This example was designed on the base of the diagram from the article "How secure is that mobile app?" by N.V. Fleming on the website of the U.S. Federal Trade Commission (FTC).
"Neither company validated security certificates to make sure the app was sending the information to the right place. That left users vulnerable to “man in the middle attacks.” An attacker could trick the app into letting him access communications between the app and the online service. Neither the person using the app nor the online service would know the attacker was there." [consumer.ftc.gov/ blog/ how-secure-mobile-app]
The cybersecurity diagram example "Mobile app security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Neither company validated security certificates to make sure the app was sending the information to the right place. That left users vulnerable to “man in the middle attacks.” An attacker could trick the app into letting him access communications between the app and the online service. Neither the person using the app nor the online service would know the attacker was there." [consumer.ftc.gov/ blog/ how-secure-mobile-app]
The cybersecurity diagram example "Mobile app security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
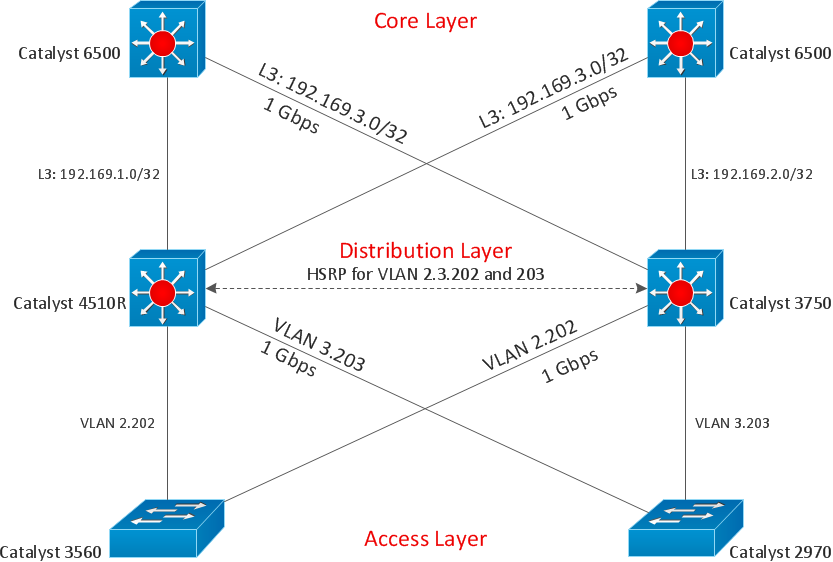
 Accounting Flowcharts
Accounting Flowcharts
Accounting Flowcharts solution extends ConceptDraw PRO software with templates, samples and library of vector stencils for drawing the accounting flow charts.
 Cisco Network Diagrams
Cisco Network Diagrams
Cisco Network Diagrams solution extends ConceptDraw PRO with the best characteristics of network diagramming software. Included samples, templates and libraries of built-in standardized vector Cisco network icons and Cisco symbols of computers, network devices, network appliances and other Cisco network equipment will help network engineers, network designers, network and system administrators, as well as other IT professionals and corporate IT departments to diagram efficiently the network infrastructure, to visualize computer networks topologies, to design Cisco computer networks, and to create professional-looking Cisco Computer network diagrams, Cisco network designs and schematics, Network maps, and Network topology diagrams in minutes.
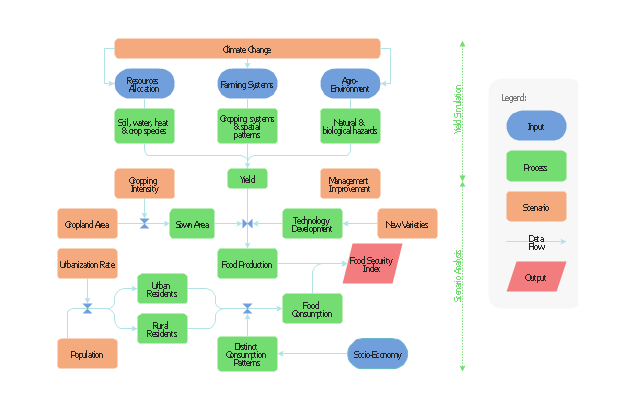
This flow chart sample was drawn on the base on the illustration of the article "Climate change impact on China food security in 2050" from the website of Chinese Academy of Agricultural Sciences .
[caas.cn/ en/ newsroom/ research_ update/ 67347.shtml]
"Food security is a condition related to the ongoing availability of food. ...
According to the Food and Agriculture Organization (FAO), food security "exists when all people, at all times, have physical and economic access to sufficient, safe and nutritious food to meet their dietary needs and food preferences for an active and healthy life". ...
Extreme events, such as droughts and floods, are forecast to increase as climate change takes hold. Ranging from overnight floods to gradually worsening droughts, these will have a range of impacts on the agricultural sector. ...
According to the Climate & Development Knowledge Network report Managing Climate Extremes and Disasters in the Agriculture Sectors: Lessons from the IPCC SREX Report, the impacts will include changing productivity and livelihood patterns, economic losses, and impacts on infrastructure, markets and food security. Food security in future will be linked to our ability to adapt agricultural systems to extreme events." [Food security. Wikipedia]
The flowchart example "Food security assessment" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Flowcharts solution from the area "What is a Diagram" of ConceptDraw Solution Park.
[caas.cn/ en/ newsroom/ research_ update/ 67347.shtml]
"Food security is a condition related to the ongoing availability of food. ...
According to the Food and Agriculture Organization (FAO), food security "exists when all people, at all times, have physical and economic access to sufficient, safe and nutritious food to meet their dietary needs and food preferences for an active and healthy life". ...
Extreme events, such as droughts and floods, are forecast to increase as climate change takes hold. Ranging from overnight floods to gradually worsening droughts, these will have a range of impacts on the agricultural sector. ...
According to the Climate & Development Knowledge Network report Managing Climate Extremes and Disasters in the Agriculture Sectors: Lessons from the IPCC SREX Report, the impacts will include changing productivity and livelihood patterns, economic losses, and impacts on infrastructure, markets and food security. Food security in future will be linked to our ability to adapt agricultural systems to extreme events." [Food security. Wikipedia]
The flowchart example "Food security assessment" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Flowcharts solution from the area "What is a Diagram" of ConceptDraw Solution Park.
 Word Exchange
Word Exchange
This solution extends ConceptDraw MINDMAP software with the ability to quickly create the framework for a future article or book, fill the structure with ideas, and use it to produce an MS Word document with just a simple click of the mouse.
 Enterprise Architecture Diagrams
Enterprise Architecture Diagrams
Enterprise Architecture Diagrams solution extends ConceptDraw PRO software with templates, samples and library of vector stencils for drawing the diagrams of enterprise architecture models.
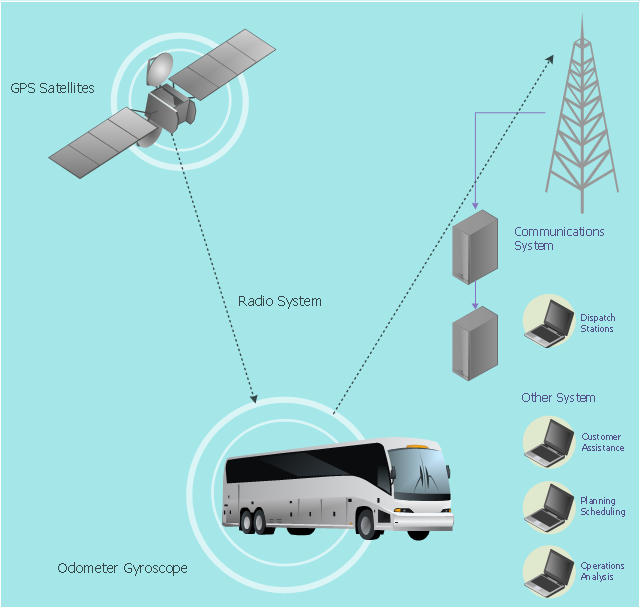
This vehicular network diagram example was drawn on the base of picture illustrating the article "Automatic Vehicle Location: Rural Transit" from the website of the Research and Innovative Technology Administration (RITA), U.S. Department of Transportation (US DOT).
"Automatic Vehicle Location (AVL) systems calculate the real-time location of any vehicle equipped with a Global Positioning Satellite (GPS) receiver. Data are then transmitted to the transit center with use of radio or cellular communications and can be used immediately for daily operations as well as archived for further analysis.
As a stand-alone technology, an AVL system can be used to monitor on-time performance. When combined with other technologies, AVL can deliver many benefits in the areas of fleet management, service planning, safety and security, traveler information, fare payment, vehicle component monitoring, and data collection. Since the greatest benefits from AVL are achieved by combining it with other Intelligent Transportation System (ITS) technologies, AVL is most appropriate for large rural agencies with more than 30 vehicles that plan to implement a comprehensive ITS."
[pcb.its.dot.gov/ factsheets/ avl/ avlRural_ overview.asp]
The vehicular network diagram example "Automatic vehicle location" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Vehicular Networking solution from the Computer and Networks area of ConceptDraw Solution Park.
"Automatic Vehicle Location (AVL) systems calculate the real-time location of any vehicle equipped with a Global Positioning Satellite (GPS) receiver. Data are then transmitted to the transit center with use of radio or cellular communications and can be used immediately for daily operations as well as archived for further analysis.
As a stand-alone technology, an AVL system can be used to monitor on-time performance. When combined with other technologies, AVL can deliver many benefits in the areas of fleet management, service planning, safety and security, traveler information, fare payment, vehicle component monitoring, and data collection. Since the greatest benefits from AVL are achieved by combining it with other Intelligent Transportation System (ITS) technologies, AVL is most appropriate for large rural agencies with more than 30 vehicles that plan to implement a comprehensive ITS."
[pcb.its.dot.gov/ factsheets/ avl/ avlRural_ overview.asp]
The vehicular network diagram example "Automatic vehicle location" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Vehicular Networking solution from the Computer and Networks area of ConceptDraw Solution Park.
Used Solutions
HelpDesk
Download and Install ConceptDraw Office on Mac
Find out how to download and install ConceptDraw software products for OS X on your computer. The download process is very simple due to the fact that all ConceptDraw applications are pooled into the ConceptDraw Office bundle. ConceptDraw STORE is a download manager that is responsible for downloading, installing, uninstalling and updating of the ConceptDraw Office for Windows and associated solutions.This Azure cloud architecture pattern diagram template was created on the base of figure in the article "Valet Key Pattern" from the Microsoft Developer Network (MSDN) website.
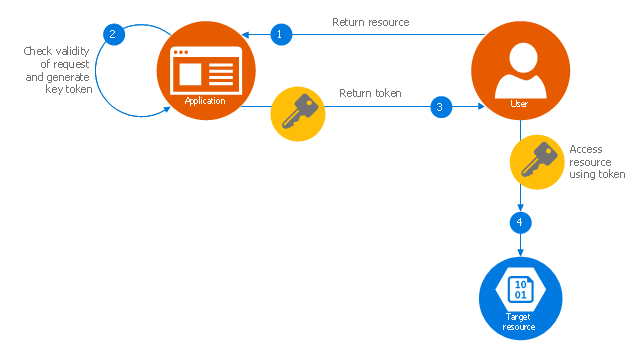
"Valet Key Pattern.
Use a token or key that provides clients with restricted direct access to a specific resource or service in order to offload data transfer operations from the application code. This pattern is particularly useful in applications that use cloud-hosted storage systems or queues, and can minimize cost and maximize scalability and performance. ...
Client programs and web browsers often need to read and write files or data streams to and from an application’s storage. ...
Data stores have the capability to handle upload and download of data directly, without requiring the application to perform any processing to move this data, but this typically requires the client to have access to the security credentials for the store.
... applications must be able to securely control access to data in a granular way, but still reduce the load on the server by setting up this connection and then allowing the client to communicate directly with the data store to perform the required read or write operations. ...
To resolve the problem of controlling access to a data store where the store itself cannot manage authentication and authorization of clients, one typical solution is to restrict access to the data store’s public connection and provide the client with a key or token that the data store itself can validate.
This key or token is usually referred to as a valet key. It provides time-limited access to specific resources and allows only predefined operations such as reading and writing to storage or queues, or uploading and downloading in a web browser. Applications can create and issue valet keys to client devices and web browsers quickly and easily, allowing clients to perform the required operations without requiring the application to directly handle the data transfer. This removes the processing overhead, and the consequent impact on performance and scalability, from the application and the server." [msdn.microsoft.com/ ru-RU/ library/ dn568102.aspx]
The Azure cloud system architecture diagram template "Valet key pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
"Valet Key Pattern.
Use a token or key that provides clients with restricted direct access to a specific resource or service in order to offload data transfer operations from the application code. This pattern is particularly useful in applications that use cloud-hosted storage systems or queues, and can minimize cost and maximize scalability and performance. ...
Client programs and web browsers often need to read and write files or data streams to and from an application’s storage. ...
Data stores have the capability to handle upload and download of data directly, without requiring the application to perform any processing to move this data, but this typically requires the client to have access to the security credentials for the store.
... applications must be able to securely control access to data in a granular way, but still reduce the load on the server by setting up this connection and then allowing the client to communicate directly with the data store to perform the required read or write operations. ...
To resolve the problem of controlling access to a data store where the store itself cannot manage authentication and authorization of clients, one typical solution is to restrict access to the data store’s public connection and provide the client with a key or token that the data store itself can validate.
This key or token is usually referred to as a valet key. It provides time-limited access to specific resources and allows only predefined operations such as reading and writing to storage or queues, or uploading and downloading in a web browser. Applications can create and issue valet keys to client devices and web browsers quickly and easily, allowing clients to perform the required operations without requiring the application to directly handle the data transfer. This removes the processing overhead, and the consequent impact on performance and scalability, from the application and the server." [msdn.microsoft.com/ ru-RU/ library/ dn568102.aspx]
The Azure cloud system architecture diagram template "Valet key pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
Cisco Design
Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park provides 14 libraries with 450 ready-to-use predesigned vector objects that can be used for quickly and easily drawing the professional Cisco Network Diagrams.How To Draw Building Plans
Building Plan is the basis for implementation construction and repair works. Creation of Building Plans is the main purpose of architects and designers. They are required and even obligatory for builders to accurately implement your wishes and ideas during the building, designing or redesigning your home, flat, office, or any other premise. ConceptDraw PRO is a powerful quick building plan software for creating great-looking Office layouts, Home floor plans, Commercial floor plans, Storage building plans, Expo and Shopping mall building plans, School and Training building plans, Cafe or Restaurant plans, Gym and Spa area plans, Sport field plans, House interior designs, Electric and Telecom building plans, Fire and Emergency plans, HVAC plans, Security and Access plans, Plumbing and Piping plans, Plant layouts, etc. Use helpful samples, templates and variety of libraries with numerous building design elements from Floor Plans solution for ConceptDraw PRO software to facilitate design drawing process.
- Mobile app security | Network Security Diagrams | IT Security ...
- Network Security Devices | Food security assessment - Flowchart ...
- Flowcharts | Food security assessment - Flowchart | Food Court ...
- Security Organizational Chart
- CCTV Network Example | Audio, Video, Media | Security and Access ...
- Security and Access Plans | How to Draw a Security and Access ...
- Food security assessment - Flowchart | Flowcharts | Contoh ...
- Basic CCTV System Diagram. CCTV Network Diagram Example ...
- CCTV Surveillance System Diagram. CCTV Network Diagram ...
- CCTV Surveillance System Diagram. CCTV Network Diagram ...
- Account Flowchart. Flowchart Examples | Budgeted appropriations ...
- How To Create CCTV Network Diagram | How to Create a CCTV ...
- Examples of Flowcharts, Org Charts and More | Bubble Diagrams ...
- CCTV Network Example | CCTV Surveillance System Diagram ...
- Block diagram - Types of individual behavior in organization | Block ...
- CCTV Network Example | CCTV Surveillance System Diagram ...
- Enterprise Architecture Diagrams | Network Diagram Software ...
- UML interaction overview diagram - System authentication ...
- Food security assessment - Flowchart | Opportunities in agro and ...
- Food security assessment - Flowchart | Weather - Vector stencils ...