"The ideal telecommunication network has the following characteristics: broadband, multi-media, multi-point, multi-rate and economical implementation for a diversity of services (multi-services). The Broadband Integrated Services Digital Network (B-ISDN) intended to provide these characteristics. Asynchronous Transfer Mode (ATM) was promoted as a target technology for meeting these requirements" [Broadband networks. Wikipedia]
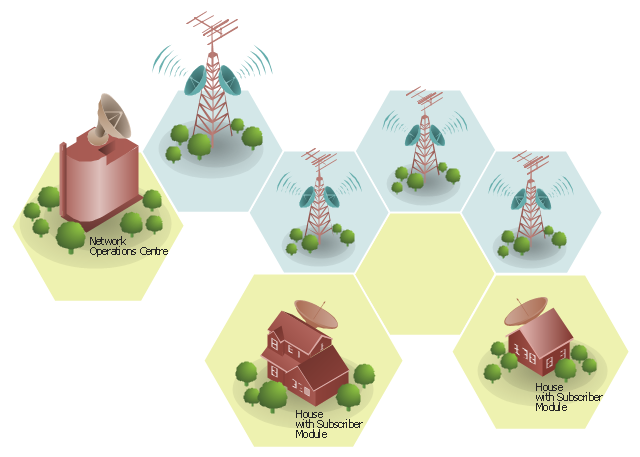
"Wireless broadband is technology that provides high-speed wireless Internet access or computer networking access over a wide area. ...
Wireless networks can feature data rates roughly equivalent to some wired networks, such as that of asymmetric digital subscriber line (ADSL) or a cable modem. Wireless networks can also be symmetrical, meaning the same rate in both directions (downstream and upstream), which is most commonly associated with fixed wireless networks. A fixed wireless network link is a stationary terrestrial wireless connection, which can support higher data rates for the same power as mobile or satellite systems.
Few wireless Internet service providers (WISPs) provide download speeds of over 100 Mbit/ s; most broadband wireless access (BWA) services are estimated to have a range of 50 km (31 mi) from a tower. Technologies used include LMDS and MMDS, as well as heavy use of the ISM bands and one particular access technology was standardized by IEEE 802.16, with products known as WiMAX." [Wireless broadband. Wikipedia]
Wireless broadband is technology that provides high-speed wireless Internet access or computer networking access over a wide area. [Wireless broadband. Wikipedia]
This wireless broadband network diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Telecommunication Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"Wireless broadband is technology that provides high-speed wireless Internet access or computer networking access over a wide area. ...
Wireless networks can feature data rates roughly equivalent to some wired networks, such as that of asymmetric digital subscriber line (ADSL) or a cable modem. Wireless networks can also be symmetrical, meaning the same rate in both directions (downstream and upstream), which is most commonly associated with fixed wireless networks. A fixed wireless network link is a stationary terrestrial wireless connection, which can support higher data rates for the same power as mobile or satellite systems.
Few wireless Internet service providers (WISPs) provide download speeds of over 100 Mbit/ s; most broadband wireless access (BWA) services are estimated to have a range of 50 km (31 mi) from a tower. Technologies used include LMDS and MMDS, as well as heavy use of the ISM bands and one particular access technology was standardized by IEEE 802.16, with products known as WiMAX." [Wireless broadband. Wikipedia]
Wireless broadband is technology that provides high-speed wireless Internet access or computer networking access over a wide area. [Wireless broadband. Wikipedia]
This wireless broadband network diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Telecommunication Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
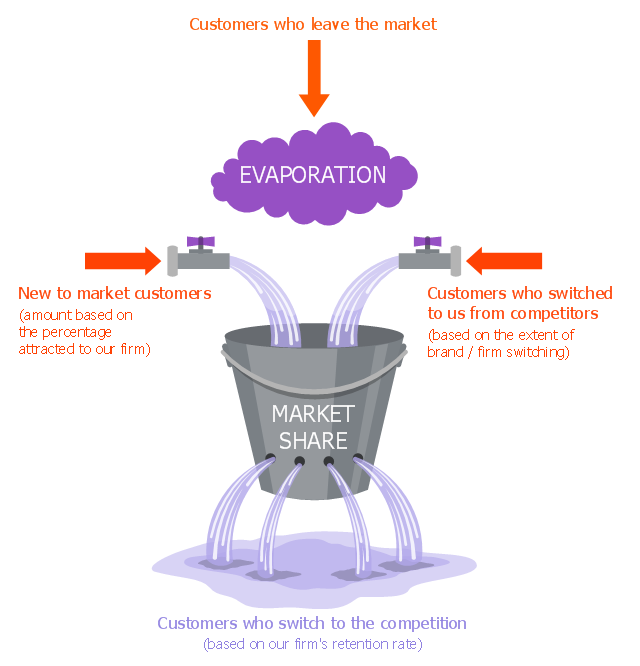
"The leaky bucket theory The leaky bucket theory is the model that seeks to describe the process of customer gain and loss, otherwise known as customer churn . Customer retention is one of the key concepts in relationship marketing. Most companies concentrate on recruiting new customers to replace customers who move on, rather than seeking to retain customers." [Blythe J. Key Concepts in Marketing. 2009. knowledge.sagepub.com/ view/ key-concepts-in-marketing/ n5.xml]
"Customer attrition, also known as customer churn, customer turnover, or customer defection, is the loss of clients or customers.
Banks, telephone service companies, Internet service providers, pay TV companies, insurance firms, and alarm monitoring services, often use customer attrition analysis and customer attrition rates as one of their key business metrics (along with cash flow, EBITDA, etc.) because the "...cost of retaining an existing customer is far less than acquiring a new one." Companies from these sectors often have customer service branches which attempt to win back defecting clients, because recovered long-term customers can be worth much more to a company than newly recruited clients." [Customer attrition. Wikipedia]
The example "Leaky bucket diagram" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Marketing Diagrams solution from the Marketing area of ConceptDraw Solution Park.
"Customer attrition, also known as customer churn, customer turnover, or customer defection, is the loss of clients or customers.
Banks, telephone service companies, Internet service providers, pay TV companies, insurance firms, and alarm monitoring services, often use customer attrition analysis and customer attrition rates as one of their key business metrics (along with cash flow, EBITDA, etc.) because the "...cost of retaining an existing customer is far less than acquiring a new one." Companies from these sectors often have customer service branches which attempt to win back defecting clients, because recovered long-term customers can be worth much more to a company than newly recruited clients." [Customer attrition. Wikipedia]
The example "Leaky bucket diagram" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Marketing Diagrams solution from the Marketing area of ConceptDraw Solution Park.
"There are two definitions for wireless LAN roaming:
Internal Roaming (1): The Mobile Station (MS) moves from one access point (AP) to another AP within a home network because the signal strength is too weak. An authentication server (RADIUS) performs the re-authentication of MS via 802.1x (e.g. with PEAP). The billing of QoS is in the home network. A Mobile Station roaming from one access point to another often interrupts the flow of data among the Mobile Station and an application connected to the network. The Mobile Station, for instance, periodically monitors the presence of alternative access points (ones that will provide a better connection). At some point, based on proprietary mechanisms, the Mobile Station decides to re-associate with an access point having a stronger wireless signal. The Mobile Station, however, may lose a connection with an access point before associating with another access point. In order to provide reliable connections with applications, the Mobile Station must generally include software that provides session persistence.
External Roaming (2): The MS (client) moves into a WLAN of another Wireless Internet Service Provider (WISP) and takes their services (Hotspot). The user can independently of his home network use another foreign network, if this is open for visitors. There must be special authentication and billing systems for mobile services in a foreign network." [Wireless LAN. Wikipedia]
This Cisco roaming wireless local area network diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Internal Roaming (1): The Mobile Station (MS) moves from one access point (AP) to another AP within a home network because the signal strength is too weak. An authentication server (RADIUS) performs the re-authentication of MS via 802.1x (e.g. with PEAP). The billing of QoS is in the home network. A Mobile Station roaming from one access point to another often interrupts the flow of data among the Mobile Station and an application connected to the network. The Mobile Station, for instance, periodically monitors the presence of alternative access points (ones that will provide a better connection). At some point, based on proprietary mechanisms, the Mobile Station decides to re-associate with an access point having a stronger wireless signal. The Mobile Station, however, may lose a connection with an access point before associating with another access point. In order to provide reliable connections with applications, the Mobile Station must generally include software that provides session persistence.
External Roaming (2): The MS (client) moves into a WLAN of another Wireless Internet Service Provider (WISP) and takes their services (Hotspot). The user can independently of his home network use another foreign network, if this is open for visitors. There must be special authentication and billing systems for mobile services in a foreign network." [Wireless LAN. Wikipedia]
This Cisco roaming wireless local area network diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Used Solutions
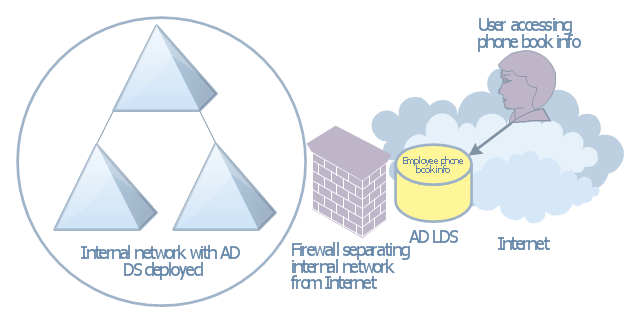
This AD diagram example was created based on the picture "AD LDS as a phone book service" from the book "Active Directory for Dummies".
"Directory services are a great way of providing information that can be fre-
quently retrieved and searched on in a hierarchical way. ... Well, there’s no reason that you can’t create a directory service that’s actually a phone book. Imagine that you need to make a searchable phone directory of your organization available on the Internet. ... This isn’t a difficult task, but it has security repercussions. If you’ve already deployed AD DS and you have the employees’ phone numbers available in that directory, it might not be a good idea to expose your AD DS environment to the Internet for security reasons. Using AD LDS is a great alternative because it can be deployed separately from AD DS and it’s designed to simply provide the information retrieval service that you need without the complications involved with Kerberos authentication and group policies." [Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "AD LDS as a phone book service" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"Directory services are a great way of providing information that can be fre-
quently retrieved and searched on in a hierarchical way. ... Well, there’s no reason that you can’t create a directory service that’s actually a phone book. Imagine that you need to make a searchable phone directory of your organization available on the Internet. ... This isn’t a difficult task, but it has security repercussions. If you’ve already deployed AD DS and you have the employees’ phone numbers available in that directory, it might not be a good idea to expose your AD DS environment to the Internet for security reasons. Using AD LDS is a great alternative because it can be deployed separately from AD DS and it’s designed to simply provide the information retrieval service that you need without the complications involved with Kerberos authentication and group policies." [Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "AD LDS as a phone book service" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
- Chart On Internet Service With Diagram
- Service Provided By Internet With Diagram
- Service -goods continuum diagram | Pyramid Chart Examples ...
- Computer Networks Service Characteristics Diagram
- Service Provided By Internet Diagram
- Copying Service Process Flowchart. Flowchart Examples | Process ...
- Different Services Provided By Internet Diagram
- Wan Network Simple Diagram Wikipedia
- Internet Service Provider Network Diagram
- Wireless Networks | How to Create a Wireless Network Diagram ...
- Satellite telecom network diagram | Mobile satellite communication ...
- How to Build Cloud Computing Diagram Principal Cloud ...
- Leaky bucket diagram | Marketing Diagrams | Bucket Theory In ...
- Wireless Internet Service Provider
- Satellite telecom network diagram | How to Build Cloud Computing ...
- Wireless broadband network diagram | Illustrate the Computer ...
- Wireless broadband network diagram | Internet Connectivity ...
- Network Security Diagrams | Network Glossary Definition | Network ...
- Local Area Network Diagram
- UML interaction overview diagram - System authentication ...