Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution enhances the ConceptDraw PRO v10 functionality with large collection of predesigned vector stencils of cybersecurity clipart, shapes, icons and connectors to help you succeed in designing professional and accurate Ne
Network Security
The Internet is a giant computer network which connects computers all over the world. It is integral part of human society and business. But the serious question for network engineers, designers, lawmakers and enforcers is the need for protect the Internet networks from the Internet crimes, hacking and attacks. There are quite a number of hardware, software and physical methods of protection against them.The samples you see on this page were created in ConceptDraw PRO using the tools of Network Security Diagrams Solution for ConceptDraw PRO software. They show protection networks with Firewalls and other network security devices.
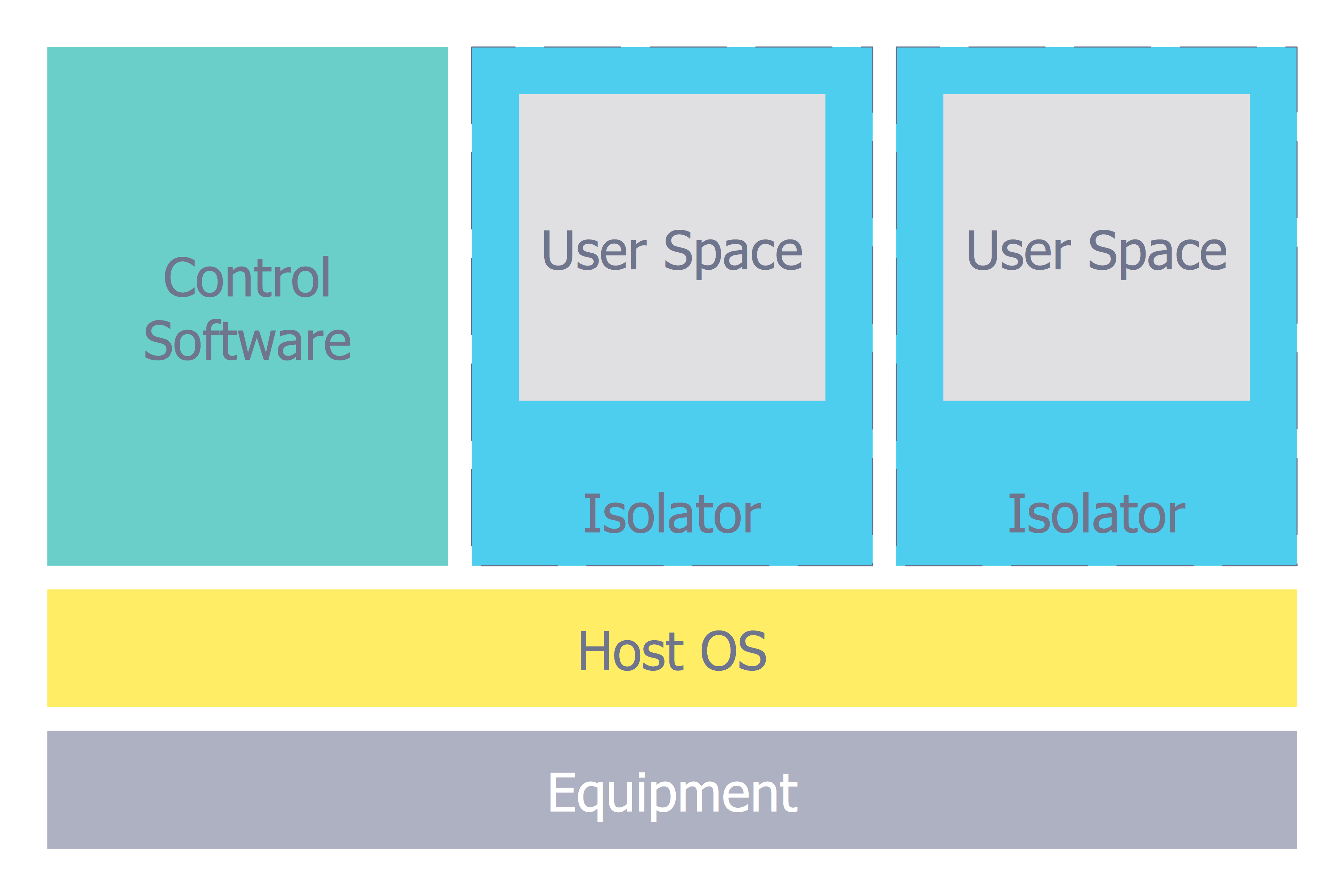
Network Security Architecture Diagram
Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram? We recommend to use ConceptDraw PRO extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.HelpDesk
How to Create a Network Security Diagram Using ConceptDraw PRO
Network security requires constant work and attention to details. Each user, whether an individual or organization, owns an information, considered to be valuable. The enforcement of network security, whether it be a local network security, or wireless network security is core for creating the secure environment of the daily working processes. Network security is accomplished through hardware and software. Network security system must be sophisticated and modern inside, but simple and understandable for the user. The visual scheme of security system can be presented in the form of a Network Security diagram. ConceptDraw PRO provides the toolkit for network security system visualization with its Network Security Diagram solution.Cyber Security Degrees
For protection various cyber environments are developed and applied large variety of cyber security standards, techniques, security concepts and approaches with different cyber security degrees. The ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park offers the number of useful tools which will help network security engineers, cyber security specialists, network and computer analysts easily and visually depict the knowledge and skills for research and prevention of intrusions, about protection critical information and analysis of cyber incidents, and for how to assess threats and vulnerabilities.Network Security Diagram
ConceptDraw PRO diagramming and vector drawing software enhanced with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is the best for effective design professional, colorful and attractive Network Security Diagram of any complexity and degree of detailing.IT Security Solutions
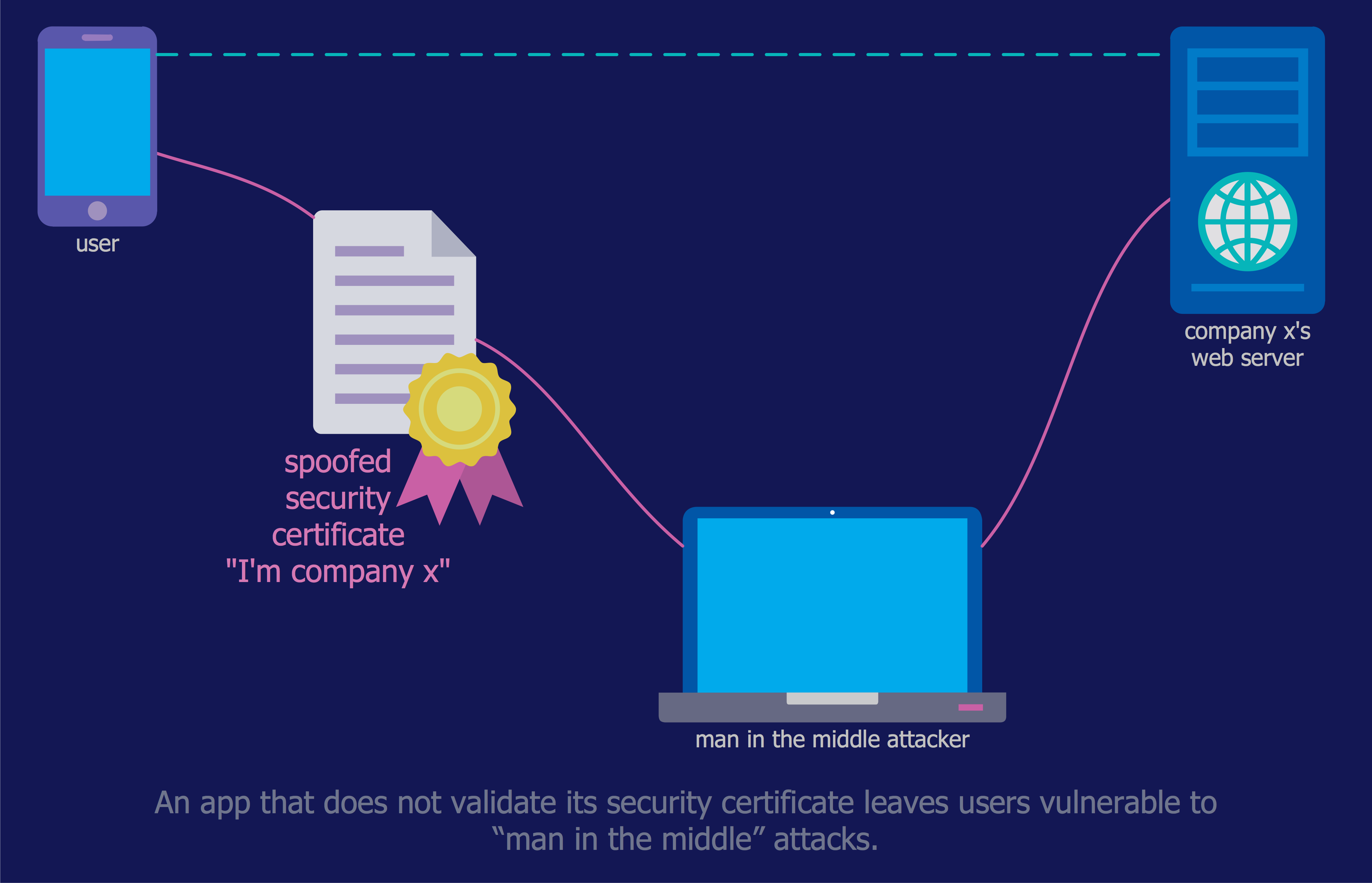
Dynamic of development computer and network technologies increases the need in modern cyber security strategies and IT security solutions to support security of your data, to ensure data privacy, and to protect your operations from the cyber threats. Thanks to the Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park, the ConceptDraw PRO diagramming and vector drawing software is one of the unique IT security solutions for professional designing Network Security Diagrams.This example was designed on the base of the diagram from the article "How secure is that mobile app?" by N.V. Fleming on the website of the U.S. Federal Trade Commission (FTC).
"Neither company validated security certificates to make sure the app was sending the information to the right place. That left users vulnerable to “man in the middle attacks.” An attacker could trick the app into letting him access communications between the app and the online service. Neither the person using the app nor the online service would know the attacker was there." [consumer.ftc.gov/ blog/ how-secure-mobile-app]
The cybersecurity diagram example "Mobile app security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Neither company validated security certificates to make sure the app was sending the information to the right place. That left users vulnerable to “man in the middle attacks.” An attacker could trick the app into letting him access communications between the app and the online service. Neither the person using the app nor the online service would know the attacker was there." [consumer.ftc.gov/ blog/ how-secure-mobile-app]
The cybersecurity diagram example "Mobile app security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
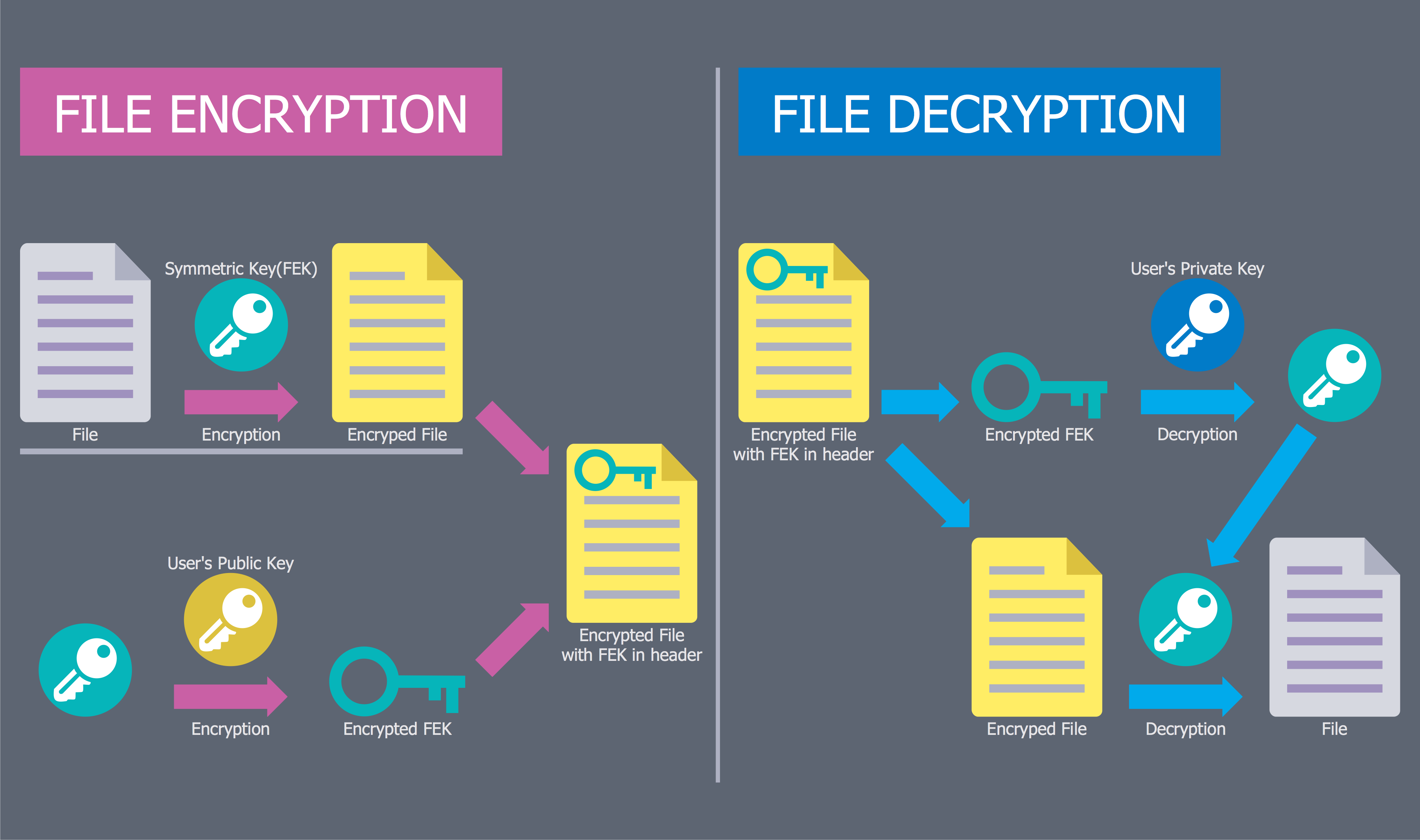
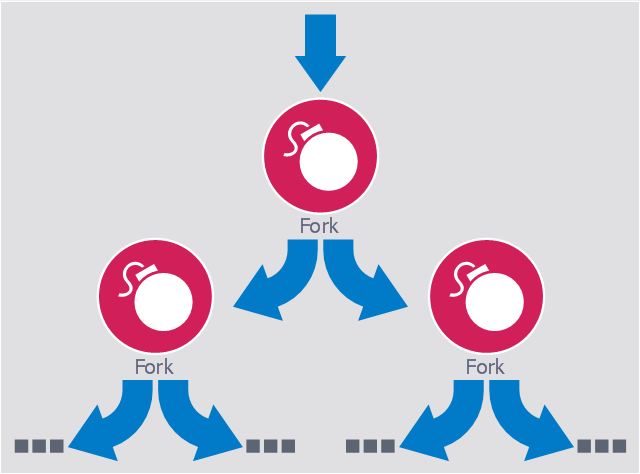
This computer security diagram example was designed on the base of the Wikimedia Commons file: Fork bomb.svg.
"Fork bomb principle. The processes are recursively forked, resulting in a saturation of the available ressources and denial of service." [commons.wikimedia.org/ wiki/ File:Fork_ bomb.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a fork bomb (also called rabbit virus or wabbit) is a denial-of-service attack wherein a process continually replicates itself to deplete available system resources, slowing down or crashing the system due to resource starvation. ...
Fork bombs operate both by consuming CPU time in the process of forking, and by saturating the operating system's process table. A basic implementation of a fork bomb is an infinite loop that repeatedly launches the same process." [Fork bomb. Wikipedia]
The cybersecurity diagram example "Fork bomb" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Fork bomb principle. The processes are recursively forked, resulting in a saturation of the available ressources and denial of service." [commons.wikimedia.org/ wiki/ File:Fork_ bomb.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a fork bomb (also called rabbit virus or wabbit) is a denial-of-service attack wherein a process continually replicates itself to deplete available system resources, slowing down or crashing the system due to resource starvation. ...
Fork bombs operate both by consuming CPU time in the process of forking, and by saturating the operating system's process table. A basic implementation of a fork bomb is an infinite loop that repeatedly launches the same process." [Fork bomb. Wikipedia]
The cybersecurity diagram example "Fork bomb" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
- Network Security Diagrams | Advanced persistent threat lifecycle ...
- Internet symbols - Vector stencils library | | Network Security ...
- Network Security Model | Network Security | Secure Wireless ...
- Network Security | Types of Flowchart - Overview | Process ...
- Fork bomb | IT Security Solutions | Network Security Diagrams ...
- Network Security Tips | Network Security Diagrams | ConceptDraw ...
- How to Create a Network Security Diagram Using ConceptDraw PRO
- Design elements - Cybersecurity shapes | Cyber Security Degrees ...
- Design elements - Cybersecurity round icons | Cyber Security ...
- Network Security | Network Security Model | ConceptDraw PRO ...
- Secure Wireless Network | Network Security Diagrams ...
- Network Security Devices | Network Security | Network Security ...
- Cyber Security Degrees | | Network Security Devices | Cyber ...
- Network Security | Hotel Network Topology Diagram | Cisco Network ...
- Active Directory Diagrams | Network Security | Draw The Diagram Of ...
- Design elements - Cybersecurity clipart | Cyber Security Degrees ...
- ConceptDraw PRO Network Diagram Tool | Computer and Networks ...
- Design elements - Cybersecurity connectors | Cyber Security ...
- Mobile app security | Network Security Diagrams | IT Security ...
- Recommended network architecture for BlackBerry SWS | Network ...