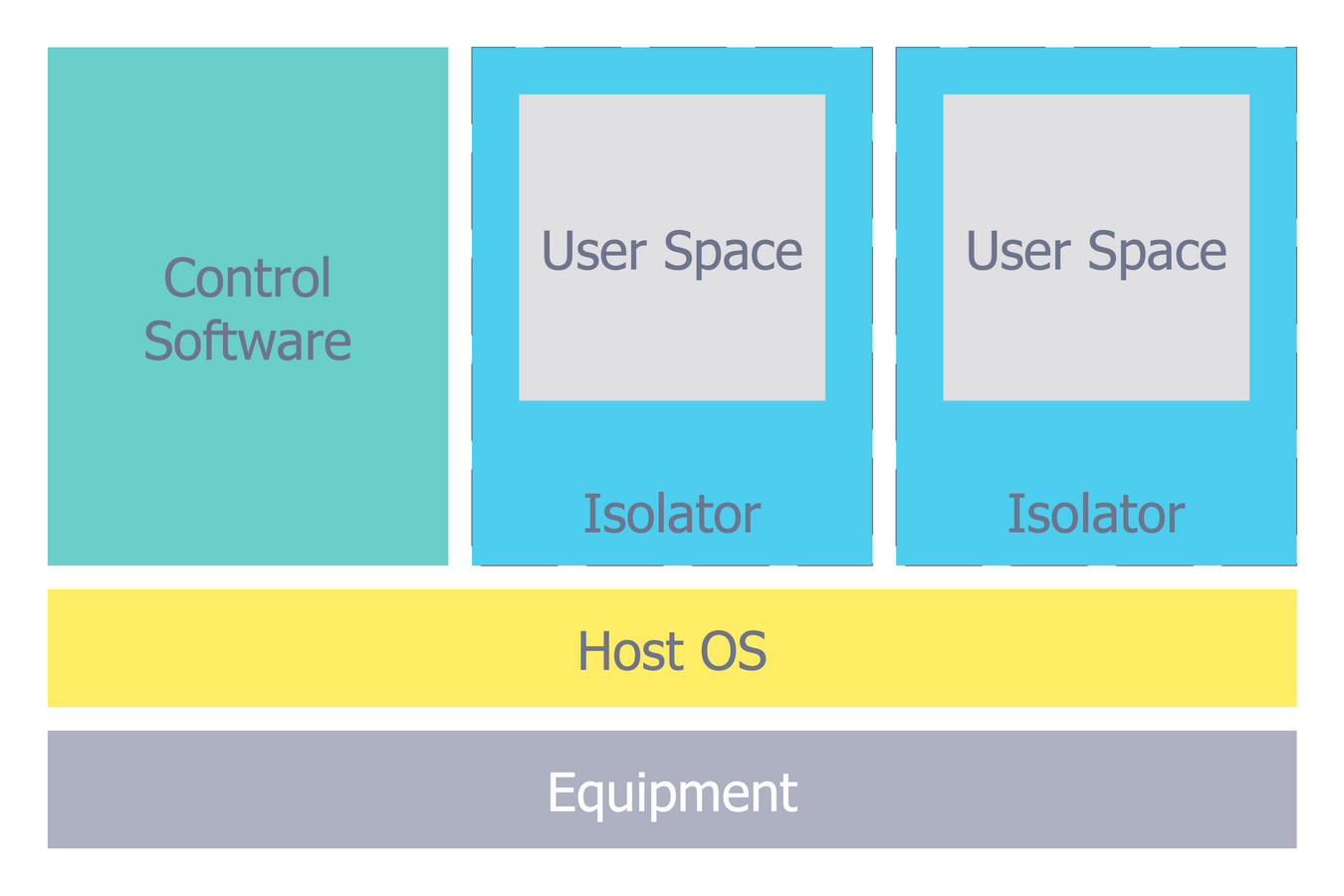
Network Security Architecture Diagram
Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram? We recommend to use ConceptDraw DIAGRAM extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.Cyber Security Degrees
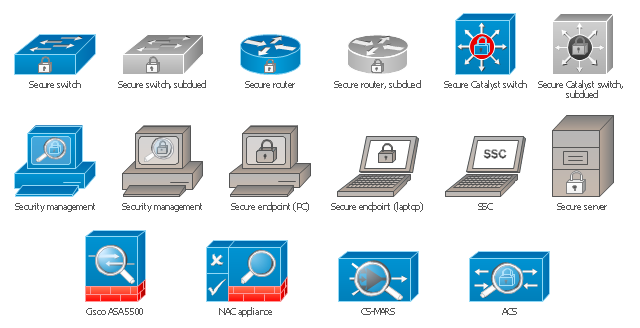
For protection various cyber environments are developed and applied large variety of cyber security standards, techniques, security concepts and approaches with different cyber security degrees. The ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park offers the number of useful tools which will help network security engineers, cyber security specialists, network and computer analysts easily and visually depict the knowledge and skills for research and prevention of intrusions, about protection critical information and analysis of cyber incidents, and for how to assess threats and vulnerabilities.The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
Network Security Diagram
ConceptDraw DIAGRAM diagramming and vector drawing software enhanced with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is the best for effective design professional, colorful and attractive Network Security Diagram of any complexity and degree of detailing.The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
 Computer and Networks Area
Computer and Networks Area
The solutions from Computer and Networks Area of ConceptDraw Solution Park collect samples, templates and vector stencils libraries for drawing computer and network diagrams, schemes and technical drawings.
Activity Network Diagram Method
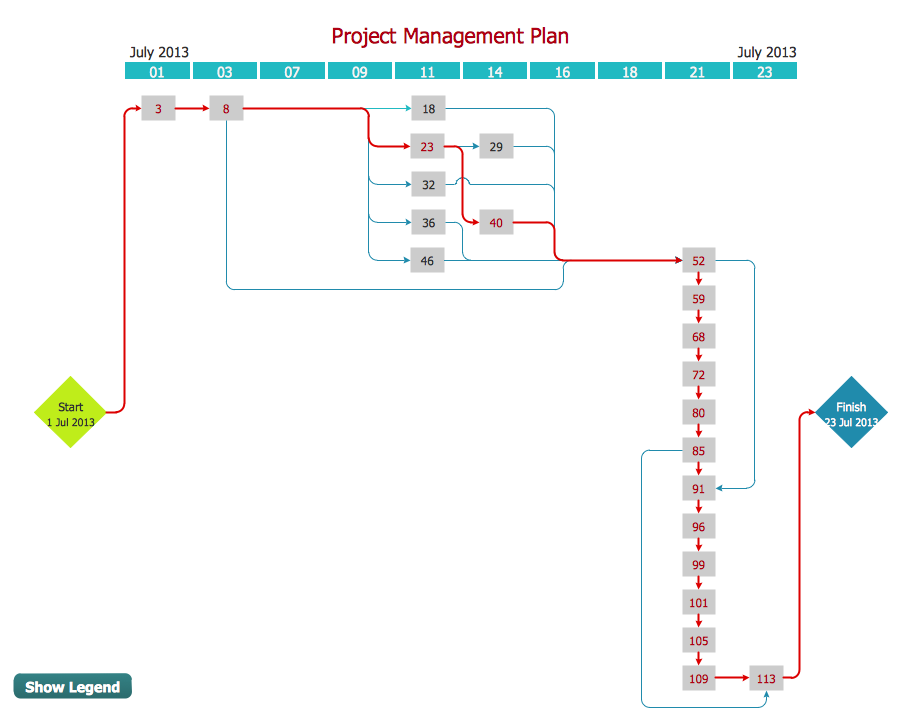
Activity Network Diagram - This sample was created in ConceptDraw DIAGRAM diagramming and vector drawing software using the Seven Management and Planning Tools solution from the Management area of ConceptDraw Solution Park. This sample shows the PERT (Program Evaluation Review Technique) chart of the request on proposal. A request for proposal (RFP) is a request of the company or the organization to potential suppliers to submit the business proposals for service or goods that it is interested to purchase. The RFP is represented on the initial procurement stage and allows to define the risks and benefits.Cloud Computing Architecture Diagrams
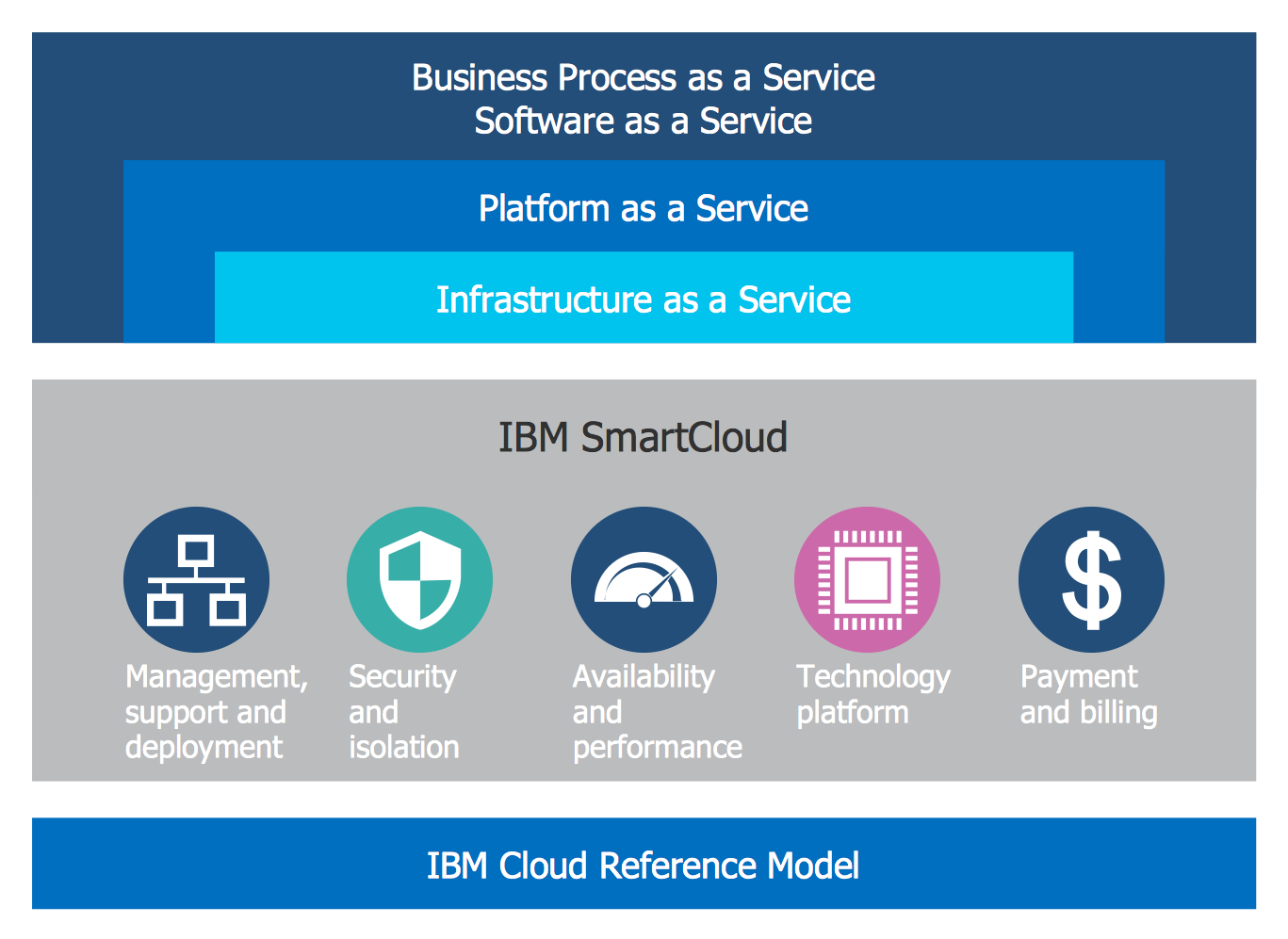
For documenting the Cloud Computing Architecture with a goal to facilitate the communication between stakeholders are successfully used the Cloud Computing Architecture diagrams. It is convenient and easy to draw various Cloud Computing Architecture diagrams in ConceptDraw DIAGRAM software with help of tools of the Cloud Computing Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw DIAGRAM software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
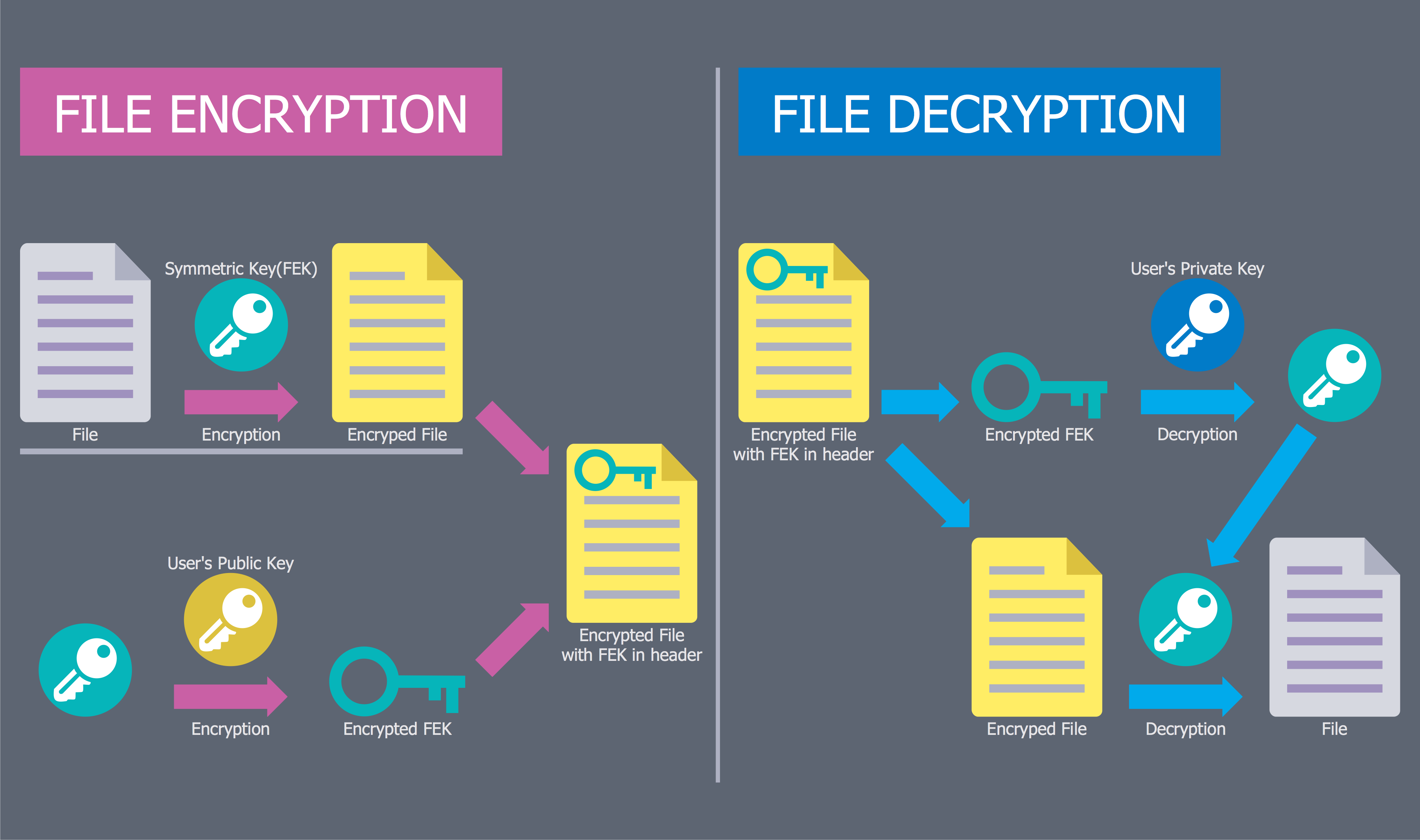
The vector stencils library "AWS Security, Identity and Compliance" contains 23 Amazon Web Services icons: AWS Directory Service, AWS Config, AWS CloudTrail, AWS Trusted Advisor, Amazon CloudWatch, Alarm. Use it to draw AWS architecture diagrams of your cloud infrastructure services.
"The AWS infrastructure puts strong safeguards in place to help protect customer privacy. All data is stored in highly secure AWS data centers. ...
AWS manages dozens of compliance programs in its infrastructure. This means that segments of your compliance have already been completed. ...
Cut costs by using AWS data centers. Maintain the highest standard of security without having to manage your own facility. ...
Security scales with your AWS cloud usage. No matter the size of your business the AWS infrastructure is designed to keep data safe." [aws.amazon.com/ security/ ]
The symbols example "AWS Security, Identity and Compliance - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"The AWS infrastructure puts strong safeguards in place to help protect customer privacy. All data is stored in highly secure AWS data centers. ...
AWS manages dozens of compliance programs in its infrastructure. This means that segments of your compliance have already been completed. ...
Cut costs by using AWS data centers. Maintain the highest standard of security without having to manage your own facility. ...
Security scales with your AWS cloud usage. No matter the size of your business the AWS infrastructure is designed to keep data safe." [aws.amazon.com/ security/ ]
The symbols example "AWS Security, Identity and Compliance - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Network Security Model
Creation of well thought-out network security model will effectively help you in realization your network's security. ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park lets fast and easy design all variety of network security models: Open network security model, Closed network security model, Restrictive network access model.Contoh Flowchart
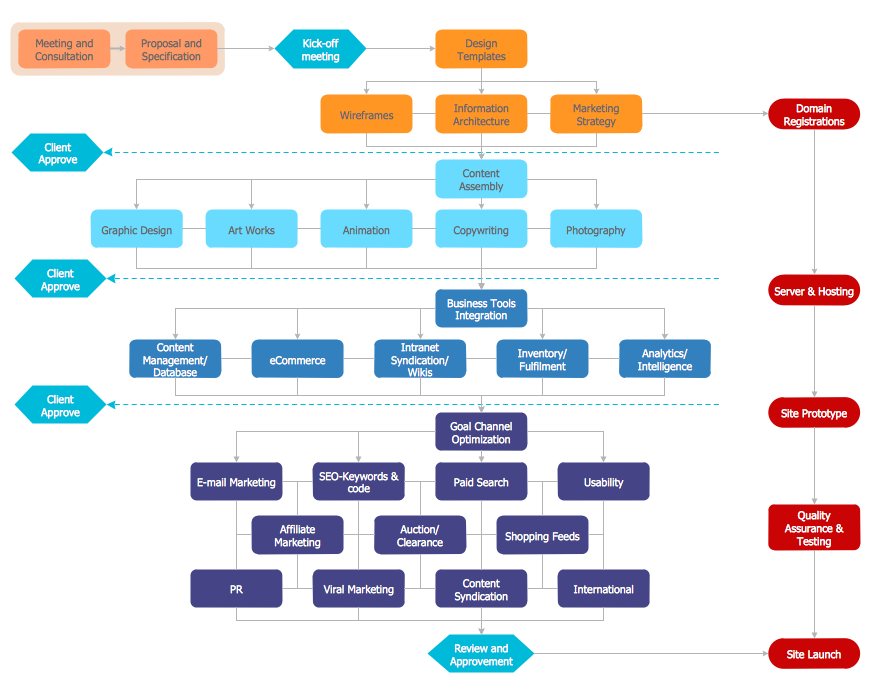
The Flowcharts are graphical representations of algorithms, processes or step-by-step solutions problems. There are many different types of Flowcharts, among them Process Flowchart, Cross Functional Flowchart, Data Flow Diagram, IDEF Flowchart, Workflow Diagram, Contoh Flowchart and many others. They have especial value when you need represent a complex process, depict in details the process of solution problems, efficiently plan and set the tasks priorities. The Flowcharts must to be constructed brief, clear and logical, simplifying the process or procedure, and making easier the comprehension and perception of information. The ConceptDraw DIAGRAM software makes the process of creating the flowcharts of any types well organized and clear for developers and customers also, including the Contoh Flowchart. It is possible due to the Flowcharts solution from ConceptDraw Solution Park, its predesigned vector objects, templates, and a lot of professional-looking practical samples and examples which can be quick and easy modified, printed, or published on web.Process Flow Maps
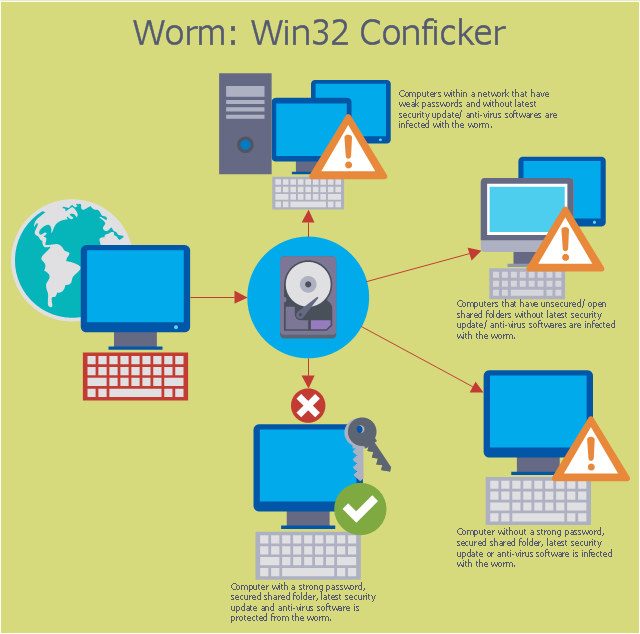
What is a Process Flow Map? It is a chart which visually illustrates a business process and how its steps work together. Process Flow Maps help companies define problem areas, inefficient activities for the purpose of further increasing performance and profitability of businesses. ConceptDraw DIAGRAM diagramming and vector drawing software extended with Flowcharts solution from the "Diagrams" area of ConceptDraw Solution Park is efficient and productive software for fast and simple creating professional looking Process Flow Map.This computer security diagram example was designed on the base of the Wikimedia Commons file: Conficker.svg. [commons.wikimedia.org/ wiki/ File:Conficker.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer." [Computer worm. Wikipedia]
The cybersecurity diagram example "Spread of Conficker worm" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer." [Computer worm. Wikipedia]
The cybersecurity diagram example "Spread of Conficker worm" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
Technical Flow Chart Example
What illustrates a technical flow chart? Technical flow chart is a diagrammatic representation which visually illustrates the sequence of operations that must to be performed to get the problem's solution. ConceptDraw DIAGRAM enhanced with Flowcharts Solution from the "Diagrams" Area of ConceptDraw Solution is a perfect software for drawing Technical Flow Chart Example illustrating the essence and importance of the technical flow chart use.- Internet Security Program
- Computer Security Program
- Network Security Diagrams | Network Security Model | Cisco security ...
- Sample Flow Diagram On Security Process
- Network Security Devices | Network Security Diagrams | Network ...
- Network Security Diagrams | Network Security | Network Security ...
- Network Security Diagrams | Network Security Architecture Diagram ...
- Windows 8 apps - Vector stencils library | Network Security Tips ...
- 10 Steps to Cyber Security | Camera layout schematic | Pyramid ...
- Security and Access Plans | How to Draw a Security and Access ...
- Network Security Devices | Secure Wireless Network | Design ...
- Cisco security - Vector stencils library | Cisco Security . Cisco icons ...
- Data Flow Diagram (DFD) | Account Flowchart. Flowchart Examples ...
- Network Security Devices | Cisco security - Vector stencils library ...
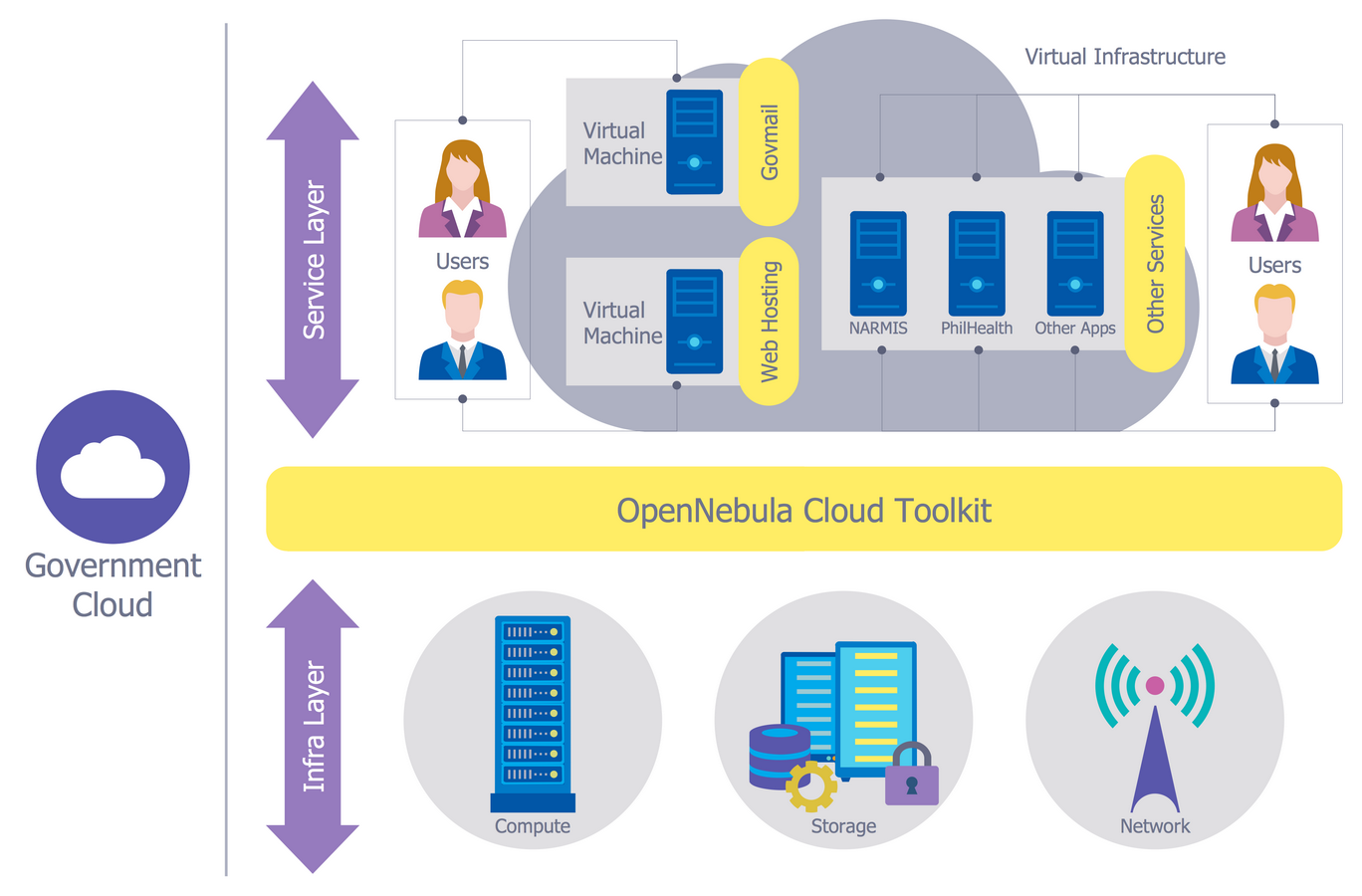
- Network Security Devices | Government Cloud | 10 Steps to Cyber ...
- Security and Access Plans | Camera layout schematic | Camera ...
- Network Security Diagrams | Computer Worms Diagram
- Audit Flowcharts | Flowcharts | Network Security Devices | Flow ...
- Network Security Architecture Diagram | Network Security Diagrams ...
- Camera layout schematic | Security and Access Plans | Camera ...






-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)











-aws-security,-identity-and-compliance---vector-stencils-library.png--diagram-flowchart-example.png)