Introduction to Cloud Computing Architecture
The best way to visualize the introduction to Cloud computing architecture is to create diagrams and schematics representing what is a cloud computing and how it works. For their design, we recommend to use a powerful ConceptDraw DIAGRAM diagramming and vector drawing software supplied with Cloud Computing Diagrams solution from the Computers and Network area of ConceptDraw Solution ParkThis Azure cloud architecture pattern diagram template was created on the base of figure in the article "External Configuration Store Pattern" from the Microsoft Developer Network (MSDN) website.
"External Configuration Store Pattern.
Move configuration information out of the application deployment package to a centralized location. This pattern can provide opportunities for easier management and control of configuration data, and for sharing configuration data across applications and application instances. ...
The majority of application runtime environments include configuration information that is held in files deployed with the application, located within the application folders. In some cases it is possible to edit these files to change the behavior of the application after it has been deployed. However, in many cases, changes to the configuration require the application to be redeployed, resulting in unacceptable downtime and additional administrative overhead. ...
Store the configuration information in external storage, and provide an interface that can be used to quickly and efficiently read and update configuration settings. The type of external store depends on the hosting and runtime environment of the application. In a cloud-hosted scenario it is typically a cloud-based storage service, but could be a hosted database or other system.
The backing store chosen for configuration information should be fronted by a suitable interface that provides consistent and easy to use access in a controlled way that enables reuse. Ideally, it should expose the information in a correctly typed and structured format. The implementation may also need to authorize users’ access in order to protect configuration data, and be flexible enough to allow multiple versions of the configuration (such as development, staging, or production, and multiple release versions of each one) to be stored." [msdn.microsoft.com/ ru-RU/ library/ dn589803.aspx]
The Azure cloud system architecture diagram template "External Configuration Store Pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
"External Configuration Store Pattern.
Move configuration information out of the application deployment package to a centralized location. This pattern can provide opportunities for easier management and control of configuration data, and for sharing configuration data across applications and application instances. ...
The majority of application runtime environments include configuration information that is held in files deployed with the application, located within the application folders. In some cases it is possible to edit these files to change the behavior of the application after it has been deployed. However, in many cases, changes to the configuration require the application to be redeployed, resulting in unacceptable downtime and additional administrative overhead. ...
Store the configuration information in external storage, and provide an interface that can be used to quickly and efficiently read and update configuration settings. The type of external store depends on the hosting and runtime environment of the application. In a cloud-hosted scenario it is typically a cloud-based storage service, but could be a hosted database or other system.
The backing store chosen for configuration information should be fronted by a suitable interface that provides consistent and easy to use access in a controlled way that enables reuse. Ideally, it should expose the information in a correctly typed and structured format. The implementation may also need to authorize users’ access in order to protect configuration data, and be flexible enough to allow multiple versions of the configuration (such as development, staging, or production, and multiple release versions of each one) to be stored." [msdn.microsoft.com/ ru-RU/ library/ dn589803.aspx]
The Azure cloud system architecture diagram template "External Configuration Store Pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
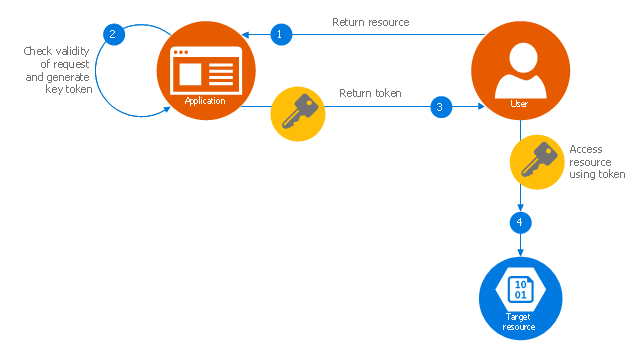
This Azure cloud architecture pattern diagram template was created on the base of figure in the article "Valet Key Pattern" from the Microsoft Developer Network (MSDN) website.
"Valet Key Pattern.
Use a token or key that provides clients with restricted direct access to a specific resource or service in order to offload data transfer operations from the application code. This pattern is particularly useful in applications that use cloud-hosted storage systems or queues, and can minimize cost and maximize scalability and performance. ...
Client programs and web browsers often need to read and write files or data streams to and from an application’s storage. ...
Data stores have the capability to handle upload and download of data directly, without requiring the application to perform any processing to move this data, but this typically requires the client to have access to the security credentials for the store.
... applications must be able to securely control access to data in a granular way, but still reduce the load on the server by setting up this connection and then allowing the client to communicate directly with the data store to perform the required read or write operations. ...
To resolve the problem of controlling access to a data store where the store itself cannot manage authentication and authorization of clients, one typical solution is to restrict access to the data store’s public connection and provide the client with a key or token that the data store itself can validate.
This key or token is usually referred to as a valet key. It provides time-limited access to specific resources and allows only predefined operations such as reading and writing to storage or queues, or uploading and downloading in a web browser. Applications can create and issue valet keys to client devices and web browsers quickly and easily, allowing clients to perform the required operations without requiring the application to directly handle the data transfer. This removes the processing overhead, and the consequent impact on performance and scalability, from the application and the server." [msdn.microsoft.com/ ru-RU/ library/ dn568102.aspx]
The Azure cloud system architecture diagram template "Valet key pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
"Valet Key Pattern.
Use a token or key that provides clients with restricted direct access to a specific resource or service in order to offload data transfer operations from the application code. This pattern is particularly useful in applications that use cloud-hosted storage systems or queues, and can minimize cost and maximize scalability and performance. ...
Client programs and web browsers often need to read and write files or data streams to and from an application’s storage. ...
Data stores have the capability to handle upload and download of data directly, without requiring the application to perform any processing to move this data, but this typically requires the client to have access to the security credentials for the store.
... applications must be able to securely control access to data in a granular way, but still reduce the load on the server by setting up this connection and then allowing the client to communicate directly with the data store to perform the required read or write operations. ...
To resolve the problem of controlling access to a data store where the store itself cannot manage authentication and authorization of clients, one typical solution is to restrict access to the data store’s public connection and provide the client with a key or token that the data store itself can validate.
This key or token is usually referred to as a valet key. It provides time-limited access to specific resources and allows only predefined operations such as reading and writing to storage or queues, or uploading and downloading in a web browser. Applications can create and issue valet keys to client devices and web browsers quickly and easily, allowing clients to perform the required operations without requiring the application to directly handle the data transfer. This removes the processing overhead, and the consequent impact on performance and scalability, from the application and the server." [msdn.microsoft.com/ ru-RU/ library/ dn568102.aspx]
The Azure cloud system architecture diagram template "Valet key pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
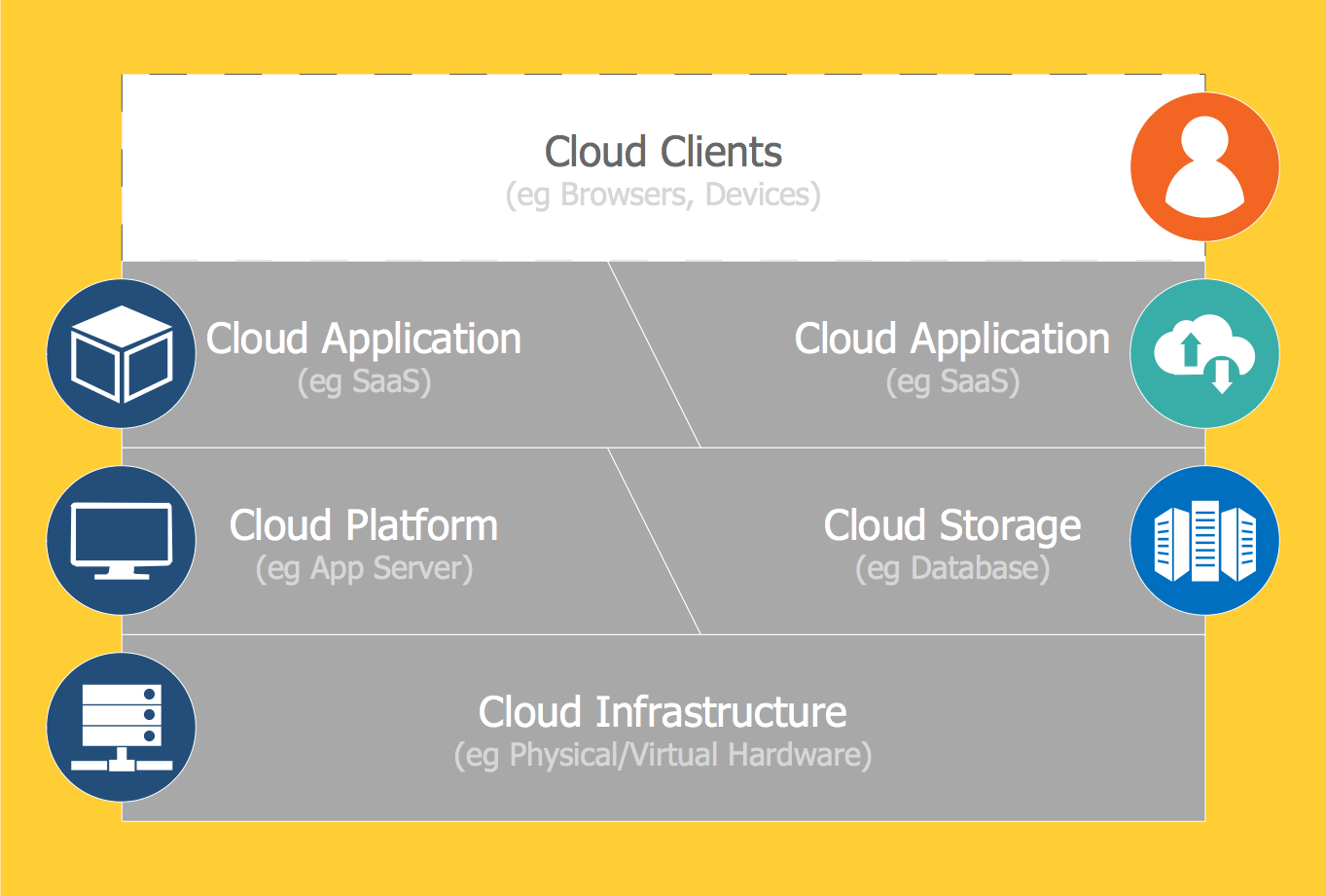
"In computer networking, cloud computing is computing that involves a large number of computers connected through a communication network such as the Internet, similar to utility computing. ...
Network-based services, which appear to be provided by real server hardware, and are in fact served up by virtual hardware, simulated by software running on one or more real machines are often called cloud computing. Such virtual servers do not physically exist and can therefore be moved around and scaled up or down on the fly without affecting the end user, somewhat like a cloud becoming larger or smaller without being a physical object. ...
Typically, the seller has actual energy-consuming servers which host products and services from a remote location, so end-users don't have to; they can simply log on to the network without installing anything. The major models of cloud computing service are known as software as a service, platform as a service, and infrastructure as a service. These cloud services may be offered in a public, private or hybrid network. Google, Amazon,leadsquared.com, Oracle Cloud, Salesforce, Zoho, Access2MyPC, and Microsoft Azure are some well-known cloud vendors." [Cloud computing. Wikipedia]
The AWS architecture diagram example "2-Tier Auto-scalable Web Application Architecture in 1 AZ" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Network-based services, which appear to be provided by real server hardware, and are in fact served up by virtual hardware, simulated by software running on one or more real machines are often called cloud computing. Such virtual servers do not physically exist and can therefore be moved around and scaled up or down on the fly without affecting the end user, somewhat like a cloud becoming larger or smaller without being a physical object. ...
Typically, the seller has actual energy-consuming servers which host products and services from a remote location, so end-users don't have to; they can simply log on to the network without installing anything. The major models of cloud computing service are known as software as a service, platform as a service, and infrastructure as a service. These cloud services may be offered in a public, private or hybrid network. Google, Amazon,leadsquared.com, Oracle Cloud, Salesforce, Zoho, Access2MyPC, and Microsoft Azure are some well-known cloud vendors." [Cloud computing. Wikipedia]
The AWS architecture diagram example "2-Tier Auto-scalable Web Application Architecture in 1 AZ" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
 Astronomy
Astronomy
Astronomy solution extends ConceptDraw DIAGRAM software with illustration and sketching software with templates, samples and libraries of a variety of astronomy symbols, including constellations, galaxies, stars, and planet vector shapes; a whole host of cele
The vector stencils library "AWS Compute and Networking" contains 23 Amazon Web Services compute and networking icons: Amazon Elastic Compute Cloud symbols, Amazon Virtual Private Cloud symbols, Amazom Route 53 symbols, Elastic Load Balancing symbol, AWS Direct Connect symbol, Auto Scaling symbol, Elastic Network Instance symbol. Use it to draw AWS architecture diagrams of your cloud service. The symbols example "AWS Compute and Networking - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Network Topologies
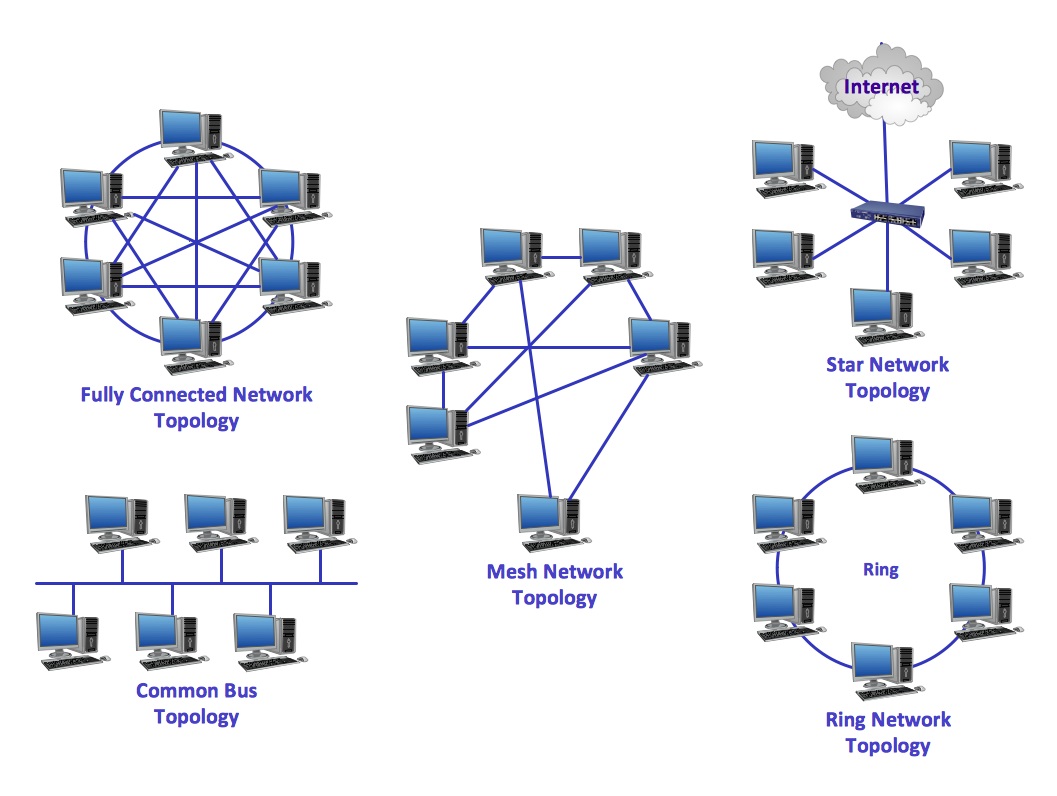
Network topology is a topological structure of computer network, which can be physical or logical. The physical topology depicts location of different computer network elements such as computers, cables and other devices. The logical topology visually displays network dataflows from one device to another. Sometimes network logical and physical topologies can be the same. ConceptDraw DIAGRAM diagramming and vector drawing software is powerful for drawing network maps and network topologies diagrams of any kinds and complexity thanks to the Computer Network Diagrams solution from the Computer and Networks area. ConceptDraw STORE proposes collection of network icons libraries and a lot of Network Topology Diagram examples, samples and templates which were created at ConceptDraw DIAGRAM software specially for Computer Network Diagrams solution. There are six basic types of the network topologies: Bus, Star, Ring, Mesh, Tree, Fully Connected. You can fast and easy design professional-looking diagram for each of them using the ConceptDraw DIAGRAM tools. There are plenty of web Visio-like diagramming software available. Web based diagrams software can be powerful, but sometimes it is essential to have desktop software. One of the most advanced diagrams tools like Visio for Mac OS is ConceptDraw DIAGRAM app.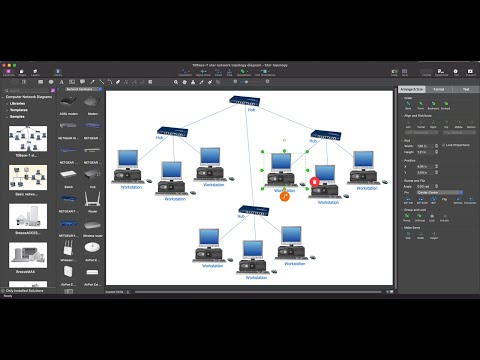
The vector stencils library "Cisco network topology" contains 89 symbols of Cisco network devices and design elements for drawing computer network topology diagrams.
"There are two basic categories of network topologies:
(1) Physical topologies,
(2) Logical topologies.
The shape of the cabling layout used to link devices is called the physical topology of the network. This refers to the layout of cabling, the locations of nodes, and the interconnections between the nodes and the cabling. The physical topology of a network is determined by the capabilities of the network access devices and media, the level of control or fault tolerance desired, and the cost associated with cabling or telecommunications circuits.
The logical topology in contrast, is the way that the signals act on the network media, or the way that the data passes through the network from one device to the next without regard to the physical interconnection of the devices." [Network topology. Wikipedia]
The symbols example "Cisco network topology - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"There are two basic categories of network topologies:
(1) Physical topologies,
(2) Logical topologies.
The shape of the cabling layout used to link devices is called the physical topology of the network. This refers to the layout of cabling, the locations of nodes, and the interconnections between the nodes and the cabling. The physical topology of a network is determined by the capabilities of the network access devices and media, the level of control or fault tolerance desired, and the cost associated with cabling or telecommunications circuits.
The logical topology in contrast, is the way that the signals act on the network media, or the way that the data passes through the network from one device to the next without regard to the physical interconnection of the devices." [Network topology. Wikipedia]
The symbols example "Cisco network topology - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
- Cloud Computing . Computer and Network Examples | Mobile cloud ...
- 3-Tier Auto-scalable Web Application Architecture | Amazon Web ...
- Amazon Cloud | Cloud Computing | Mobile cloud architecture ...
- AWS Architecture Diagrams | AWS Simple Icons for Architecture ...
- Internet symbols - Vector stencils library | Cloud Computing ...
- 3-Tier Auto-scalable Web Application Architecture | 2-Tier Auto ...
- Mobile cloud architecture diagram | AWS Architecture Diagrams ...
- AWS Architecture Diagrams | Amazon Web Services Diagrams ...
- Diagramming tool - Amazon Web Services and Cloud Computing ...
- Microsoft Azure | Azure Storage | Windows Azure | Cloud Platforms
- Server hardware - Rack diagram | Software and Database Design ...
- Microsoft Azure reference architecture | Microsoft Azure network and ...
- SharePoint server reference architecture for public-facing website ...
- Azure Cloud Application
- Amazon Web Services Diagrams - diagramming tool for architecture ...
- Diagramming tool - Amazon Web Services and Cloud Computing ...
- AWS Architecture Diagrams | ConceptDraw Solution Park ...
- Diagramming tool - Amazon Web Services and Cloud Computing ...
- Aws Solution Architecture Diagram
- AWS Architecture Diagrams | 3-Tier Auto-scalable Web Application ...

.png--diagram-flowchart-example.png)






























-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)














-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)



-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)











-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)