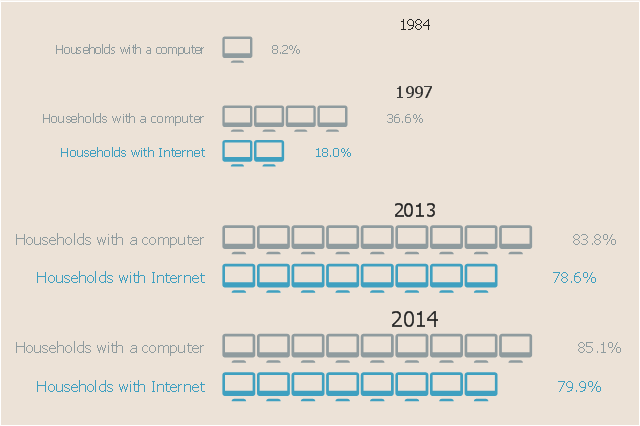
This picture bar graph sample shows the computer and Internet use at home from 1984 to 2014. It was designed using data from website of the United States Census Bureau (USCB).
[census.gov/ content/ dam/ Census/ library/ visualizations/ 2016/ comm/ digital_ nation.png]
"Home automation is the residential extension of building automation and involves the control and automation of lighting, heating, ventilation, air conditioning (HVAC), appliances, and security. Modern systems generally consist of switches and sensors connected to a central hub sometimes called a "gateway" from which the system is controlled with a user interface that is interacted either with a wall-mounted terminal, mobile phone software, tablet computer or a web interface." [Home automation. Wikipedia]
The pictorial chart example "Computer and Internet use at home over time" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Picture Graphs solution from the Graphs and Charts area of ConceptDraw Solution Park.
[census.gov/ content/ dam/ Census/ library/ visualizations/ 2016/ comm/ digital_ nation.png]
"Home automation is the residential extension of building automation and involves the control and automation of lighting, heating, ventilation, air conditioning (HVAC), appliances, and security. Modern systems generally consist of switches and sensors connected to a central hub sometimes called a "gateway" from which the system is controlled with a user interface that is interacted either with a wall-mounted terminal, mobile phone software, tablet computer or a web interface." [Home automation. Wikipedia]
The pictorial chart example "Computer and Internet use at home over time" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Picture Graphs solution from the Graphs and Charts area of ConceptDraw Solution Park.
This computer security diagram example was designed on the base of the Wikimedia Commons file: Firewall.png.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
 Interactive Voice Response Diagrams
Interactive Voice Response Diagrams
Interactive Voice Response Diagrams solution extends ConceptDraw PRO v10 software with samples, templates and libraries of ready-to-use vector stencils that help create Interactive Voice Response (IVR) diagrams illustrating in details a work of interactive voice response system, the IVR system’s logical and physical structure, Voice-over-Internet Protocol (VoIP) diagrams, and Action VoIP diagrams with representing voice actions on them, to visualize how the computers interact with callers through voice recognition and dual-tone multi-frequency signaling (DTMF) keypad inputs.
 ConceptDraw Solution Park
ConceptDraw Solution Park
ConceptDraw Solution Park collects graphic extensions, examples and learning materials
- Computer Security Systems
- Internet Security Companies
- Internet symbols - Vector stencils library | Network Security Devices ...
- Internet Security Appliance
- Security system plan
- Network Security Devices | Block Diagrams | ConceptDraw Solution ...
- Flowchart Internet Security
- Network Security Diagrams | Network Security Architecture Diagram ...
- Website launch - Flowchart | Website Wireframe | Security system ...
- Network Security Diagrams | How to Create a Network Security ...
- Internet Security Or Its Block Diagram
- Internet Security Program
- Camera layout schematic
- Network VOIP. Computer and Network Examples | What is IVR ...
- Security system plan | Security Plans | Network Security Devices ...
- Network Security | Network Security Diagram | How to Create a ...
- Internet Internal Process Flow Chart
- Process Flowchart | Network Security | Types of Flowchart ...
- Internet Security Tools