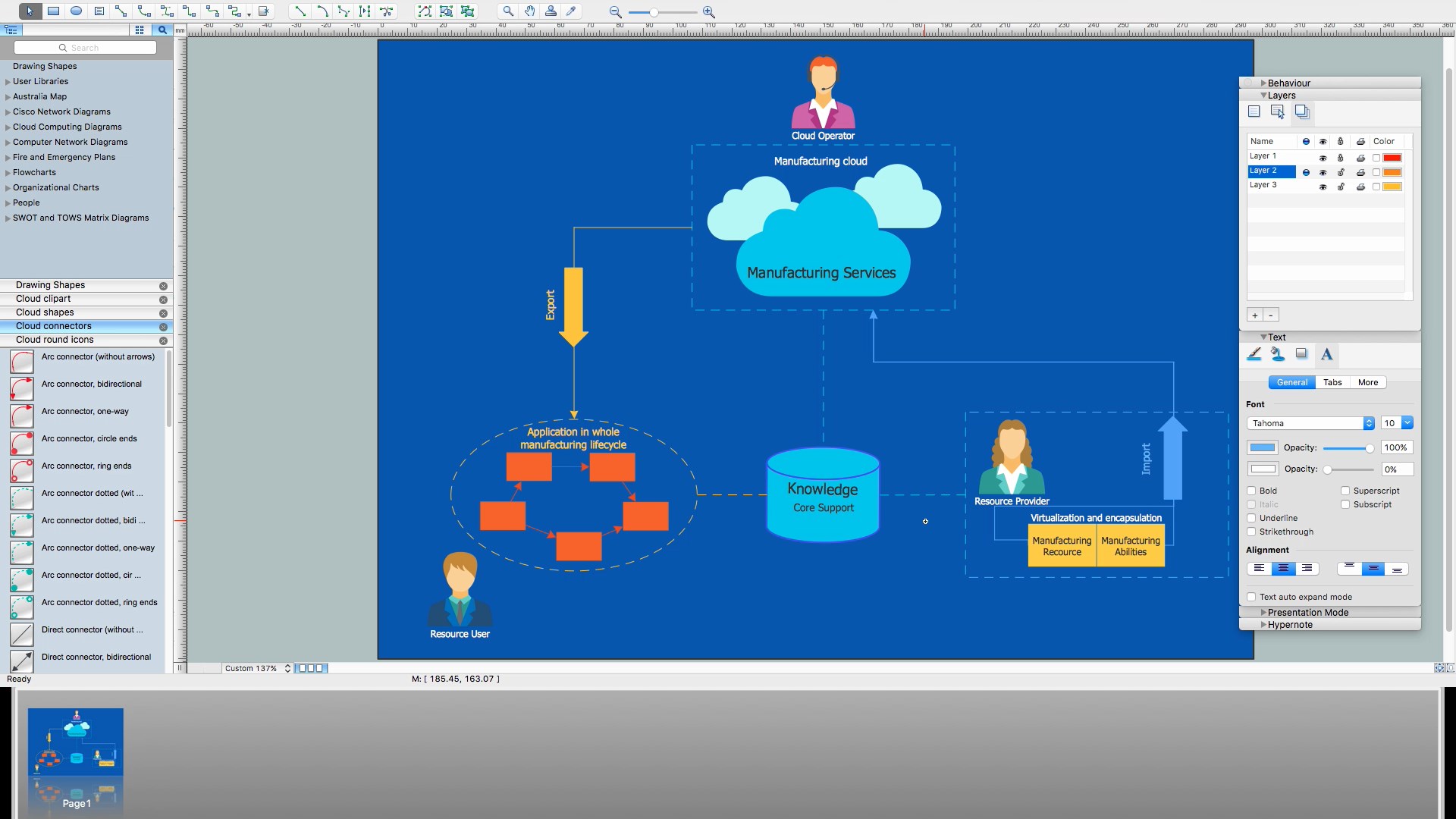
How to Build Cloud Computing Diagram Principal Cloud Manufacturing
The term “cloud” is very popular and widely used now, it is a server, data processing centre, or a network which lets to store the data and software, provides access to them, allows to run applications without installation and gives the possibility to process data hosted remotely via the Internet connection. For documenting the Cloud Computing Architecture with a goal to facilitate the communication between stakeholders are successfully used the Cloud Computing Architecture diagrams. It is convenient and easy to draw various Cloud Computing Architecture diagrams in ConceptDraw DIAGRAM software with help of tools of the Cloud Computing Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.This computer security diagram example was designed on the base of the diagram from the website of the Centers for Disease Control and Prevention (CDC).
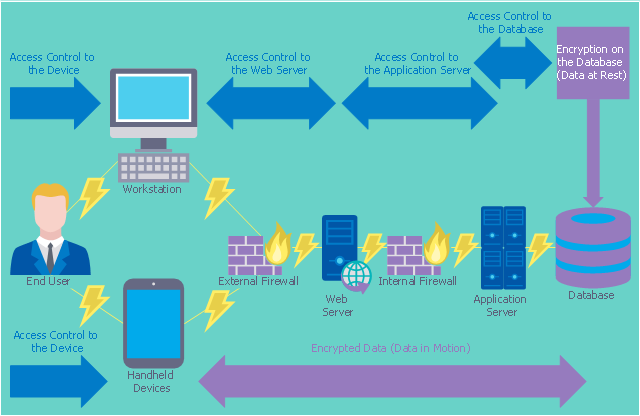
"Encryption and Cryptography
Encryption converts plain text into ciphertext, and decryption converts ciphertext back into plain text. Ciphertext looks like random characters, but is actually the result of the application of a key to the plain text. A key is usually a mathematical algorithm known only to the sender and the intended recipient of the message.
A cryptosystem is a system for encrypting and decrypting data. A strong cryptosystem has many possible keys, so a third party would be unlikely to find the correct key by trying all possible keys. A strong cryptosystem also produces ciphertext that appears random to all standard statistical tests and resists all known methods for breaking codes.
Access Control
Before implementing encryption, an organization needs to ensure access to the database is limited to authorized users. Access controls that should be addressed include rules for creating users, users’ privileges to access objects, and users’ permissions to perform commands and various tasks.
The following diagram illustrates how access control and encryption work together to secure data" [cdc.gov/ cancer/ npcr/ tools/ security/ encryption2.htm]
The cybersecurity diagram example "Access control and encryption " was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Encryption and Cryptography
Encryption converts plain text into ciphertext, and decryption converts ciphertext back into plain text. Ciphertext looks like random characters, but is actually the result of the application of a key to the plain text. A key is usually a mathematical algorithm known only to the sender and the intended recipient of the message.
A cryptosystem is a system for encrypting and decrypting data. A strong cryptosystem has many possible keys, so a third party would be unlikely to find the correct key by trying all possible keys. A strong cryptosystem also produces ciphertext that appears random to all standard statistical tests and resists all known methods for breaking codes.
Access Control
Before implementing encryption, an organization needs to ensure access to the database is limited to authorized users. Access controls that should be addressed include rules for creating users, users’ privileges to access objects, and users’ permissions to perform commands and various tasks.
The following diagram illustrates how access control and encryption work together to secure data" [cdc.gov/ cancer/ npcr/ tools/ security/ encryption2.htm]
The cybersecurity diagram example "Access control and encryption " was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
COM and OLE Diagram
The vector stencils library COM and OLE from the solution Software Engineering contains 15 symbols of the COM and OLE objects for ConceptDraw DIAGRAM diagramming and vector drawing software. The Software Engineering solution is contained in the Software Development area of ConceptDraw Solution Park.
 Mechanical Engineering
Mechanical Engineering
This solution extends ConceptDraw DIAGRAM.9 mechanical drawing software (or later) with samples of mechanical drawing symbols, templates and libraries of design elements, for help when drafting mechanical engineering drawings, or parts, assembly, pneumatic,
Network Security Devices
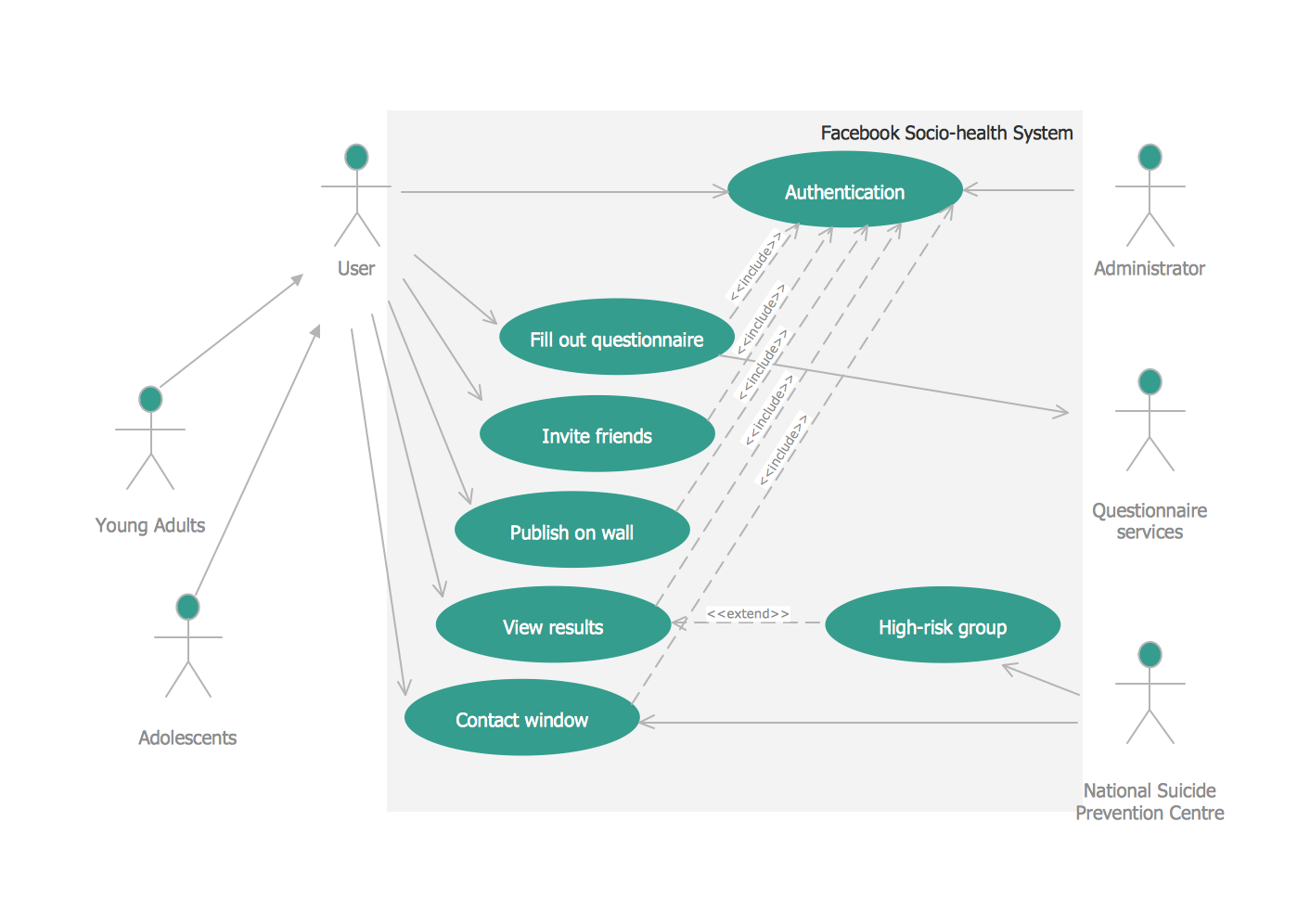
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.UML Use Case Diagram Example. Social Networking Sites Project
UML Diagrams Social Networking Sites Project. This sample was created in ConceptDraw DIAGRAM diagramming and vector drawing software using the UML Use Case Diagram library of the Rapid UML Solution from the Software Development area of ConceptDraw Solution Park. This sample shows the Facebook Socio-health system and is used at the projection and creating of the social networking sites.
 Rapid UML
Rapid UML
Rapid UML solution extends ConceptDraw DIAGRAM software with templates, samples and libraries of vector stencils for quick drawing the UML diagrams using Rapid Draw technology.
Network Glossary Definition
The network glossary contains a complete list of network, computer-related and technical terms in alphabetic order, explanations and definitions for them, among them there are words well known for you and also specific, rare-used, uncommon or newly introduced terms. This specialized glossary, also known as a vocabulary, is the best in its field and covers in details the various aspects of computer network technologies. This glossary was developed by specialists using the practical experience and many useful sources to help the ConceptDraw users in their work, you can read and learn it from the screen on-line or print, it can be also used as a perfect educational guide or tutorial. ConceptDraw DIAGRAM software extended with Computer and Networks solution is easy to draw various types of Network diagrams, Network topology diagrams, Computer networking schematics, Network maps, Cisco network topology, Computer network architecture, Wireless networks, Vehicular networks, Rack diagrams, Logical, Physical, Cable networks, etc. Desktop ConceptDraw DIAGRAM Software is a good Visio for Mac Os X replacement. It gives you rich productivity and quality of the produced diagrams.
- Cloud Computing Diagrams | Cloud Computing Architecture ...
- Cloud Computing Architecture Diagrams | Cloud Computing ...
- Cloud Computing Architecture Diagrams | How to Build Cloud ...
- Er Diagram Testing Automation Tool
- Process Flowchart | Work Flow Process Chart | Create Graphs and ...
- Amazon Cloud | Cloud Computing Architecture Diagrams | Cloud ...
- Workflow Testing
- ERD Symbols and Meanings | How to Create an ERD Diagram | ER ...
- Cloud Computing Architecture Diagrams | Amazon Cloud | UML Use ...
- Block diagram - Selling technology patent process | Process ...
- Technical Drawing Software | Process Flowchart | How To Create ...
- How to Create an ERD Diagram | EPC diagrams - Vector stencils ...
- Test Drawing Symbol
- Entity Relationship Diagram Software Engineering | Introduction to ...
- Entity-Relationship Diagram (ERD) | HR Management Software ...
- ER Diagram for Cloud Computing | Entity Relationship Diagrams ...
- Access Control Diagram
- Design elements - Meter indicators | IP Subnet mask calculator ...
- Diagram Of Cost Audit
- Access control and encryption | Network Security Model | Network ...