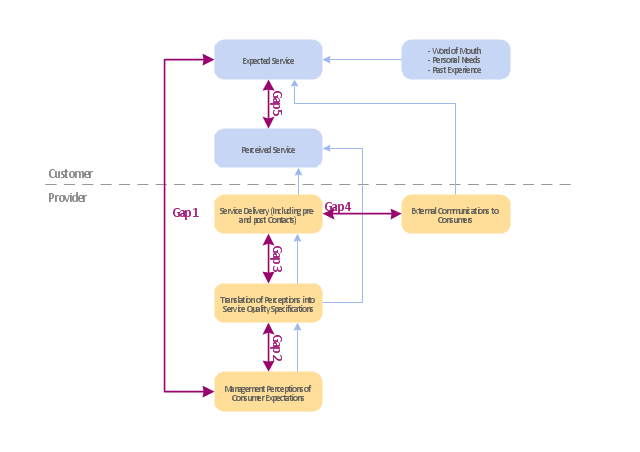
"Dimensions of service quality.
A customer's expectation of a particular service is determined by factors such as recommendations, personal needs and past experiences. The expected service and the perceived service sometimes may not be equal, thus leaving a gap. The service quality model or the ‘GAP model’ developed by a group of authors- Parasuraman, Zeithaml and Berry at Texas and North Carolina in 1985 , highlights the main requirements for delivering high service quality. It identifies five ‘gaps’ that cause unsuccessful delivery. Customers generally have a tendency to compare the service they 'experience' with the service they 'expect' . If the experience does not match the expectation , there arises a gap. Ten determinants that may influence the appearance of a gap were described by Parasuraman, Zeithaml and Berry. in the SERVQUAL model: reliability, responsiveness, competence, access, courtesy, communication, credibility, security, understanding the customer and tangibles.
Later, the determinants were reduced to five: tangibles; reliability; responsiveness; service assurance and empathy in the so called RATER model." [Service quality. Wikipedia]
The block diagram example "Gap model of service quality" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Block Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
A customer's expectation of a particular service is determined by factors such as recommendations, personal needs and past experiences. The expected service and the perceived service sometimes may not be equal, thus leaving a gap. The service quality model or the ‘GAP model’ developed by a group of authors- Parasuraman, Zeithaml and Berry at Texas and North Carolina in 1985 , highlights the main requirements for delivering high service quality. It identifies five ‘gaps’ that cause unsuccessful delivery. Customers generally have a tendency to compare the service they 'experience' with the service they 'expect' . If the experience does not match the expectation , there arises a gap. Ten determinants that may influence the appearance of a gap were described by Parasuraman, Zeithaml and Berry. in the SERVQUAL model: reliability, responsiveness, competence, access, courtesy, communication, credibility, security, understanding the customer and tangibles.
Later, the determinants were reduced to five: tangibles; reliability; responsiveness; service assurance and empathy in the so called RATER model." [Service quality. Wikipedia]
The block diagram example "Gap model of service quality" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Block Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
 Block Diagrams
Block Diagrams
Block diagrams solution extends ConceptDraw PRO software with templates, samples and libraries of vector stencils for drawing the block diagrams.
Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution enhances the ConceptDraw PRO v10 functionality with large collection of predesigned vector stencils of cybersecurity clipart, shapes, icons and connectors to help you succeed in designing professional and accurate Ne
HelpDesk
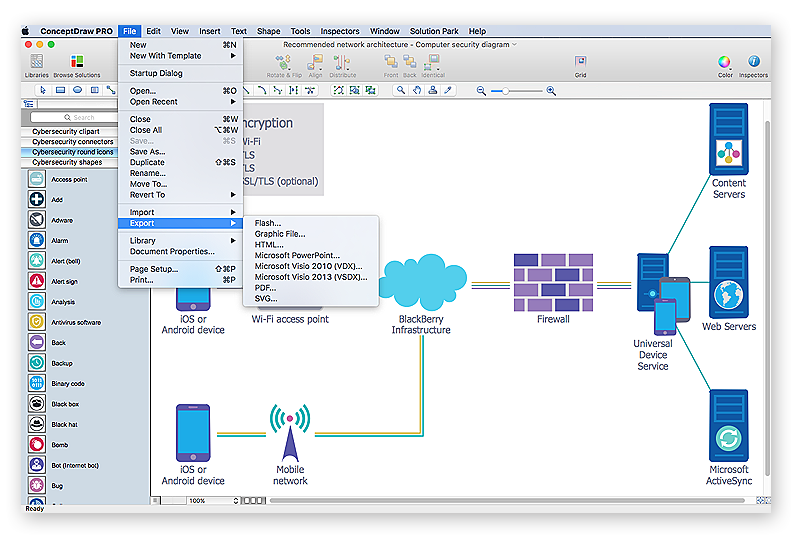
How to Create a Network Security Diagram Using ConceptDraw PRO
Network security requires constant work and attention to details. Each user, whether an individual or organization, owns an information, considered to be valuable. The enforcement of network security, whether it be a local network security, or wireless network security is core for creating the secure environment of the daily working processes. Network security is accomplished through hardware and software. Network security system must be sophisticated and modern inside, but simple and understandable for the user. The visual scheme of security system can be presented in the form of a Network Security diagram. ConceptDraw PRO provides the toolkit for network security system visualization with its Network Security Diagram solution.
 ConceptDraw Solution Park
ConceptDraw Solution Park
ConceptDraw Solution Park collects graphic extensions, examples and learning materials
Daisy Chain Network Topology
This sample was created in ConceptDraw PRO diagramming and vector drawing software using the Computer and Networks solution from Computer and Networks area of ConceptDraw Solution Park. A Daisy Chain is the simple computer network. It is the easiest way to add more Ethernet devices into the network. In the Daisy Chain network one computer is connected to the next without any intervening devices, thus the message is sent from one computer to the next and then to the next and so on. A Daisy Chain can be linear or ringCloud Computing Architecture Diagrams
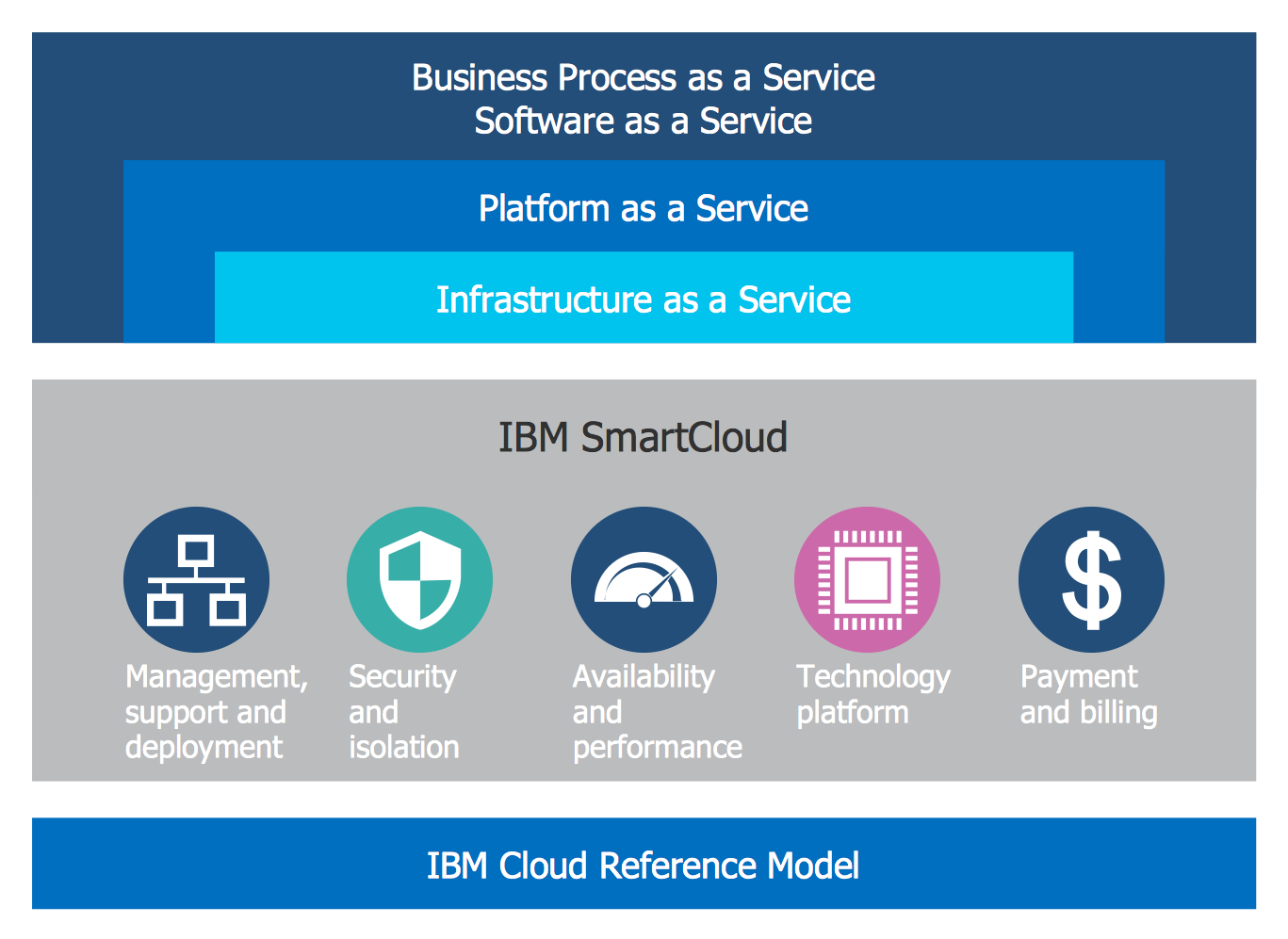
For documenting the Cloud Computing Architecture with a goal to facilitate the communication between stakeholders are successfully used the Cloud Computing Architecture diagrams. It is convenient and easy to draw various Cloud Computing Architecture diagrams in ConceptDraw PRO software with help of tools of the Cloud Computing Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.
 Security and Access Plans
Security and Access Plans
This solution extends ConceptDraw PRO software with physical security plan, security chart, access chart, security plans, access schemes, access plans , CCTV System Plan samples, templates and libraries of design elements for drawing the Security and Acce
 Computer and Network Package
Computer and Network Package
Computer and Network Package is a large set of valuable graphical solutions from ConceptDraw Solution Park, developed and specially selected to help computer network specialists and IT professionals to realize their daily work the most efficiently and quickly. This package contains extensive set of graphic design tools, ready-to-use vector elements, built-in templates and samples for designing professional-looking diagrams, charts, schematics and infographics in a field of computer network technologies, cloud computing, vehicular networking, wireless networking, ensuring networks security and networks protection. It is useful for designing different floor plans and layout plans for homes, offices, hotels and instantly construction detailed schemes of computer networks and wireless networks on them, for making professional-looking and colorful Pie Charts, Bar Graphs and Line Charts visualizing the relevant information and data.
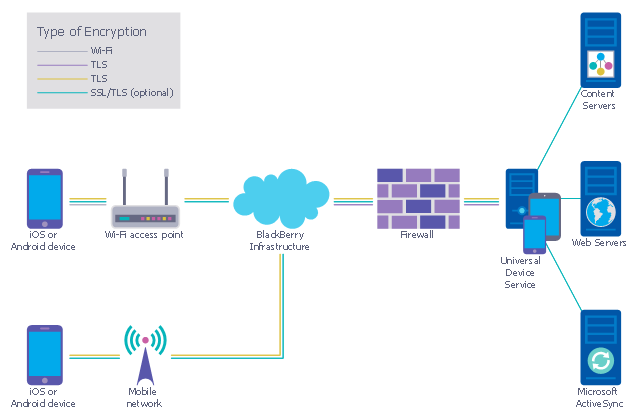
This example was designed on the base of the diagram from the "BYOD Guidance: BlackBerry Secure Work Space" on the website of the UK Communications Electronics Security Group (CESG).
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
 Telecommunication Network Diagrams
Telecommunication Network Diagrams
Telecommunication Network Diagrams solution extends ConceptDraw PRO software with samples, templates and libraries of vector stencils for drawing the diagrams of telecommunication networks.
 SYSML
SYSML
The SysML solution helps to present diagrams using Systems Modeling Language; a perfect tool for system engineering.
Electrical Symbols, Electrical Schematic Symbols
Electrical Schematics and Electrical Circuit Diagrams are included to the number of obligatory diagrams and documents while developing the package of construction documentation for the building project. It is comfortable to use the special drawing software for designing diagrams of this type. ConceptDraw PRO diagramming and vector drawing software extended with Electrical Engineering solution from Engineering Area of ConceptDraw Solution Park provides the powerful drawing tools, a lot of specific samples and templates, and numerous libraries with incredibly large quantity of predesigned electrical schematic symbols, including analog and digital logic electrical symbols, electrical circuits symbols, inductors, power sources, lamps, resistors, transistors, delay elements, switches and relays, terminals and connectors, and many other useful electrical symbols, which will be helpful for easy designing professional looking Electrical Schematics, Electrical Engineering Diagrams, Circuit and Wiring Diagrams, Power Systems Diagrams, Digital and Analog Logic Schematics.HelpDesk
How to Draw a Security and Access Floor Plan
When you are dealing with floor plans for your office or home, it's good to have a security and access plan as well. Any equipment that is responsible for certain aspects of security can be incorporated into a security and access floor plan. Any equipment that is responsible for certain aspects of security can be incorporated into a security and access floor plan. Ability to create a security and access plan in ConceptDraw PRO is contained in the Security and Access Plans solution. You can use ConceptDraw PRO to make the security and access plans for your office simple, accurate and easy-to-read.- Network Security Devices | Block Diagrams | How to Create a ...
- Network Security Model Block Diagram
- Explain Network Security Model With Block Diagram
- Explain Model Of Security With Block Diagram
- Network Security Model | Network Security Tips | Network Security ...
- Network Security Model | Network Security Diagram | Network ...
- Network Security Model | Network Security Architecture Diagram ...
- Network Security Block Diagram And Explanation
- Network Security Diagrams | Network Security Architecture Diagram ...
- Block Diagrams | Network Security Diagrams | Bubble Diagrams ...
- Block Diagrams | Network Security Diagrams | Campus Area ...
- Network Security Model | Network Security Diagram | Network ...
- About Explain Security Model With Diagram
- Explain Network Security Model With Diagram
- Block diagram - Porter's five forces model | Swot Analysis Examples ...
- Cyber Security Degrees | Network Security Model | Network Security ...
- Block Diagram Creator | Electrical Engineering | Security and ...
- Network Security Model | Network Security Architecture Diagram ...
- Network Security Devices | Network Security Diagrams | Storage ...
- Network Security Devices | Network Security Diagram | Network ...