HelpDesk
How to Create a Network Security Diagram Using ConceptDraw PRO
Network security requires constant work and attention to details. Each user, whether an individual or organization, owns an information, considered to be valuable. The enforcement of network security, whether it be a local network security, or wireless network security is core for creating the secure environment of the daily working processes. Network security is accomplished through hardware and software. Network security system must be sophisticated and modern inside, but simple and understandable for the user. The visual scheme of security system can be presented in the form of a Network Security diagram. ConceptDraw PRO provides the toolkit for network security system visualization with its Network Security Diagram solution.IDEF3 Standard
Use Case Diagrams technology. IDEF3 Standard is intended for description and further analysis of technological processes of an enterprise. Using IDEF3 standard it is possible to examine and model scenarios of technological processes.IDEF1X Standard
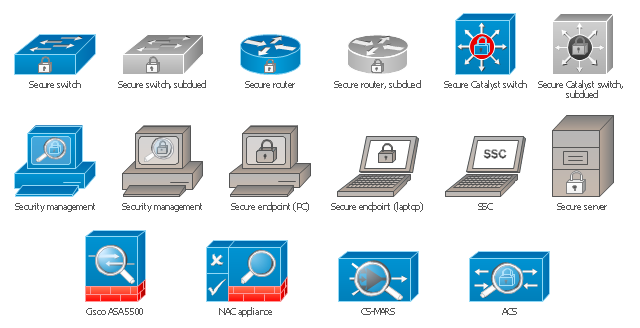
Use Case Diagrams technology. IDEF1x standard - for work with relational data bases. IDEF1x standard is meant for constructing of conceptual schemes which represent the structure of data in the context of the concerned system, for example, a commercial organization.The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
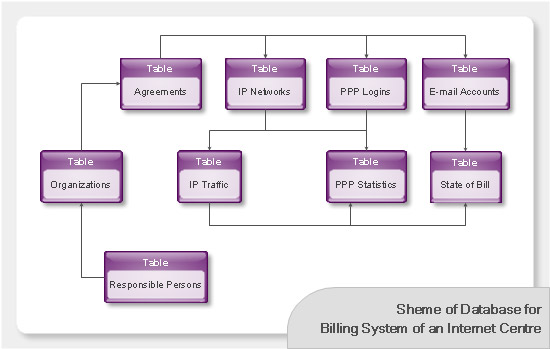
Databases Access Objects Model with ConceptDraw PRO
ConceptDraw Basic gives the opportunity of interaction with any ODBC-compatible databases. For this the Database Access Objects Model is provided. All calls to the database are made by certain methods of objects of this model.
 Event-driven Process Chain Diagrams
Event-driven Process Chain Diagrams
Event-driven Process Chain (EPC) Diagram is a type of flowchart widely used for modeling in business engineering and reengineering, business process improvement, and analysis. EPC method was developed within the Architecture of Integrated Information Systems (ARIS) framework.
GUI Prototyping with ConceptDraw PRO
All about prototyping. GUI Prototyping with ConceptDraw. Download prototyping software.
 Histograms
Histograms
How to make a Histogram? Making a Histogram is an incredibly easy process when it is done with ConceptDraw PRO. The Histograms Solution enhances ConceptDraw PRO v10 functionality with extensive drawing tools, numerous samples, and examples; also a quick-start template and library of ready vector stencils for visualization the data and professional drawing Histograms.
- How Many Types Of Computer And Their Diagram
- Basic Flowchart Symbols and Meaning | Computer Network ...
- Computer Network Diagrams | Bubble diagrams in Landscape ...
- Computer peripheral devices - Vector stencils library | Types of ...
- 2-bit ALU - Logic gate diagram | Computer network - Vector stencils ...
- Computer Networking Tools List | Computer Network Diagrams ...
- Computer Networking Tools List | Find out what amount and type of ...
- UML Diagram | Computer Network Diagrams | UML Diagrams with ...
- Basic Flowchart Symbols and Meaning | Process Flowchart | Types ...
- Types Of Router
- Computer Network Diagrams | Computer and Networks Area ...
- How To Convert a Computer Network Diagram to Adobe PDF Using ...
- How to Draw a Computer Network Diagrams | How to draw Metro ...
- How to Draw a Computer Network Diagrams | Workflow Diagram ...
- How To Add a Computer Network Diagram to a PowerPoint ...
- MS Visio Look a Like Diagrams | Cloud Computing Architecture ...
- Different Type Of Tools Their Diagram And Functions
- Process Flowchart | Types of Flowcharts | Basic Flowchart Symbols ...
- How to Draw a Computer Network Diagrams | Computer Network ...
- Computer Network Diagrams | Server hardware - Rack diagram ...






-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)