Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution enhances the ConceptDraw PRO v10 functionality with large collection of predesigned vector stencils of cybersecurity clipart, shapes, icons and connectors to help you succeed in designing professional and accurate Ne
Network Security Model
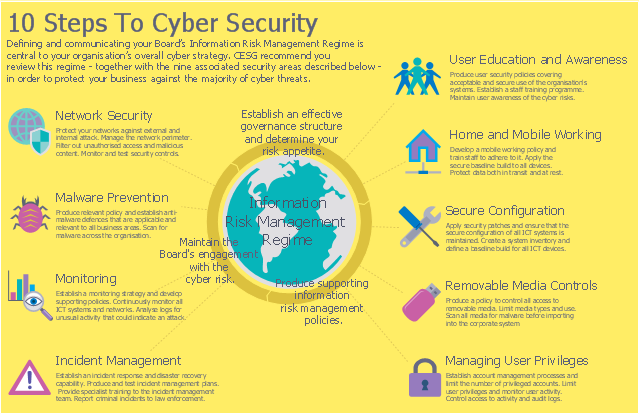
Creation of well thought-out network security model will effectively help you in realization your network's security. ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park lets fast and easy design all variety of network security models: Open network security model, Closed network security model, Restrictive network access model.- 10 Steps to Cyber Security | Network Security Diagrams | Network ...
- Cyber Security Degrees | 10 Steps to Cyber Security | Network ...
- Network Security Diagrams | Network Security Devices ...
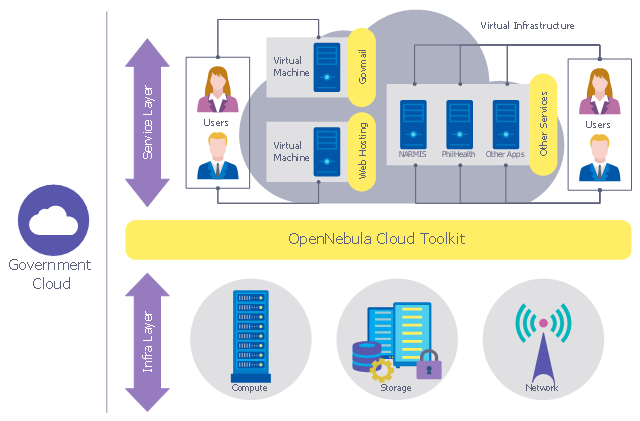
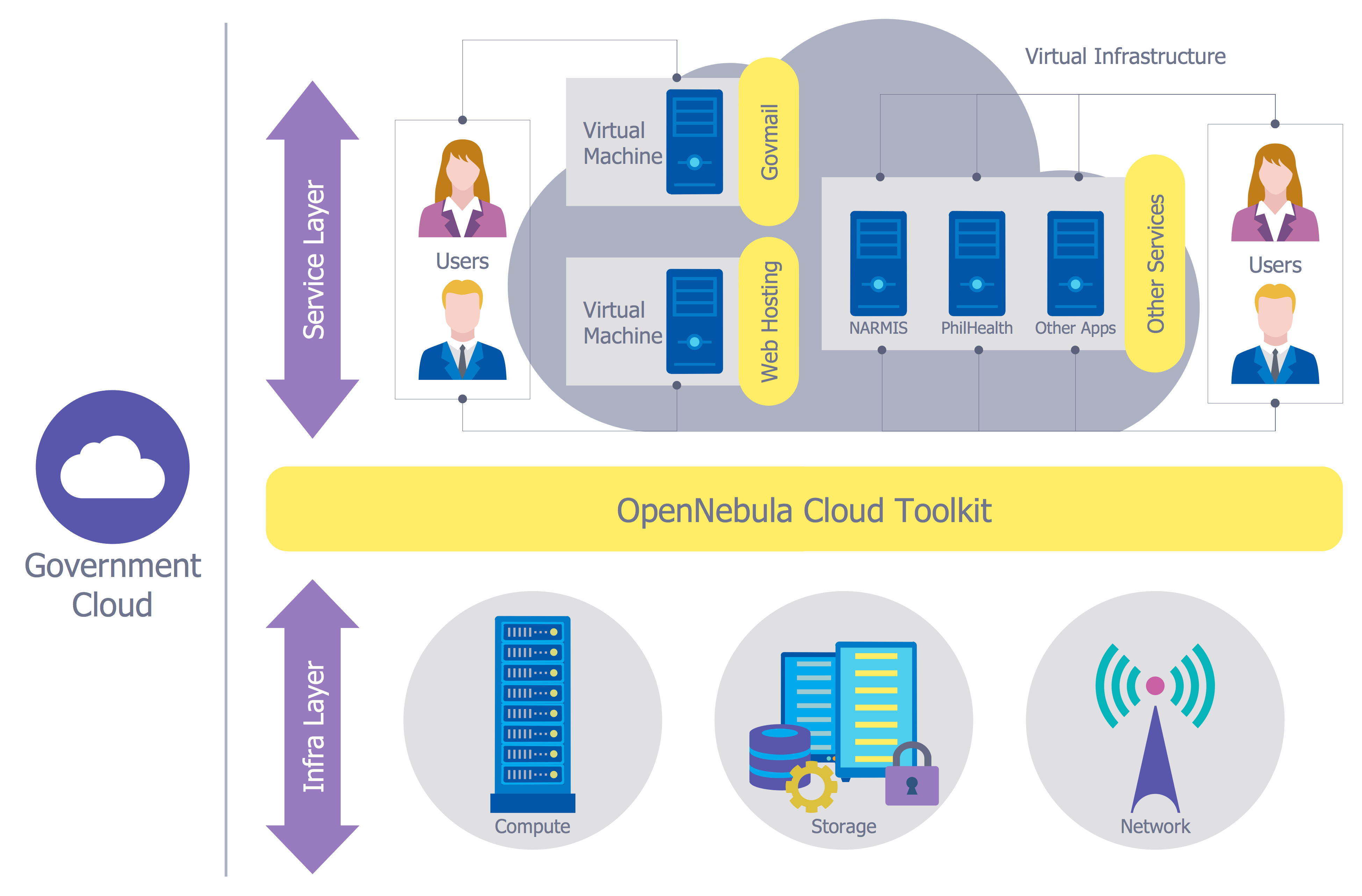
- Government Cloud | Network Security Diagrams | Network Security ...
- Design elements - Cybersecurity connectors | Cyber Security ...
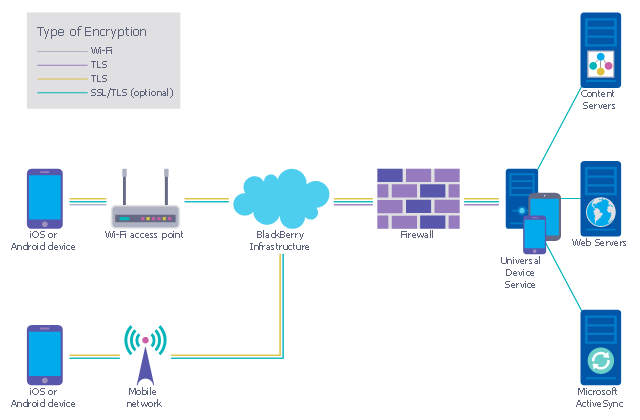
- Recommended network architecture for BlackBerry SWS | Network ...
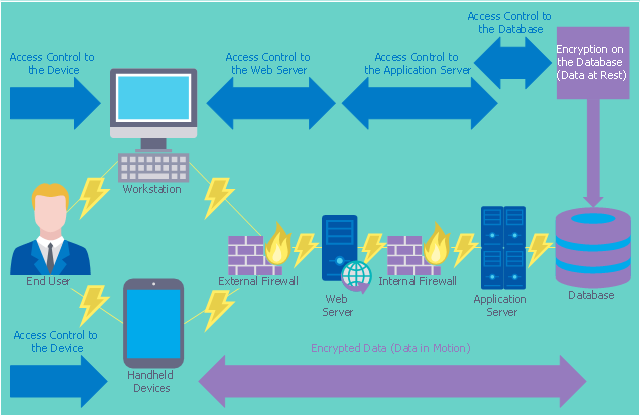
- Access control and encryption
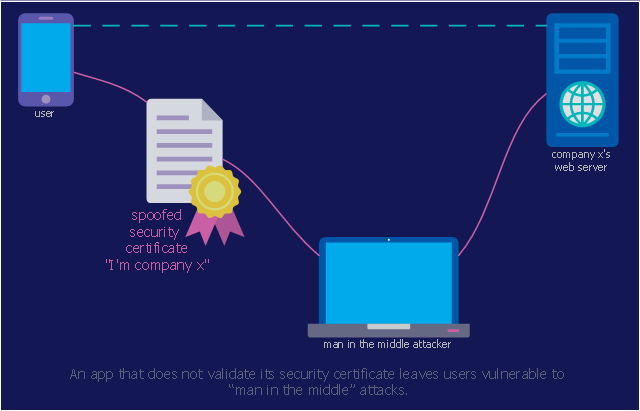
- Mobile app security | Network Security Diagrams | IT Security ...
- Design elements - Cybersecurity round icons | Cyber Security ...
- Design elements - Cybersecurity shapes | Cyber Security Degrees ...
- Network Security Devices | Network Security | Network Security ...
- Health IT dashboard | EPC IT Solutions | NIH IT enterprise ...
- How to Create a Network Security Diagram Using ConceptDraw ...
- Data Flow Diagram For Online News
- Network Security Model | Network Security | Secure Wireless ...
- Network Security . Computer and Network Examples | Cisco security ...
- Wide area network (WAN) topology. Computer and Network ...
- Intelligence analyst cycle - Arrow loop diagram | The Circular Flow ...