The vector stencils library "Workflow IT and security" contains 52 icons.
Use it to design your business process workflow diagrams with ConceptDraw PRO software.
"Information technology (IT) is the application of computers to store, retrieve, transmit and manipulate data, often in the context of a business or other enterprise. IT is considered a subset of information and communications technology (ICT)." [Information technology. Wikipedia]
The icons example "Design elements - Workflow IT and security" is included in the Business Process Workflow Diagrams solution from the Business Processes area of ConceptDraw Solution Park.
Use it to design your business process workflow diagrams with ConceptDraw PRO software.
"Information technology (IT) is the application of computers to store, retrieve, transmit and manipulate data, often in the context of a business or other enterprise. IT is considered a subset of information and communications technology (ICT)." [Information technology. Wikipedia]
The icons example "Design elements - Workflow IT and security" is included in the Business Process Workflow Diagrams solution from the Business Processes area of ConceptDraw Solution Park.
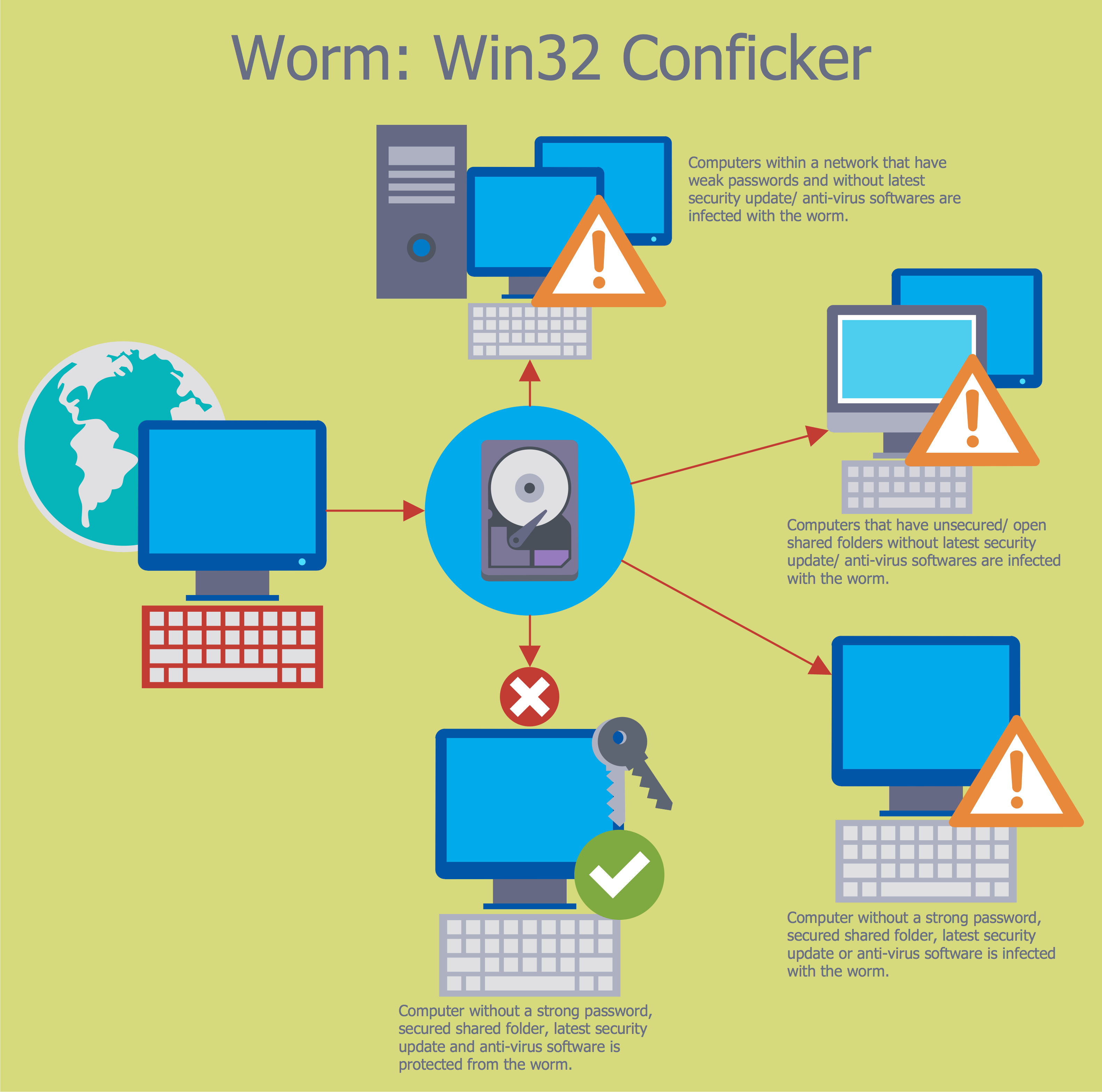
Cyber Security Degrees
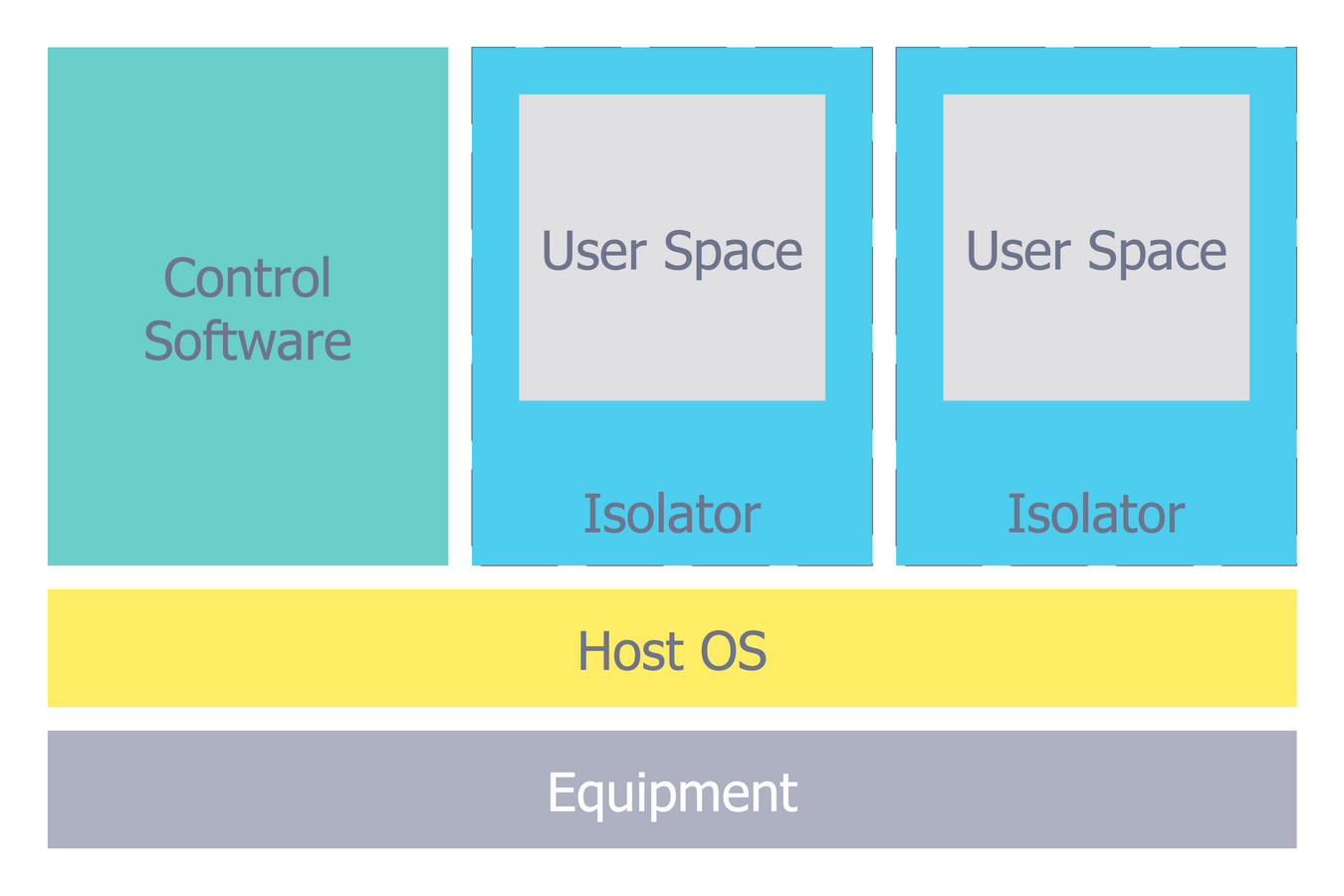
For protection various cyber environments are developed and applied large variety of cyber security standards, techniques, security concepts and approaches with different cyber security degrees. The ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park offers the number of useful tools which will help network security engineers, cyber security specialists, network and computer analysts easily and visually depict the knowledge and skills for research and prevention of intrusions, about protection critical information and analysis of cyber incidents, and for how to assess threats and vulnerabilities.Network Security Architecture Diagram
Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram? We recommend to use ConceptDraw DIAGRAM extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.Local area network (LAN). Computer and Network Examples
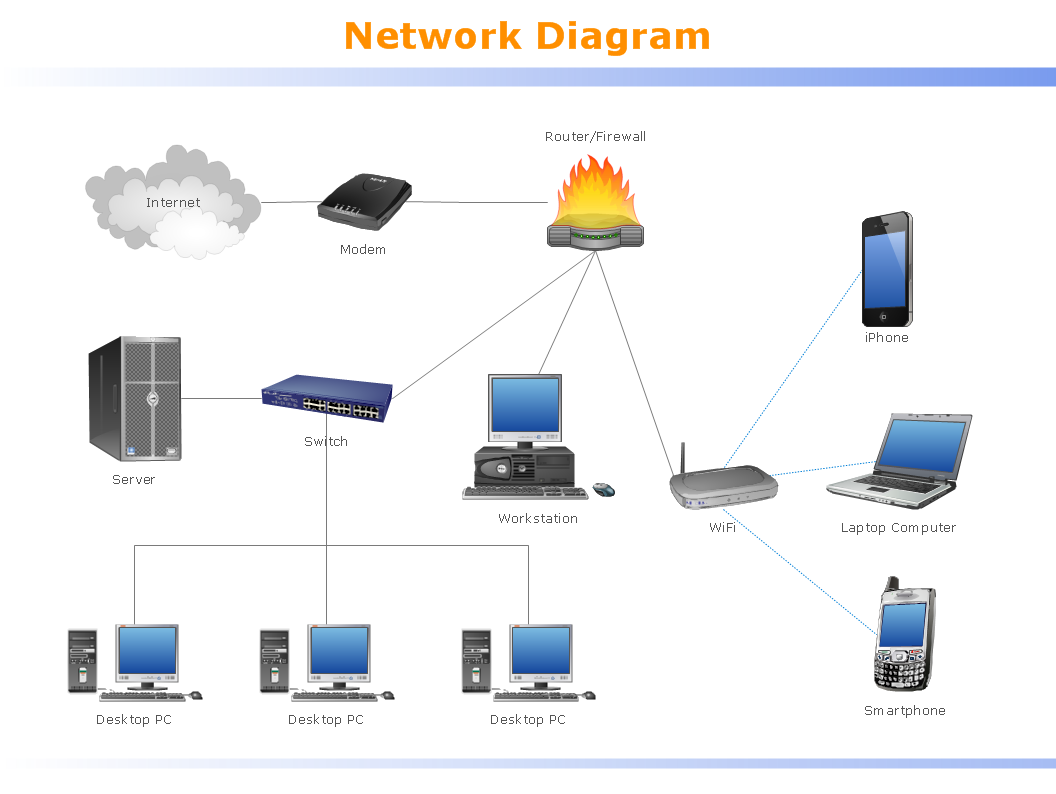
Local Area Network (LAN) is a network which consists of computers and peripheral devices connected each other and to the local domain server, and covers a little territory or small number of buildings, such as home, school, laboratory, office, etc. LAN serves for few hundreds of users. It includes many cables and wires, and demands to design previously a Network diagram. All local area network devices can use the shared printers and disk storage. ConceptDraw DIAGRAM is a perfect network diagramming software with examples of LAN Diagrams, templates and predesigned vector objects. ConceptDraw DIAGRAM is the ideal choice for network engineers and network designers who need to draw fast and easy Local Area Network Diagrams, for IT specialists, developers and other IT professionals which need to visualize the communication schemes of LAN and visually document the LAN's physical structure and arrangement in houses, offices and other buildings. Ready-to-use vector objects from Computer Network Diagrams solution will help you design LAN diagrams in minutes.
 Network Security Diagrams
Network Security Diagrams
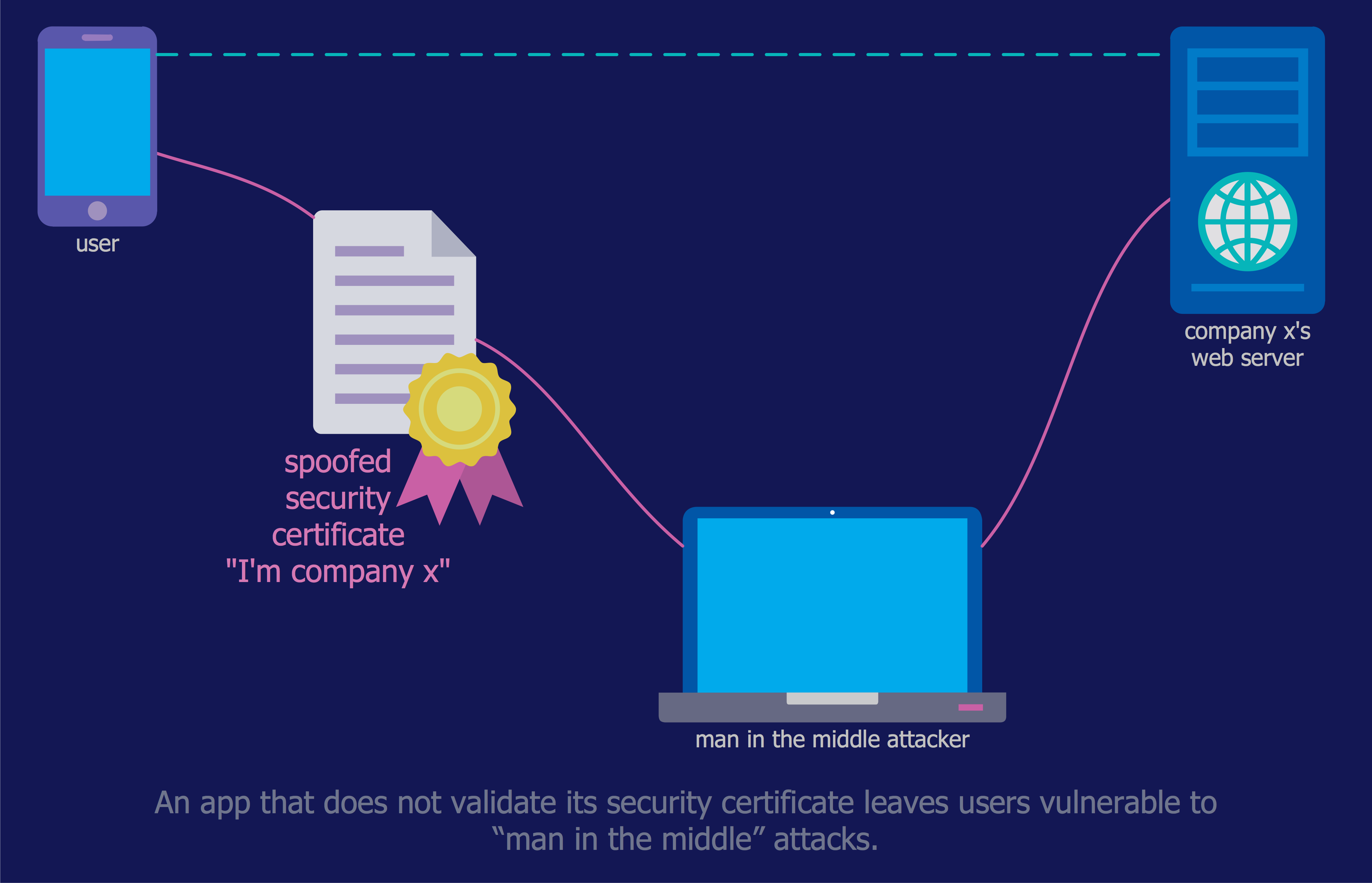
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw DIAGRAM software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
Network Security
The Internet is a giant computer network which connects computers all over the world. It is integral part of human society and business. But the serious question for network engineers, designers, lawmakers and enforcers is the need for protect the Internet networks from the Internet crimes, hacking and attacks. There are quite a number of hardware, software and physical methods of protection against them. The samples you see on this page were created in ConceptDraw DIAGRAM using the tools of Network Security Diagrams Solution for ConceptDraw DIAGRAM software. They show protection networks with Firewalls and other network security devices.IT Security Solutions
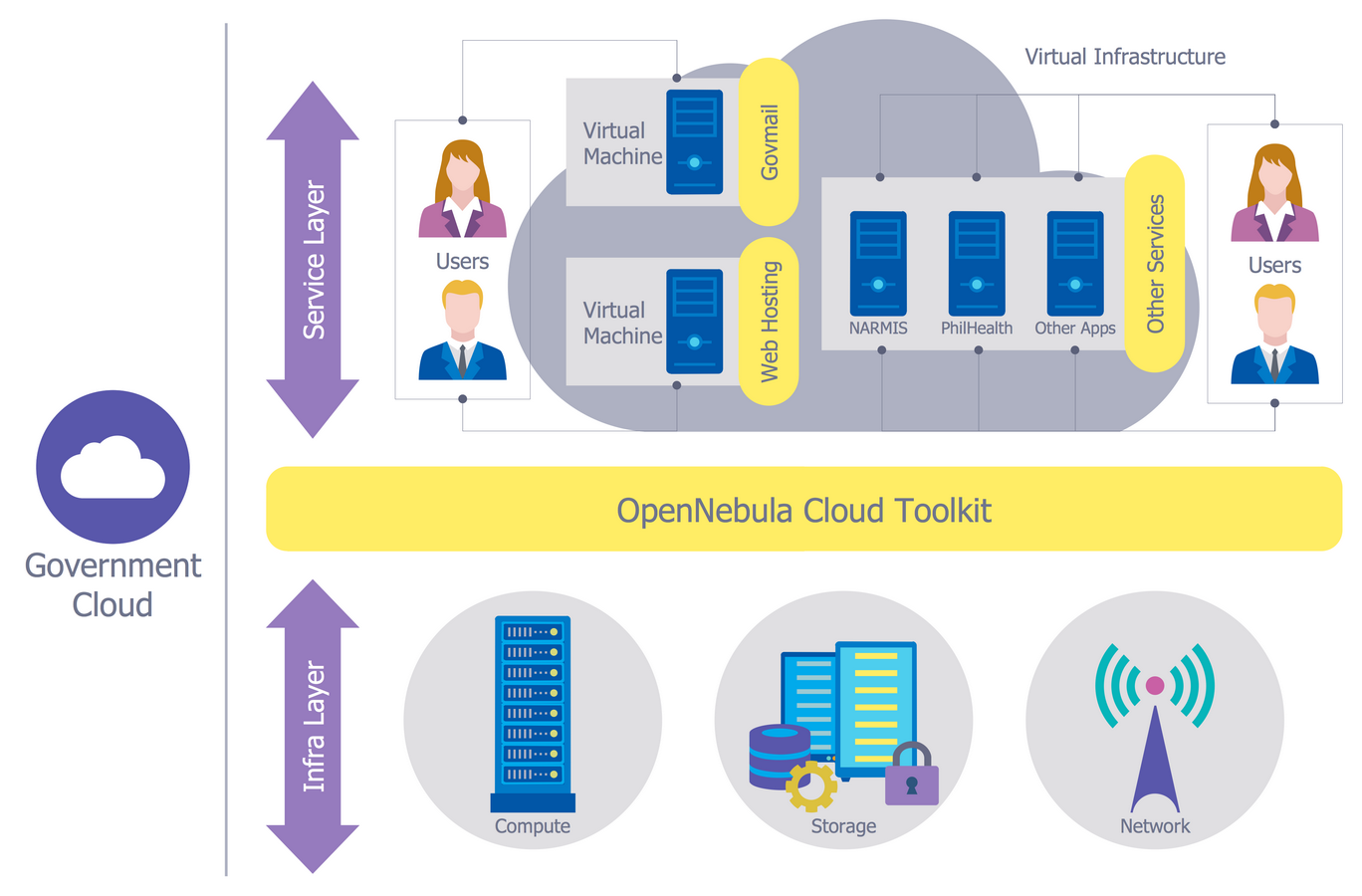
Dynamic of development computer and network technologies increases the need in modern cyber security strategies and IT security solutions to support security of your data, to ensure data privacy, and to protect your operations from the cyber threats. Thanks to the Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park, the ConceptDraw DIAGRAM diagramming and vector drawing software is one of the unique IT security solutions for professional designing Network Security Diagrams.Network Security Model
Creation of well thought-out network security model will effectively help you in realization your network's security. ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park lets fast and easy design all variety of network security models: Open network security model, Closed network security model, Restrictive network access model.Network Security Tips
The Internet is a huge world with unlimited possibilities. But with all its numerous advantages, the Internet also conceals many dangers and security threats, that's why we advise you to follow simple network security tips. ConceptDraw DIAGRAM diagramming and vector drawing software supplied with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is an ideal software for easy designing Network Security Diagrams and attractive illustrations with effective network security tips.Personal area (PAN) networks. Computer and Network Examples
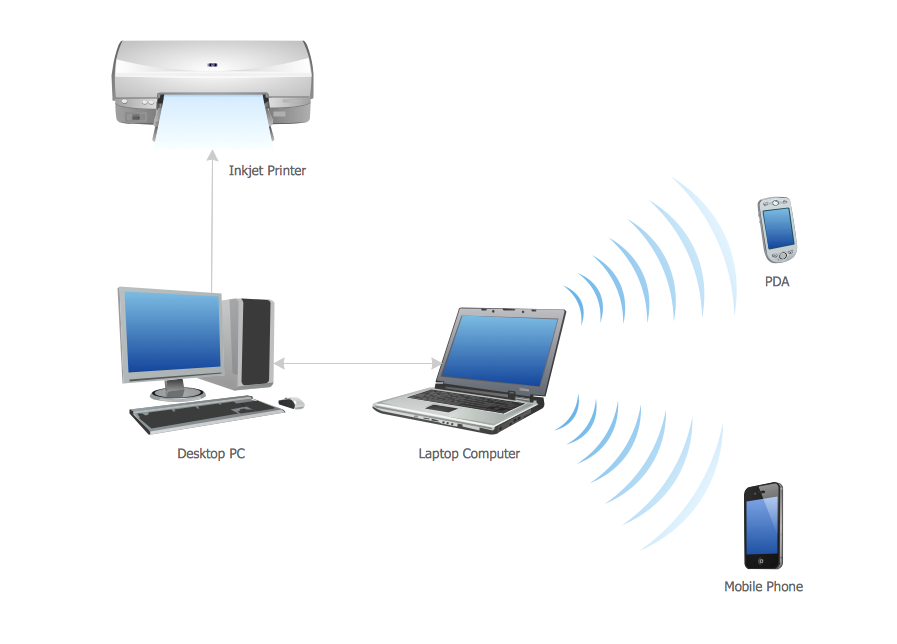
Personal area network (PAN) is a network organized on a limited area and used for data transmission between various personal devices, such as computers, tablets, laptops, telephones, different digital and mobile devices, etc. and also for connecting to higher level network and Internet. PAN is used to manage the interconnections of IT devices which surround a single user and generally contains such appliances, as cordless mice, keyboard, phone, and Bluetooth handsets. PANs can be wired with computer buses, or wirelessly connected to the Internet using such network technologies as Bluetooth, Z-Wave, ZigBee, IrDa, UWB, Body Area Network. PANs have a lot of pros and cons, they are expedient, lucrative and handy, but sometimes have bad connection with other networks on the same radio bands, Bluetooth has distance limits and slow data transfer speed, but is comparatively safe. ConceptDraw DIAGRAM diagramming software supplied with numerous solutions of Computer and Networks Area included to ConceptDraw Solution Park perfectly suits for designing the Personal Area Networks.
- Design elements - Workflow IT and security | Scanning Operator ...
- Network Security Devices | Cyber Security Degrees | Network ...
- Upload Icon Design
- 10 Steps to Cyber Security | Network Security Diagrams | 10 Steps ...
- 10 Steps to Cyber Security | Network Security Diagrams | Network ...
- Operator Computer Icon
- Operator Icon Png
- Network Security Diagrams | Cyber Security Degrees | 10 Steps to ...
- Cyber Security Degrees | 10 Steps to Cyber Security | Network ...
- Top 5 Android Flow Chart Apps | Top iPad Business Process ...