Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution enhances the ConceptDraw PRO v10 functionality with large collection of predesigned vector stencils of cybersecurity clipart, shapes, icons and connectors to help you succeed in designing professional and accurate Ne
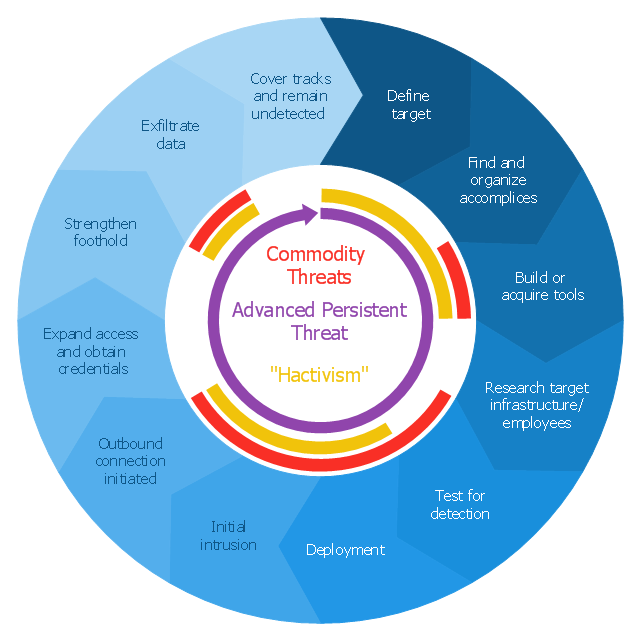
"Advanced Persistent Threat (APT) APT is a set of stealthy and continuous hacking processes often orchestrated by human targeting a specific entity. APT usually targets organizations and or nations for business or political motives. APT processes require high degree of covertness over a long period of time. As the name implies, APT consists of three major components/ processes: advanced, persistent, and threat. The advanced process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The persistent process suggests that an external command and control is continuously monitoring and extracting data off a specific target. The threat process indicates human involvement in orchestrating the attack.
APT usually refers to a group, such as a government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack. Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target." [Advanced persistent threat. Wikipedia]
This circular arrows diagram example was redesigned from the Wikimedia Commons file: Advanced persistent threat lifecycle.jpg.
[commons.wikimedia.org/ wiki/ File:Advanced_ persistent_ threat_ lifecycle.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
The example "Advanced persistent threat lifecycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
APT usually refers to a group, such as a government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack. Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target." [Advanced persistent threat. Wikipedia]
This circular arrows diagram example was redesigned from the Wikimedia Commons file: Advanced persistent threat lifecycle.jpg.
[commons.wikimedia.org/ wiki/ File:Advanced_ persistent_ threat_ lifecycle.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
The example "Advanced persistent threat lifecycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
 ConceptDraw Solution Park
ConceptDraw Solution Park
ConceptDraw Solution Park collects graphic extensions, examples and learning materials
 Computer and Networks Area
Computer and Networks Area
The solutions from Computer and Networks Area of ConceptDraw Solution Park collect samples, templates and vector stencils libraries for drawing computer and network diagrams, schemes and technical drawings.
HelpDesk
How to Convert a Mind Map into MS Word Document
Mind maps are often used for structuring ideas, planning and organizing of various documents. ConceptDraw MINDMAP allows you transfer a mind map to MS Word format using its export facilities. You can convert a mind map to a MS Word outline using the set of standard templates, or even your custom template. Thus, your mind map will be transformed into the proper document format. Using a custom MS Word template allows you apply your individual style to each document, being exported from ConceptDraw MINDMAP. You can use a mind mapping to capture ideas and structure information. Then making a quick conversion to MS Word and you finally obtain a clean and stylish document.Secure Wireless Network
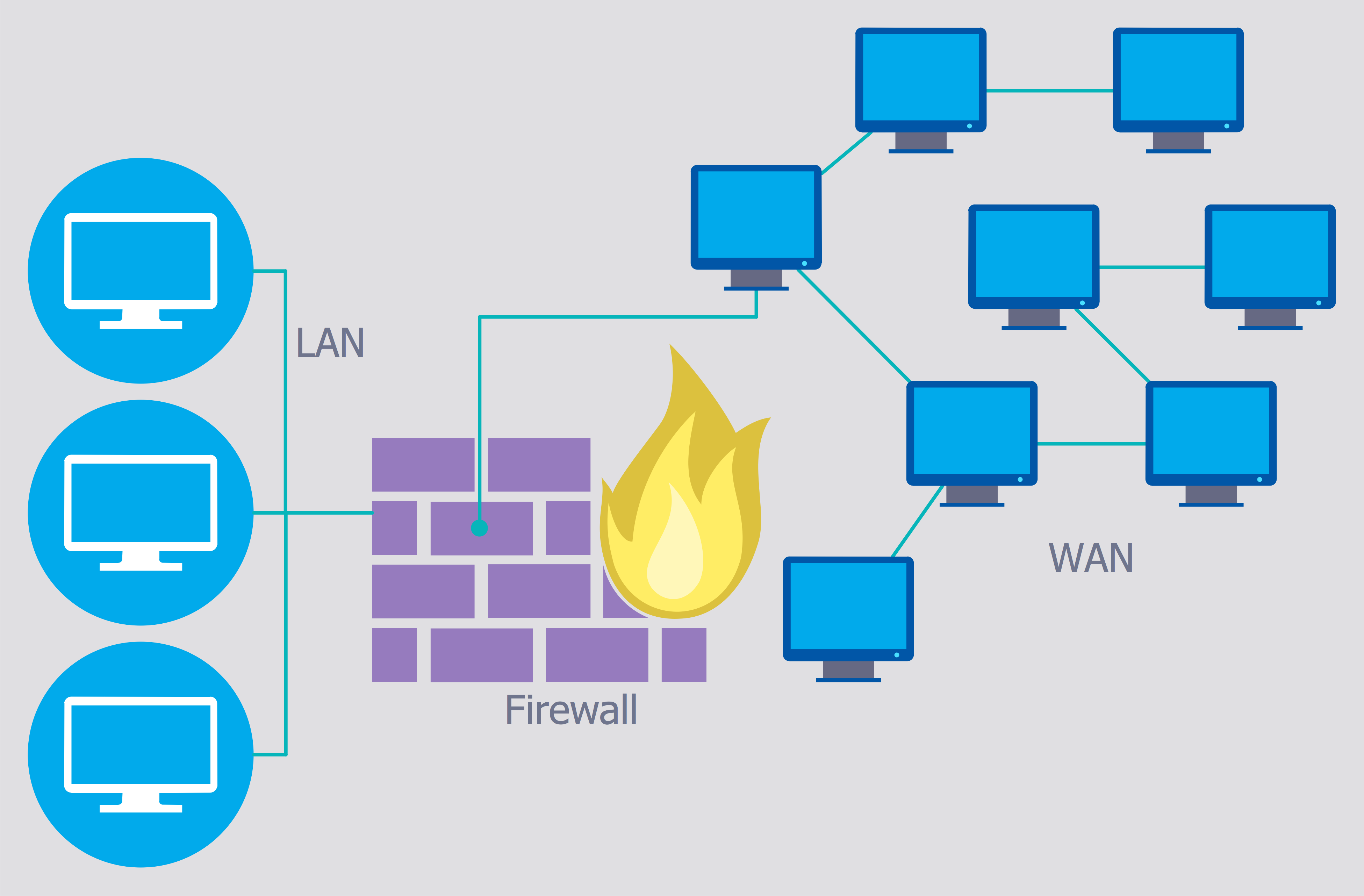
Use the ConceptDraw PRO diagramming and vector drawing software enhanced with powerful tools of Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park to effectively visualize the importance of network security and wireless network security, and ways to ensure them, to easily design Network Security Diagrams and Maps, Network Security Model, Secure Wireless Network and Network Security Architecture diagrams.- Cyber Security Degrees | 10 Steps to Cyber Security | Network ...
- 10 Steps to Cyber Security | Network Security Diagrams | Network ...
- Design elements - Cybersecurity round icons | Cyber Security ...
- How to Create a Network Security Diagram Using ConceptDraw PRO
- Erd Dfd Examples For Cyber Cafe
- How to Create a Network Security Diagram Using ConceptDraw ...
- Fork bomb | IT Security Solutions | Network Security Diagrams ...
- Recommended network architecture for BlackBerry SWS | Network ...
- Network Glossary Definition | Network diagrams with ConceptDraw ...
- How To Draw A Floor Plan Of Cyber Cafe
- Network Security Model | Network Security | Secure Wireless ...
- Hardware And Networking In Diagrams Format Pdf
- Network Security Diagrams | AWS Architecture Diagrams | iPhone ...
- Advanced persistent threat lifecycle | Creatively Draw A Diagram ...
- Physical Security Plan | Security and Access Plans | Gym and Spa ...
- Organizational Charts | ConceptDraw Solution Park | 25 Typical ...
- Why Is The System Life Cycle A Circular Process
- Cisco Network Diagrams | Storage area networks (SAN). Computer ...
- Event-driven Process Chain Diagrams EPC | Value stream map
- Security and Access Plans | How to Draw a Security and Access ...