ConceptDraw Solution Park
ConceptDraw Solution Park
ConceptDraw Solution Park collects graphic extensions, examples and learning materials
HelpDesk
How to Draw a Security and Access Floor Plan
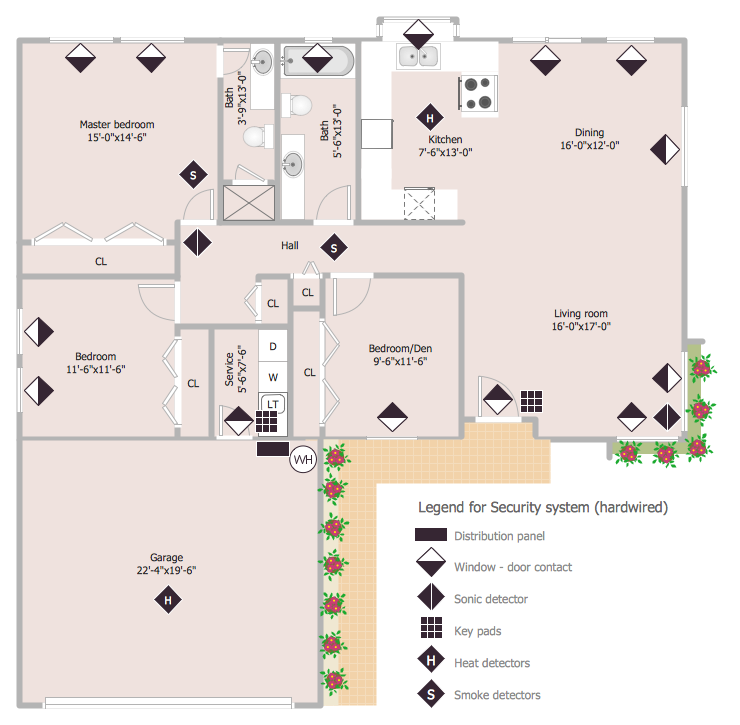
When you are dealing with floor plans for your office or home, it's good to have a security and access plan as well. Any equipment that is responsible for certain aspects of security can be incorporated into a security and access floor plan. Any equipment that is responsible for certain aspects of security can be incorporated into a security and access floor plan. Ability to create a security and access plan in ConceptDraw PRO is contained in the Security and Access Plans solution. You can use ConceptDraw PRO to make the security and access plans for your office simple, accurate and easy-to-read.The vector stencils library "Cisco network topology" contains 89 symbols of Cisco network devices and design elements for drawing computer network topology diagrams.
"There are two basic categories of network topologies:
(1) Physical topologies,
(2) Logical topologies.
The shape of the cabling layout used to link devices is called the physical topology of the network. This refers to the layout of cabling, the locations of nodes, and the interconnections between the nodes and the cabling. The physical topology of a network is determined by the capabilities of the network access devices and media, the level of control or fault tolerance desired, and the cost associated with cabling or telecommunications circuits.
The logical topology in contrast, is the way that the signals act on the network media, or the way that the data passes through the network from one device to the next without regard to the physical interconnection of the devices." [Network topology. Wikipedia]
The symbols example "Cisco network topology - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"There are two basic categories of network topologies:
(1) Physical topologies,
(2) Logical topologies.
The shape of the cabling layout used to link devices is called the physical topology of the network. This refers to the layout of cabling, the locations of nodes, and the interconnections between the nodes and the cabling. The physical topology of a network is determined by the capabilities of the network access devices and media, the level of control or fault tolerance desired, and the cost associated with cabling or telecommunications circuits.
The logical topology in contrast, is the way that the signals act on the network media, or the way that the data passes through the network from one device to the next without regard to the physical interconnection of the devices." [Network topology. Wikipedia]
The symbols example "Cisco network topology - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
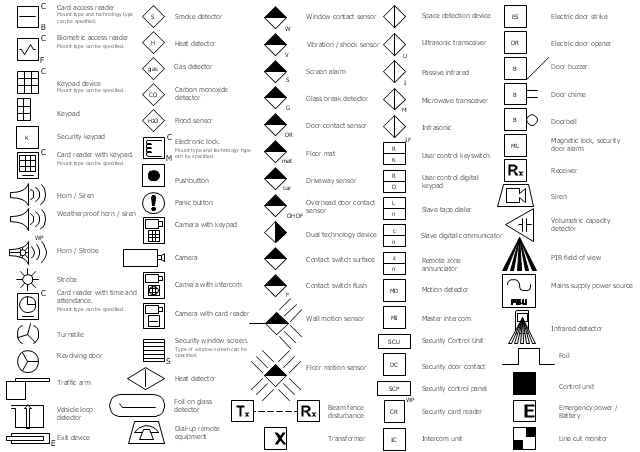
The vector stencils library Alarm and access control contains 80 symbols of digital proximity equipment, locking hardware, and access control equipment.
"An alarm device or system of alarm devices gives an audible, visual or other form of alarm signal about a problem or condition. Alarm devices are often outfitted with a siren." [Alarm device. Wikipedia]
"An access control point, which can be a door, turnstile, parking gate, elevator, or other physical barrier, where granting access can be electronically controlled. Typically, the access point is a door. An electronic access control door can contain several elements. At its most basic, there is a stand-alone electric lock. The lock is unlocked by an operator with a switch. To automate this, operator intervention is replaced by a reader. The reader could be a keypad where a code is entered, it could be a card reader, or it could be a biometric reader. Readers do not usually make an access decision, but send a card number to an access control panel that verifies the number against an access list. To monitor the door position a magnetic door switch can be used. In concept, the door switch is not unlike those on refrigerators or car doors. Generally only entry is controlled, and exit is uncontrolled. In cases where exit is also controlled, a second reader is used on the opposite side of the door. In cases where exit is not controlled, free exit, a device called a request-to-exit (REX) is used. Request-to-exit devices can be a push-button or a motion detector. When the button is pushed, or the motion detector detects motion at the door, the door alarm is temporarily ignored while the door is opened. Exiting a door without having to electrically unlock the door is called mechanical free egress. This is an important safety feature. In cases where the lock must be electrically unlocked on exit, the request-to-exit device also unlocks the door." [Access control. Wikipedia]
Use the design elements library Alarm and access control for drawing layout floor plans, blueprints, and wiring diagrams of intrusion systems, time and attendance systems, card and code access control security systems, internal and external security control systems using the ConceptDraw PRO diagramming and vector drawing software.
The shapes library Alarm and access control is included in the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
"An alarm device or system of alarm devices gives an audible, visual or other form of alarm signal about a problem or condition. Alarm devices are often outfitted with a siren." [Alarm device. Wikipedia]
"An access control point, which can be a door, turnstile, parking gate, elevator, or other physical barrier, where granting access can be electronically controlled. Typically, the access point is a door. An electronic access control door can contain several elements. At its most basic, there is a stand-alone electric lock. The lock is unlocked by an operator with a switch. To automate this, operator intervention is replaced by a reader. The reader could be a keypad where a code is entered, it could be a card reader, or it could be a biometric reader. Readers do not usually make an access decision, but send a card number to an access control panel that verifies the number against an access list. To monitor the door position a magnetic door switch can be used. In concept, the door switch is not unlike those on refrigerators or car doors. Generally only entry is controlled, and exit is uncontrolled. In cases where exit is also controlled, a second reader is used on the opposite side of the door. In cases where exit is not controlled, free exit, a device called a request-to-exit (REX) is used. Request-to-exit devices can be a push-button or a motion detector. When the button is pushed, or the motion detector detects motion at the door, the door alarm is temporarily ignored while the door is opened. Exiting a door without having to electrically unlock the door is called mechanical free egress. This is an important safety feature. In cases where the lock must be electrically unlocked on exit, the request-to-exit device also unlocks the door." [Access control. Wikipedia]
Use the design elements library Alarm and access control for drawing layout floor plans, blueprints, and wiring diagrams of intrusion systems, time and attendance systems, card and code access control security systems, internal and external security control systems using the ConceptDraw PRO diagramming and vector drawing software.
The shapes library Alarm and access control is included in the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
 Specification and Description Language (SDL)
Specification and Description Language (SDL)
For people in the field of systems engineering or system design, working with specification and description language (sdl) and finite state machines (fsm).
"Microsoft SharePoint is a Web application platform developed by Microsoft. First launched in 2001, SharePoint has historically been associated with intranet, content management and document management, but recent versions have significantly broader capabilities.
SharePoint comprises a multipurpose set of Web technologies backed by a common technical infrastructure. By default, SharePoint has a Microsoft Office-like interface, and it is closely integrated with the Office suite. The web tools are designed to be usable by non-technical users. SharePoint can be used to provide intranet portals, document & file management, collaboration, social networks, extranets, websites, enterprise search, and business intelligence. It also has system integration, process integration, and workflow automation capabilities.
Enterprise application software (e.g. ERP or CRM packages) often provide some SharePoint integration capability, and SharePoint also incorporates a complete development stack based on web technologies and standards-based APIs. As an application platform, SharePoint provides central management, governance, and security controls for implementation of these requirements. The SharePoint platform integrates directly into IIS - enabling bulk management, scaling, and provisioning of servers, as is often required by large organizations or cloud hosting providers." [Microsoft SharePoint. Wikipedia]
The AWS architecture diagram example "SharePoint server reference architecture for public-facing website scenario" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
SharePoint comprises a multipurpose set of Web technologies backed by a common technical infrastructure. By default, SharePoint has a Microsoft Office-like interface, and it is closely integrated with the Office suite. The web tools are designed to be usable by non-technical users. SharePoint can be used to provide intranet portals, document & file management, collaboration, social networks, extranets, websites, enterprise search, and business intelligence. It also has system integration, process integration, and workflow automation capabilities.
Enterprise application software (e.g. ERP or CRM packages) often provide some SharePoint integration capability, and SharePoint also incorporates a complete development stack based on web technologies and standards-based APIs. As an application platform, SharePoint provides central management, governance, and security controls for implementation of these requirements. The SharePoint platform integrates directly into IIS - enabling bulk management, scaling, and provisioning of servers, as is often required by large organizations or cloud hosting providers." [Microsoft SharePoint. Wikipedia]
The AWS architecture diagram example "SharePoint server reference architecture for public-facing website scenario" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
 Business Process Diagrams
Business Process Diagrams
Business Process Diagrams solution extends the ConceptDraw PRO BPM software with RapidDraw interface, templates, samples and numerous libraries based on the BPMN 1.2 and BPMN 2.0 standards, which give you the possibility to visualize equally easy simple and complex processes, to design business models, to quickly develop and document in details any business processes on the stages of project’s planning and implementation.
- How to Create a Network Security Diagram Using ConceptDraw ...
- Cyber Security Degrees | 10 Steps to Cyber Security | Network ...
- 10 Steps to Cyber Security | Network Security Diagrams | Network ...
- Design elements - Cybersecurity round icons | Cyber Security ...
- Design elements - Cybersecurity shapes | Cyber Security Degrees ...
- Design elements - Cybersecurity clipart | Cyber Security Degrees ...
- Cyber Security Degrees | Network Security Diagrams | Computer ...
- Design elements - Cybersecurity connectors | Cyber Security ...
- Network Security Model | Network Security | Secure Wireless ...
- Secure Wireless Network | Network Security Diagrams ...
- How to Create a Network Security Diagram Using ConceptDraw PRO
- ConceptDraw PRO Network Diagram Tool | Network Security ...
- Network Security Diagrams | IT Security Solutions | Network Security ...
- Recommended network architecture for BlackBerry SWS | Network ...
- Network Security Devices | Network Security | Network Security ...
- Discuss Two Types Of Communication Standard Commonly Used
- Internet symbols - Vector stencils library | | Network Security ...
- Hardware And Networking In Diagrams Format Pdf
- Cloud Computing | AWS Administration and Security - Vector ...
- Standard Used In Design Office Example










-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)














-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)



-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)











-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)