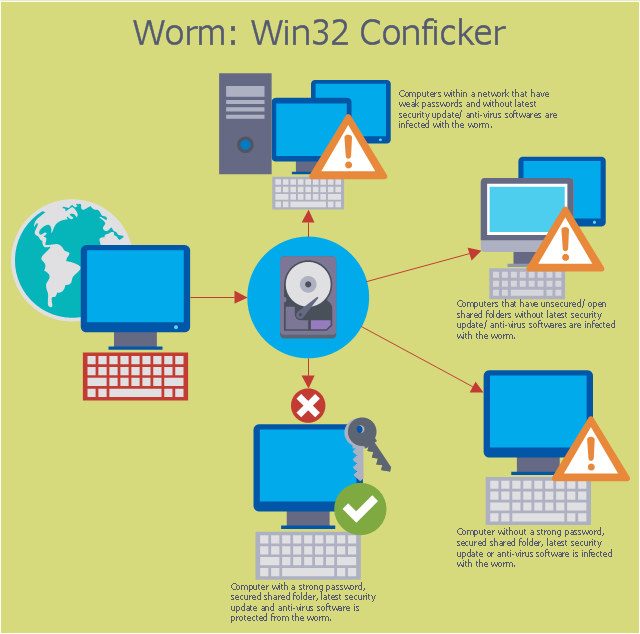
This computer security diagram example was designed on the base of the Wikimedia Commons file: Conficker.svg. [commons.wikimedia.org/ wiki/ File:Conficker.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer." [Computer worm. Wikipedia]
The cybersecurity diagram example "Spread of Conficker worm" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer." [Computer worm. Wikipedia]
The cybersecurity diagram example "Spread of Conficker worm" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw PRO software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
- Spread of Conficker worm | Spread of Conficker worm | Design ...
- Cyber Security Degrees | Spread of Conficker worm | Network ...
- Spread of Conficker worm | Computer network - Vector stencils ...
- Spread of Conficker worm | Entity-Relationship Diagram (ERD ...
- Basic computer network diagram | Network topologies diagram ...
- In searching of alternative to MS Visio for MAC and PC with ...
- Computer Worm Visio
- Computer network - Vector stencils library | In searching of ...
- Computer Worm And Virus In Block Diagram
- Campus Area Networks (CAN). Computer and Network Examples ...
- Network Diagrams for Bandwidth Management | Home area ...
- Network Security Devices | Network Security Diagrams | Network ...
- Network Security Devices | Network Security Diagrams | Network ...
- In searching of alternative to MS Visio for MAC and PC with ...
- Recommended network architecture for BlackBerry SWS | Firewall ...
- Basic computer network diagram | Network topologies diagram | Bus ...
- Top 5 Android Flow Chart Apps | Example of DFD for Online Store ...
- Network Security Diagrams | Network Security | Design elements ...
- Computer network - Vector stencils library | Basic computer network ...