Introduction to Cloud Computing Architecture
The best way to visualize the introduction to Cloud computing architecture is to create diagrams and schematics representing what is a cloud computing and how it works. For their design, we recommend to use a powerful ConceptDraw DIAGRAM diagramming and vector drawing software supplied with Cloud Computing Diagrams solution from the Computers and Network area of ConceptDraw Solution ParkCisco Security. Cisco icons, shapes, stencils and symbols
The ConceptDraw vector stencils library "Cisco Security" contains 16 symbols of security devices and equipment for drawing the computer network diagrams using the ConceptDraw DIAGRAM diagramming and vector drawing software.Cloud Computing Architecture Diagrams
For documenting the Cloud Computing Architecture with a goal to facilitate the communication between stakeholders are successfully used the Cloud Computing Architecture diagrams. It is convenient and easy to draw various Cloud Computing Architecture diagrams in ConceptDraw DIAGRAM software with help of tools of the Cloud Computing Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.This vector stencils library contains 184 round icons.
Use it to design cloud computing infographics and diagrams with ConceptDraw PRO software.
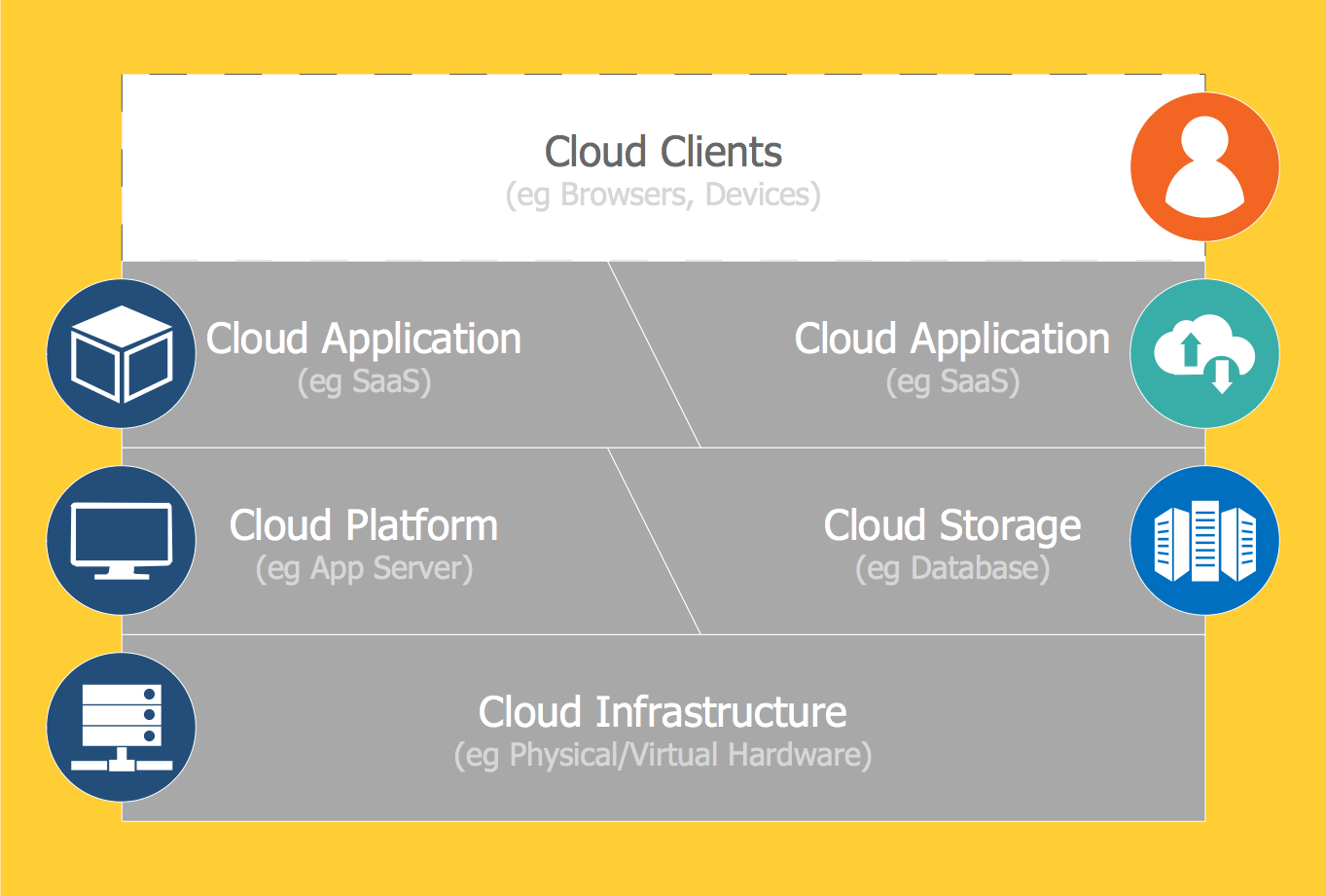
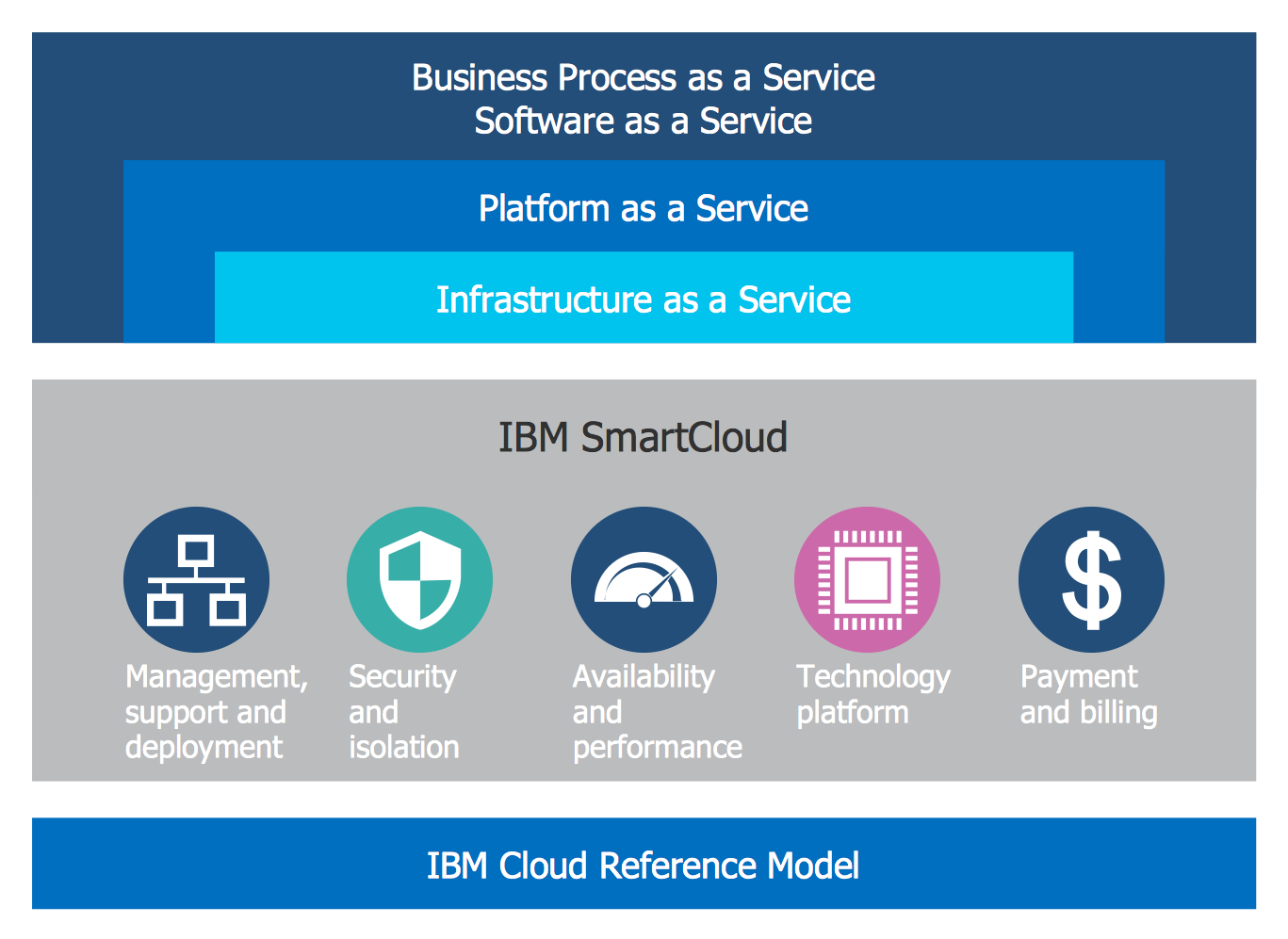
"Though service-oriented architecture advocates "everything as a service" (with the acronyms EaaS or XaaS or simply aas), cloud-computing providers offer their "services" according to different models, which happen to form a stack: infrastructure-, platform- and software-as-a-service.
Infrastructure as a service (IaaS)
In the most basic cloud-service model ... providers of IaaS offer computers — physical or (more often) virtual machines — and other resources. IaaS refers to online services that abstract the user from the details of infrastructure like physical computing resources, location, data partitioning, scaling, security, backup etc.
Platform as a service (PaaS)
PaaS vendors offer a development environment to application developers. The provider typically develops toolkit and standards for development and channels for distribution and payment. In the PaaS models, cloud providers deliver a computing platform, typically including operating system, programming-language execution environment, database, and web server. Application developers can develop and run their software solutions on a cloud platform without the cost and complexity of buying and managing the underlying hardware and software layers.
Software as a service (SaaS)
In the software as a service (SaaS) model, users gain access to application software and databases. Cloud providers manage the infrastructure and platforms that run the applications. SaaS is sometimes referred to as "on-demand software" and is usually priced on a pay-per-use basis or using a subscription fee.
In the SaaS model, cloud providers install and operate application software in the cloud and cloud users access the software from cloud clients. Cloud users do not manage the cloud infrastructure and platform where the application runs. This eliminates the need to install and run the application on the cloud user's own computers, which simplifies maintenance and support. Cloud applications differ from other applications in their scalability — which can be achieved by cloning tasks onto multiple virtual machines at run-time to meet changing work demand." [Cloud computing. Wikipedia]
The vector stencils library "Cloud round icons" is included in the Cloud Computing Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design cloud computing infographics and diagrams with ConceptDraw PRO software.
"Though service-oriented architecture advocates "everything as a service" (with the acronyms EaaS or XaaS or simply aas), cloud-computing providers offer their "services" according to different models, which happen to form a stack: infrastructure-, platform- and software-as-a-service.
Infrastructure as a service (IaaS)
In the most basic cloud-service model ... providers of IaaS offer computers — physical or (more often) virtual machines — and other resources. IaaS refers to online services that abstract the user from the details of infrastructure like physical computing resources, location, data partitioning, scaling, security, backup etc.
Platform as a service (PaaS)
PaaS vendors offer a development environment to application developers. The provider typically develops toolkit and standards for development and channels for distribution and payment. In the PaaS models, cloud providers deliver a computing platform, typically including operating system, programming-language execution environment, database, and web server. Application developers can develop and run their software solutions on a cloud platform without the cost and complexity of buying and managing the underlying hardware and software layers.
Software as a service (SaaS)
In the software as a service (SaaS) model, users gain access to application software and databases. Cloud providers manage the infrastructure and platforms that run the applications. SaaS is sometimes referred to as "on-demand software" and is usually priced on a pay-per-use basis or using a subscription fee.
In the SaaS model, cloud providers install and operate application software in the cloud and cloud users access the software from cloud clients. Cloud users do not manage the cloud infrastructure and platform where the application runs. This eliminates the need to install and run the application on the cloud user's own computers, which simplifies maintenance and support. Cloud applications differ from other applications in their scalability — which can be achieved by cloning tasks onto multiple virtual machines at run-time to meet changing work demand." [Cloud computing. Wikipedia]
The vector stencils library "Cloud round icons" is included in the Cloud Computing Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
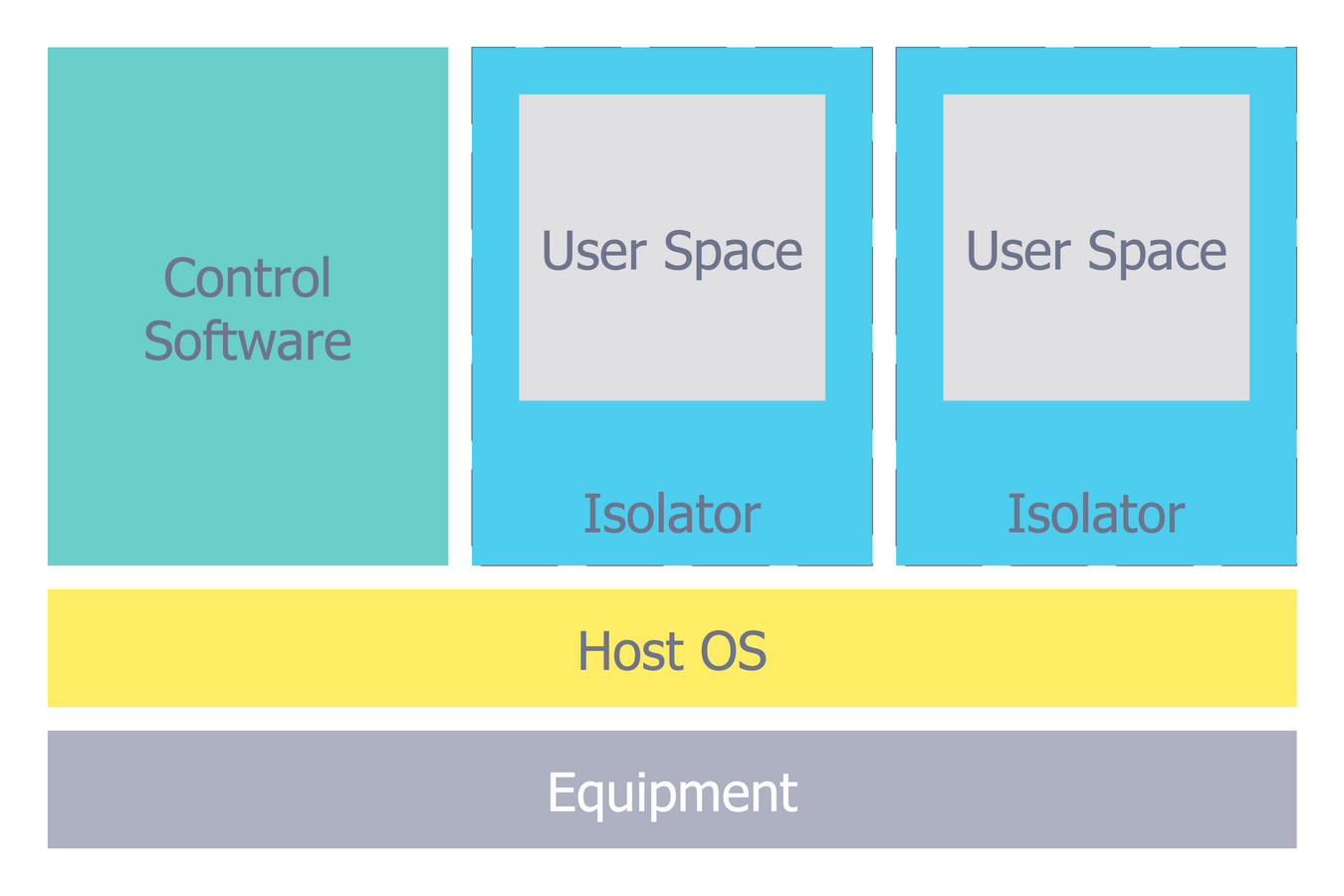
Network Security Architecture Diagram
Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram? We recommend to use ConceptDraw DIAGRAM extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.Storage area networks (SAN). Computer and Network Examples
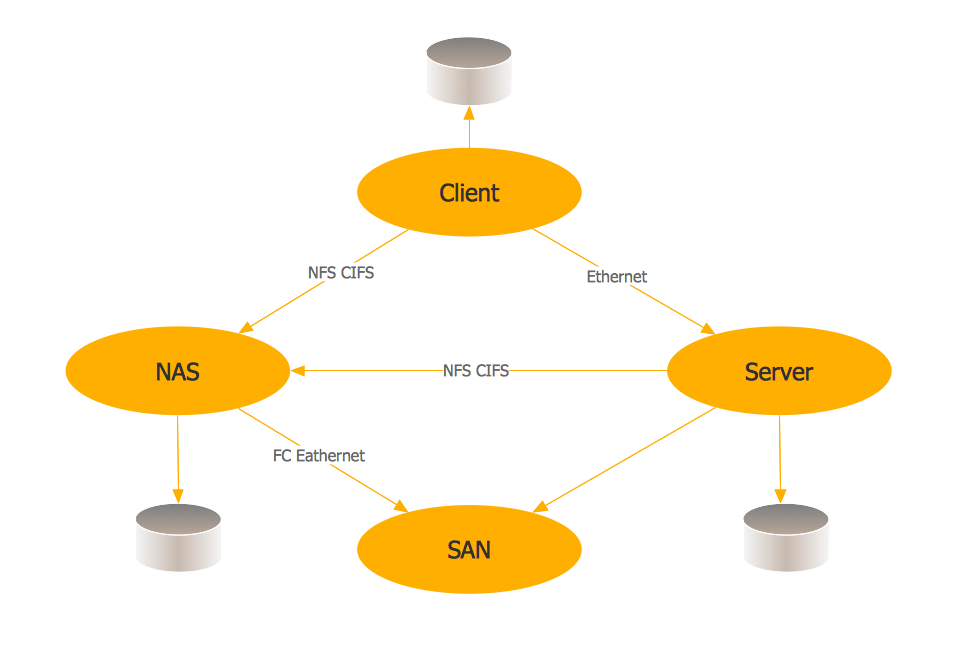
A Storage area network (SAN) is a dedicated network that provides access to data storage and operations only on the block level. SAN usually has own network of storage devices/elements and disk arrays that are connected with each other and to a remote data-sharing network. SANs are widely used for enhancing the storage devices (optical jukeboxes, disk arrays, tape libraries) that are accessible for networked servers. This example was created in ConceptDraw DIAGRAM using the Computer and Networks Area of ConceptDraw Solution Park. It shows the hybrid of Storage area network (SAN) and Network Attached Storage (NAS) technologies.
Network Security Model
Creation of well thought-out network security model will effectively help you in realization your network's security. ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park lets fast and easy design all variety of network security models: Open network security model, Closed network security model, Restrictive network access model.Network Security Diagram
ConceptDraw DIAGRAM diagramming and vector drawing software enhanced with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is the best for effective design professional, colorful and attractive Network Security Diagram of any complexity and degree of detailing.Cyber Security Degrees
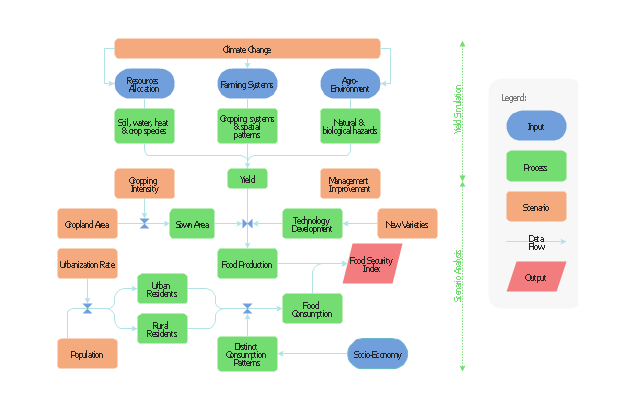
For protection various cyber environments are developed and applied large variety of cyber security standards, techniques, security concepts and approaches with different cyber security degrees. The ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park offers the number of useful tools which will help network security engineers, cyber security specialists, network and computer analysts easily and visually depict the knowledge and skills for research and prevention of intrusions, about protection critical information and analysis of cyber incidents, and for how to assess threats and vulnerabilities.This flow chart sample was drawn on the base on the illustration of the article "Climate change impact on China food security in 2050" from the website of Chinese Academy of Agricultural Sciences .
[caas.cn/ en/ newsroom/ research_ update/ 67347.shtml]
"Food security is a condition related to the ongoing availability of food. ...
According to the Food and Agriculture Organization (FAO), food security "exists when all people, at all times, have physical and economic access to sufficient, safe and nutritious food to meet their dietary needs and food preferences for an active and healthy life". ...
Extreme events, such as droughts and floods, are forecast to increase as climate change takes hold. Ranging from overnight floods to gradually worsening droughts, these will have a range of impacts on the agricultural sector. ...
According to the Climate & Development Knowledge Network report Managing Climate Extremes and Disasters in the Agriculture Sectors: Lessons from the IPCC SREX Report, the impacts will include changing productivity and livelihood patterns, economic losses, and impacts on infrastructure, markets and food security. Food security in future will be linked to our ability to adapt agricultural systems to extreme events." [Food security. Wikipedia]
The flowchart example "Food security assessment" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Flowcharts solution from the area "What is a Diagram" of ConceptDraw Solution Park.
[caas.cn/ en/ newsroom/ research_ update/ 67347.shtml]
"Food security is a condition related to the ongoing availability of food. ...
According to the Food and Agriculture Organization (FAO), food security "exists when all people, at all times, have physical and economic access to sufficient, safe and nutritious food to meet their dietary needs and food preferences for an active and healthy life". ...
Extreme events, such as droughts and floods, are forecast to increase as climate change takes hold. Ranging from overnight floods to gradually worsening droughts, these will have a range of impacts on the agricultural sector. ...
According to the Climate & Development Knowledge Network report Managing Climate Extremes and Disasters in the Agriculture Sectors: Lessons from the IPCC SREX Report, the impacts will include changing productivity and livelihood patterns, economic losses, and impacts on infrastructure, markets and food security. Food security in future will be linked to our ability to adapt agricultural systems to extreme events." [Food security. Wikipedia]
The flowchart example "Food security assessment" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Flowcharts solution from the area "What is a Diagram" of ConceptDraw Solution Park.
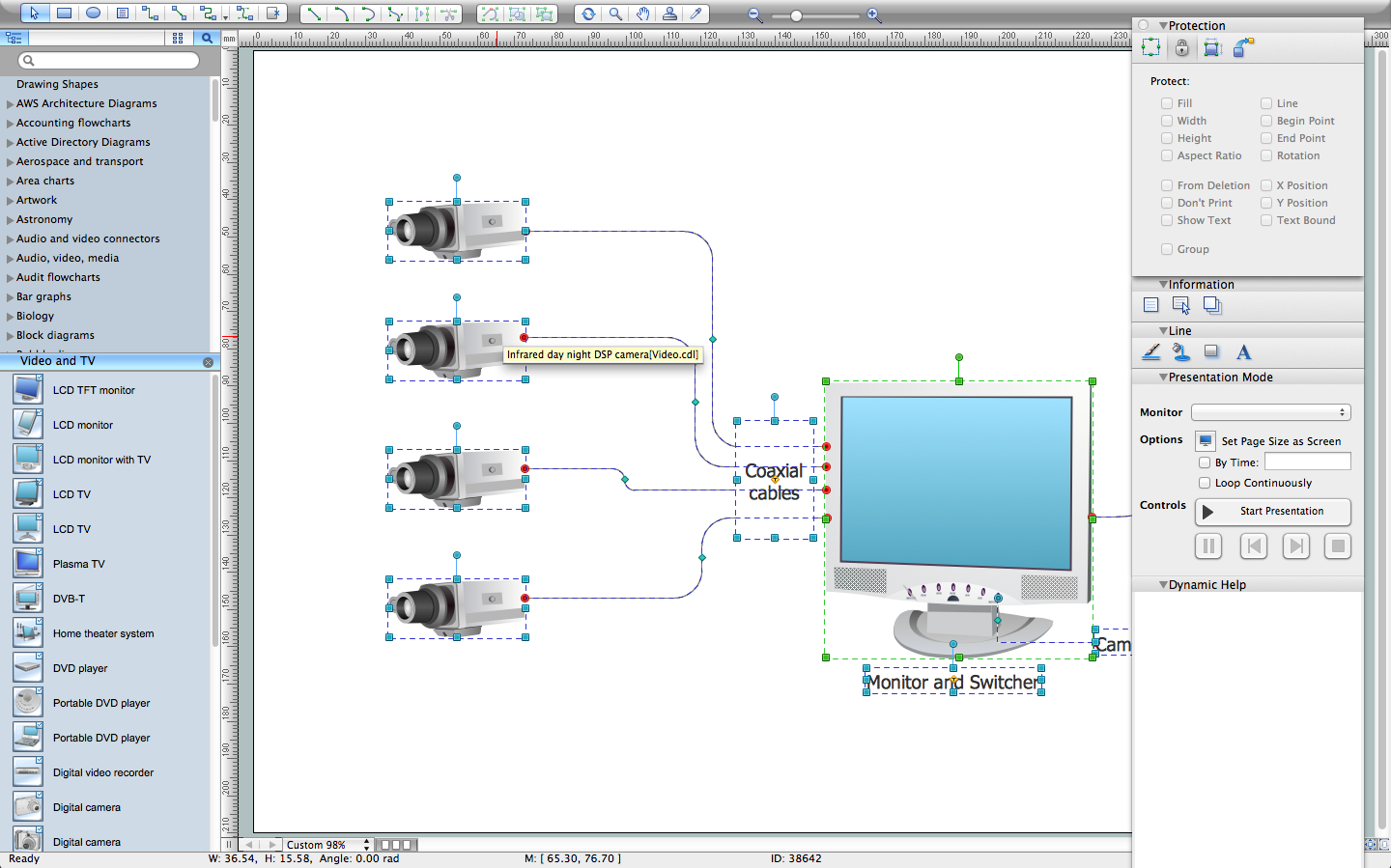
CCTV Network Diagram Software
The CCTV is the process that carried out using the video cameras for transmitting the signal to the specific location, on the limited set of monitors. We are talking about the video cameras that are used for monitoring on such guarded objects as airports, banks, stores, military objects, etc. CCTV equipment is also used in the industrial installations, for surveillance in the public places, for recording the video on the digital video recorders.Network Topologies
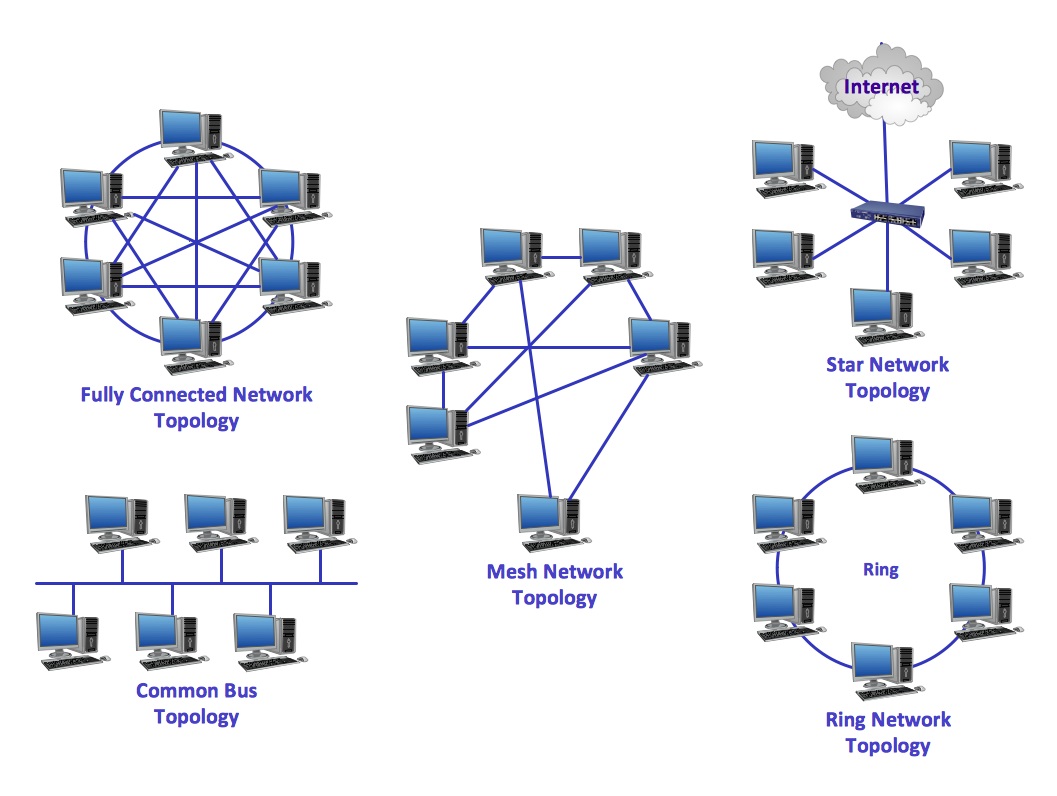
Network topology is a topological structure of computer network, which can be physical or logical. The physical topology depicts location of different computer network elements such as computers, cables and other devices. The logical topology visually displays network dataflows from one device to another. Sometimes network logical and physical topologies can be the same. ConceptDraw DIAGRAM diagramming and vector drawing software is powerful for drawing network maps and network topologies diagrams of any kinds and complexity thanks to the Computer Network Diagrams solution from the Computer and Networks area. ConceptDraw STORE proposes collection of network icons libraries and a lot of Network Topology Diagram examples, samples and templates which were created at ConceptDraw DIAGRAM software specially for Computer Network Diagrams solution. There are six basic types of the network topologies: Bus, Star, Ring, Mesh, Tree, Fully Connected. You can fast and easy design professional-looking diagram for each of them using the ConceptDraw DIAGRAM tools. There are plenty of web Visio-like diagramming software available. Web based diagrams software can be powerful, but sometimes it is essential to have desktop software. One of the most advanced diagrams tools like Visio for Mac OS is ConceptDraw DIAGRAM app.
The vector stencils library "AWS Security, Identity and Compliance" contains 23 Amazon Web Services icons: AWS Directory Service, AWS Config, AWS CloudTrail, AWS Trusted Advisor, Amazon CloudWatch, Alarm. Use it to draw AWS architecture diagrams of your cloud infrastructure services.
"The AWS infrastructure puts strong safeguards in place to help protect customer privacy. All data is stored in highly secure AWS data centers. ...
AWS manages dozens of compliance programs in its infrastructure. This means that segments of your compliance have already been completed. ...
Cut costs by using AWS data centers. Maintain the highest standard of security without having to manage your own facility. ...
Security scales with your AWS cloud usage. No matter the size of your business the AWS infrastructure is designed to keep data safe." [aws.amazon.com/ security/ ]
The symbols example "AWS Security, Identity and Compliance - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"The AWS infrastructure puts strong safeguards in place to help protect customer privacy. All data is stored in highly secure AWS data centers. ...
AWS manages dozens of compliance programs in its infrastructure. This means that segments of your compliance have already been completed. ...
Cut costs by using AWS data centers. Maintain the highest standard of security without having to manage your own facility. ...
Security scales with your AWS cloud usage. No matter the size of your business the AWS infrastructure is designed to keep data safe." [aws.amazon.com/ security/ ]
The symbols example "AWS Security, Identity and Compliance - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Cisco People. Cisco icons, shapes, stencils and symbols
The ConceptDraw vector stencils library Cisco People contains symbols for drawing the computer network diagrams. Vector stencils library "Cisco People" contains 17 pictogram symbols and clipart for drawing the computer network diagrams using the ConceptDraw DIAGRAM diagramming and vector drawing software.- Network Security Infrastructure
- Infrastructure Security
- Network Security Diagrams | How to Create a Network Security ...
- Food security assessment - Flowchart
- Network Infrastructure Diagram Software
- Aws Infrastructure
- Infrastructure Shapes Set Png
- Cloud Computing Architecture Diagrams | Cloud Computing ...
- It Infrastructure Architecture Diagram
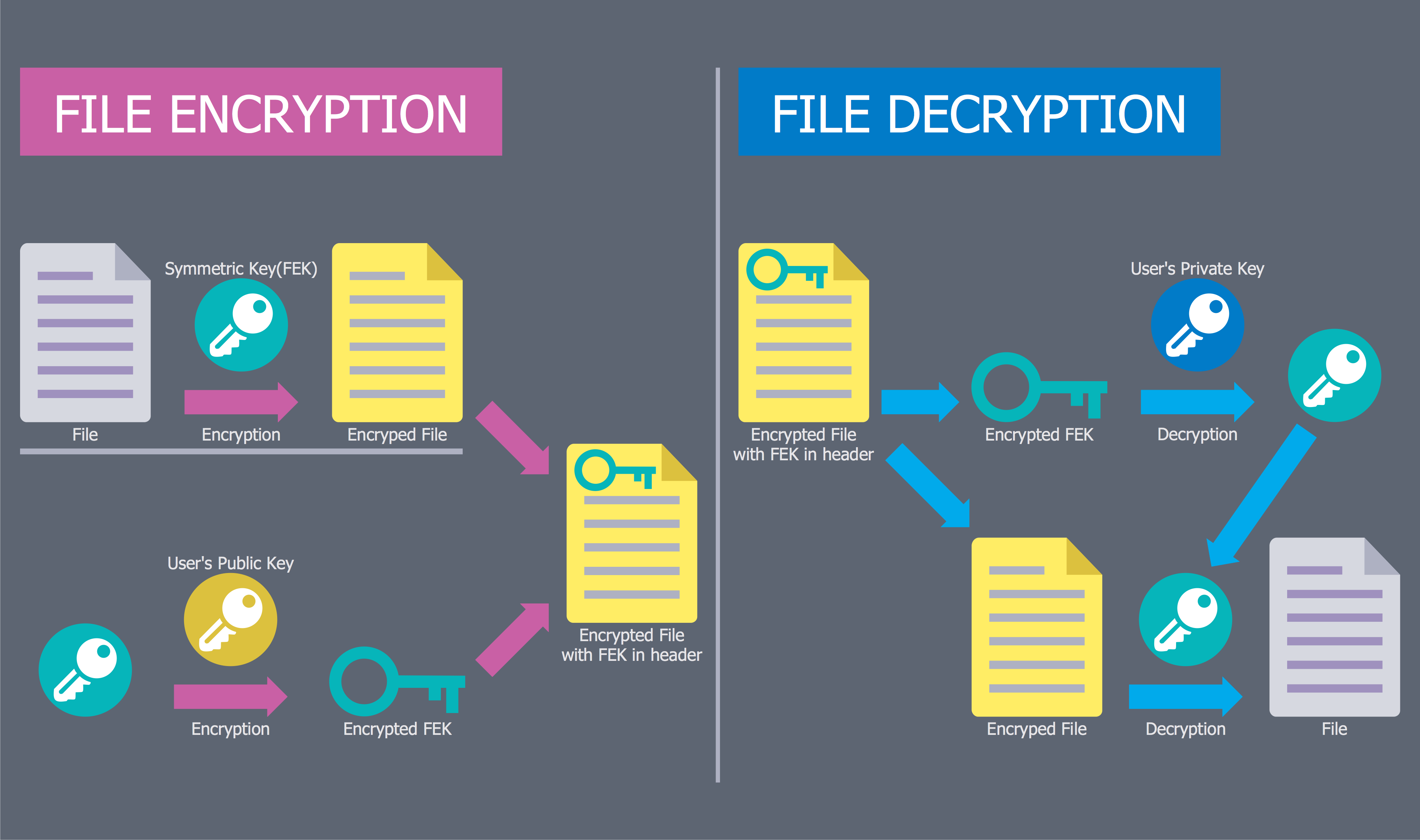
- Access control and encryption | Network Security Model | Network ...
- AWS Architecture Diagrams | Mobile app security | Diagramming ...
- Server Infrastructure Diagram
- Food security assessment - Flowchart | Opportunities in agro and ...
- Account Flowchart. Flowchart Examples | Cloud round icons - Vector ...
- Food security assessment - Flowchart | Block Diagram Software ...
- Diagrams For Food Security
- Network Security Devices | Food security assessment - Flowchart ...
- Network Diagramming Software for Design Network Layout ...
- Flowcharts | Food security assessment - Flowchart | Flowchart ...
- BPM Software | Fishbone Diagram | Cyber Security Degrees ...












-aws-security,-identity-and-compliance---vector-stencils-library.png--diagram-flowchart-example.png)