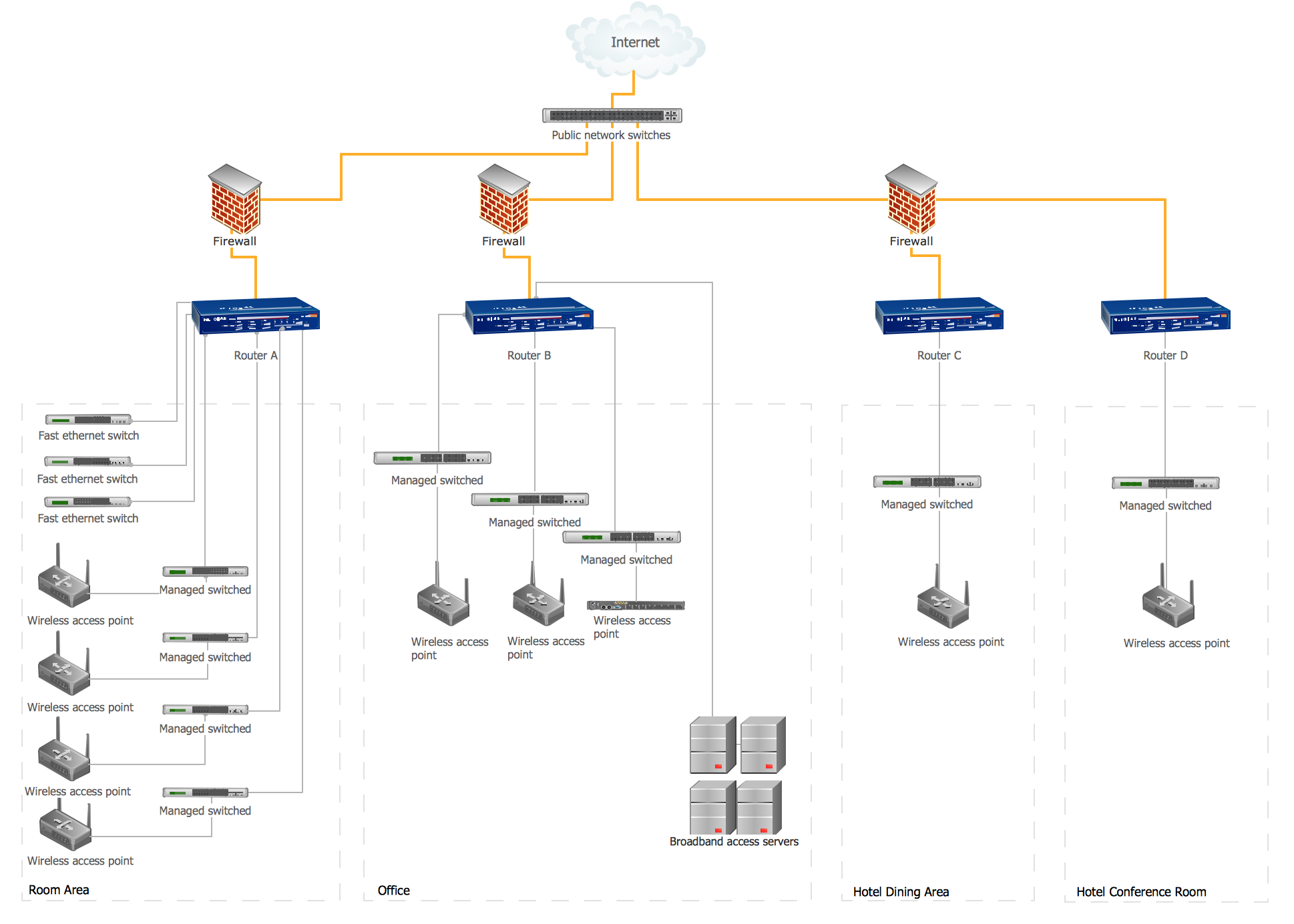
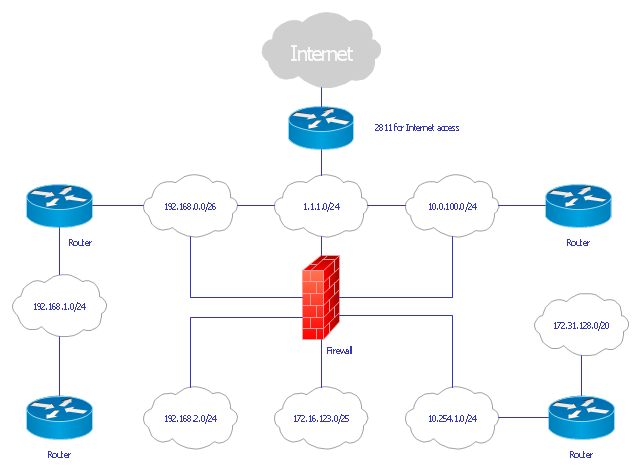
This computer security diagram example was designed on the base of the Wikimedia Commons file: Firewall.png.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
Network Security
The Internet is a giant computer network which connects computers all over the world. It is integral part of human society and business. But the serious question for network engineers, designers, lawmakers and enforcers is the need for protect the Internet networks from the Internet crimes, hacking and attacks. There are quite a number of hardware, software and physical methods of protection against them. The samples you see on this page were created in ConceptDraw DIAGRAM using the tools of Network Security Diagrams Solution for ConceptDraw DIAGRAM software. They show protection networks with Firewalls and other network security devices.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw DIAGRAM software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
Cisco Network Topology. Cisco icons, shapes, stencils and symbols
Cisco Network Topology represents the arrangement of worldwide recognized and standardized Cisco network symbols, icons, shapes, and stencils which help visualize the schemes of computer networks. Any equipment used in Cisco networks is also named a node and network topology diagram represents the scheme of connection the used nodes. Cisco Network Diagram illustrates how the signals enter on the networked devices and how the data spread within a network from one device to another. These diagrams are useful for engineers while constructing computer networks and working with them. Cisco Network Diagrams solution included to Computer and Networks area of ConceptDraw Solution Park contains quick-start templates, professionally designed samples and examples, and numerous libraries with a lot of predesigned vector design elements, icons, and shapes of Cisco equipment, components, devices, links which provide for ConceptDraw DIAGRAM users a perfect possibility of simple and quick drawing Cisco Network Diagrams and Schematics, Network Designs and Maps of any complexity.Network Security Devices
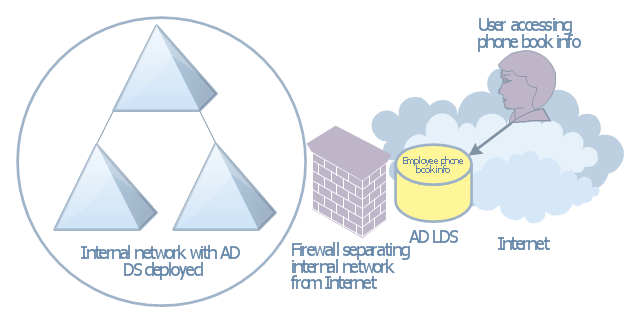
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.This AD diagram example was created based on the picture "AD LDS as a phone book service" from the book "Active Directory for Dummies".
"Directory services are a great way of providing information that can be fre-
quently retrieved and searched on in a hierarchical way. ... Well, there’s no reason that you can’t create a directory service that’s actually a phone book. Imagine that you need to make a searchable phone directory of your organization available on the Internet. ... This isn’t a difficult task, but it has security repercussions. If you’ve already deployed AD DS and you have the employees’ phone numbers available in that directory, it might not be a good idea to expose your AD DS environment to the Internet for security reasons. Using AD LDS is a great alternative because it can be deployed separately from AD DS and it’s designed to simply provide the information retrieval service that you need without the complications involved with Kerberos authentication and group policies." [Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "AD LDS as a phone book service" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"Directory services are a great way of providing information that can be fre-
quently retrieved and searched on in a hierarchical way. ... Well, there’s no reason that you can’t create a directory service that’s actually a phone book. Imagine that you need to make a searchable phone directory of your organization available on the Internet. ... This isn’t a difficult task, but it has security repercussions. If you’ve already deployed AD DS and you have the employees’ phone numbers available in that directory, it might not be a good idea to expose your AD DS environment to the Internet for security reasons. Using AD LDS is a great alternative because it can be deployed separately from AD DS and it’s designed to simply provide the information retrieval service that you need without the complications involved with Kerberos authentication and group policies." [Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "AD LDS as a phone book service" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
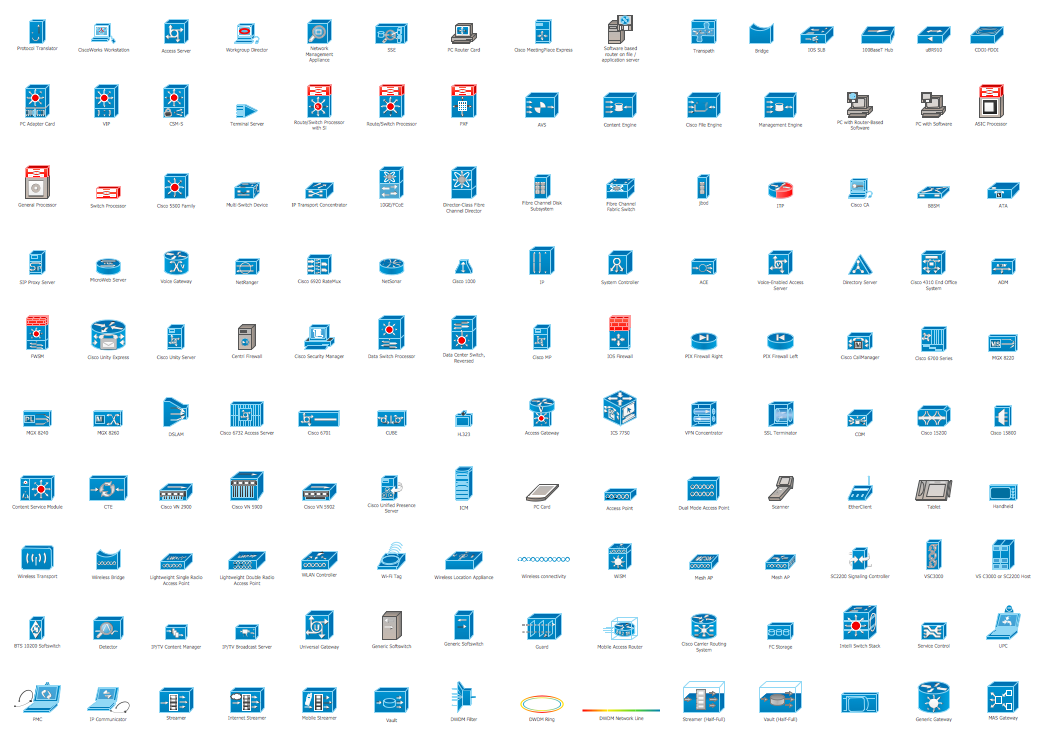
Cisco Products Additional. Cisco icons, shapes, stencils and symbols
The ConceptDraw vector stencils library Cisco Products Additional contains equipment symbols for drawing the computer network diagrams."A computer network or data network is a telecommunications network that allows computers to exchange data. In computer networks, networked computing devices (network nodes) pass data to each other along data connections. The connections (network links) between nodes are established using either cable media or wireless media. The best-known computer network is the Internet.
Network devices that originate, route and terminate the data are called network nodes. Nodes can include hosts such as servers and personal computers, as well as networking hardware. Two devices are said to be networked when a device is able to exchange information with another device." [Computer network. Wikipedia]
This computer communication network diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
Network devices that originate, route and terminate the data are called network nodes. Nodes can include hosts such as servers and personal computers, as well as networking hardware. Two devices are said to be networked when a device is able to exchange information with another device." [Computer network. Wikipedia]
This computer communication network diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
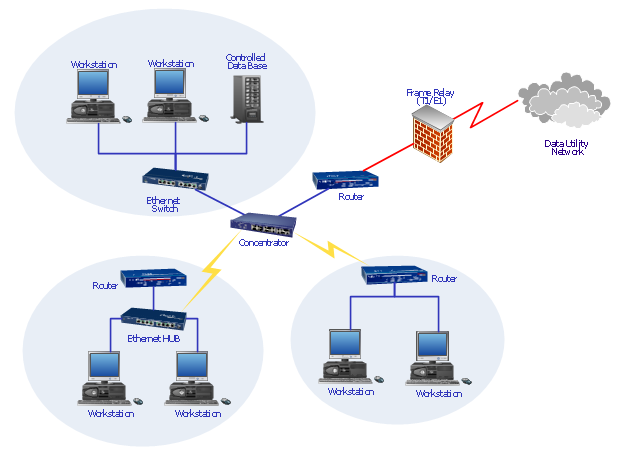
Hotel Network Topology Diagram
Network topology is a layout of various elements of computer network, such as nodes, links, routers, etc. It is a network topological structure which can be depicted logically or physically. Physical topology shows the physical location of network's components and cable connections between network nodes. Logical topology describes the data flows, the circulation of signals in physical topology. The physical and logical topologies for two networks can be identical, while their physical interconnections, the distances between nodes, transmission rates, and/or signal types may be differ. ConceptDraw DIAGRAM with Computer and Networks solution from Computer and Networks area of ConceptDraw Solution Park lets you design physical and logical network topology diagrams for wireless and wired computer communication networks located in various premises, including the hotels. You can easy design Hotel Network Topology Diagram, diagrams depicted LANs and WLANs, and also any of eight basic topologies (Point-to-point, Star, Bus, Mesh, Ring, Tree, Hybrid, Daisy chain).
The vector stencils library "Computer network" contains 51 symbols of computer network devices and equipment for drawing computer network diagrams.
"Network Mapping Software.
A number of software tools exist to design computer network diagrams / or generate visual maps of networks, servers, storage, services, data centers, and other peripherals. Broadly, there are two types of software tools - those that help create diagrams manually and those that generate them using automated / semi-automated approaches.
Type of Software.
(1) Manual - allows users to design and draw logical and physical topology diagrams by manually placing icons and connections.
(2) Automated - generate topology diagrams / maps by traversing the network and automatically discovering resident devices or by importing network data." [Comparison of network diagram software. Wikipedia]
ConceptDraw PRO is the software for manual design of computer network diagrams. The solutions of the Computer and Networks area in ConceptDraw Solution Park extend ConceptDraw PRO with vector stencils libraries, templates and examples for creating the computer network diagrams.
The symbols example "Computer network - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
"Network Mapping Software.
A number of software tools exist to design computer network diagrams / or generate visual maps of networks, servers, storage, services, data centers, and other peripherals. Broadly, there are two types of software tools - those that help create diagrams manually and those that generate them using automated / semi-automated approaches.
Type of Software.
(1) Manual - allows users to design and draw logical and physical topology diagrams by manually placing icons and connections.
(2) Automated - generate topology diagrams / maps by traversing the network and automatically discovering resident devices or by importing network data." [Comparison of network diagram software. Wikipedia]
ConceptDraw PRO is the software for manual design of computer network diagrams. The solutions of the Computer and Networks area in ConceptDraw Solution Park extend ConceptDraw PRO with vector stencils libraries, templates and examples for creating the computer network diagrams.
The symbols example "Computer network - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
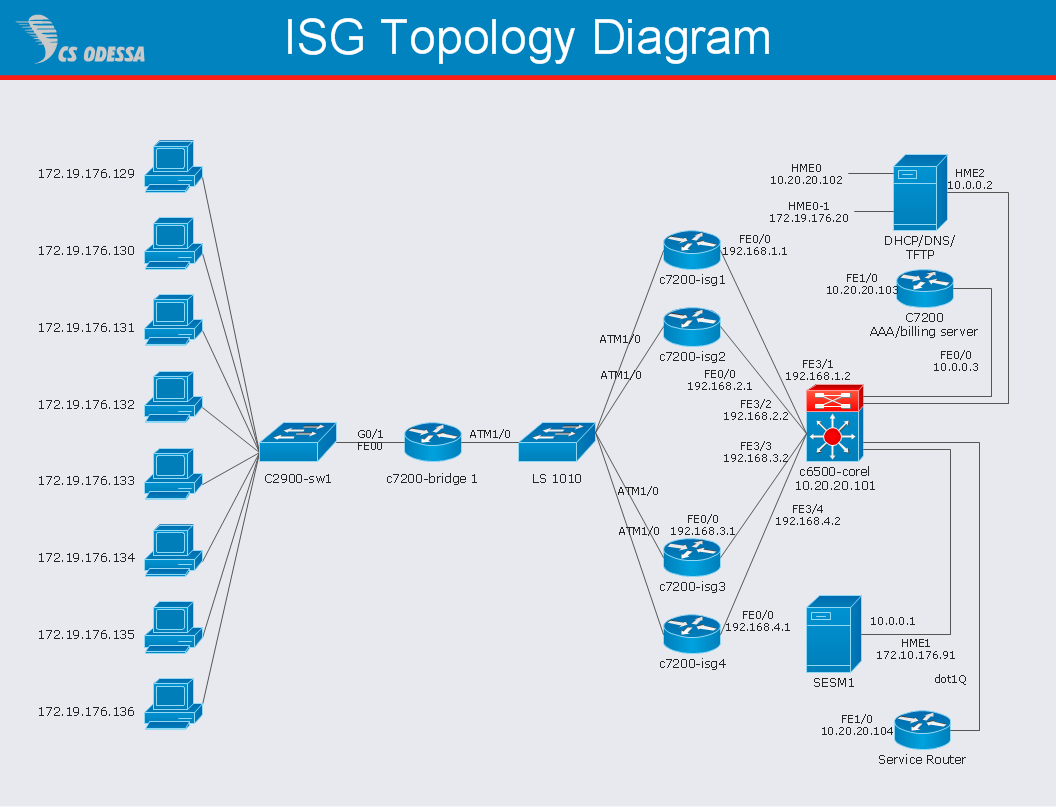
Network Diagram Software ISG Network Diagram
Drawing ISG Network Diagram using ConceptDraw DIAGRAM stencils
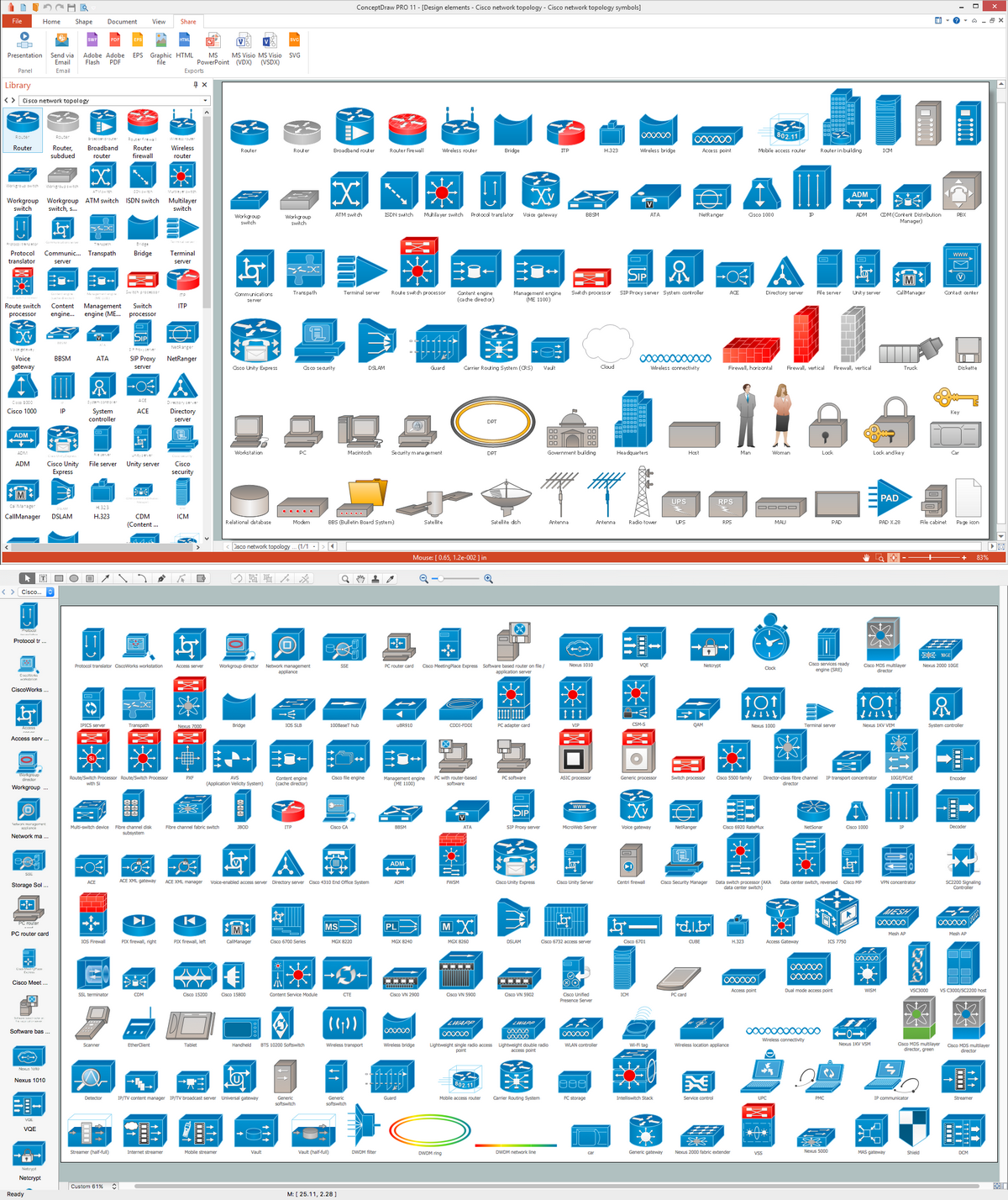
The vector stencils library "Cisco network topology" contains 89 symbols of Cisco network devices and design elements for drawing computer network topology diagrams.
"There are two basic categories of network topologies:
(1) Physical topologies,
(2) Logical topologies.
The shape of the cabling layout used to link devices is called the physical topology of the network. This refers to the layout of cabling, the locations of nodes, and the interconnections between the nodes and the cabling. The physical topology of a network is determined by the capabilities of the network access devices and media, the level of control or fault tolerance desired, and the cost associated with cabling or telecommunications circuits.
The logical topology in contrast, is the way that the signals act on the network media, or the way that the data passes through the network from one device to the next without regard to the physical interconnection of the devices." [Network topology. Wikipedia]
The symbols example "Cisco network topology - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"There are two basic categories of network topologies:
(1) Physical topologies,
(2) Logical topologies.
The shape of the cabling layout used to link devices is called the physical topology of the network. This refers to the layout of cabling, the locations of nodes, and the interconnections between the nodes and the cabling. The physical topology of a network is determined by the capabilities of the network access devices and media, the level of control or fault tolerance desired, and the cost associated with cabling or telecommunications circuits.
The logical topology in contrast, is the way that the signals act on the network media, or the way that the data passes through the network from one device to the next without regard to the physical interconnection of the devices." [Network topology. Wikipedia]
The symbols example "Cisco network topology - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"... logical topology shows how data flows within a network, regardless of its physical design. ...
... mapping the data flow between the components determines the logical topology of the network." [Network topology. Wikipedia]
"In a shared media topology, all the systems have the ability to access the physical layout whenever they need it. The main advantage in a shared media topology is that the systems have unrestricted access to the physical media. Of course, the main disadvantage to this topology is collisions. If two systems send information out on the wire at the same time, the packets collide and kill both packets. Ethernet is an example of a shared media topology. ...
The token-based topology works by using a token to provide access to the physical media. In a token-based network, there is a token that travels around the network. When a system needs to send out packets, it grabs the token off of the wire, attaches it to the packets that are sent, and sends it back out on the wire. As the token travels around the network, each system examines the token. When the packets arrive at the destination systems, those systems copy the information off of the wire and the token continues its journey until it gets back to the sender. When the sender receives the token back, it pulls the token off of the wire and sends out a new empty token to be used by the next machine." [Logical topology. Wikipedia]
This Cisco logical computer network diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
... mapping the data flow between the components determines the logical topology of the network." [Network topology. Wikipedia]
"In a shared media topology, all the systems have the ability to access the physical layout whenever they need it. The main advantage in a shared media topology is that the systems have unrestricted access to the physical media. Of course, the main disadvantage to this topology is collisions. If two systems send information out on the wire at the same time, the packets collide and kill both packets. Ethernet is an example of a shared media topology. ...
The token-based topology works by using a token to provide access to the physical media. In a token-based network, there is a token that travels around the network. When a system needs to send out packets, it grabs the token off of the wire, attaches it to the packets that are sent, and sends it back out on the wire. As the token travels around the network, each system examines the token. When the packets arrive at the destination systems, those systems copy the information off of the wire and the token continues its journey until it gets back to the sender. When the sender receives the token back, it pulls the token off of the wire and sends out a new empty token to be used by the next machine." [Logical topology. Wikipedia]
This Cisco logical computer network diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Cisco Routers. Cisco icons, shapes, stencils and symbols
Network infrastructure planning is a very important process in the network construction, and the share of time allocated to this within the scope of the entire project may reach 60-80%. A competent and thorough approach to planning contributes to the quick investment return, and also increases the reliability and flexibility of the final system, reducing the probability of additional costs related to the incorrect implementation. Any planning begins with an analysis of the business requirements to the final system. Basic network parameters, which should be assessed are the scalability, accessibility, cost, speed and safety. Speed and cost are often mistaken for the most important parameters, and the rest of the parameters aren't even remembered. This is not entirely correct. Initially, it is necessary to assess the business plans for the future, because sometimes it is more profitable to invest more money in the beginning. If the business is to develop, then, consequently, demands onThe vector stencils library "Internet symbols" contains 11 Internet clipart images and symbols for drawing computer network diagrams.
The clip art example "Internet symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
The clip art example "Internet symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
- Firewall between LAN and WAN | Hotel Network Topology Diagram ...
- Firewall between LAN and WAN | Network Security Diagrams ...
- Internet symbols - Vector stencils library | Firewall between LAN and ...
- Firewall Diagram Ppt
- Firewall between LAN and WAN | Hotel Network Topology Diagram ...
- Draw The Diagram Of Firewall Subject Computer
- Fishbone Diagram For Firewall
- Firewall between LAN and WAN | Network diagrams with ...
- Diagram Of Firewall
- Network Diagram Cloud Firewall Workstation Switch Server
- Network Gateway Router | Communication network diagram ...
- Communication network diagram | Network Glossary Definition ...
- Use Of A Hardware Firewall With A Diagram
- Hotel Network Topology Diagram | Star Network Topology | Wireless ...
- Internet symbols - Vector stencils library | UML activity diagram ...
- Fully Connected Network Topology Diagram | Virtual networks ...
- Firewall between LAN and WAN | Australia Map | Tree and Forest ...
- Basic Network Diagram With Firewall
- Network Diagram With Router And Firewall
- Router Firewall Switch Diagram
























































-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)














-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)



-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)











-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)








-internet-symbols---vector-stencils-library.png--diagram-flowchart-example.png)