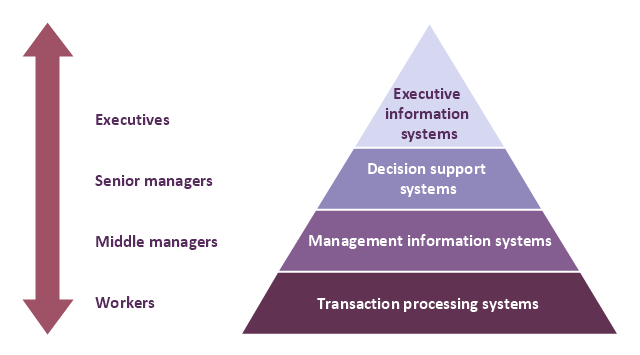
A four level pyramid model of different types of Information Systems based on the different levels of hierarchy in an organization. The first level represents transaction processing systems for workers. The second level represents management information systems for middle managers. The third level represents decision support systems for senior menegers. The fourth level represents executive information systems for executives.
"The "classic" view of Information systems found in the textbooks in the 1980s was of a pyramid of systems that reflected the hierarchy of the organization, usually transaction processing systems at the bottom of the pyramid, followed by management information systems, decision support systems, and ending with executive information systems at the top. Although the pyramid model remains useful, since it was first formulated a number of new technologies have been developed and new categories of information systems have emerged, some of which no longer fit easily into the original pyramid model.
Some examples of such systems are:
data warehouses,
enterprise resource planning,
enterprise systems,
expert systems,
search engines,
geographic information system,
global information system,
office automation." [Information systems. Wikipedia]
This diagram was redesigned using the ConceptDraw PRO diagramming and vector drawing software from Wikimedia Commons file Four-Level-Pyramid-model.png. [commons.wikimedia.org/ wiki/ File:Four-Level-Pyramid-model.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
The triangle chart example "Information systems types" is included in the Pyramid Diagrams solution from the Marketing area of ConceptDraw Solution Park.
"The "classic" view of Information systems found in the textbooks in the 1980s was of a pyramid of systems that reflected the hierarchy of the organization, usually transaction processing systems at the bottom of the pyramid, followed by management information systems, decision support systems, and ending with executive information systems at the top. Although the pyramid model remains useful, since it was first formulated a number of new technologies have been developed and new categories of information systems have emerged, some of which no longer fit easily into the original pyramid model.
Some examples of such systems are:
data warehouses,
enterprise resource planning,
enterprise systems,
expert systems,
search engines,
geographic information system,
global information system,
office automation." [Information systems. Wikipedia]
This diagram was redesigned using the ConceptDraw PRO diagramming and vector drawing software from Wikimedia Commons file Four-Level-Pyramid-model.png. [commons.wikimedia.org/ wiki/ File:Four-Level-Pyramid-model.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
The triangle chart example "Information systems types" is included in the Pyramid Diagrams solution from the Marketing area of ConceptDraw Solution Park.
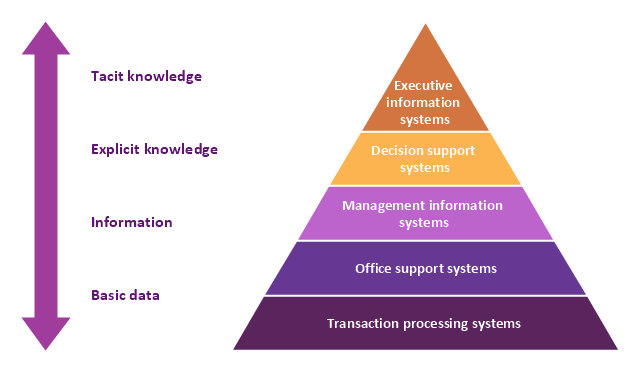
A five level pyramid model of different types of Information Systems based on the information processing requirement of different levels in the organization. The first level represents transaction processing systems to process basic data. The second level represents office support systems to process information in office. The third level represents management information systems to process information by managers. The fourth level represents decision support systems to process explicit knowledge. The fifth level represents executive information systems to process tacit knowledge.
"A Computer(-Based) Information System is essentially an IS using computer technology to carry out some or all of its planned tasks. The basic components of computer based information system are:
(1) Hardware - these are the devices like the monitor, processor, printer and keyboard, all of which work together to accept, process, show data and information.
(2) Software - are the programs that allow the hardware to process the data.
(3) Databases - are the gathering of associated files or tables containing related data.
(4) Networks - are a connecting system that allows diverse computers to distribute resources.
(5) Procedures - are the commands for combining the components above to process information and produce the preferred output.
The first four components (hardware, software, database and network) make up what is known as the information technology platform. Information technology workers could then use these components to create information systems that watch over safety measures, risk and the management of data. These actions are known as information technology services." [Information systems. Wikipedia]
This pyramid diagram was redesigned using the ConceptDraw PRO diagramming and vector drawing software from Wikimedia Commons file Five-Level-Pyramid-model.png. [commons.wikimedia.org/ wiki/ File:Five-Level-Pyramid-model.png]
This file is licensed under the Creative Commons Attribution 3.0 Unported license. [creativecommons.org/ licenses/ by/ 3.0/ deed.en]
The triangle chart example "Information systems types" is included in the Pyramid Diagrams solution from the Marketing area of ConceptDraw Solution Park.
"A Computer(-Based) Information System is essentially an IS using computer technology to carry out some or all of its planned tasks. The basic components of computer based information system are:
(1) Hardware - these are the devices like the monitor, processor, printer and keyboard, all of which work together to accept, process, show data and information.
(2) Software - are the programs that allow the hardware to process the data.
(3) Databases - are the gathering of associated files or tables containing related data.
(4) Networks - are a connecting system that allows diverse computers to distribute resources.
(5) Procedures - are the commands for combining the components above to process information and produce the preferred output.
The first four components (hardware, software, database and network) make up what is known as the information technology platform. Information technology workers could then use these components to create information systems that watch over safety measures, risk and the management of data. These actions are known as information technology services." [Information systems. Wikipedia]
This pyramid diagram was redesigned using the ConceptDraw PRO diagramming and vector drawing software from Wikimedia Commons file Five-Level-Pyramid-model.png. [commons.wikimedia.org/ wiki/ File:Five-Level-Pyramid-model.png]
This file is licensed under the Creative Commons Attribution 3.0 Unported license. [creativecommons.org/ licenses/ by/ 3.0/ deed.en]
The triangle chart example "Information systems types" is included in the Pyramid Diagrams solution from the Marketing area of ConceptDraw Solution Park.
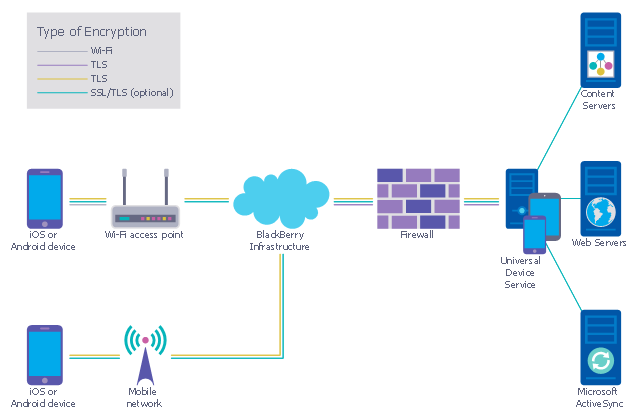
This example was designed on the base of the diagram from the "BYOD Guidance: BlackBerry Secure Work Space" on the website of the UK Communications Electronics Security Group (CESG).
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
- 4 Level pyramid model diagram - Information systems types ...
- Chart Of Management Information System With Diagram
- Info About System Level Of Organisation
- 5 Level pyramid model diagram - Information systems types ...
- 4 Level pyramid model diagram - Information systems types
- Organisation Information System Level
- Levels Of An Organisation Information
- System Level Organisation Information
- Drawing Of Levels Of Organisation
- Types Of Information Flow In An Organisation
- Information Sytem That Serve Each Level Of Organisation
- What Are Three Levels Of Information In Organisation
- Pyramid Diagram | 4 Level pyramid model diagram - Information ...
- Identify The Difference Level Found Organisations Hierarchy And
- Pyramid Diagram | 4 Level pyramid model diagram - Information ...
- 5 Level pyramid model diagram - Information systems types | Major ...
- Level Of Organisation Hirarchy In Information Management
- Pyramid Diagram | 4 Level pyramid model diagram - Information ...
- Hierarchical Pyramid On How Information Flow In An Organisation
- Four Levels Of Organisation Hierachy