AWS Architecture Diagrams
AWS Architecture Diagrams
AWS Architecture Diagrams with powerful drawing tools and numerous predesigned Amazon icons and AWS simple icons is the best for creation the AWS Architecture Diagrams, describing the use of Amazon Web Services or Amazon Cloud Services, their application for development and implementation the systems running on the AWS infrastructure. The multifarious samples give you the good understanding of AWS platform, its structure, services, resources and features, wide opportunities, advantages and benefits from their use; solution’s templates are essential and helpful when designing, description and implementing the AWS infrastructure based systems. Use them in technical documentation, advertising and marketing materials, in specifications, presentation slides, whitepapers, datasheets, posters, etc.
This Azure cloud architecture pattern diagram template was created on the base of figure in the article "Valet Key Pattern" from the Microsoft Developer Network (MSDN) website.
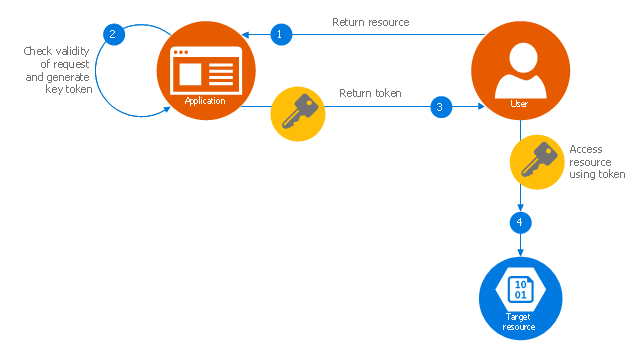
"Valet Key Pattern.
Use a token or key that provides clients with restricted direct access to a specific resource or service in order to offload data transfer operations from the application code. This pattern is particularly useful in applications that use cloud-hosted storage systems or queues, and can minimize cost and maximize scalability and performance. ...
Client programs and web browsers often need to read and write files or data streams to and from an application’s storage. ...
Data stores have the capability to handle upload and download of data directly, without requiring the application to perform any processing to move this data, but this typically requires the client to have access to the security credentials for the store.
... applications must be able to securely control access to data in a granular way, but still reduce the load on the server by setting up this connection and then allowing the client to communicate directly with the data store to perform the required read or write operations. ...
To resolve the problem of controlling access to a data store where the store itself cannot manage authentication and authorization of clients, one typical solution is to restrict access to the data store’s public connection and provide the client with a key or token that the data store itself can validate.
This key or token is usually referred to as a valet key. It provides time-limited access to specific resources and allows only predefined operations such as reading and writing to storage or queues, or uploading and downloading in a web browser. Applications can create and issue valet keys to client devices and web browsers quickly and easily, allowing clients to perform the required operations without requiring the application to directly handle the data transfer. This removes the processing overhead, and the consequent impact on performance and scalability, from the application and the server." [msdn.microsoft.com/ ru-RU/ library/ dn568102.aspx]
The Azure cloud system architecture diagram template "Valet key pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
"Valet Key Pattern.
Use a token or key that provides clients with restricted direct access to a specific resource or service in order to offload data transfer operations from the application code. This pattern is particularly useful in applications that use cloud-hosted storage systems or queues, and can minimize cost and maximize scalability and performance. ...
Client programs and web browsers often need to read and write files or data streams to and from an application’s storage. ...
Data stores have the capability to handle upload and download of data directly, without requiring the application to perform any processing to move this data, but this typically requires the client to have access to the security credentials for the store.
... applications must be able to securely control access to data in a granular way, but still reduce the load on the server by setting up this connection and then allowing the client to communicate directly with the data store to perform the required read or write operations. ...
To resolve the problem of controlling access to a data store where the store itself cannot manage authentication and authorization of clients, one typical solution is to restrict access to the data store’s public connection and provide the client with a key or token that the data store itself can validate.
This key or token is usually referred to as a valet key. It provides time-limited access to specific resources and allows only predefined operations such as reading and writing to storage or queues, or uploading and downloading in a web browser. Applications can create and issue valet keys to client devices and web browsers quickly and easily, allowing clients to perform the required operations without requiring the application to directly handle the data transfer. This removes the processing overhead, and the consequent impact on performance and scalability, from the application and the server." [msdn.microsoft.com/ ru-RU/ library/ dn568102.aspx]
The Azure cloud system architecture diagram template "Valet key pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
This Azure cloud architecture pattern diagram template was created on the base of figure in the article "Health Endpoint Monitoring Pattern" from the Microsoft Developer Network (MSDN) website.
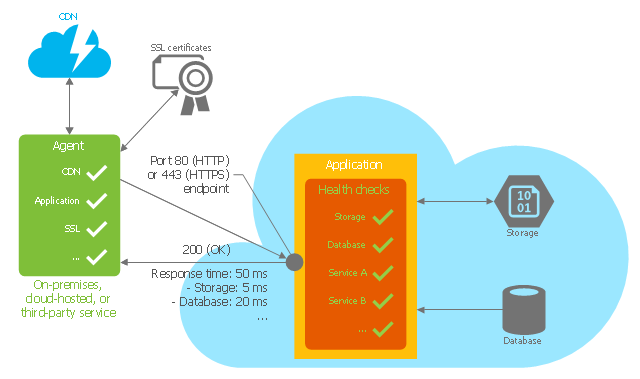
"Health Endpoint Monitoring Pattern.
Implement functional checks within an application that external tools can access through exposed endpoints at regular intervals. This pattern can help to verify that applications and services are performing correctly. ...
It is good practice—and often a business requirement—to monitor web applications, and middle-tier and shared services, to ensure that they are available and performing correctly. However, it is more difficult to monitor services running in the cloud than it is to monitor on-premises services. ...
Implement health monitoring by sending requests to an endpoint on the application. The application should perform the necessary checks, and return an indication of its status.
A health monitoring check typically combines two factors: the checks (if any) performed by the application or service in response to the request to the health verification endpoint, and analysis of the result by the tool or framework that is performing the health verification check. The response code indicates the status of the application and, optionally, any components or services it uses. The latency or response time check is performed by the monitoring tool or framework." [msdn.microsoft.com/ ru-RU/ library/ dn589789.aspx]
The Azure cloud system architecture diagram template "Health endpoint monitoring pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
"Health Endpoint Monitoring Pattern.
Implement functional checks within an application that external tools can access through exposed endpoints at regular intervals. This pattern can help to verify that applications and services are performing correctly. ...
It is good practice—and often a business requirement—to monitor web applications, and middle-tier and shared services, to ensure that they are available and performing correctly. However, it is more difficult to monitor services running in the cloud than it is to monitor on-premises services. ...
Implement health monitoring by sending requests to an endpoint on the application. The application should perform the necessary checks, and return an indication of its status.
A health monitoring check typically combines two factors: the checks (if any) performed by the application or service in response to the request to the health verification endpoint, and analysis of the result by the tool or framework that is performing the health verification check. The response code indicates the status of the application and, optionally, any components or services it uses. The latency or response time check is performed by the monitoring tool or framework." [msdn.microsoft.com/ ru-RU/ library/ dn589789.aspx]
The Azure cloud system architecture diagram template "Health endpoint monitoring pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
- 3-Tier Auto-scalable Web Application Architecture | 2-Tier Auto ...
- Enterprise Architecture Diagrams | AWS Architecture Diagrams ...
- Web Service Diagram
- Block diagram - Document management system architecture ...
- AWS Architecture Diagrams | Amazon Web Services Diagrams ...
- 3-Tier Auto-scalable Web Application Architecture | Amazon Web ...
- Amazon Web Services Diagrams diagramming tool for architecture ...
- Amazon Web Services Diagrams diagramming tool for architecture ...
- 2-Tier Auto-scalable Web Application Architecture in 1 AZ (v2.0 ...
- 3-Tier Auto-scalable Web Application Architecture | Amazon Web ...
- Amazon Web Services Diagrams diagramming tool for architecture
- 3-Tier Auto-scalable Web Application Architecture | Amazon Web ...
- How To create Diagrams for Amazon Web Services architecture ...
- Amazon Web Services Diagrams diagramming tool for architecture
- Amazon Web Services Diagrams diagramming tool for architecture ...
- Diagramming tool - Amazon Web Services and Cloud Computing ...
- Amazon Web Services Diagrams diagramming tool for architecture ...
- Diagramming tool - Amazon Web Services and Cloud Computing ...
- Microsoft Azure | Azure Architecture | Microsoft Azure reference ...
- SharePoint server reference architecture for public-facing website ...