"General packet radio service (GPRS) is a packet oriented mobile data service on the 2G and 3G cellular communication system's global system for mobile communications (GSM). GPRS was originally standardized by European Telecommunications Standards Institute (ETSI) in response to the earlier CDPD and i-mode packet-switched cellular technologies. It is now maintained by the 3rd Generation Partnership Project (3GPP).
GPRS usage is typically charged based on volume of data transferred, contrasting with circuit switched data, which is usually billed per minute of connection time. Usage above the bundle cap is either charged per megabyte or disallowed.
GPRS is a best-effort service, implying variable throughput and latency that depend on the number of other users sharing the service concurrently, as opposed to circuit switching, where a certain quality of service (QoS) is guaranteed during the connection. In 2G systems, GPRS provides data rates of 56–114 kbit/ second. 2G cellular technology combined with GPRS is sometimes described as 2.5G, that is, a technology between the second (2G) and third (3G) generations of mobile telephony. It provides moderate-speed data transfer, by using unused time division multiple access (TDMA) channels in, for example, the GSM system. GPRS is integrated into GSM Release 97 and newer releases." [General Packet Radio Service. Wikipedia]
This GPRS network diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Telecommunication Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
GPRS usage is typically charged based on volume of data transferred, contrasting with circuit switched data, which is usually billed per minute of connection time. Usage above the bundle cap is either charged per megabyte or disallowed.
GPRS is a best-effort service, implying variable throughput and latency that depend on the number of other users sharing the service concurrently, as opposed to circuit switching, where a certain quality of service (QoS) is guaranteed during the connection. In 2G systems, GPRS provides data rates of 56–114 kbit/ second. 2G cellular technology combined with GPRS is sometimes described as 2.5G, that is, a technology between the second (2G) and third (3G) generations of mobile telephony. It provides moderate-speed data transfer, by using unused time division multiple access (TDMA) channels in, for example, the GSM system. GPRS is integrated into GSM Release 97 and newer releases." [General Packet Radio Service. Wikipedia]
This GPRS network diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Telecommunication Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Personal area (PAN) networks. Computer and Network Examples
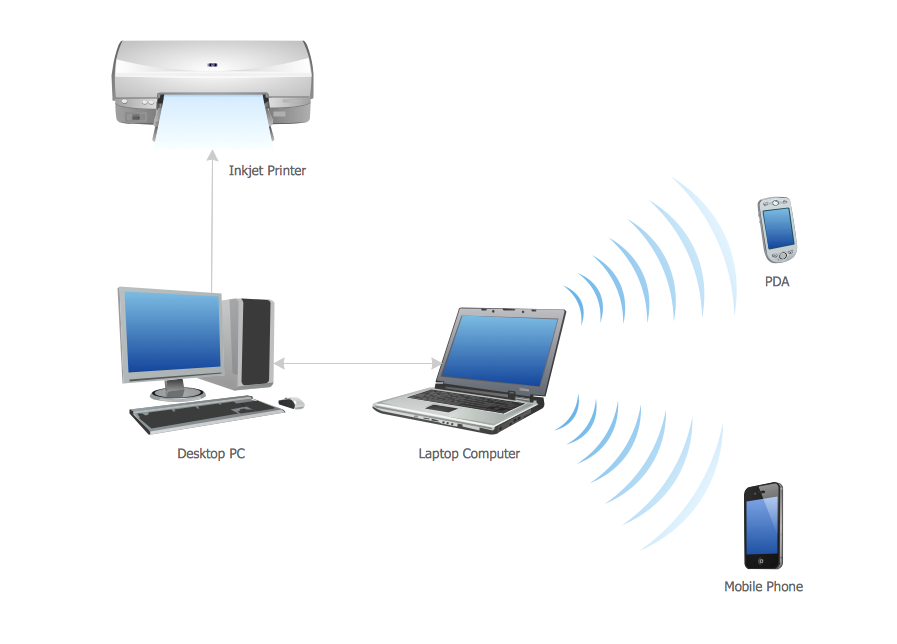
Personal area network (PAN) is a network organized on a limited area and used for data transmission between various personal devices, such as computers, tablets, laptops, telephones, different digital and mobile devices, etc. and also for connecting to higher level network and Internet. PAN is used to manage the interconnections of IT devices which surround a single user and generally contains such appliances, as cordless mice, keyboard, phone, and Bluetooth handsets. PANs can be wired with computer buses, or wirelessly connected to the Internet using such network technologies as Bluetooth, Z-Wave, ZigBee, IrDa, UWB, Body Area Network. PANs have a lot of pros and cons, they are expedient, lucrative and handy, but sometimes have bad connection with other networks on the same radio bands, Bluetooth has distance limits and slow data transfer speed, but is comparatively safe. ConceptDraw DIAGRAM diagramming software supplied with numerous solutions of Computer and Networks Area included to ConceptDraw Solution Park perfectly suits for designing the Personal Area Networks.
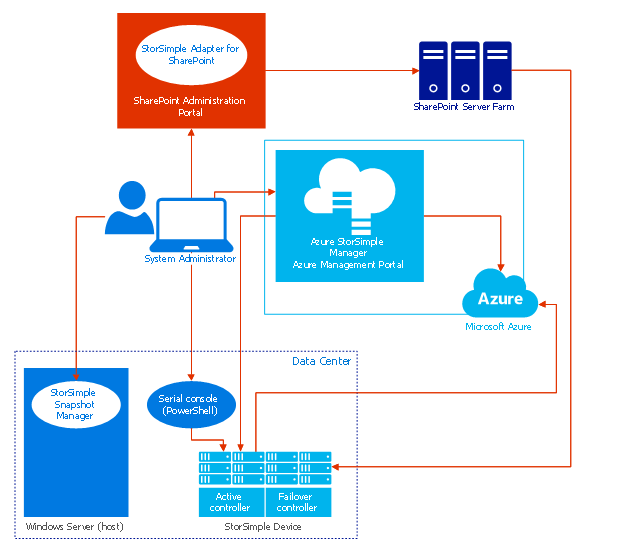
This example of cloud computing system architecture diagram was created on the base of picture in the article "What is StorSimple?" by Sharon Smith from the Microsoft Azure website.
"Microsoft Azure StorSimple is an efficient, cost-effective, and manageable solution that eliminates many of the issues and expense associated with enterprise storage and data protection. It uses a proprietary device (the Microsoft Azure StorSimple device) and integrated management tools to provide a seamless view of all enterprise storage, including cloud storage." [azure.microsoft.com/ en-us/ documentation/ articles/ storsimple-overview/ ]
The diagram example "Microsoft Azure StorSimple architecture" was created using ConceptDraw PRO diagramming and vector drawing software extended with the Azure Architecture solution from the Computer and Networks area of ConceptDraw Solution Park.
"Microsoft Azure StorSimple is an efficient, cost-effective, and manageable solution that eliminates many of the issues and expense associated with enterprise storage and data protection. It uses a proprietary device (the Microsoft Azure StorSimple device) and integrated management tools to provide a seamless view of all enterprise storage, including cloud storage." [azure.microsoft.com/ en-us/ documentation/ articles/ storsimple-overview/ ]
The diagram example "Microsoft Azure StorSimple architecture" was created using ConceptDraw PRO diagramming and vector drawing software extended with the Azure Architecture solution from the Computer and Networks area of ConceptDraw Solution Park.
HelpDesk
How to Convert a Mind Map into MS Word Document
Mind maps are often used for structuring ideas, planning, and organizing of various documents. ConceptDraw MINDMAP allows you to transfer a mind map to MS Word format using its export facilities. You can convert a mind map to an MS Word outline using the set of standard templates, or even your custom template. Thus, your mind map will be transformed into the proper document format. Using a custom MS Word template allows you to apply your individual style to each document, being exported from ConceptDraw MINDMAP. You can use a mind mapping to capture ideas and structure information. Then make a quick conversion to MS Word and you finally obtain a clean and stylish document.The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The vector stencils library "Cisco LAN" contains 23 symbols of local area network (LAN) devices and equipment for drawing Cisco LAN topology diagrams.
"Network topology describes the layout of interconnections between devices and network segments. At the Data Link Layer and Physical Layer, a wide variety of LAN topologies have been used, including ring, bus, mesh and star, but the most common LAN topology in use today is switched Ethernet. At the higher layers, the Internet Protocol (TCP/ IP) has become the standard, replacing NetBEUI, IPX/ SPX, AppleTalk and others.
Simple LANs generally consist of one or more switches. A switch can be connected to a router, cable modem, or ADSL modem for Internet access. Complex LANs are characterized by their use of redundant links with switches using the spanning tree protocol to prevent loops, their ability to manage differing traffic types via quality of service (QoS), and to segregate traffic with VLANs. A LAN can include a wide variety of network devices such as switches, firewalls, routers, load balancers, and sensors.
LANs can maintain connections with other LANs via leased lines, leased services, or the Internet using virtual private network technologies. Depending on how the connections are established and secured in a LAN, and the distance involved, a LAN may also be classified as a metropolitan area network (MAN) or a wide area network (WAN)." [Local area network. Wikipedia]
The symbols example "Cisco LAN - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network topology describes the layout of interconnections between devices and network segments. At the Data Link Layer and Physical Layer, a wide variety of LAN topologies have been used, including ring, bus, mesh and star, but the most common LAN topology in use today is switched Ethernet. At the higher layers, the Internet Protocol (TCP/ IP) has become the standard, replacing NetBEUI, IPX/ SPX, AppleTalk and others.
Simple LANs generally consist of one or more switches. A switch can be connected to a router, cable modem, or ADSL modem for Internet access. Complex LANs are characterized by their use of redundant links with switches using the spanning tree protocol to prevent loops, their ability to manage differing traffic types via quality of service (QoS), and to segregate traffic with VLANs. A LAN can include a wide variety of network devices such as switches, firewalls, routers, load balancers, and sensors.
LANs can maintain connections with other LANs via leased lines, leased services, or the Internet using virtual private network technologies. Depending on how the connections are established and secured in a LAN, and the distance involved, a LAN may also be classified as a metropolitan area network (MAN) or a wide area network (WAN)." [Local area network. Wikipedia]
The symbols example "Cisco LAN - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The vector stencils library "Hardware" contains 32 computer hardware and telecommunication equipment icons.
Use it to design your computing and telecom illustrations and infographics with ConceptDraw PRO diagramming and vector drawing software.
The vector stencils library "Hardware" is included in the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
Use it to design your computing and telecom illustrations and infographics with ConceptDraw PRO diagramming and vector drawing software.
The vector stencils library "Hardware" is included in the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
- Simple Diagram Of Lan Man Wan
- Simple Diagram Of A Cellphone Tower
- Call center network diagram | Computers and network isometric ...
- Cisco LAN - Vector stencils library | Simple Networking Diagram Of ...
- Wan Network Simple Diagram Wikipedia
- Wireless router network diagram | Cisco Routers. Cisco icons ...
- Physical LAN topology diagram | Network Diagram Software LAN ...
- Network Printer | Physical LAN topology diagram | Network Diagram ...
- Physical LAN and WAN diagram - Template | Wide area network ...
- Physical LAN and WAN diagram
- Simple Affinity Diagram Example
- Simple Diagram Of Man Wan
- Network diagrams with ConceptDraw PRO | Server | Rack Rate ...
- Basic Flowchart Symbols and Meaning | Process Flowchart | Types ...
- How To use Switches in Network Diagram | Star Network Topology ...
- Basic Network Diagram | Network Topology | Network Configuration ...
- Simple Diagram Of Lan Man Anf Wan
- Network Printer | Network Diagram Software | Network diagrams ...
- Basic Network Diagram | Network Diagram Software LAN Network ...
- Diagram Of Desktop Laptop And Tower






-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)