Personal area (PAN) networks. Computer and Network Examples
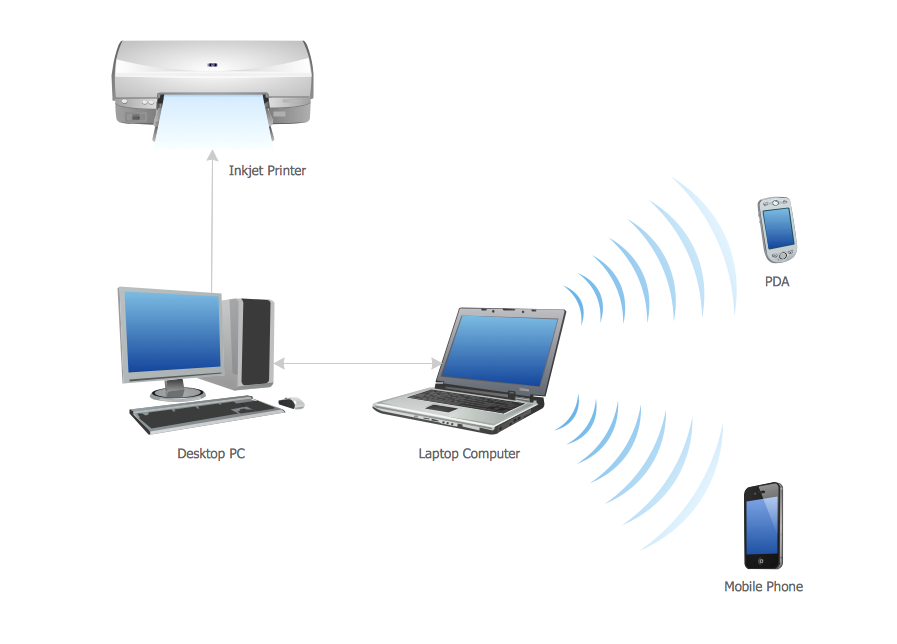
Personal area network (PAN) is a network organized on a limited area and used for data transmission between various personal devices, such as computers, tablets, laptops, telephones, different digital and mobile devices, etc. and also for connecting to higher level network and Internet. PAN is used to manage the interconnections of IT devices which surround a single user and generally contains such appliances, as cordless mice, keyboard, phone, and Bluetooth handsets. PANs can be wired with computer buses, or wirelessly connected to the Internet using such network technologies as Bluetooth, Z-Wave, ZigBee, IrDa, UWB, Body Area Network. PANs have a lot of pros and cons, they are expedient, lucrative and handy, but sometimes have bad connection with other networks on the same radio bands, Bluetooth has distance limits and slow data transfer speed, but is comparatively safe. ConceptDraw DIAGRAM diagramming software supplied with numerous solutions of Computer and Networks Area included to ConceptDraw Solution Park perfectly suits for designing the Personal Area Networks.
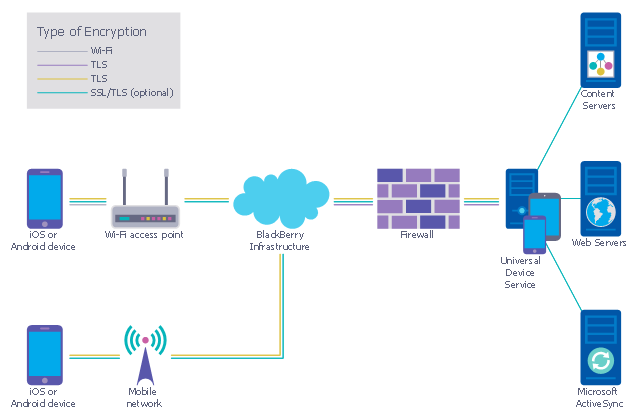
This example was designed on the base of the diagram from the "BYOD Guidance: BlackBerry Secure Work Space" on the website of the UK Communications Electronics Security Group (CESG).
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
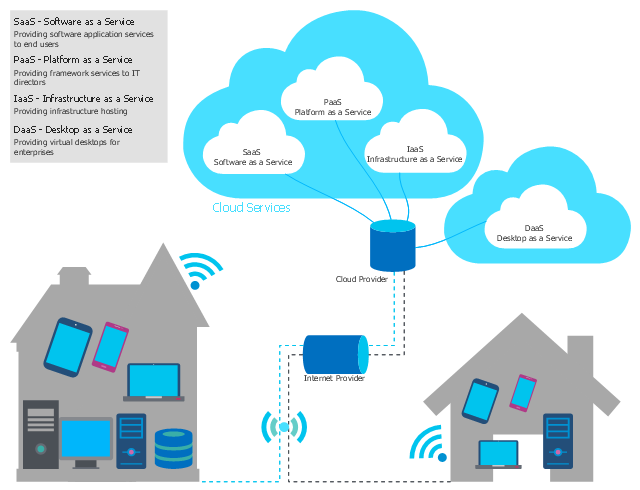
This cloud computing diagram example was drawn on the base of Wikimedia Commons file: Schéma-Cloud-Computing.png. [commons.wikimedia.org/ wiki/ File:Schéma-Cloud-Computing.png]
This file is licensed under the Creative Commons Attribution 3.0 Unported license. [creativecommons.org/ licenses/ by/ 3.0/ deed.en]
"Service models
Though service-oriented architecture advocates "everything as a service" (with the acronyms EaaS or XaaS or simply aas), cloud-computing providers offer their "services" according to different models, which happen to form a stack: infrastructure-, platform- and software-as-a-service." [Cloud computing. Wikipedia]
The example "Cloud computing diagram" was drawn using ConceptDraw PRO software extended with the Cloud Computing Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
This file is licensed under the Creative Commons Attribution 3.0 Unported license. [creativecommons.org/ licenses/ by/ 3.0/ deed.en]
"Service models
Though service-oriented architecture advocates "everything as a service" (with the acronyms EaaS or XaaS or simply aas), cloud-computing providers offer their "services" according to different models, which happen to form a stack: infrastructure-, platform- and software-as-a-service." [Cloud computing. Wikipedia]
The example "Cloud computing diagram" was drawn using ConceptDraw PRO software extended with the Cloud Computing Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
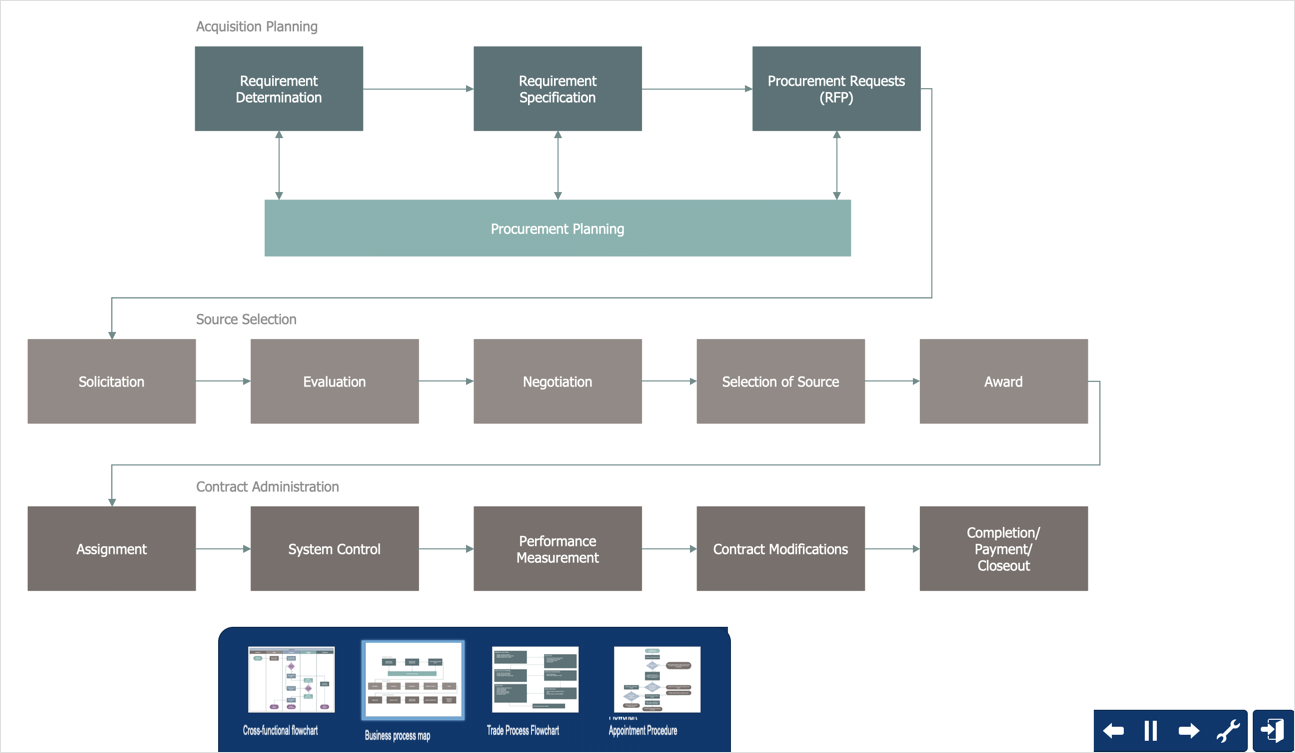
 Infographics Area
Infographics Area
Solutions of the area What is Infographics from ConceptDraw Solution Park collect templates, samples and vector stencils libraries with design elements for the drawing information graphics.
HelpDesk
How to Perform a Dynamic Presentation
ConceptDraw DIAGRAM document can be displayed as a dynamic interactive presentation. You can select presentation options using a Presentation panel. And even during presentation performance, you can make it accurate and up to date in a moment: edit the document by making changes, adding comments. ConceptDraw DIAGRAM allows you to save a presentation as a slide show that opens immediately in a full-screen. Any ConceptDraw presentation can be performed in three ways; manually, automatic slide-show, and cyclic-playing mode.
 Windows 10 User Interface
Windows 10 User Interface
Windows 10 User Interface solution extends significantly ConceptDraw DIAGRAM functionality with look-and-feel functions of GUI software and makes it a great assistant for Win10 designers, developers, and software engineers. This solution provides a wide s
This example was designed on the base of the diagram from the "BYOD Guidance: BlackBerry Secure Work Space" on the website of the UK Communications Electronics Security Group (CESG).
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
 iPhone User Interface
iPhone User Interface
iPhone User Interface solution extends ConceptDraw DIAGRAM software with templates, samples and libraries with large quantity of vector stencils of graphical user interface elements, Apps icons, UI patterns for designing and prototyping of the iOS applic
 Android User Interface
Android User Interface
The Android User Interface solution allows ConceptDraw DIAGRAM act as an Android UI design tool. Libraries and templates contain a variety of Android GUI elements to help users create images based on Android UI design.
Android GUI
Android is an operating system based on the Linux kernel and developed by Google for smartphones, tablet computers, electronic books, netbooks, smartbooks, digital players, watches, game consoles, TV and other devices. ConceptDraw DIAGRAM extended with Android User Interface Solution from the Software Development Area is a powerful software with extensive drawing tools which can help you to build the intelligible, attractive and easy for perception Android GUI for your application.
 Wireless Networks
Wireless Networks
The Wireless Networks Solution extends ConceptDraw DIAGRAM software with professional diagramming tools, set of wireless network diagram templates and samples, comprehensive library of wireless communications and WLAN objects to help network engineers and designers efficiently design and create Wireless network diagrams that illustrate wireless networks of any speed and complexity, and help to identify all required equipment for construction and updating wireless networks, and calculating their costs.
- Presentation Clipart | Business People Clipart | Arrows - Vector ...
- Arrows - Vector clipart library | Presentation design elements ...
- Arrows - Vector clipart library | Presentation Clipart | Illustration ...
- HR arrows - Vector stencils library | Sales arrows - Vector stencils ...
- Lightning Arrow
- Arrows - Vector clipart library | Presentation Clipart | Illustration | Clip ...
- Funnel Arrow Icon
- Arrows - Vector clipart library | Status indicators - Vector stencils ...
- Education pictograms - Vector stencils library | Education pictograms ...
- Education pictograms - Vector stencils library | Ribbon interface ...
- Lighting - Vector stencils library | Sales arrows - Vector stencils ...
- Ribbon interface - Vector stencils library | How to Build a Flowchart ...
- Arrows - Vector clipart library | Presentation design elements ...
- Arrows - Vector clipart library | Glyph icons - Vector stencils library ...
- Arrows - Vector clipart library | Sales arrows - Vector stencils library ...
- Computer and Internet use at home over time | Manufacturing in ...
- Vector stencils library - IDEF0 | Circular Arrows Diagrams | Basic ...
- How to Create a Custom Library | Presentation design elements ...
- Single Line Diagram Software For Android
- IVR mobile - Vector stencils library | Basic Flowchart Symbols and ...