Network Security Tips
The Internet is a huge world with unlimited possibilities. But with all its numerous advantages, the Internet also conceals many dangers and security threats, that's why we advise you to follow simple network security tips. ConceptDraw DIAGRAM diagramming and vector drawing software supplied with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is an ideal software for easy designing Network Security Diagrams and attractive illustrations with effective network security tips.Network Security
The Internet is a giant computer network which connects computers all over the world. It is integral part of human society and business. But the serious question for network engineers, designers, lawmakers and enforcers is the need for protect the Internet networks from the Internet crimes, hacking and attacks. There are quite a number of hardware, software and physical methods of protection against them. The samples you see on this page were created in ConceptDraw DIAGRAM using the tools of Network Security Diagrams Solution for ConceptDraw DIAGRAM software. They show protection networks with Firewalls and other network security devices.Network Security Diagram
ConceptDraw DIAGRAM diagramming and vector drawing software enhanced with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is the best for effective design professional, colorful and attractive Network Security Diagram of any complexity and degree of detailing.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw DIAGRAM software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.IT Security Solutions
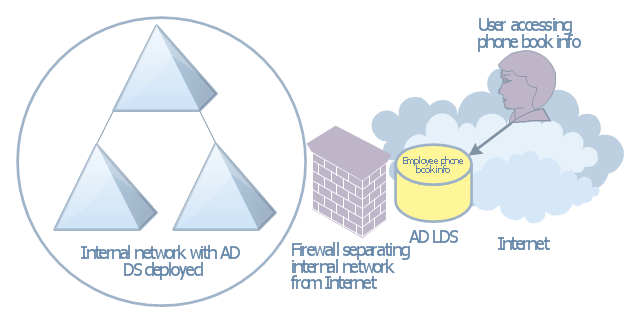
Dynamic of development computer and network technologies increases the need in modern cyber security strategies and IT security solutions to support security of your data, to ensure data privacy, and to protect your operations from the cyber threats. Thanks to the Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park, the ConceptDraw DIAGRAM diagramming and vector drawing software is one of the unique IT security solutions for professional designing Network Security Diagrams.This AD diagram example was created based on the picture "AD LDS as a phone book service" from the book "Active Directory for Dummies".
"Directory services are a great way of providing information that can be fre-
quently retrieved and searched on in a hierarchical way. ... Well, there’s no reason that you can’t create a directory service that’s actually a phone book. Imagine that you need to make a searchable phone directory of your organization available on the Internet. ... This isn’t a difficult task, but it has security repercussions. If you’ve already deployed AD DS and you have the employees’ phone numbers available in that directory, it might not be a good idea to expose your AD DS environment to the Internet for security reasons. Using AD LDS is a great alternative because it can be deployed separately from AD DS and it’s designed to simply provide the information retrieval service that you need without the complications involved with Kerberos authentication and group policies." [Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "AD LDS as a phone book service" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"Directory services are a great way of providing information that can be fre-
quently retrieved and searched on in a hierarchical way. ... Well, there’s no reason that you can’t create a directory service that’s actually a phone book. Imagine that you need to make a searchable phone directory of your organization available on the Internet. ... This isn’t a difficult task, but it has security repercussions. If you’ve already deployed AD DS and you have the employees’ phone numbers available in that directory, it might not be a good idea to expose your AD DS environment to the Internet for security reasons. Using AD LDS is a great alternative because it can be deployed separately from AD DS and it’s designed to simply provide the information retrieval service that you need without the complications involved with Kerberos authentication and group policies." [Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "AD LDS as a phone book service" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"A website, also written as Web site, web site, or simply site, is a set of related web pages served from a single web domain. A website is hosted on at least one web server, accessible via a network such as the Internet or a private local area network through an Internet address known as a Uniform resource locator. All publicly accessible websites collectively constitute the World Wide Web.
A webpage is a document, typically written in plain text interspersed with formatting instructions of Hypertext Markup Language (HTML, XHTML). A webpage may incorporate elements from other websites with suitable markup anchors.
Webpages are accessed and transported with the Hypertext Transfer Protocol (HTTP), which may optionally employ encryption (HTTP Secure, HTTPS) to provide security and privacy for the user of the webpage content. The user's application, often a web browser, renders the page content according to its HTML markup instructions onto a display terminal.
The pages of a website can usually be accessed from a simple Uniform Resource Locator (URL) called the web address. The URLs of the pages organize them into a hierarchy, although hyperlinking between them conveys the reader's perceived site structure and guides the reader's navigation of the site which generally includes a home page with most of the links to the site's web content, and a supplementary about, contact and link page." [Website. Wikipedia]
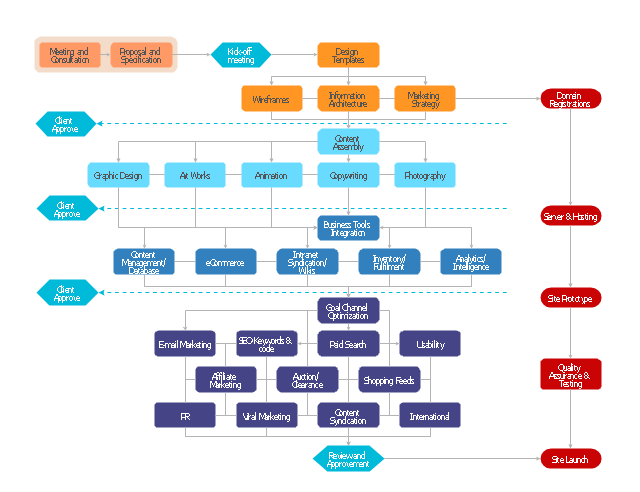
The flow chart example "Website launch" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Flowcharts solution from the area "What is a Diagram" of ConceptDraw Solution Park.
A webpage is a document, typically written in plain text interspersed with formatting instructions of Hypertext Markup Language (HTML, XHTML). A webpage may incorporate elements from other websites with suitable markup anchors.
Webpages are accessed and transported with the Hypertext Transfer Protocol (HTTP), which may optionally employ encryption (HTTP Secure, HTTPS) to provide security and privacy for the user of the webpage content. The user's application, often a web browser, renders the page content according to its HTML markup instructions onto a display terminal.
The pages of a website can usually be accessed from a simple Uniform Resource Locator (URL) called the web address. The URLs of the pages organize them into a hierarchy, although hyperlinking between them conveys the reader's perceived site structure and guides the reader's navigation of the site which generally includes a home page with most of the links to the site's web content, and a supplementary about, contact and link page." [Website. Wikipedia]
The flow chart example "Website launch" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Flowcharts solution from the area "What is a Diagram" of ConceptDraw Solution Park.
The vector stencils library "Computers and network isometric" contains 56 3D clipart images of computer and network devices and equipment for drawing network diagrams.
The clip art example "Computers and network isometric - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
The clip art example "Computers and network isometric - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
 ConceptDraw Solution Park
ConceptDraw Solution Park
ConceptDraw Solution Park collects graphic extensions, examples and learning materials
 Interactive Voice Response Diagrams
Interactive Voice Response Diagrams
Interactive Voice Response Diagrams solution extends ConceptDraw DIAGRAM software with samples, templates and libraries of ready-to-use vector stencils that help create Interactive Voice Response (IVR) diagrams illustrating in details a work of interactive voice response system, the IVR system’s logical and physical structure, Voice-over-Internet Protocol (VoIP) diagrams, and Action VoIP diagrams with representing voice actions on them, to visualize how the computers interact with callers through voice recognition and dual-tone multi-frequency signaling (DTMF) keypad inputs.
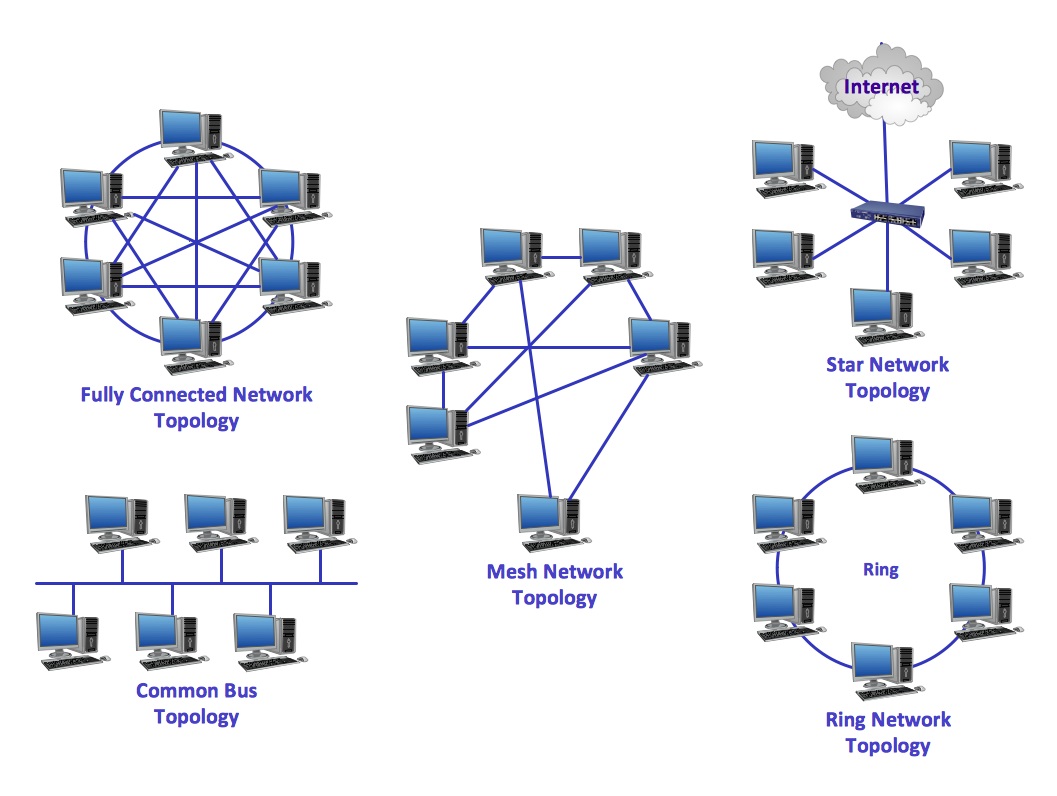
Network Topologies
Network topology is a topological structure of computer network, which can be physical or logical. The physical topology depicts location of different computer network elements such as computers, cables and other devices. The logical topology visually displays network dataflows from one device to another. Sometimes network logical and physical topologies can be the same. ConceptDraw DIAGRAM diagramming and vector drawing software is powerful for drawing network maps and network topologies diagrams of any kinds and complexity thanks to the Computer Network Diagrams solution from the Computer and Networks area. ConceptDraw STORE proposes collection of network icons libraries and a lot of Network Topology Diagram examples, samples and templates which were created at ConceptDraw DIAGRAM software specially for Computer Network Diagrams solution. There are six basic types of the network topologies: Bus, Star, Ring, Mesh, Tree, Fully Connected. You can fast and easy design professional-looking diagram for each of them using the ConceptDraw DIAGRAM tools. There are plenty of web Visio-like diagramming software available. Web based diagrams software can be powerful, but sometimes it is essential to have desktop software. One of the most advanced diagrams tools like Visio for Mac OS is ConceptDraw DIAGRAM app.
This computer security diagram example was designed on the base of the Wikimedia Commons file: Firewall.png.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
This VANET diagram example was drawn on the base of picture from the webpage "Security and Privacy in Location-based MANETs/ VANETs" from the Donald Bren School of Information and Computer Sciences, the University of California, Irvine. [ics.uci.edu/ ~keldefra/ manet.htm]
"A vehicular ad hoc network (VANET) uses cars as mobile nodes in a MANET to create a mobile network. A VANET turns every participating car into a wireless router or node, allowing cars approximately 100 to 300 metres of each other to connect and, in turn, create a network with a wide range. As cars fall out of the signal range and drop out of the network, other cars can join in, connecting vehicles to one another so that a mobile Internet is created. It is estimated that the first systems that will integrate this technology are police and fire vehicles to communicate with each other for safety purposes. Automotive companies like General Motors, Toyota, Nissan, DaimlerChrysler, BMW and Ford promote this term." [Vehicular ad hoc network. Wikipedia]
The VANET diagram example "Vehicular ad-hoc network" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Vehicular Networking solution from the Computer and Networks area of ConceptDraw Solution Park.
"A vehicular ad hoc network (VANET) uses cars as mobile nodes in a MANET to create a mobile network. A VANET turns every participating car into a wireless router or node, allowing cars approximately 100 to 300 metres of each other to connect and, in turn, create a network with a wide range. As cars fall out of the signal range and drop out of the network, other cars can join in, connecting vehicles to one another so that a mobile Internet is created. It is estimated that the first systems that will integrate this technology are police and fire vehicles to communicate with each other for safety purposes. Automotive companies like General Motors, Toyota, Nissan, DaimlerChrysler, BMW and Ford promote this term." [Vehicular ad hoc network. Wikipedia]
The VANET diagram example "Vehicular ad-hoc network" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Vehicular Networking solution from the Computer and Networks area of ConceptDraw Solution Park.
- Internet symbols - Vector stencils library | | Network Security ...
- Internet symbols - Vector stencils library | Access and security ...
- | | | Internet Clipart
- Cisco Security . Cisco icons, shapes, stencils and symbols | Internet ...
- Network Security Model | Network Security | Secure Wireless ...
- Design elements - Cybersecurity round icons | Cyber Security ...
- ConceptDraw PRO Network Diagram Tool | Network Security ...
- Make A Diagram Of Computer Security
- Network Security | Hotel Network Topology Diagram | Cisco Network ...
- Network Security . Computer and Network Examples | Cisco security ...
- Network Security | Types of Flowchart - Overview | Process ...
- Network Security Diagrams | Network Glossary Definition | Network ...
- Diagram Of Idea Of Internet
- Service Provided By Internet With Diagram
- Security and Access Plans | How to Draw a Security and Access ...
- Camera layout schematic | Security and Access Plans | Security ...
- Cloud Computing | AWS Administration and Security - Vector ...
- AWS | Satellite telecom network diagram | Network Glossary ...
- Venn diagram - Internet marketing professions | Local area network ...
- Camera layout schematic | Marketing Diagrams | Computers and ...