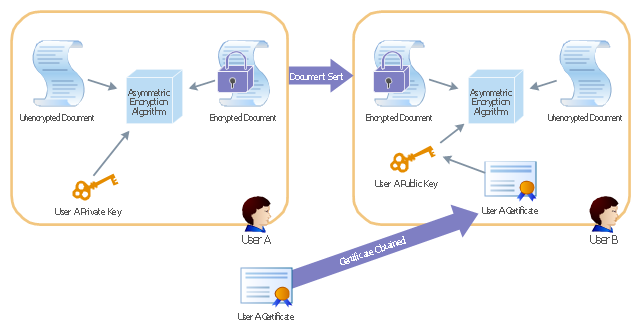
This AD diagram example was redesigned from the picture "Asymmetric
encryption" from the book "Active Directory for Dummies".
"Asymmetric Encryption:
This scenario uses a public and private key pair that is associated with each other. With this type of encryption, one of the keys is used to encrypt the data in such a way that only the corresponding second key is capable of decrypting the information. ...
In asymmetric encryption, two different keys are involved in the process: one for encrypting the document and a different but related key for decrypting the document. The two keys are generated at the same time so that if a document is encrypted with one of the keys, only the second related key can decrypt the document. ... Typically, these keys are referred to as a private key and a public key. A private key is one that is generated for a particular user and is never shared with any other user or computer. A public key is typically one of the pieces of data that’s stored in a PKI certificate. Although this type of encryption creates a very secure way of sharing data, an added benefit is you knowing that a piece of data decrypted by using a particular user’s public key must have come from that user because no other user would have the private key the document was encrypted with."
[Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Asymmetric encryption" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
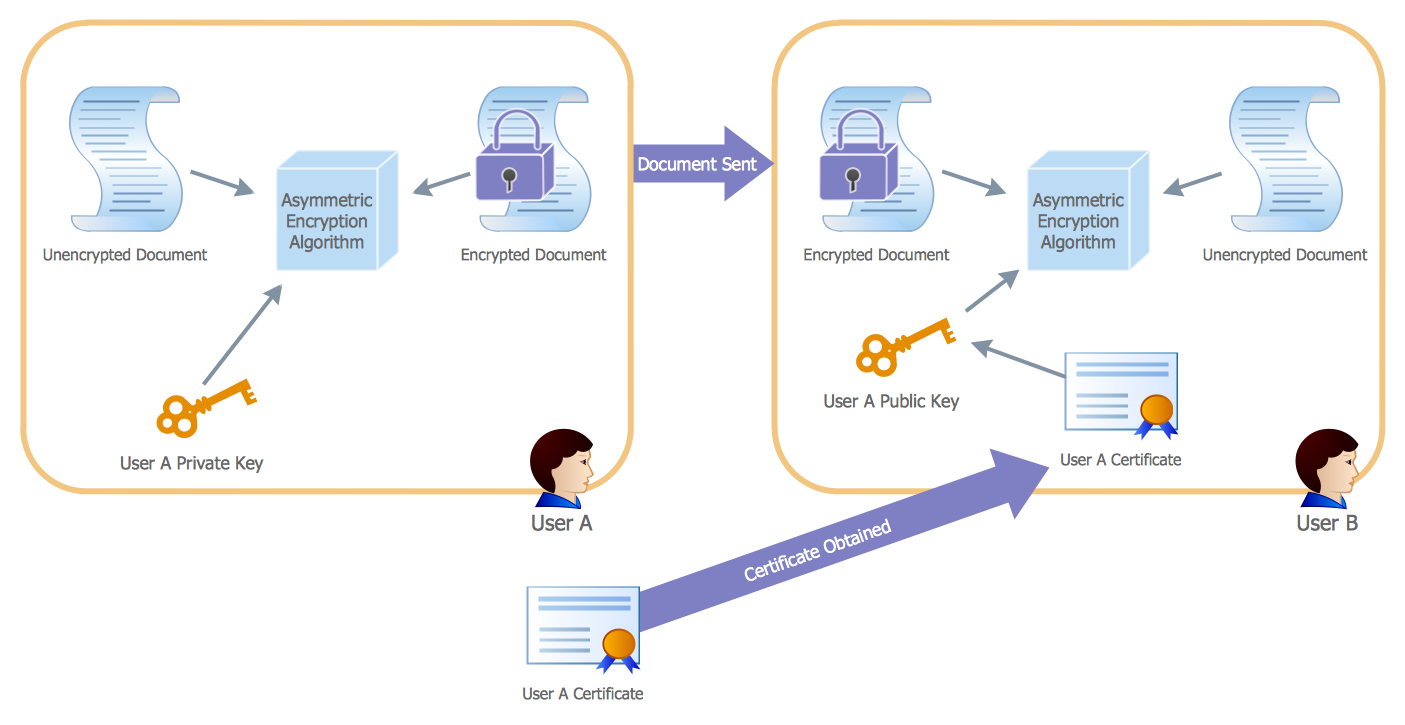
encryption" from the book "Active Directory for Dummies".
"Asymmetric Encryption:
This scenario uses a public and private key pair that is associated with each other. With this type of encryption, one of the keys is used to encrypt the data in such a way that only the corresponding second key is capable of decrypting the information. ...
In asymmetric encryption, two different keys are involved in the process: one for encrypting the document and a different but related key for decrypting the document. The two keys are generated at the same time so that if a document is encrypted with one of the keys, only the second related key can decrypt the document. ... Typically, these keys are referred to as a private key and a public key. A private key is one that is generated for a particular user and is never shared with any other user or computer. A public key is typically one of the pieces of data that’s stored in a PKI certificate. Although this type of encryption creates a very secure way of sharing data, an added benefit is you knowing that a piece of data decrypted by using a particular user’s public key must have come from that user because no other user would have the private key the document was encrypted with."
[Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Asymmetric encryption" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
 Active Directory Diagrams
Active Directory Diagrams
Active Directory Diagrams solution extends ConceptDraw PRO software with samples, templates and libraries of vector stencils for drawing the AD diagrams to visualize the detail structures of the Microsoft Windows networks.
Active Directory
The Active Directory Diagrams solution from ConceptDraw Solution Park extends ConceptDraw PRO diagramming and vector drawing software to help network engineers, designers and administrators efficiently design and create various active directory diagrams.Active Directory Domain
System administrators of the whole world successfully use the Active Directory Domain Services. ConceptDraw PRO offers the Active Directory Diagrams Solution from the Computer and Networks Area with powerful drawing tools developed specially for all specialists which need create various active directory domain diagrams in their work activity.- Active Directory Domain | Active Directory Diagram | Active Directory ...
- Create Flow Chart on Mac | Active Directory diagram - Asymmetric ...
- Active Directory diagram - Asymmetric encryption | Active Directory ...
- Active Directory diagram - Asymmetric encryption | Access control ...
- Website launch - Flowchart | Active Directory Diagrams | Network ...
- Active Directory Diagram | Network Diagramming Software for ...
- Entity Relationship Diagram Symbols | ERD Symbols and Meanings ...
- Active Directory Diagram | Active Directory Domain | Active Directory ...
- Examples of Flowcharts, Org Charts and More | Basic CCTV System ...
- Active Directory Diagram
- AD LDS as a phone book service | Active Directory structure ...
- ConceptDraw Solution Park | Comparing ConceptDraw PRO to ...
- Conceptual Diagram Of Active Directory
- Active Directory Diagram
- Active Directory Diagrams | Network Diagramming Software for ...
- Diagramme Zeichnen | Symboles Organigramme | Conception d ...
- Active Directory Diagram | Active Directory structure diagram ...
- Active Directory Domain Services | Design Element: Active Directory ...
- Active Directory Domain Services | Active Directory Diagram | Active ...
- Active Directory Diagram | Tree and Forest (Full Trust) - Active ...