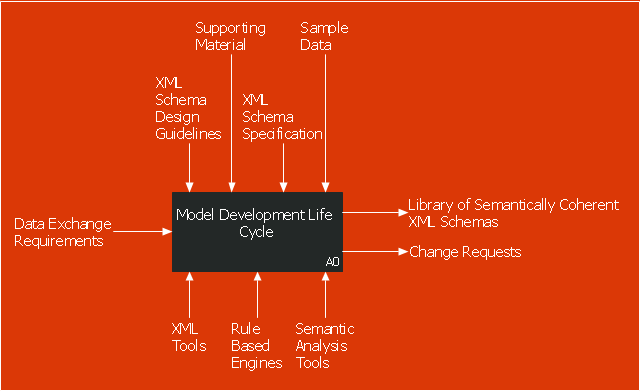
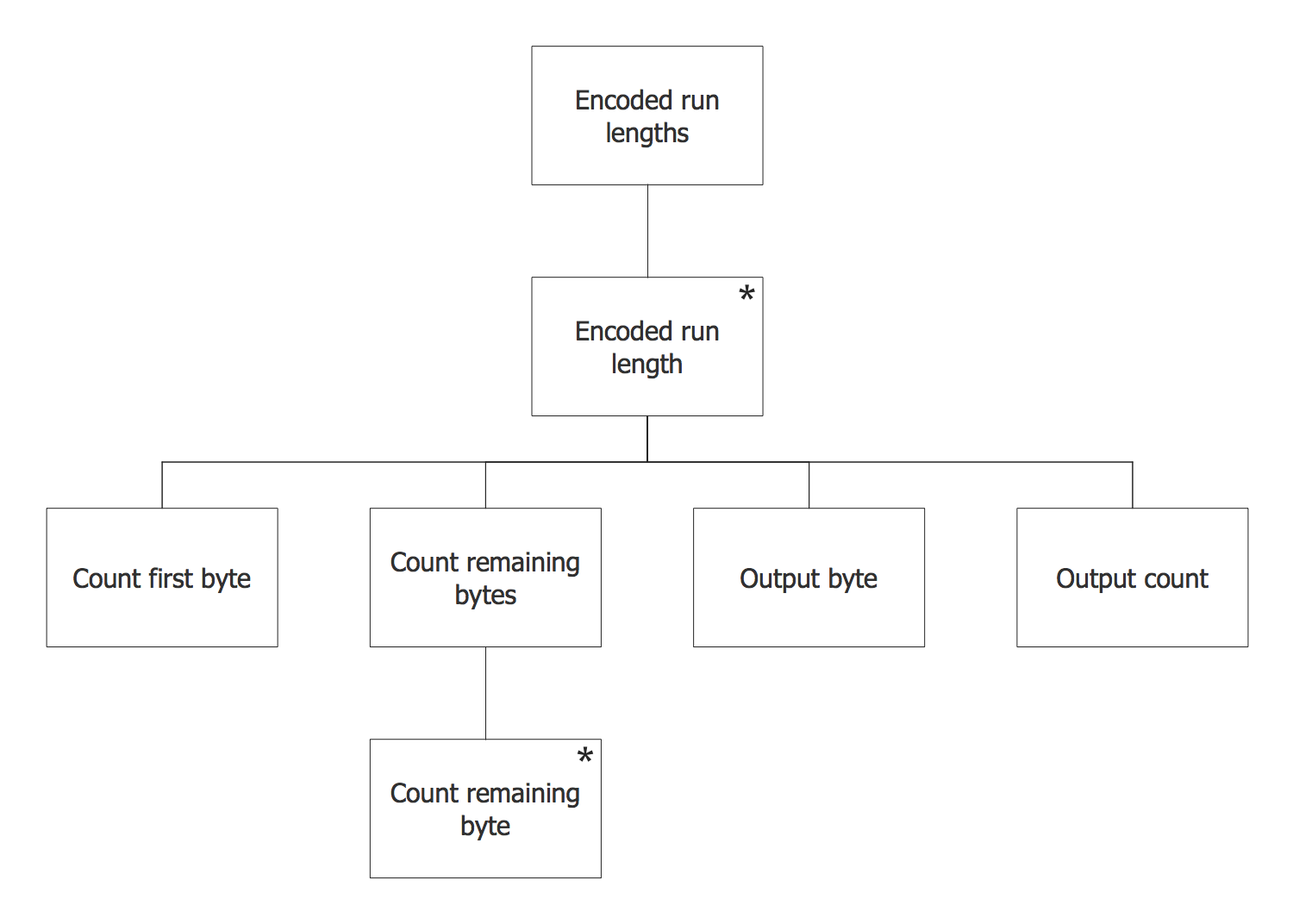
This IDEF0 diagram sample was created on the base of the figure from the website of the Engineering Laboratory of the National Institute of Standards and Technology (NIST). [mel.nist.gov/ msidlibrary/ doc/ kc_ morris/ gsa-final_ files/ image002.gif]
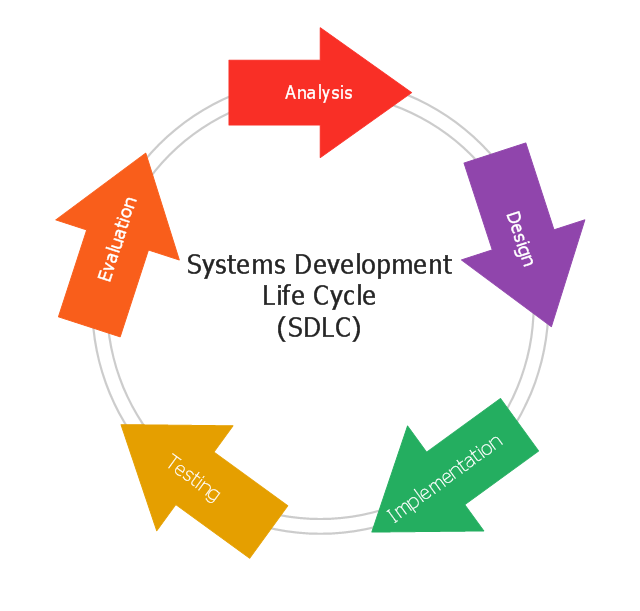
"The systems development life cycle (SDLC), also referred to as the application development life-cycle, is a term used in systems engineering, information systems and software engineering to describe a process for planning, creating, testing, and deploying an information system. The systems development life-cycle concept applies to a range of hardware and software configurations, as a system can be composed of hardware only, software only, or a combination of both." [Systems development life cycle. Wikipedia]
The IDEF0 diagram example "Model development life cycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the IDEF0 Diagrams solution from the Software Development area of ConceptDraw Solution Park.
"The systems development life cycle (SDLC), also referred to as the application development life-cycle, is a term used in systems engineering, information systems and software engineering to describe a process for planning, creating, testing, and deploying an information system. The systems development life-cycle concept applies to a range of hardware and software configurations, as a system can be composed of hardware only, software only, or a combination of both." [Systems development life cycle. Wikipedia]
The IDEF0 diagram example "Model development life cycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the IDEF0 Diagrams solution from the Software Development area of ConceptDraw Solution Park.
This circular arrows diagram sample shows the systems development life cycle (SDLC) stages.
"The systems development life cycle (SDLC), also referred to as the application development life-cycle, is a term used in systems engineering, information systems and software engineering to describe a process for planning, creating, testing, and deploying an information system. The systems development life-cycle concept applies to a range of hardware and software configurations, as a system can be composed of hardware only, software only, or a combination of both." [Systems development life-cycle. Wikipedia]
The arrow circle diagram example "Systems development life cycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
"The systems development life cycle (SDLC), also referred to as the application development life-cycle, is a term used in systems engineering, information systems and software engineering to describe a process for planning, creating, testing, and deploying an information system. The systems development life-cycle concept applies to a range of hardware and software configurations, as a system can be composed of hardware only, software only, or a combination of both." [Systems development life-cycle. Wikipedia]
The arrow circle diagram example "Systems development life cycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
Program to Make Flow Chart
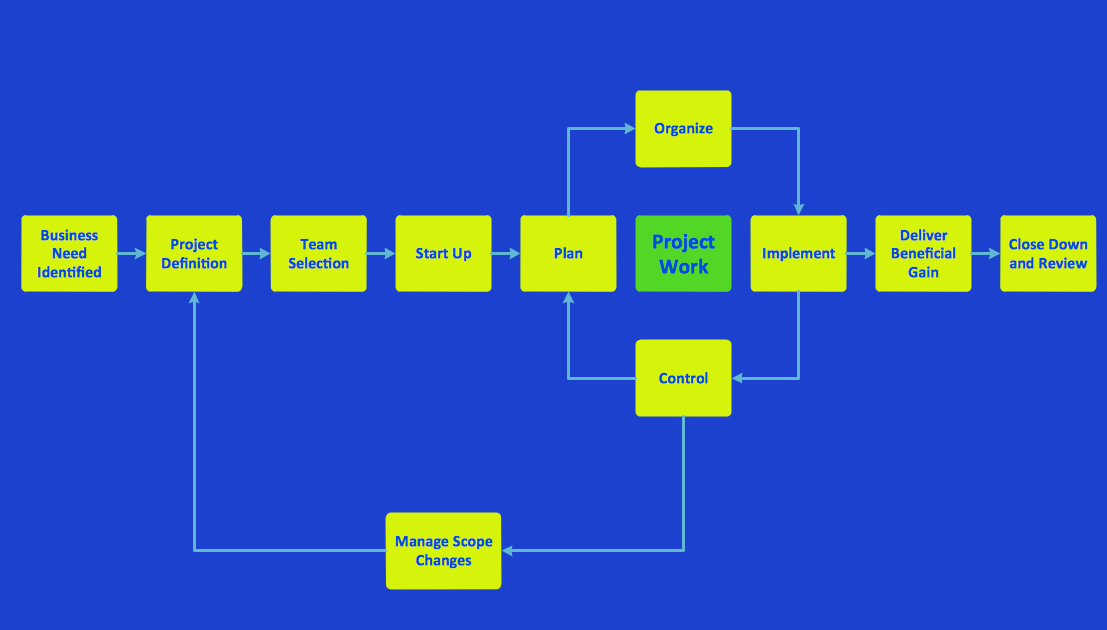
Use ConceptDraw PRO diagramming and business graphics software for drawing your own PM life cycle flow charts.Structured Systems Analysis and Design Method (SSADM) with ConceptDraw PRO
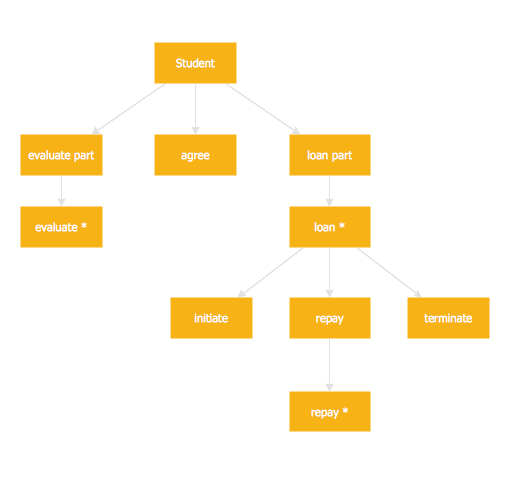
Structured Systems Analysis and Design Method (abbr. SSADM) is a method developed in Great Britain and accepted in 1993 as a national standard for information systems development and analysis. SSADM is based on Data Flow Diagrams and is characterized with presence of clear sequence of steps at projecting, analysis, and documenting of information system. It involves 6 main stages: analysis of existing system or estimation of practicability, requirements definition, determination of technical requirements and equipment cost, development of logical data model, projecting of logical requirements and specification them, physical projecting. Each of them is also divided into several steps defining the tasks that should be fulfilled at a given stage. The most important SSADM elements are flows modeling with help of DFD, data logic modeling with help of LDS (Logical Data Structure) and description of entities behavior. Applying of SSADM is easy with ConceptDraw PRO diagramming and vector drawing software and Data Flow Diagram solution.Data Flow Diagram
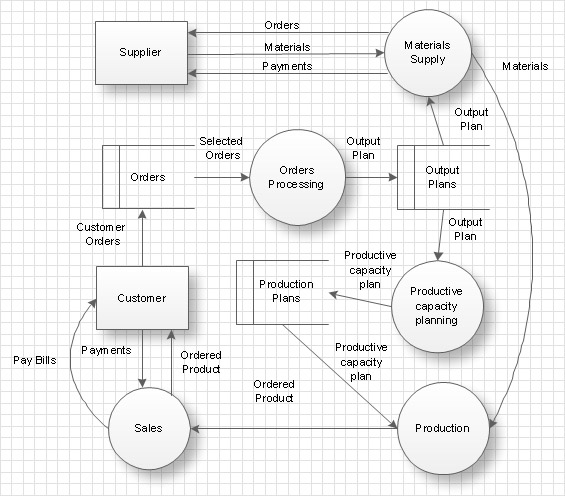
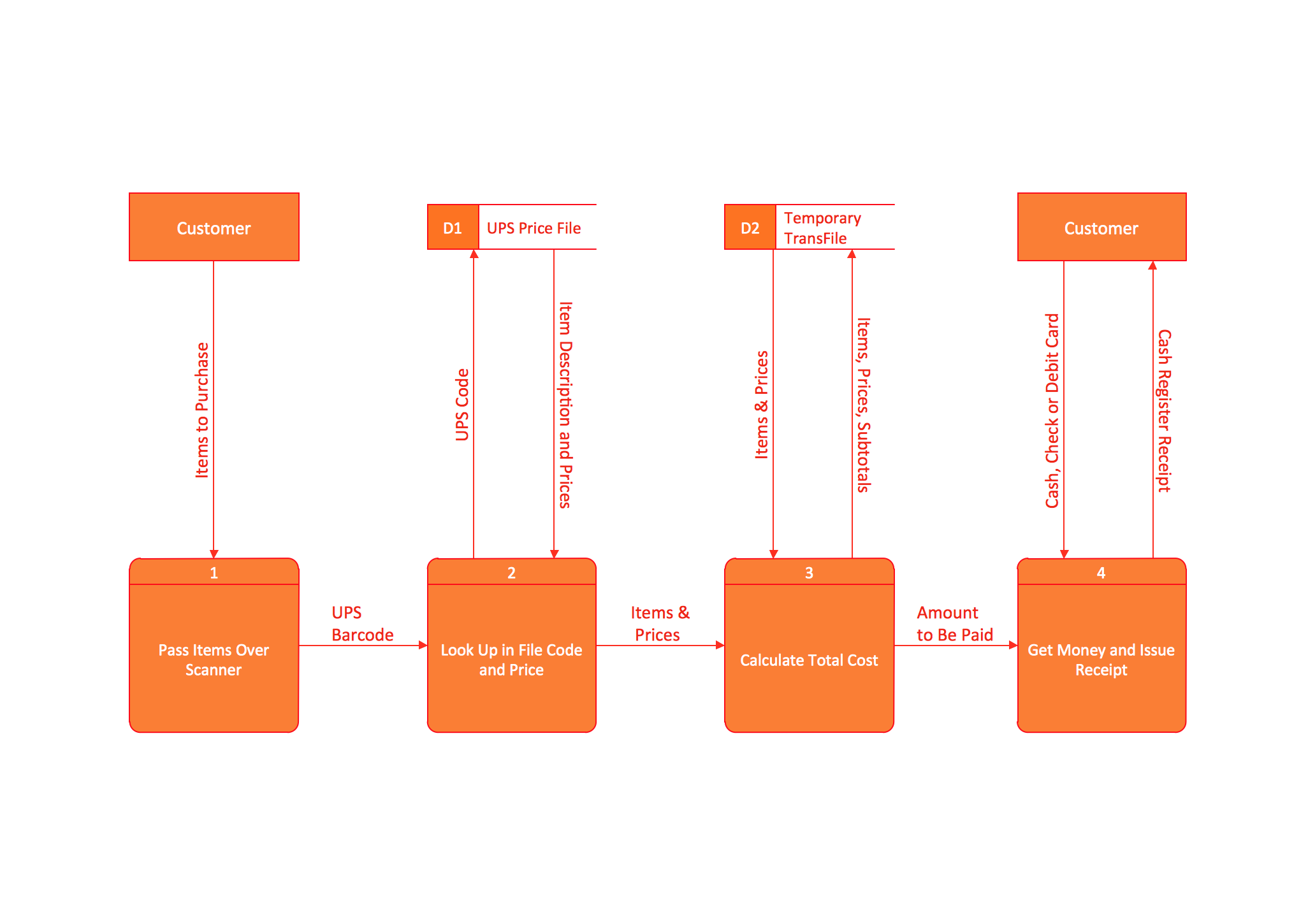
Data Flow Diagram (DFD) is the part of the Structured Systems Analysis and Design Methodology (SSADM), which is intended for information systems projection and analysis. Data Flow Diagrams allow graphically represent the data flows in information system and analyze the data processing during the structural projection. This type of diagrams lets visually show a work of information system and results of this work, it is often used in connection with human processes and can be displayed as Workflow diagram. Data Flow Diagram visualizes processes and functions, external entities, data depositories, and data flows connecting these elements and indicating direction and data character. Each of these elements used for DFD has its own graphical notation. There are two notations to draw DFDs - Yourdon & Coad and Gane & Sarson. ConceptDraw PRO extended with Data Flow Diagrams (DFD) solution from Software Developmant area is ideal for designing professional looking DFDs, which can be then easily exported in various formats.Jackson Systems
Entity structure diagram (ESD) notations may be created in the ConceptDraw PRO same as any other diagram, including a Jackson Structured Programming (JSP) Diagram. Having the Jackson Structured Programming (JSP) Diagrams solution may simplify the work of drawing the needed illustration representing the given data within only a few minutes. Having the pre-made examples of the JSP diagrams, any ConceptDraw PRO user is able to make his own unique as well as smart looking drawing in a fun and entertaining way.JSD - Jackson system development
Jackson System Development (JSD) is a linear method of system development created by Michael A. Jackson and John Cameron in the 1980s. It comprises the whole software life cycle directly or providing a framework for more specialized techniques. When implementing the Jackson System Development method and designing JSD diagrams, you can succesfully use the powerful and helpful tools of ConceptDraw PRO software extended with Entity-Relationship Diagram (ERD) solution from the Software Development area of ConceptDraw Solution Park.Total Quality Management Value
The Total quality management (TQM) is an enterprise-wide method of continuous quality improvement of all organizational processes, including the enhancement of ability to deliver high-quality products and services to the customers. The TQM includes eight main elements, which have great value: customer-focused, process-centered, total employee involvement, integrated system, continual improvement, strategic and systematic approach, fact-based decision making, communications. ConceptDraw PRO diagramming and vector drawing software offers the Total Quality Management Diagram solution with effective drawing tools, predesigned vector elements, samples and templates that help easy design the Total Quality Management diagrams, TQM flowcharts and Mind Maps widely used in quality management projects to visualize the business processes and industrial processes for your organization, to demonstrate the quality control step-by-step in a visual manner, to compare visually the ideal and real stages of processes.Data Flow Diagram (DFD)
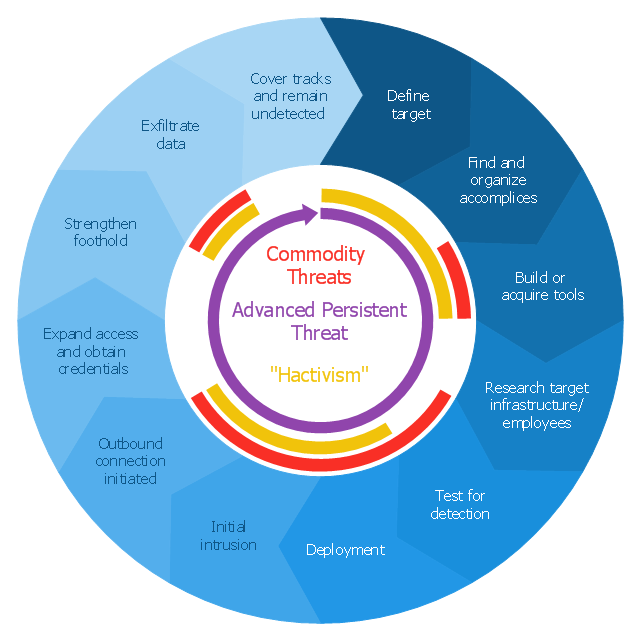
A Data Flow Diagram (DFD) illustrates the flow of data through an information system, visualizes how the information is handled in terms of inputs and outputs, how the data enter to system and leave it. It is effective to use a Data Flow Diagram for creation the system's overview, to show the system's scope and boundaries. There are two different types of notations for DFDs: Yourdon-Coad and Gane-Sarson, which differ in visual representations for processes, data flow, data stores, external entities, etc. Thus, for example the processes are depicted as circles in Yourdon-Coad notation and as rounded squares in Gane-Sarson notation. Gane-Sarson notation is usually used for visualization information systems and Yourdon-Coad - for system analysis and design. The Data Flow Diagrams solution included to Software Development area of ConceptDraw Solution Park offers a lot of DFD templates, samples and examples, libraries of vector stencils for construction without efforts the DFDs according to both Gane-Sarson and Yourdon-Coad notations.This circular arrows diagram sample shows advanced persistent threat lifecycle.
It was designed on the base of the Wikimedia Commons file: Advanced persistent threat lifecycle.jpg.
[commons.wikimedia.org/ wiki/ File:Advanced_ persistent_ threat_ lifecycle.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Advanced Persistent Threat (APT) APT is a set of stealthy and continuous hacking processes often orchestrated by human targeting a specific entity. APT usually targets organizations and or nations for business or political motives. APT processes require high degree of covertness over a long period of time. As the name implies, APT consists of three major components/ processes: advanced, persistent, and threat. The advanced process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The persistent process suggests that an external command and control is continuously monitoring and extracting data off a specific target. The threat process indicates human involvement in orchestrating the attack.
APT usually refers to a group, such as a government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack. Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target." [Advanced persistent threat. Wikipedia]
The arrow donut chart example
"Advanced persistent threat lifecycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
It was designed on the base of the Wikimedia Commons file: Advanced persistent threat lifecycle.jpg.
[commons.wikimedia.org/ wiki/ File:Advanced_ persistent_ threat_ lifecycle.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Advanced Persistent Threat (APT) APT is a set of stealthy and continuous hacking processes often orchestrated by human targeting a specific entity. APT usually targets organizations and or nations for business or political motives. APT processes require high degree of covertness over a long period of time. As the name implies, APT consists of three major components/ processes: advanced, persistent, and threat. The advanced process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The persistent process suggests that an external command and control is continuously monitoring and extracting data off a specific target. The threat process indicates human involvement in orchestrating the attack.
APT usually refers to a group, such as a government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack. Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target." [Advanced persistent threat. Wikipedia]
The arrow donut chart example
"Advanced persistent threat lifecycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
- Systems development life cycle | Circular Arrows Diagrams | Circular ...
- Draw A Sketch Of System Development Cycle
- Systems development life cycle | SSADM Diagram | Process ...
- BPM life cycle | Systems development life cycle | Innovation life cycle ...
- Systems development life cycle | Explain System Development ...
- Systems development life cycle | Circular Arrows Diagrams | Data ...
- Systems development life cycle | DFD - Process of account ...
- Product life cycle graph | Push Notification Lifecycle Overview ...
- Systems development life cycle | SSADM Diagram | Circular Flow ...