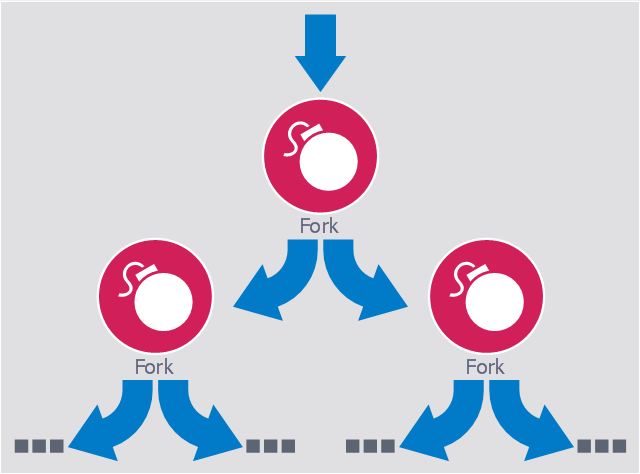
This computer security diagram example was designed on the base of the Wikimedia Commons file: Fork bomb.svg.
"Fork bomb principle. The processes are recursively forked, resulting in a saturation of the available ressources and denial of service." [commons.wikimedia.org/ wiki/ File:Fork_ bomb.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a fork bomb (also called rabbit virus or wabbit) is a denial-of-service attack wherein a process continually replicates itself to deplete available system resources, slowing down or crashing the system due to resource starvation. ...
Fork bombs operate both by consuming CPU time in the process of forking, and by saturating the operating system's process table. A basic implementation of a fork bomb is an infinite loop that repeatedly launches the same process." [Fork bomb. Wikipedia]
The cybersecurity diagram example "Fork bomb" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Fork bomb principle. The processes are recursively forked, resulting in a saturation of the available ressources and denial of service." [commons.wikimedia.org/ wiki/ File:Fork_ bomb.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a fork bomb (also called rabbit virus or wabbit) is a denial-of-service attack wherein a process continually replicates itself to deplete available system resources, slowing down or crashing the system due to resource starvation. ...
Fork bombs operate both by consuming CPU time in the process of forking, and by saturating the operating system's process table. A basic implementation of a fork bomb is an infinite loop that repeatedly launches the same process." [Fork bomb. Wikipedia]
The cybersecurity diagram example "Fork bomb" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
IT Security Solutions
Dynamic of development computer and network technologies increases the need in modern cyber security strategies and IT security solutions to support security of your data, to ensure data privacy, and to protect your operations from the cyber threats. Thanks to the Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park, the ConceptDraw PRO diagramming and vector drawing software is one of the unique IT security solutions for professional designing Network Security Diagrams.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution enhances the ConceptDraw PRO v10 functionality with large collection of predesigned vector stencils of cybersecurity clipart, shapes, icons and connectors to help you succeed in designing professional and accurate Ne
- Fork bomb | Concept Maps | Block Forked Arrow
- Network Security Diagrams | Daisy Chain Network Topology | Fork ...
- Network Security Diagrams | Network Security | Network Security ...
- Recommended network architecture for BlackBerry SWS | Firewall ...
- Fork Arrows
- Example Flowchart Fork
- IT Security Solutions | Network Security Diagrams | Safety and ...
- Network Security Diagrams | ConceptDraw Solution Park | Network ...
- Cyber Security Degrees | Cisco Security. Cisco icons, shapes ...
- Cyber Security Degrees | Network Security Diagrams | IT Security ...
- Network Security Devices | Network Security Tips | IT Security ...
- Computers and network isometric - Vector stencils library ...