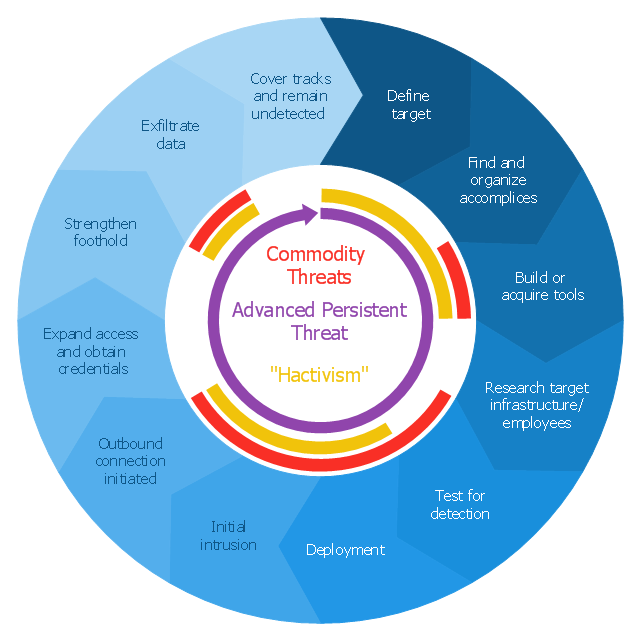
This circular arrows diagram sample shows advanced persistent threat lifecycle.
It was designed on the base of the Wikimedia Commons file: Advanced persistent threat lifecycle.jpg.
[commons.wikimedia.org/ wiki/ File:Advanced_ persistent_ threat_ lifecycle.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Advanced Persistent Threat (APT) APT is a set of stealthy and continuous hacking processes often orchestrated by human targeting a specific entity. APT usually targets organizations and or nations for business or political motives. APT processes require high degree of covertness over a long period of time. As the name implies, APT consists of three major components/ processes: advanced, persistent, and threat. The advanced process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The persistent process suggests that an external command and control is continuously monitoring and extracting data off a specific target. The threat process indicates human involvement in orchestrating the attack.
APT usually refers to a group, such as a government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack. Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target." [Advanced persistent threat. Wikipedia]
The arrow donut chart example
"Advanced persistent threat lifecycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
It was designed on the base of the Wikimedia Commons file: Advanced persistent threat lifecycle.jpg.
[commons.wikimedia.org/ wiki/ File:Advanced_ persistent_ threat_ lifecycle.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Advanced Persistent Threat (APT) APT is a set of stealthy and continuous hacking processes often orchestrated by human targeting a specific entity. APT usually targets organizations and or nations for business or political motives. APT processes require high degree of covertness over a long period of time. As the name implies, APT consists of three major components/ processes: advanced, persistent, and threat. The advanced process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The persistent process suggests that an external command and control is continuously monitoring and extracting data off a specific target. The threat process indicates human involvement in orchestrating the attack.
APT usually refers to a group, such as a government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack. Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target." [Advanced persistent threat. Wikipedia]
The arrow donut chart example
"Advanced persistent threat lifecycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
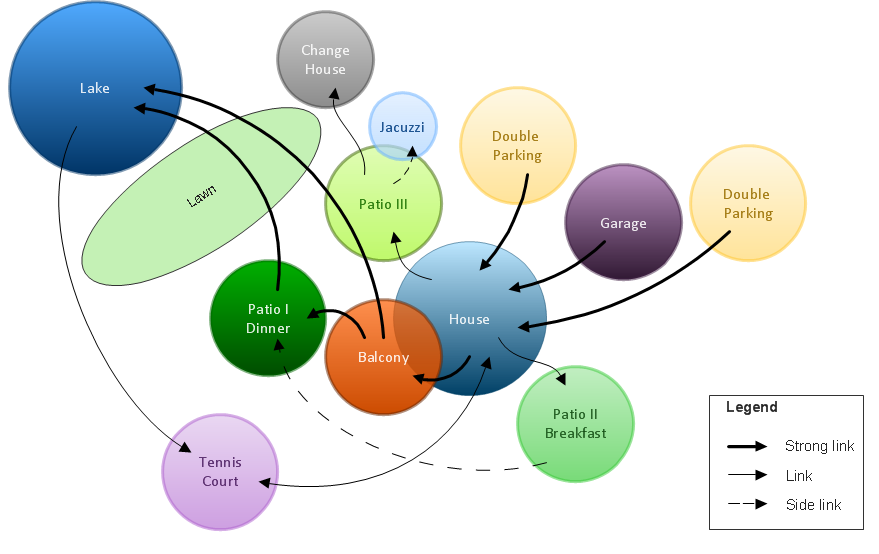
Bubble diagrams in Landscape Design with ConceptDraw DIAGRAM
Bubble Diagrams are the charts with a bubble presentation of data with obligatory consideration of bubble's sizes. They are analogs of Mind Maps and find their application at many fields, and even in landscape design. At this case the bubbles are applied to illustrate the arrangement of different areas of future landscape design, such as lawns, flowerbeds, playgrounds, pools, recreation areas, etc. Bubble Diagram helps to see instantly the whole project, it is easy for design and quite informative, in most cases it reflects all needed information. Often Bubble Diagram is used as a draft for the future landscape project, on the first stage of its design, and in case of approval of chosen design concept is created advanced detailed landscape plan with specification of plants and used materials. Creation of Bubble Diagrams for landscape in ConceptDraw DIAGRAM software is an easy task thanks to the Bubble Diagrams solution from "Diagrams" area. You can use the ready scanned location plan as the base or create it easy using the special ConceptDraw libraries and templates.HelpDesk
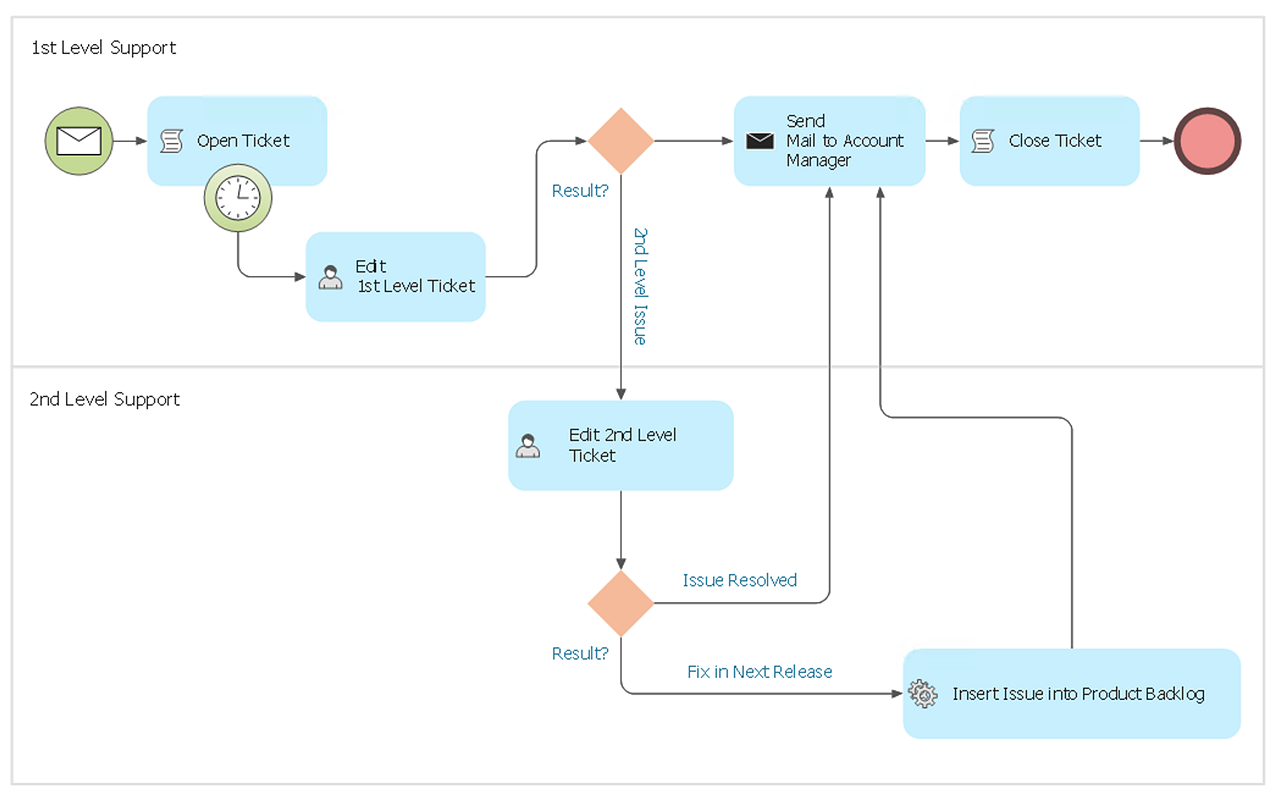
How to Create a BPMN Diagram
Business Process Modeling Notation (BPMN) is a method of illustrating business processes in the form of a diagram. The most effective method of creating or analyzing a business process is to visually interpret the steps using a business process diagram, flowchart or workflow. This is known as business process modeling and will be performed within a company by a team who have detailed knowledge of company process, and analysts with expertise in the modeling discipline. The objective is often to increase production or lower costs — by modeling the process initially using a flowchart, inefficiencies and problems can be spotted before committing to a decision or strategy. You can create BPMN diagrams using the ConceptDraw DIAGRAM diagramming tools. ConceptDraw has designed a solution that combines BPMN v2.0 methodology and graphical notification into one powerful package. The Business Process Diagrams solution from ConceptDraw Solution Park provides a comprehensive collection of vectorHelpDesk
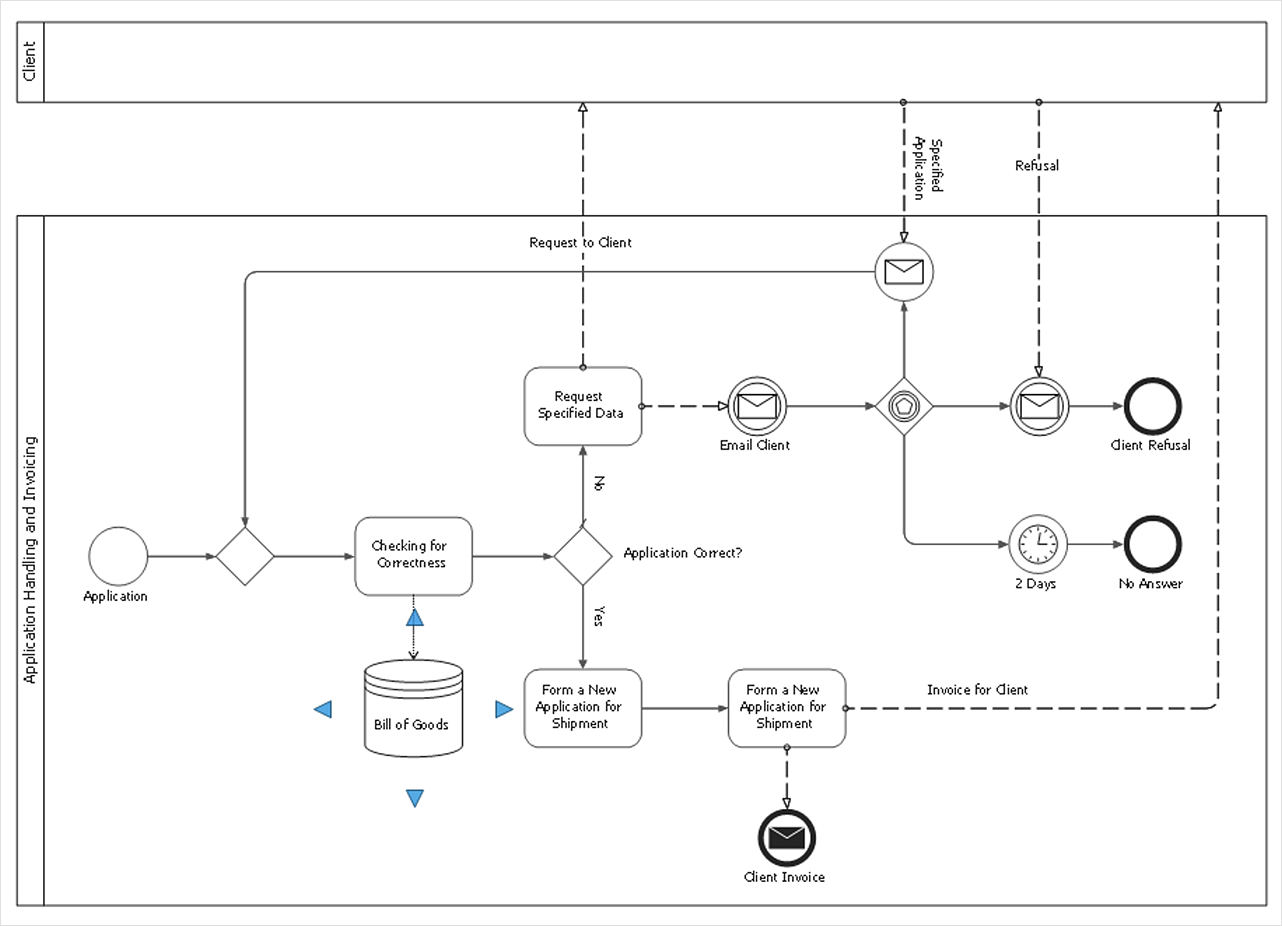
How to Develop a Business Process Model
Making a Business Process diagram involves many different elements that can be managed using ConceptDraw DIAGRAM. The ability to design Business Process diagrams is delivered by the Business Process Diagrams solution.- Strategic planning - Cycle diagram | Strategic planning cycle - Arrow ...
- Successful Strategic Plan | Strategic planning - Cycle diagram ...
- Strategic planning - Cycle diagram | Successful Strategic Plan ...
- Active Directory Diagram | Active Directory Domain Services ...
- PROBLEM ANALYSIS. Root Cause Analysis Tree Diagram | Fault ...
- Active Directory Diagram
- Basic Flowchart Symbols and Meaning | Audit Flowchart Symbols ...
- Strategic planning - Cycle diagram | Strategic planning cycle - Arrow ...
- Active Directory Domain Services | Design Element: Active Directory ...
- Design Element: Active Directory for Network Diagrams | Active ...
- Elements location of a welding symbol | Location of the Migration ...
- How to Draw a Circular Arrows Diagram Using ConceptDraw PRO ...
- Block diagram - Types of individual behavior in organization | Basic ...
- Successful Strategic Plan | Strategic planning - Cycle diagram ...
- Basic Flowchart Symbols and Meaning | IDEF0 diagram - Inter-box ...
- Active Directory Diagram | Tree and Forest (Full Trust) - Active ...
- Product life cycle process - Flowchart | BPM life cycle | Innovation life ...
- Area chart template
- Strategic planning - Cycle diagram | Organizational Structure ...
- Draw Flowcharts with ConceptDraw | Circular Arrows Diagrams ...