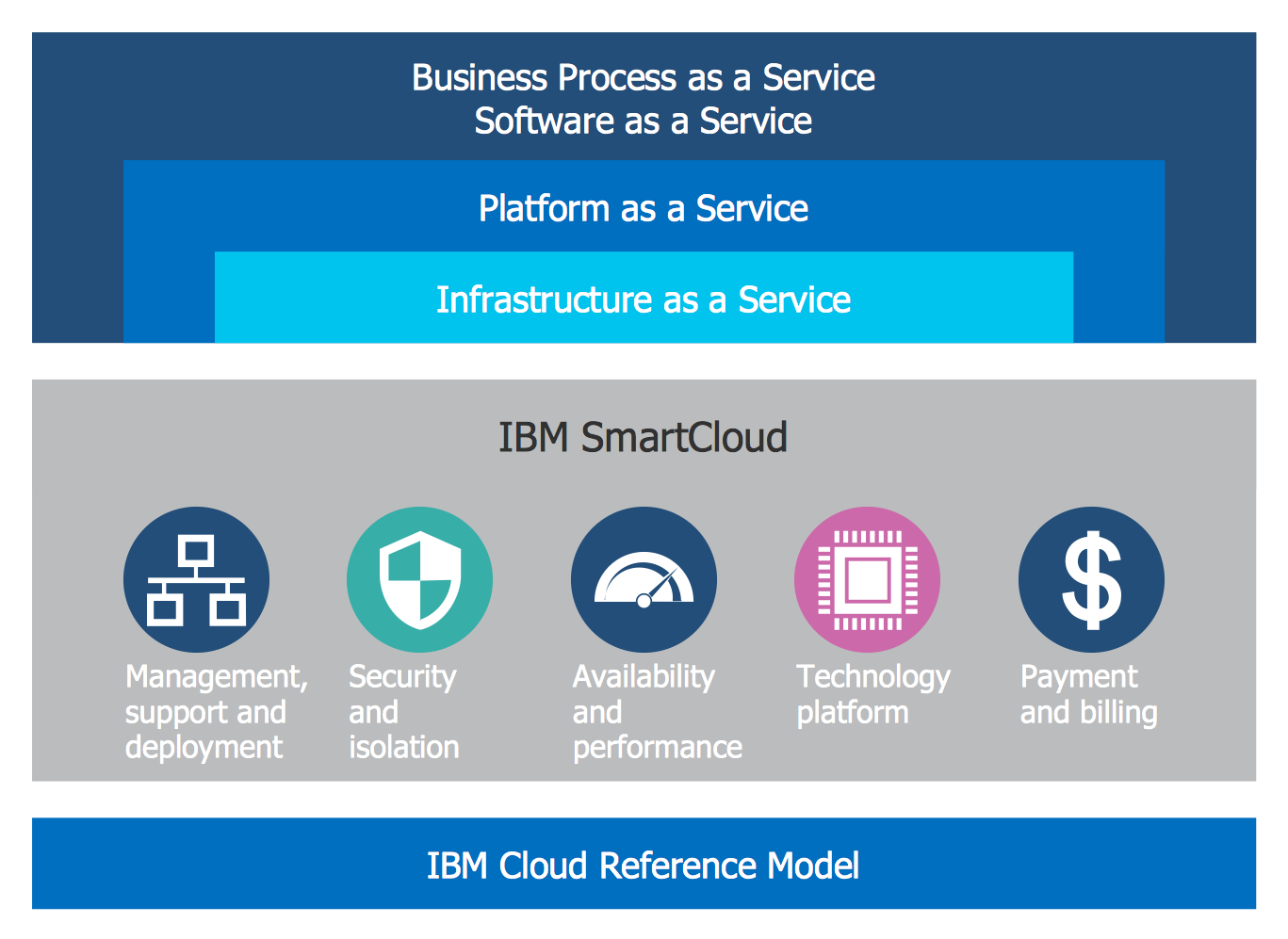
Cloud Computing Architecture Diagrams
For documenting the Cloud Computing Architecture with a goal to facilitate the communication between stakeholders are successfully used the Cloud Computing Architecture diagrams. It is convenient and easy to draw various Cloud Computing Architecture diagrams in ConceptDraw PRO software with help of tools of the Cloud Computing Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.HelpDesk
How to Create a Network Security Diagram Using ConceptDraw PRO
Network security requires constant work and attention to details. Each user, whether an individual or organization, owns an information, considered to be valuable. The enforcement of network security, whether it be a local network security, or wireless network security is core for creating the secure environment of the daily working processes. Network security is accomplished through hardware and software. Network security system must be sophisticated and modern inside, but simple and understandable for the user. The visual scheme of security system can be presented in the form of a Network Security diagram. ConceptDraw PRO provides the toolkit for network security system visualization with its Network Security Diagram solution.Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution enhances the ConceptDraw PRO v10 functionality with large collection of predesigned vector stencils of cybersecurity clipart, shapes, icons and connectors to help you succeed in designing professional and accurate Ne
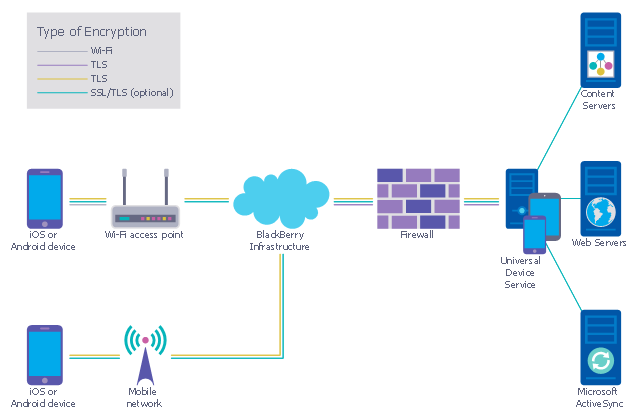
This example was designed on the base of the diagram from the "BYOD Guidance: BlackBerry Secure Work Space" on the website of the UK Communications Electronics Security Group (CESG).
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
 AWS Architecture Diagrams
AWS Architecture Diagrams
The flexible AWS cloud solutions will help you to create reliable applications with a high level of scaling in the AWS cloud, to run your applications and accelerate their work on the level of security. Besides AWS resources are available worldwide and yo
Daisy Chain Network Topology
This sample was created in ConceptDraw PRO diagramming and vector drawing software using the Computer and Networks solution from Computer and Networks area of ConceptDraw Solution Park. A Daisy Chain is the simple computer network. It is the easiest way to add more Ethernet devices into the network. In the Daisy Chain network one computer is connected to the next without any intervening devices, thus the message is sent from one computer to the next and then to the next and so on. A Daisy Chain can be linear or ring
 Block Diagrams
Block Diagrams
Block diagrams solution extends ConceptDraw PRO software with templates, samples and libraries of vector stencils for drawing the block diagrams.
"A document management system (DMS) is a computer system (or set of computer programs) used to track and store electronic documents. It is usually also capable of keeping track of the different versions modified by different users (history tracking). The term has some overlap with the concepts of content management systems. It is often viewed as a component of enterprise content management (ECM) systems and related to digital asset management, document imaging, workflow systems and records management systems. ...
Document management systems commonly provide storage, versioning, metadata, security, as well as indexing and retrieval capabilities." [Document management system. Wikipedia]
The block diagram example "Document management system architecture" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Block Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
Document management systems commonly provide storage, versioning, metadata, security, as well as indexing and retrieval capabilities." [Document management system. Wikipedia]
The block diagram example "Document management system architecture" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Block Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
 ConceptDraw Solution Park
ConceptDraw Solution Park
ConceptDraw Solution Park collects graphic extensions, examples and learning materials
 Security and Access Plans
Security and Access Plans
This solution extends ConceptDraw PRO software with physical security plan, security chart, access chart, security plans, access schemes, access plans , CCTV System Plan samples, templates and libraries of design elements for drawing the Security and Acce
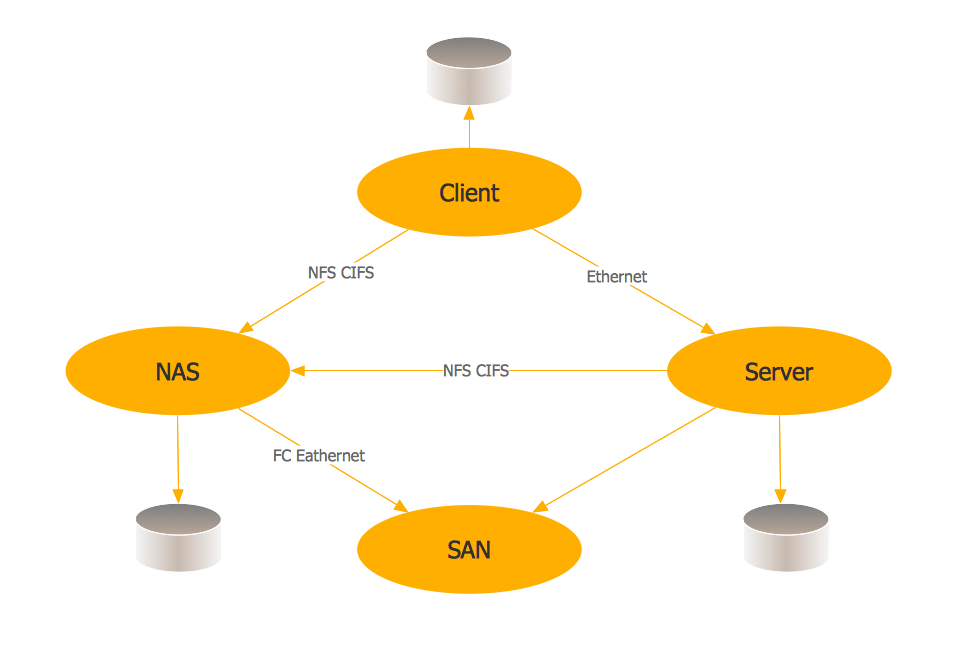
Storage area networks (SAN). Computer and Network Examples
A Storage area network (SAN) is a dedicated network that provides access to data storage and operations only on the block level. SAN usually has own network of storage devices/elements and disk arrays that are connected with each other and to a remote data-sharing network. SANs are widely used for enhancing the storage devices (optical jukeboxes, disk arrays, tape libraries) that are accessible for networked servers. This example was created in ConceptDraw PRO using the Computer and Networks Area of ConceptDraw Solution Park. It shows the hybrid of Storage area network (SAN) and Network Attached Storage (NAS) technologies.
Cisco Buildings. Cisco icons, shapes, stencils and symbols
Cisco icons are globally recognized and generally accepted as standard for network icon topologies. The ConceptDraw vector stencils library "Cisco buildings" contains 21 symbols for drawing the computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
 Safety and Security
Safety and Security
Safety and security solution extends ConceptDraw PRO software with illustration samples, templates and vector stencils libraries with clip art of fire safety, access and security equipment.
 Azure Architecture
Azure Architecture
Create Microsoft Azure architecture diagrams using icons and templates regarding Azure management, Azure storage and Azure services.
- Cloud Computing Security Architecture Using Block Diagram
- Network Security Diagrams | Network Security Architecture Diagram ...
- Network Security Devices | Block Diagrams | How to Create a ...
- Cloud Computing Architecture Diagrams | ConceptDraw Solution ...
- Network Security Architecture Diagram | How to Create a Network ...
- Network Security Model | Network Security Architecture Diagram ...
- Network Security Devices | Network Security Diagrams | Storage ...
- Network Security Model | Network Security Diagram | Network ...
- Network Security Devices | Network Security Diagram | Network ...
- Network Security Devices | Block Diagrams | ConceptDraw Solution ...
- Network Security Diagrams | How to Create a Network Security ...
- Security Model With Block Diagram
- Diagram Of Various Security Attack
- Block Diagrams | Network Security Diagrams | Campus Area ...
- Network Security Devices | Cloud Computing Architecture Diagrams ...
- Network Security Block Diagram And Explanation
- Enterprise Architecture Diagrams | Computer Network Architecture ...
- Network Security Block Diagram
- AWS Architecture Diagrams | Block Diagrams | Safety and Security ...
- Cloud Computing Architecture Diagrams | Cloud Computing ...