This computer security diagram example was designed on the base of the Wikimedia Commons file: Firewall.png.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
The vector stencils library "Access and security" contains 17 clipart images of access control and security system equipment which you can easy use in your diagrams and illustrations.
"Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources, and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physical security involves the use of multiple layers of interdependent systems which include CCTV surveillance, security guards, protective barriers, locks, access control protocols, and many other techniques." [Physical security. Wikipedia]
The clip art example "Access and security - Vector stencils library" was created in the ConceptDraw PRO diagramming and vector drawing software using the Presentation Clipart solution from the Illustration area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ illustrations-presentation-clipart
"Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources, and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physical security involves the use of multiple layers of interdependent systems which include CCTV surveillance, security guards, protective barriers, locks, access control protocols, and many other techniques." [Physical security. Wikipedia]
The clip art example "Access and security - Vector stencils library" was created in the ConceptDraw PRO diagramming and vector drawing software using the Presentation Clipart solution from the Illustration area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ illustrations-presentation-clipart
Network Security Devices
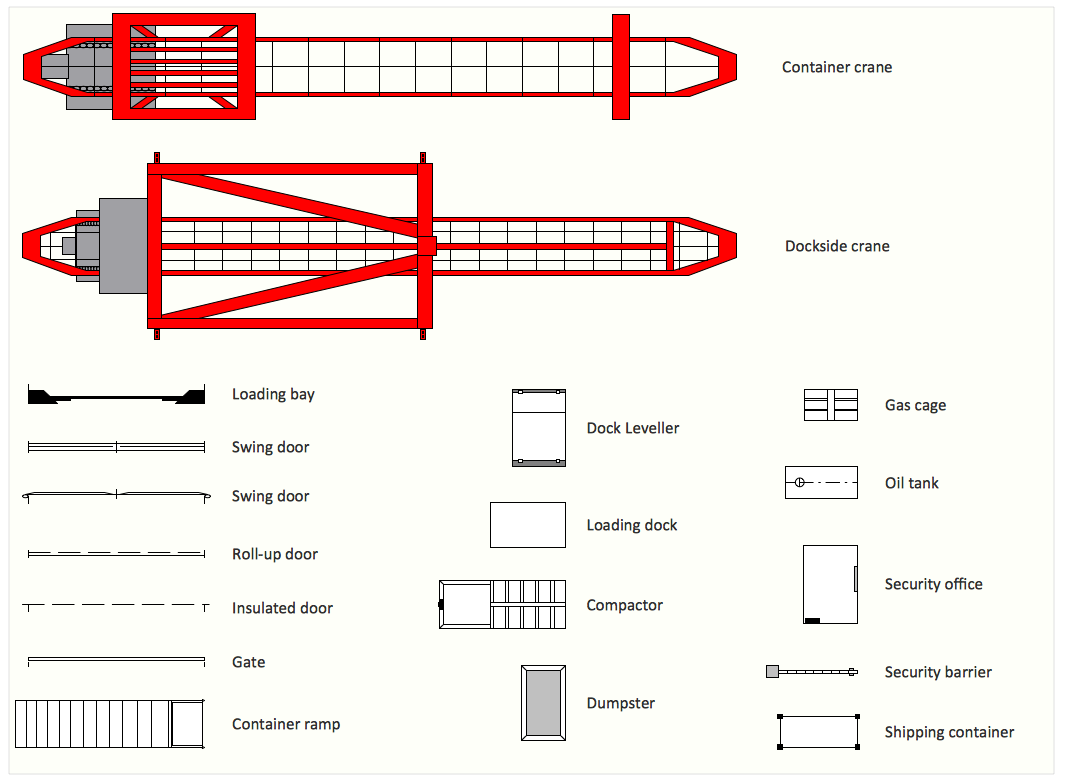
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.The vector stencils library "Shipping and receiving" contains 18 shapes of shipping and receiving equipment. Use it for drawing layouts for shipping and receiving centers with equipment for hauling, transporting, and distributing manufactured goods, freight, cargo, and stock from plants and industrial facilities with ConceptDraw PRO diagramming and vector drawing software extended with the Plant Layout Plans solution from the Building Plans area of ConceptDraw Solution Park.
The vector stencils library "Shipping and receiving" contains 18 symbols of industrial shipping and receiving equipment.
Use the design elements library "Shipping and receiving" to draw factory warehouse equipment layout plans, floor plans of shipping and receiving centers with equipment for hauling, transporting, and distributing manufactured goods, freight, cargo, and stock from plants and industrial facilities using the ConceptDraw PRO diagramming and vector drawing software.
"Freight transport, or shipping, is a key in the value chain in manufacturing.
While all modes of transport are used for cargo transport, there is high differentiation between the nature of the cargo transport, in which mode is chosen.
Logistics refers to the entire process of transferring products from producer to consumer, including storage, transport, transshipment, warehousing, material-handling and packaging, with associated exchange of information.
Containerization, with the standardization of ISO containers on all vehicles and at all ports, has revolutionized international and domestic trade, offering huge reduction in transshipment costs. Traditionally, all cargo had to be manually loaded and unloaded into the haul of any ship or car; containerization allows for automated handling and transfer between modes, and the standardized sizes allow for gains in economy of scale in vehicle operation." [Transport. Freight.
Wikipedia]
This shapes library "Shipping and receiving" is included in the Plant Layout Plans solution from the Building Plans area of ConceptDraw Solution Park.
Use the design elements library "Shipping and receiving" to draw factory warehouse equipment layout plans, floor plans of shipping and receiving centers with equipment for hauling, transporting, and distributing manufactured goods, freight, cargo, and stock from plants and industrial facilities using the ConceptDraw PRO diagramming and vector drawing software.
"Freight transport, or shipping, is a key in the value chain in manufacturing.
While all modes of transport are used for cargo transport, there is high differentiation between the nature of the cargo transport, in which mode is chosen.
Logistics refers to the entire process of transferring products from producer to consumer, including storage, transport, transshipment, warehousing, material-handling and packaging, with associated exchange of information.
Containerization, with the standardization of ISO containers on all vehicles and at all ports, has revolutionized international and domestic trade, offering huge reduction in transshipment costs. Traditionally, all cargo had to be manually loaded and unloaded into the haul of any ship or car; containerization allows for automated handling and transfer between modes, and the standardized sizes allow for gains in economy of scale in vehicle operation." [Transport. Freight.
Wikipedia]
This shapes library "Shipping and receiving" is included in the Plant Layout Plans solution from the Building Plans area of ConceptDraw Solution Park.
The vector stencils library "Shipping and receiving" contains 18 symbols of industrial shipping and receiving equipment.
Use the design elements library "Shipping and receiving" to draw factory warehouse equipment layout plans, floor plans of shipping and receiving centers with equipment for hauling, transporting, and distributing manufactured goods, freight, cargo, and stock from plants and industrial facilities using the ConceptDraw PRO diagramming and vector drawing software.
"Freight transport, or shipping, is a key in the value chain in manufacturing.
While all modes of transport are used for cargo transport, there is high differentiation between the nature of the cargo transport, in which mode is chosen.
Logistics refers to the entire process of transferring products from producer to consumer, including storage, transport, transshipment, warehousing, material-handling and packaging, with associated exchange of information.
Containerization, with the standardization of ISO containers on all vehicles and at all ports, has revolutionized international and domestic trade, offering huge reduction in transshipment costs. Traditionally, all cargo had to be manually loaded and unloaded into the haul of any ship or car; containerization allows for automated handling and transfer between modes, and the standardized sizes allow for gains in economy of scale in vehicle operation." [Transport. Freight.
Wikipedia]
This shapes library "Shipping and receiving" is included in the Plant Layout Plans solution from the Building Plans area of ConceptDraw Solution Park.
Use the design elements library "Shipping and receiving" to draw factory warehouse equipment layout plans, floor plans of shipping and receiving centers with equipment for hauling, transporting, and distributing manufactured goods, freight, cargo, and stock from plants and industrial facilities using the ConceptDraw PRO diagramming and vector drawing software.
"Freight transport, or shipping, is a key in the value chain in manufacturing.
While all modes of transport are used for cargo transport, there is high differentiation between the nature of the cargo transport, in which mode is chosen.
Logistics refers to the entire process of transferring products from producer to consumer, including storage, transport, transshipment, warehousing, material-handling and packaging, with associated exchange of information.
Containerization, with the standardization of ISO containers on all vehicles and at all ports, has revolutionized international and domestic trade, offering huge reduction in transshipment costs. Traditionally, all cargo had to be manually loaded and unloaded into the haul of any ship or car; containerization allows for automated handling and transfer between modes, and the standardized sizes allow for gains in economy of scale in vehicle operation." [Transport. Freight.
Wikipedia]
This shapes library "Shipping and receiving" is included in the Plant Layout Plans solution from the Building Plans area of ConceptDraw Solution Park.
Interior Design Shipping and Receiving - Design Elements
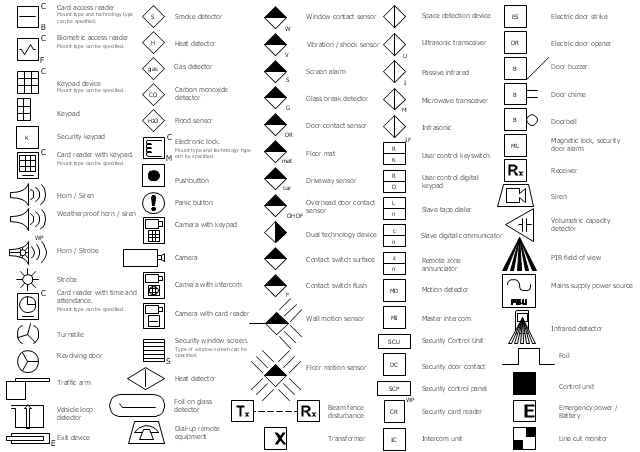
Create port terminal plans use the appropriate stencils with shipping and receiving design element.The vector stencils library Alarm and access control contains 80 symbols of digital proximity equipment, locking hardware, and access control equipment.
"An alarm device or system of alarm devices gives an audible, visual or other form of alarm signal about a problem or condition. Alarm devices are often outfitted with a siren." [Alarm device. Wikipedia]
"An access control point, which can be a door, turnstile, parking gate, elevator, or other physical barrier, where granting access can be electronically controlled. Typically, the access point is a door. An electronic access control door can contain several elements. At its most basic, there is a stand-alone electric lock. The lock is unlocked by an operator with a switch. To automate this, operator intervention is replaced by a reader. The reader could be a keypad where a code is entered, it could be a card reader, or it could be a biometric reader. Readers do not usually make an access decision, but send a card number to an access control panel that verifies the number against an access list. To monitor the door position a magnetic door switch can be used. In concept, the door switch is not unlike those on refrigerators or car doors. Generally only entry is controlled, and exit is uncontrolled. In cases where exit is also controlled, a second reader is used on the opposite side of the door. In cases where exit is not controlled, free exit, a device called a request-to-exit (REX) is used. Request-to-exit devices can be a push-button or a motion detector. When the button is pushed, or the motion detector detects motion at the door, the door alarm is temporarily ignored while the door is opened. Exiting a door without having to electrically unlock the door is called mechanical free egress. This is an important safety feature. In cases where the lock must be electrically unlocked on exit, the request-to-exit device also unlocks the door." [Access control. Wikipedia]
Use the design elements library Alarm and access control for drawing layout floor plans, blueprints, and wiring diagrams of intrusion systems, time and attendance systems, card and code access control security systems, internal and external security control systems using the ConceptDraw PRO diagramming and vector drawing software.
The shapes library Alarm and access control is included in the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
"An alarm device or system of alarm devices gives an audible, visual or other form of alarm signal about a problem or condition. Alarm devices are often outfitted with a siren." [Alarm device. Wikipedia]
"An access control point, which can be a door, turnstile, parking gate, elevator, or other physical barrier, where granting access can be electronically controlled. Typically, the access point is a door. An electronic access control door can contain several elements. At its most basic, there is a stand-alone electric lock. The lock is unlocked by an operator with a switch. To automate this, operator intervention is replaced by a reader. The reader could be a keypad where a code is entered, it could be a card reader, or it could be a biometric reader. Readers do not usually make an access decision, but send a card number to an access control panel that verifies the number against an access list. To monitor the door position a magnetic door switch can be used. In concept, the door switch is not unlike those on refrigerators or car doors. Generally only entry is controlled, and exit is uncontrolled. In cases where exit is also controlled, a second reader is used on the opposite side of the door. In cases where exit is not controlled, free exit, a device called a request-to-exit (REX) is used. Request-to-exit devices can be a push-button or a motion detector. When the button is pushed, or the motion detector detects motion at the door, the door alarm is temporarily ignored while the door is opened. Exiting a door without having to electrically unlock the door is called mechanical free egress. This is an important safety feature. In cases where the lock must be electrically unlocked on exit, the request-to-exit device also unlocks the door." [Access control. Wikipedia]
Use the design elements library Alarm and access control for drawing layout floor plans, blueprints, and wiring diagrams of intrusion systems, time and attendance systems, card and code access control security systems, internal and external security control systems using the ConceptDraw PRO diagramming and vector drawing software.
The shapes library Alarm and access control is included in the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
The vector clipart library Access and security contains 17 images of access control and security system equipment.
"In the fields of physical security and information security, access control is the selective restriction of access to a place or other resource. The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.
Locks and login credentials are two analogous mechanisms of access control. ...
The term access control refers to the practice of restricting entrance to a property, a building, or a room to authorized persons. Physical access control can be achieved by a human (a guard, bouncer, or receptionist), through mechanical means such as locks and keys, or through technological means such as access control systems like the mantrap. Within these environments, physical key management may also be employed as a means of further managing and monitoring access to mechanically keyed areas or access to certain small assets." [Access control. Wikipedia]
Use the vector stencils library Access and security to draw illustrations and diagrams of safety and security system equipment using the ConceptDraw PRO diagramming and vector drawing software.
The clipart example "Design elements - Access and security" is included in the Safety and Security solution from the Illustration area of ConceptDraw Solution Park.
"In the fields of physical security and information security, access control is the selective restriction of access to a place or other resource. The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.
Locks and login credentials are two analogous mechanisms of access control. ...
The term access control refers to the practice of restricting entrance to a property, a building, or a room to authorized persons. Physical access control can be achieved by a human (a guard, bouncer, or receptionist), through mechanical means such as locks and keys, or through technological means such as access control systems like the mantrap. Within these environments, physical key management may also be employed as a means of further managing and monitoring access to mechanically keyed areas or access to certain small assets." [Access control. Wikipedia]
Use the vector stencils library Access and security to draw illustrations and diagrams of safety and security system equipment using the ConceptDraw PRO diagramming and vector drawing software.
The clipart example "Design elements - Access and security" is included in the Safety and Security solution from the Illustration area of ConceptDraw Solution Park.
- Png Clipart Security Card
- Security Vector Png
- Football (Soccer) - Vector stencils library | Access and security ...
- Presentation Vector Png
- Vector Png Images
- Firewall Diagram Png
- Forklift Vector Png
- Network Security | Network Security Devices | Network Security ...
- Door Plant Top View Png
- Filter Png
- Firewall between LAN and WAN | Hotel Network Topology Diagram ...
- Firewall between LAN and WAN | Network Security Diagrams | Hotel ...
- Computer Server Png
- Firewall between LAN and WAN | Australia Map | Tree and Forest ...
- Network Security Devices | Netflow architecture. Computer and ...
- Operator hierarchy - Natural hierarchy rearranged | IVR systems ...
- Internet symbols - Vector stencils library | Network Security Devices ...
- Arrow Png
- Firewall between LAN and WAN | Network Security | Network ...
- How to Create a Network Security Diagram Using ConceptDraw PRO