"In software engineering, software system safety optimizes system safety in the design, development, use, and maintenance of software systems and their integration with safety-critical hardware systems in an operational environment." [Software system safety. Wikipedia]
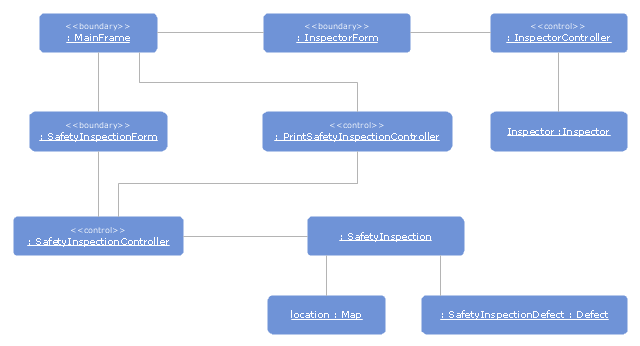
The UML object diagram example "Safety inspection" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Rapid UML solution from the Software Development area of ConceptDraw Solution Park.
The UML object diagram example "Safety inspection" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Rapid UML solution from the Software Development area of ConceptDraw Solution Park.
 Software Development Area
Software Development Area
Solutions from the Software Development Area of ConceptDraw Solution Park collect templates, samples and libraries of vector stencils for drawing the software engineering diagrams and user interface design prototypes.
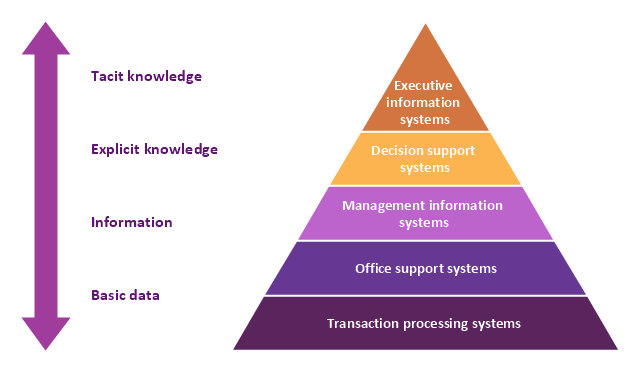
A five level pyramid model of different types of Information Systems based on the information processing requirement of different levels in the organization. The first level represents transaction processing systems to process basic data. The second level represents office support systems to process information in office. The third level represents management information systems to process information by managers. The fourth level represents decision support systems to process explicit knowledge. The fifth level represents executive information systems to process tacit knowledge.
"A Computer(-Based) Information System is essentially an IS using computer technology to carry out some or all of its planned tasks. The basic components of computer based information system are:
(1) Hardware - these are the devices like the monitor, processor, printer and keyboard, all of which work together to accept, process, show data and information.
(2) Software - are the programs that allow the hardware to process the data.
(3) Databases - are the gathering of associated files or tables containing related data.
(4) Networks - are a connecting system that allows diverse computers to distribute resources.
(5) Procedures - are the commands for combining the components above to process information and produce the preferred output.
The first four components (hardware, software, database and network) make up what is known as the information technology platform. Information technology workers could then use these components to create information systems that watch over safety measures, risk and the management of data. These actions are known as information technology services." [Information systems. Wikipedia]
This pyramid diagram was redesigned using the ConceptDraw PRO diagramming and vector drawing software from Wikimedia Commons file Five-Level-Pyramid-model.png. [commons.wikimedia.org/ wiki/ File:Five-Level-Pyramid-model.png]
This file is licensed under the Creative Commons Attribution 3.0 Unported license. [creativecommons.org/ licenses/ by/ 3.0/ deed.en]
The triangle chart example "Information systems types" is included in the Pyramid Diagrams solution from the Marketing area of ConceptDraw Solution Park.
"A Computer(-Based) Information System is essentially an IS using computer technology to carry out some or all of its planned tasks. The basic components of computer based information system are:
(1) Hardware - these are the devices like the monitor, processor, printer and keyboard, all of which work together to accept, process, show data and information.
(2) Software - are the programs that allow the hardware to process the data.
(3) Databases - are the gathering of associated files or tables containing related data.
(4) Networks - are a connecting system that allows diverse computers to distribute resources.
(5) Procedures - are the commands for combining the components above to process information and produce the preferred output.
The first four components (hardware, software, database and network) make up what is known as the information technology platform. Information technology workers could then use these components to create information systems that watch over safety measures, risk and the management of data. These actions are known as information technology services." [Information systems. Wikipedia]
This pyramid diagram was redesigned using the ConceptDraw PRO diagramming and vector drawing software from Wikimedia Commons file Five-Level-Pyramid-model.png. [commons.wikimedia.org/ wiki/ File:Five-Level-Pyramid-model.png]
This file is licensed under the Creative Commons Attribution 3.0 Unported license. [creativecommons.org/ licenses/ by/ 3.0/ deed.en]
The triangle chart example "Information systems types" is included in the Pyramid Diagrams solution from the Marketing area of ConceptDraw Solution Park.
The vector stencils library "Fire safety equipment" contains 19 clipart images of fire safety equipment which you can easy use in your presentations and illustrations.
"Fire safety refers to precautions that are taken to prevent or reduce the likelihood of a fire that may result in death, injury, or property damage, alert those in a structure to the presence of an uncontrolled fire in the event one occurs, better enable those threatened by fire to survive in and evacuate from affected areas, or to reduce the damage caused by a fire. Fire safety measures include those that are planned during the construction of a building or implemented in structures that are already standing, and those that are taught to occupants of the building.
Threats to fire safety are referred to as fire hazards. A fire hazard may include a situation that increases the likelihood a fire may start or may impede escape in the event a fire occurs." [Fire safety. Wikipedia]
The clip art example "Fire safety equipment - Vector stencils library" was created in the ConceptDraw PRO diagramming and vector drawing software using the Presentation Clipart solution from the Illustration area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ illustrations-presentation-clipart
"Fire safety refers to precautions that are taken to prevent or reduce the likelihood of a fire that may result in death, injury, or property damage, alert those in a structure to the presence of an uncontrolled fire in the event one occurs, better enable those threatened by fire to survive in and evacuate from affected areas, or to reduce the damage caused by a fire. Fire safety measures include those that are planned during the construction of a building or implemented in structures that are already standing, and those that are taught to occupants of the building.
Threats to fire safety are referred to as fire hazards. A fire hazard may include a situation that increases the likelihood a fire may start or may impede escape in the event a fire occurs." [Fire safety. Wikipedia]
The clip art example "Fire safety equipment - Vector stencils library" was created in the ConceptDraw PRO diagramming and vector drawing software using the Presentation Clipart solution from the Illustration area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ illustrations-presentation-clipart
The vector clipart library Access and security contains 17 images of access control and security system equipment.
"In the fields of physical security and information security, access control is the selective restriction of access to a place or other resource. The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.
Locks and login credentials are two analogous mechanisms of access control. ...
The term access control refers to the practice of restricting entrance to a property, a building, or a room to authorized persons. Physical access control can be achieved by a human (a guard, bouncer, or receptionist), through mechanical means such as locks and keys, or through technological means such as access control systems like the mantrap. Within these environments, physical key management may also be employed as a means of further managing and monitoring access to mechanically keyed areas or access to certain small assets." [Access control. Wikipedia]
Use the vector stencils library Access and security to draw illustrations and diagrams of safety and security system equipment using the ConceptDraw PRO diagramming and vector drawing software.
The clipart example "Design elements - Access and security" is included in the Safety and Security solution from the Illustration area of ConceptDraw Solution Park.
"In the fields of physical security and information security, access control is the selective restriction of access to a place or other resource. The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.
Locks and login credentials are two analogous mechanisms of access control. ...
The term access control refers to the practice of restricting entrance to a property, a building, or a room to authorized persons. Physical access control can be achieved by a human (a guard, bouncer, or receptionist), through mechanical means such as locks and keys, or through technological means such as access control systems like the mantrap. Within these environments, physical key management may also be employed as a means of further managing and monitoring access to mechanically keyed areas or access to certain small assets." [Access control. Wikipedia]
Use the vector stencils library Access and security to draw illustrations and diagrams of safety and security system equipment using the ConceptDraw PRO diagramming and vector drawing software.
The clipart example "Design elements - Access and security" is included in the Safety and Security solution from the Illustration area of ConceptDraw Solution Park.
Software development with ConceptDraw Products
Internet solutions on ConceptDraw base. What may interest developers of Internet solutions.- UML object diagram - Safety inspection | Diagramming Software for ...
- Diagramming Software for Design UML Object Diagrams | UML ...
- Safety Building Management System Clipart
- UML timing diagram - Inspection | UML object diagram - Safety ...
- UML object diagram - Safety inspection | Strategic planning cycle ...
- Diagramming Software for Design UML Object Diagrams ...
- Memory Object Diagram | UML Object Diagram. Design Elements ...
- Draw The Logical Structure Of The Computer System Clearly ...
- Fta Safety
- How To Implement Collaborative Project Management | Competitor ...
- Fault Tree Analysis Software | Design elements - Fault tree analysis ...
- Safety and Security | Fire safety equipment - Vector stencils library ...
- Safety and Security | Network Security Model | Access and security ...
- Alarm System Gui Design
- Fire safety equipment - Vector stencils library | Safety and Security ...
- Diagramming Software for Design UML Object Diagrams | Design ...
- FTA diagram - Hazard analysis | Accident analytic tree - FTA ...
- Water Safety Symbols
- Flow chart Example. Warehouse Flowchart | Safety and Security ...