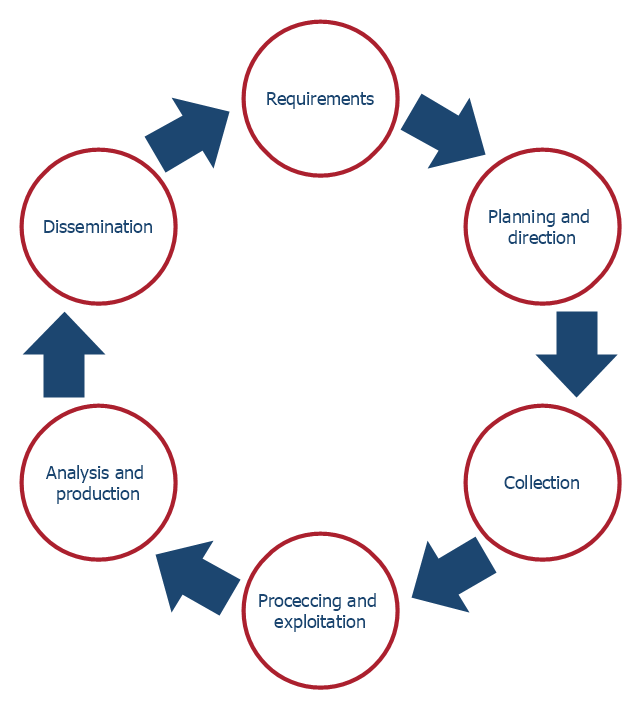
This arrow loop diagram sample was created on the base of the figure illustrating the article "Up Close and Personal. Life as an Intelligence Analyst" from the FBI website. [fbi.gov/ news/ stories/ 2006/ may/ arias050506]
"The traditional Intelligence cycle is the fundamental cycle of intelligence processing in a civilian or military intelligence agency or in law enforcement as a closed path consisting of repeating nodes. The stages of the intelligence cycle include the issuance of requirements by decision makers, collection, processing, analysis, and publication of intelligence. The circuit is completed when decision makers provide feedback and revised requirements. The intelligence cycle is also called the Intelligence Process by the U.S. Department of Defense (DoD) and the uniformed services." [Intelligence cycle. Wikipedia]
The arrow loop diagram example "Intelligence analyst cycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Target and Circular Diagrams solution from the Marketing area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ marketing-target-and-circular-diagrams
"The traditional Intelligence cycle is the fundamental cycle of intelligence processing in a civilian or military intelligence agency or in law enforcement as a closed path consisting of repeating nodes. The stages of the intelligence cycle include the issuance of requirements by decision makers, collection, processing, analysis, and publication of intelligence. The circuit is completed when decision makers provide feedback and revised requirements. The intelligence cycle is also called the Intelligence Process by the U.S. Department of Defense (DoD) and the uniformed services." [Intelligence cycle. Wikipedia]
The arrow loop diagram example "Intelligence analyst cycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Target and Circular Diagrams solution from the Marketing area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ marketing-target-and-circular-diagrams
 Target and Circular Diagrams
Target and Circular Diagrams
This solution extends ConceptDraw DIAGRAM software with samples, templates and library of design elements for drawing the Target and Circular Diagrams.
 Education Package
Education Package
Education Package is a comprehensive set of multifarious graphical solutions from ConceptDraw Solution Park, collected together in help to ConceptDraw DIAGRAM users working in a field of science, education and training, which is aimed at improving the quality of education and helping to design with ease variety of interesting and colorful educational materials, diagrams, charts and maps. Use it to present the information and knowledge in an interesting, clear, structured and simple form to achieve a success in education and pedagogy, to maintain the interest of students and pupils throughout the whole learning process, at the lectures, lessons and even during independent work with additional materials, to contribute to better perception of scientific information by listeners during the conferences and reports.
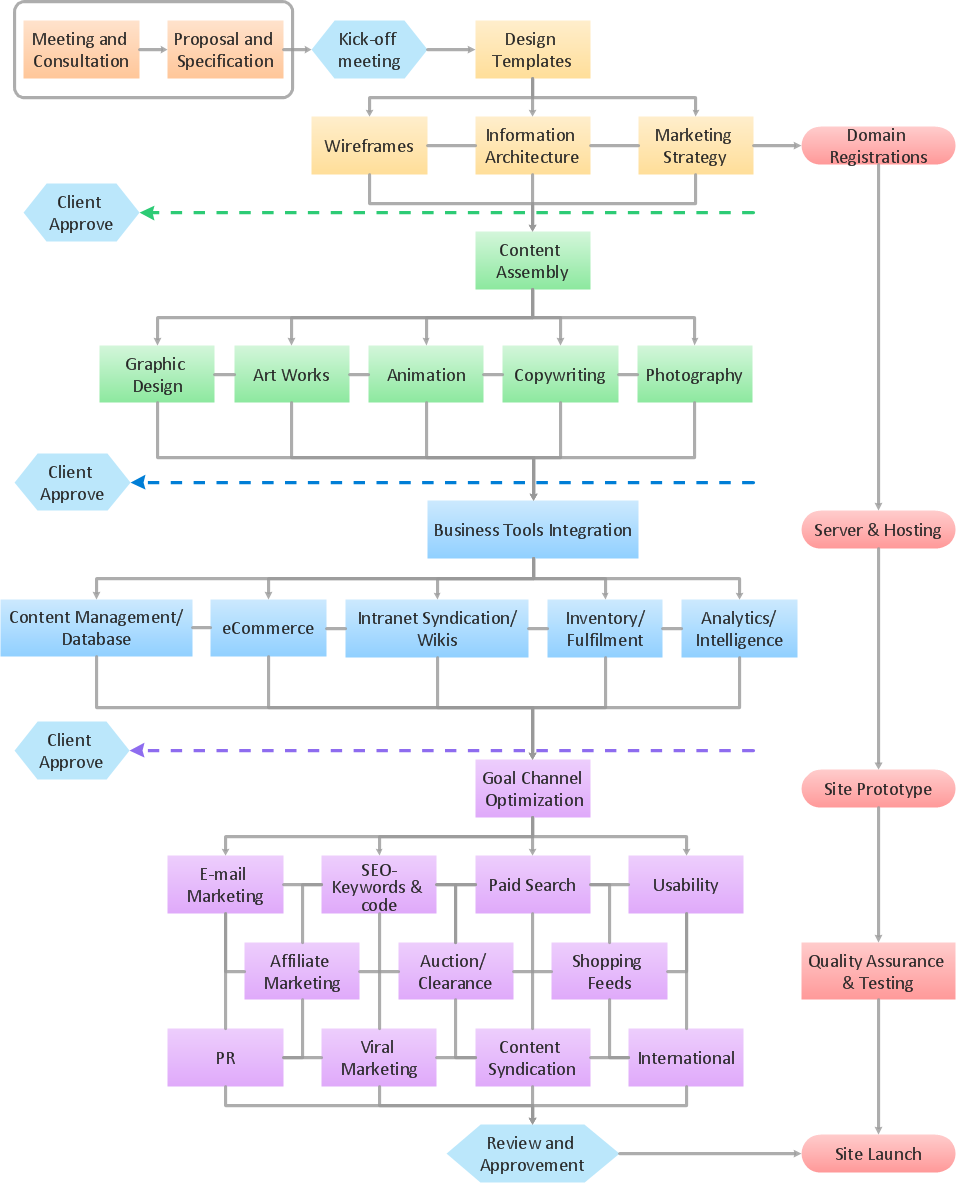
Flowchart Marketing Process. Flowchart Examples
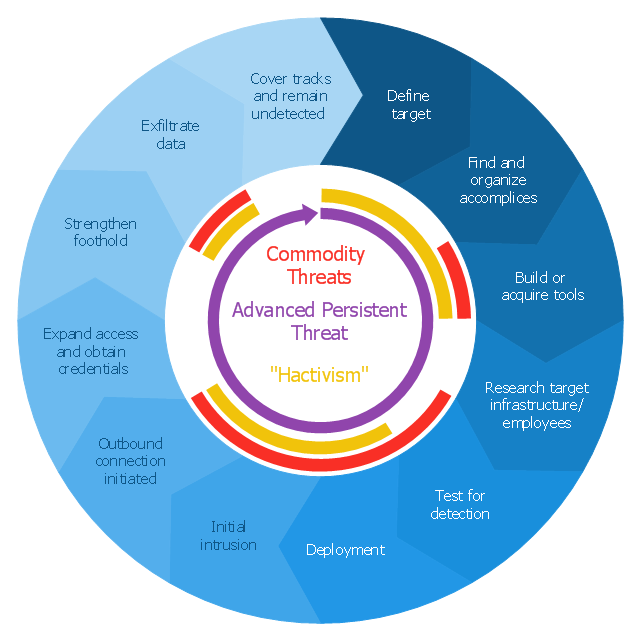
This sample shows the Flowchart that displays the layout and work flow of the cloud marketing platform. This diagram has a style of the marketing brochure. This style displays the central product that is related to the other issues. Using the ready-to-use predesigned objects, samples and templates from the Flowcharts Solution for ConceptDraw DIAGRAM you can create your own professional looking Flowchart Diagrams quick and easy.This circular arrows diagram sample shows advanced persistent threat lifecycle.
It was designed on the base of the Wikimedia Commons file: Advanced persistent threat lifecycle.jpg.
[commons.wikimedia.org/ wiki/ File:Advanced_ persistent_ threat_ lifecycle.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Advanced Persistent Threat (APT) APT is a set of stealthy and continuous hacking processes often orchestrated by human targeting a specific entity. APT usually targets organizations and or nations for business or political motives. APT processes require high degree of covertness over a long period of time. As the name implies, APT consists of three major components/ processes: advanced, persistent, and threat. The advanced process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The persistent process suggests that an external command and control is continuously monitoring and extracting data off a specific target. The threat process indicates human involvement in orchestrating the attack.
APT usually refers to a group, such as a government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack. Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target." [Advanced persistent threat. Wikipedia]
The arrow donut chart example
"Advanced persistent threat lifecycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
It was designed on the base of the Wikimedia Commons file: Advanced persistent threat lifecycle.jpg.
[commons.wikimedia.org/ wiki/ File:Advanced_ persistent_ threat_ lifecycle.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Advanced Persistent Threat (APT) APT is a set of stealthy and continuous hacking processes often orchestrated by human targeting a specific entity. APT usually targets organizations and or nations for business or political motives. APT processes require high degree of covertness over a long period of time. As the name implies, APT consists of three major components/ processes: advanced, persistent, and threat. The advanced process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The persistent process suggests that an external command and control is continuously monitoring and extracting data off a specific target. The threat process indicates human involvement in orchestrating the attack.
APT usually refers to a group, such as a government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack. Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target." [Advanced persistent threat. Wikipedia]
The arrow donut chart example
"Advanced persistent threat lifecycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
 Block Diagrams
Block Diagrams
Block diagrams solution extends ConceptDraw DIAGRAM software with templates, samples and libraries of vector stencils for drawing the block diagrams.
The Circular Flow Diagram
ConceptDraw DIAGRAM diagramming and vector drawing software extended with Target and Circular Diagrams solution from the Marketing area of ConceptDraw Solution Park is perfect for the Circular Flow Diagram creating.Best Program to Create a Fowchart
ConceptDraw - feature-rich flowchart software allows you create professional looking flowcharts.- Business Intelligence Cycle
- Intelligence analyst cycle - Arrow loop diagram | The Circular Flow ...
- Intelligence analyst cycle - Arrow loop diagram | Target and Circular ...
- Product life cycle process - Flowchart | Intelligence analyst cycle ...
- Intelligence analyst cycle - Arrow loop diagram | Business ...
- Last resort hotel book room process - DFD | Intelligence analyst ...
- Divided Bar Diagrams | Basic Circle-Spoke Diagrams | Stakeholder ...
- Block Diagrams | Business Intelligence Dashboard | SYSML ...
- Product life cycle process - Flowchart | Circular Arrows Diagrams ...
- Innovation life cycle - Arrow loop diagram | National Preparedness ...