The vector stencils library "Active Directory" contains 20 symbols of Active Directory elements for drawing AD network diagrams. It helps network and system administrators to visualize Microsoft Windows Active Directory structures for network design, installation and maintainance.
"An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The AD symbols example "Active Directory - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
"An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The AD symbols example "Active Directory - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
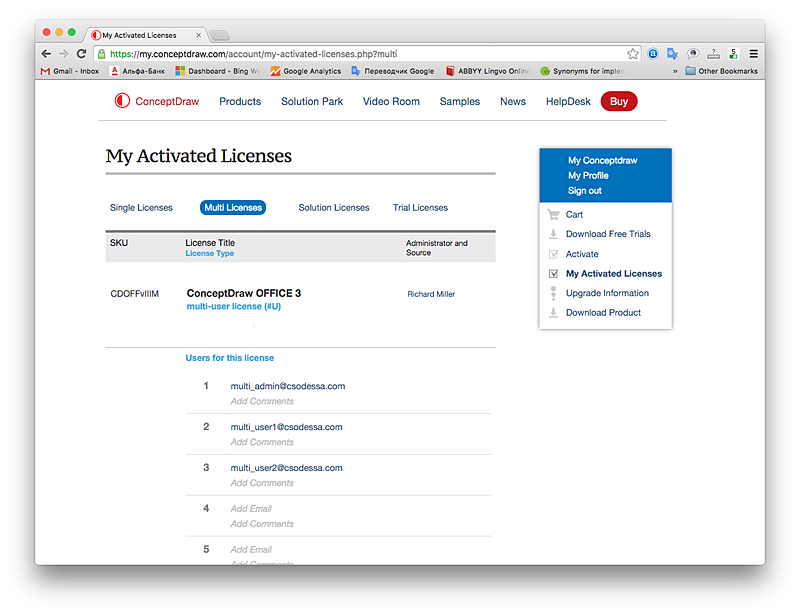
The vector stencils library "Microsoft Exchange" contains 17 symbols of Microsoft Exchange elements for drawing the logical structure diagrams of Active Directory trees.
"Windows Messaging, initially called Microsoft Exchange, is an e-mail client that was included with Windows 95 (beginning with OSR2), 98 and Windows NT 4.0. ...
Microsoft Exchange gained wide usage with the release of Windows 95, as this was the only mail client that came bundled with it. In 1996, it was renamed to Windows Messaging, because of the upcoming release of Microsoft Exchange Server, and continued to be included throughout later releases of Windows up until the initial release of Windows 98, which by then included Outlook Express 4.0 as the default mail client.
The Windows Messaging email client had two branches of successors:
(1) In software bundled with Windows itself, these were Internet Mail and News in Windows 95 (and bundled with Internet Explorer 3), which was succeeded by Outlook Express 4.0 in Windows 98 (bundled with Internet Explorer 4.0 in Windows 95) and throughout newer Windows systems. These did not use the .pst file type.
(2) Microsoft Outlook became the professional-grade and more direct successor of MS Exchange Client, which still uses the .pst file type." [Windows Messaging. Wikipedia]
The symbols example "Microsoft Exchange - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
"Windows Messaging, initially called Microsoft Exchange, is an e-mail client that was included with Windows 95 (beginning with OSR2), 98 and Windows NT 4.0. ...
Microsoft Exchange gained wide usage with the release of Windows 95, as this was the only mail client that came bundled with it. In 1996, it was renamed to Windows Messaging, because of the upcoming release of Microsoft Exchange Server, and continued to be included throughout later releases of Windows up until the initial release of Windows 98, which by then included Outlook Express 4.0 as the default mail client.
The Windows Messaging email client had two branches of successors:
(1) In software bundled with Windows itself, these were Internet Mail and News in Windows 95 (and bundled with Internet Explorer 3), which was succeeded by Outlook Express 4.0 in Windows 98 (bundled with Internet Explorer 4.0 in Windows 95) and throughout newer Windows systems. These did not use the .pst file type.
(2) Microsoft Outlook became the professional-grade and more direct successor of MS Exchange Client, which still uses the .pst file type." [Windows Messaging. Wikipedia]
The symbols example "Microsoft Exchange - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
The vector stencils library "Management pictograms" contains 72 management pictograms.
Use it to create your management infogram in the ConceptDraw PRO diagramming and vector drawing software.
The flat icons example "Management pictograms - Vector stencils library" is included in the solution "Marketing infographics" from the "Business infographics" area of ConceptDraw Solution Park.
Use it to create your management infogram in the ConceptDraw PRO diagramming and vector drawing software.
The flat icons example "Management pictograms - Vector stencils library" is included in the solution "Marketing infographics" from the "Business infographics" area of ConceptDraw Solution Park.
ConceptDraw Arrows10 Technology
When you are connecting existing objects you can control the diagram structure by changing selection order. This is how diagramming software should work. You are able to draw a diagram as quickly as the ideas come to you.HelpDesk
How to Update ConceptDraw products
The latest ConceptDraw OFFICE includes ConceptDraw MINDMAP , ConceptDraw PROJECT v9, ConceptDraw DIAGRAM v12. ConceptDraw products are constantly improving: boosting performance, enhancing functionality, fixing bugs and more. Updates are available to all ConceptDraw OFFICE users with no additional charges. ConceptDraw STORE helps to keep the installed software up-to-date, by notifying a user of any new updates and managing the downloading and installation. Using ConceptDraw STORE you can easily download and update ConceptDraw products and solutions.This AD diagram example was redesigned from the picture "Asymmetric
encryption" from the book "Active Directory for Dummies".
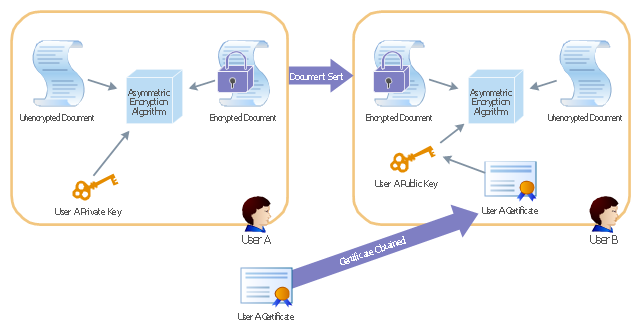
"Asymmetric Encryption:
This scenario uses a public and private key pair that is associated with each other. With this type of encryption, one of the keys is used to encrypt the data in such a way that only the corresponding second key is capable of decrypting the information. ...
In asymmetric encryption, two different keys are involved in the process: one for encrypting the document and a different but related key for decrypting the document. The two keys are generated at the same time so that if a document is encrypted with one of the keys, only the second related key can decrypt the document. ... Typically, these keys are referred to as a private key and a public key. A private key is one that is generated for a particular user and is never shared with any other user or computer. A public key is typically one of the pieces of data that’s stored in a PKI certificate. Although this type of encryption creates a very secure way of sharing data, an added benefit is you knowing that a piece of data decrypted by using a particular user’s public key must have come from that user because no other user would have the private key the document was encrypted with."
[Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Asymmetric encryption" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
encryption" from the book "Active Directory for Dummies".
"Asymmetric Encryption:
This scenario uses a public and private key pair that is associated with each other. With this type of encryption, one of the keys is used to encrypt the data in such a way that only the corresponding second key is capable of decrypting the information. ...
In asymmetric encryption, two different keys are involved in the process: one for encrypting the document and a different but related key for decrypting the document. The two keys are generated at the same time so that if a document is encrypted with one of the keys, only the second related key can decrypt the document. ... Typically, these keys are referred to as a private key and a public key. A private key is one that is generated for a particular user and is never shared with any other user or computer. A public key is typically one of the pieces of data that’s stored in a PKI certificate. Although this type of encryption creates a very secure way of sharing data, an added benefit is you knowing that a piece of data decrypted by using a particular user’s public key must have come from that user because no other user would have the private key the document was encrypted with."
[Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Asymmetric encryption" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Prioritization Matrix
You can design the Prioritization Matrix by hand on the paper, but we offer you the most easier way - to use the ConceptDraw DIAGRAM diagramming and vector drawing software extended with Seven Management and Planning Tools Solution from the Management Area.The vector stencils library "Active Directory" contains 20 symbols of Active Directory elements for drawing AD network diagrams. It helps network and system administrators to visualize Microsoft Windows Active Directory structures for network design, installation and maintainance.
"An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The AD symbols example "Active Directory - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
"An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The AD symbols example "Active Directory - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
HelpDesk
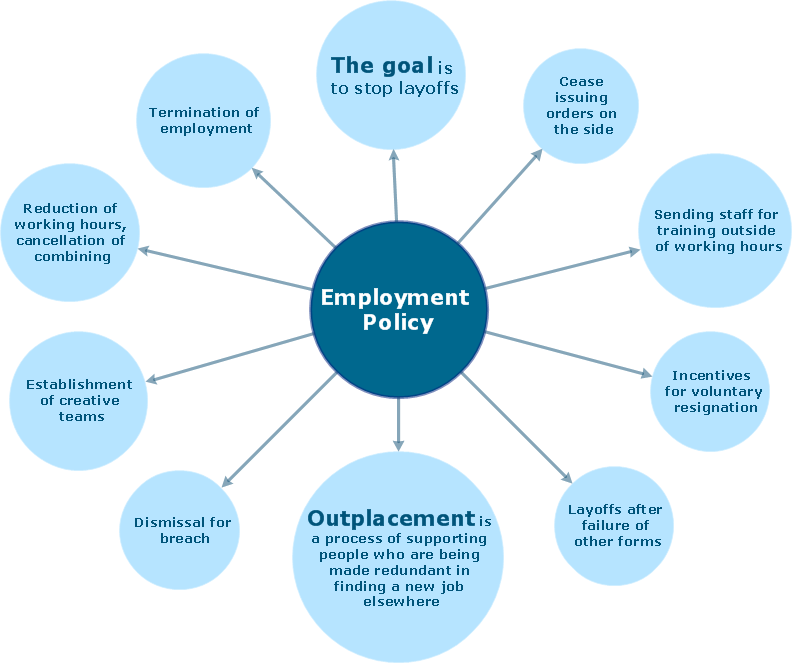
How to Track Multiple Licenses in Your Organization
Our goal behind CS Odessa’s Licensing Policy is to deliver the best value on ConceptDraw Products.The vector stencils library "Microsoft Exchange" contains 17 symbols of Microsoft Exchange elements for drawing the logical structure diagrams of Active Directory trees.
"Microsoft Exchange Server is calendaring software, a mail server and contact manager developed by Microsoft. It is a server program that runs on Windows Server and is part of the Microsoft Servers line of products." [Microsoft Exchange Server. Wikipedia]
The shapes example "Design elements - Microsoft Exchange" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"Microsoft Exchange Server is calendaring software, a mail server and contact manager developed by Microsoft. It is a server program that runs on Windows Server and is part of the Microsoft Servers line of products." [Microsoft Exchange Server. Wikipedia]
The shapes example "Design elements - Microsoft Exchange" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
- Group Policy Diagram Windows
- Flow Chart Of Policy Management
- Insurance Policy Diagrams And Flow Chart
- Business Policy Concept Map
- Examples Of Diagram Of Business Policy
- Warehouse Policy Sample
- Dfd Of Policy Management System
- Block Diagram Of Security Policy And Other Diagram
- Policy Concept Map
- Cyber Security Policy