"Problem-solving consists of using generic or ad hoc methods, in an orderly manner, for finding solutions to problems. Some of the problem-solving techniques developed and used in artificial intelligence, computer science, engineering, mathematics, medicine, etc. are related to mental problem-solving techniques studied in psychology." [Problem solving. Wikipedia]
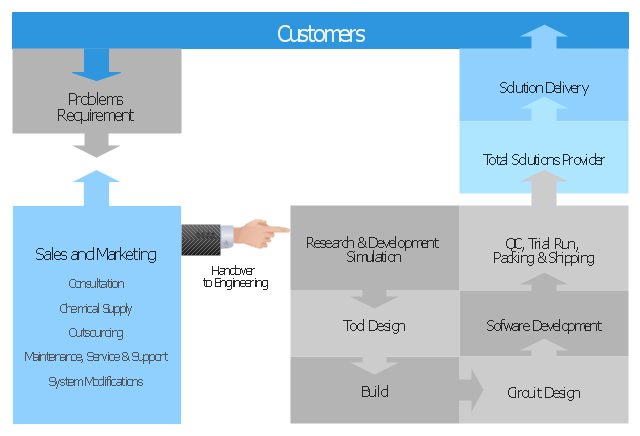
The block diagram example "Total solution process" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Block Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
The block diagram example "Total solution process" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Block Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
"Time management is the .. process of planning and exercising conscious control over the amount of time spent on specific activities, especially to increase effectiveness, efficiency or productivity. Time management may be aided by a range of skills, tools, and techniques used to manage time when accomplishing specific tasks, projects, and goals complying with a due date. Initially, time management referred to just business or work activities, but eventually the term broadened to include personal activities as well. A time management system is a designed combination of processes, tools, techniques, and methods. Time management is usually a necessity in any project development as it determines the project completion time and scope." [Time management. Wikipedia]
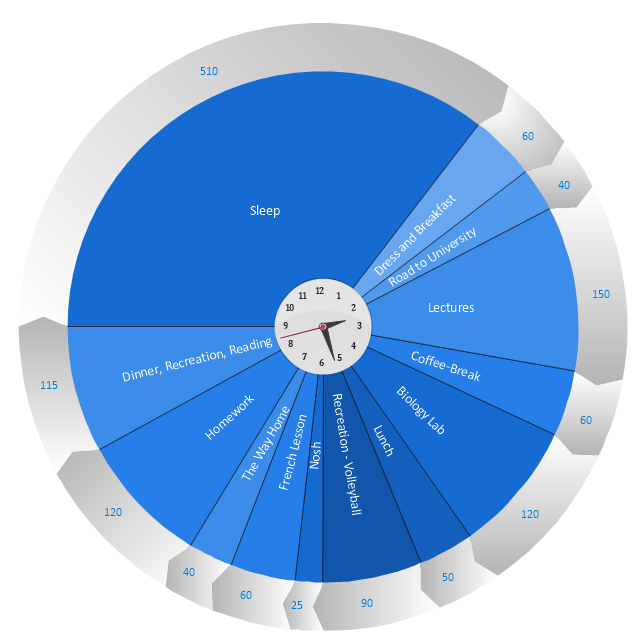
This timetable pie chart shows the plan of daily actions and its durations in minutes.
It is useful visual tool of personal time management.
This schedule pie chart example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Target and Circular Diagrams solution from the Marketing area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ marketing-target-and-circular-diagrams
This timetable pie chart shows the plan of daily actions and its durations in minutes.
It is useful visual tool of personal time management.
This schedule pie chart example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Target and Circular Diagrams solution from the Marketing area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ marketing-target-and-circular-diagrams
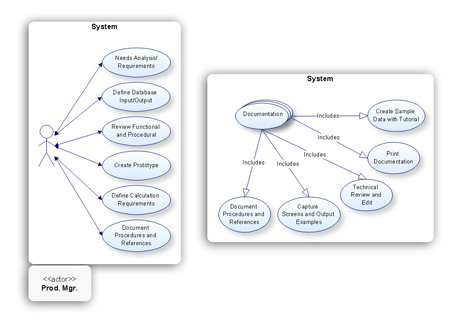
Software development with ConceptDraw Products
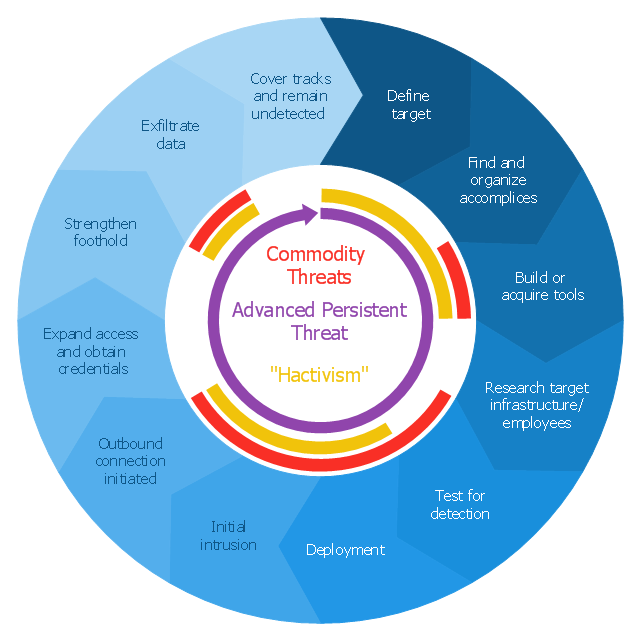
Internet solutions on ConceptDraw base. What may interest developers of Internet solutions.This circular arrows diagram sample shows advanced persistent threat lifecycle.
It was designed on the base of the Wikimedia Commons file: Advanced persistent threat lifecycle.jpg.
[commons.wikimedia.org/ wiki/ File:Advanced_ persistent_ threat_ lifecycle.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Advanced Persistent Threat (APT) APT is a set of stealthy and continuous hacking processes often orchestrated by human targeting a specific entity. APT usually targets organizations and or nations for business or political motives. APT processes require high degree of covertness over a long period of time. As the name implies, APT consists of three major components/ processes: advanced, persistent, and threat. The advanced process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The persistent process suggests that an external command and control is continuously monitoring and extracting data off a specific target. The threat process indicates human involvement in orchestrating the attack.
APT usually refers to a group, such as a government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack. Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target." [Advanced persistent threat. Wikipedia]
The arrow donut chart example
"Advanced persistent threat lifecycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
It was designed on the base of the Wikimedia Commons file: Advanced persistent threat lifecycle.jpg.
[commons.wikimedia.org/ wiki/ File:Advanced_ persistent_ threat_ lifecycle.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Advanced Persistent Threat (APT) APT is a set of stealthy and continuous hacking processes often orchestrated by human targeting a specific entity. APT usually targets organizations and or nations for business or political motives. APT processes require high degree of covertness over a long period of time. As the name implies, APT consists of three major components/ processes: advanced, persistent, and threat. The advanced process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The persistent process suggests that an external command and control is continuously monitoring and extracting data off a specific target. The threat process indicates human involvement in orchestrating the attack.
APT usually refers to a group, such as a government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack. Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target." [Advanced persistent threat. Wikipedia]
The arrow donut chart example
"Advanced persistent threat lifecycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
- Laboratory Apparatus For Separation Techniques
- Project Evaluation And Review Techniques Pert Mathematical
- Program Evaluation and Review Technique (PERT) with ...
- Program Evaluation and Review Technique (PERT) with ...
- Gravity filtration of liquids | What Is Separation Techniques In ...
- Soccer Techniques And Tactics Pdf
- Gravity filtration of liquids | Diagram Of Gravity Filtration Techniques
- Fire fighting and fire protection equipment | Illustration Techniques ...
- Competitive strategy matrix | Competitive Strategy Techniques For ...
- Lean Techniques
- Techniques Used In Structured System Analysis Diagram ...
- UML Business Process | UML Diagram | Rapid UML | Uml Techniques
- Networking Techniques
- Fault Tree Analysis Software | Hazard Analysis Techniques For ...
- Network Analysis Techniques Pert Cpm
- Flowchart Techniques
- Agile Techniques
- Scrum Techniques
- Example Of Collabration Techniques
- SSADM Diagram | UML Diagram | ConceptDraw Solution Park ...