Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw PRO software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
Network Security Model
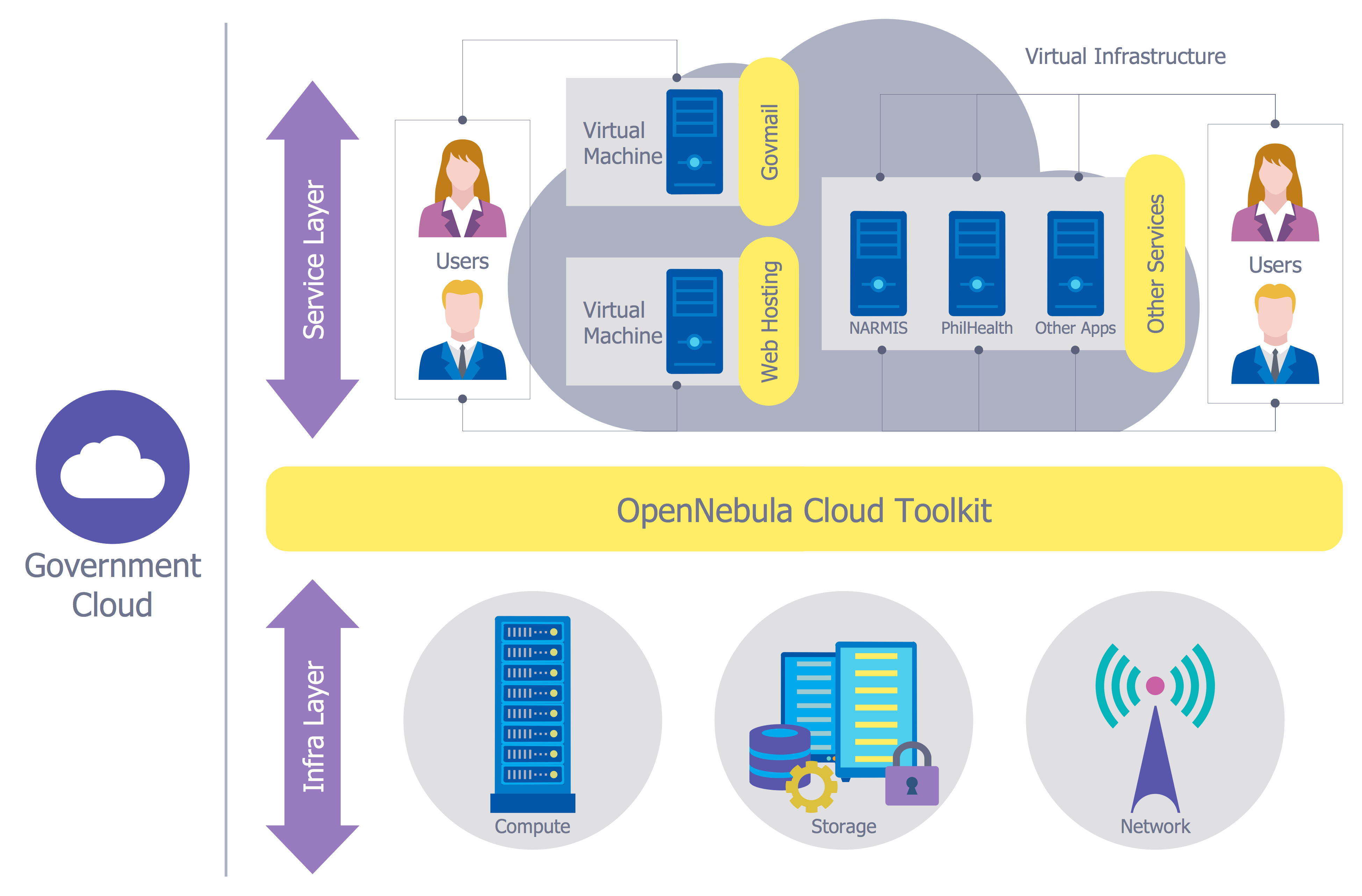
Creation of well thought-out network security model will effectively help you in realization your network's security. ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park lets fast and easy design all variety of network security models: Open network security model, Closed network security model, Restrictive network access model.IT Security Solutions
Dynamic of development computer and network technologies increases the need in modern cyber security strategies and IT security solutions to support security of your data, to ensure data privacy, and to protect your operations from the cyber threats. Thanks to the Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park, the ConceptDraw PRO diagramming and vector drawing software is one of the unique IT security solutions for professional designing Network Security Diagrams.Network Security
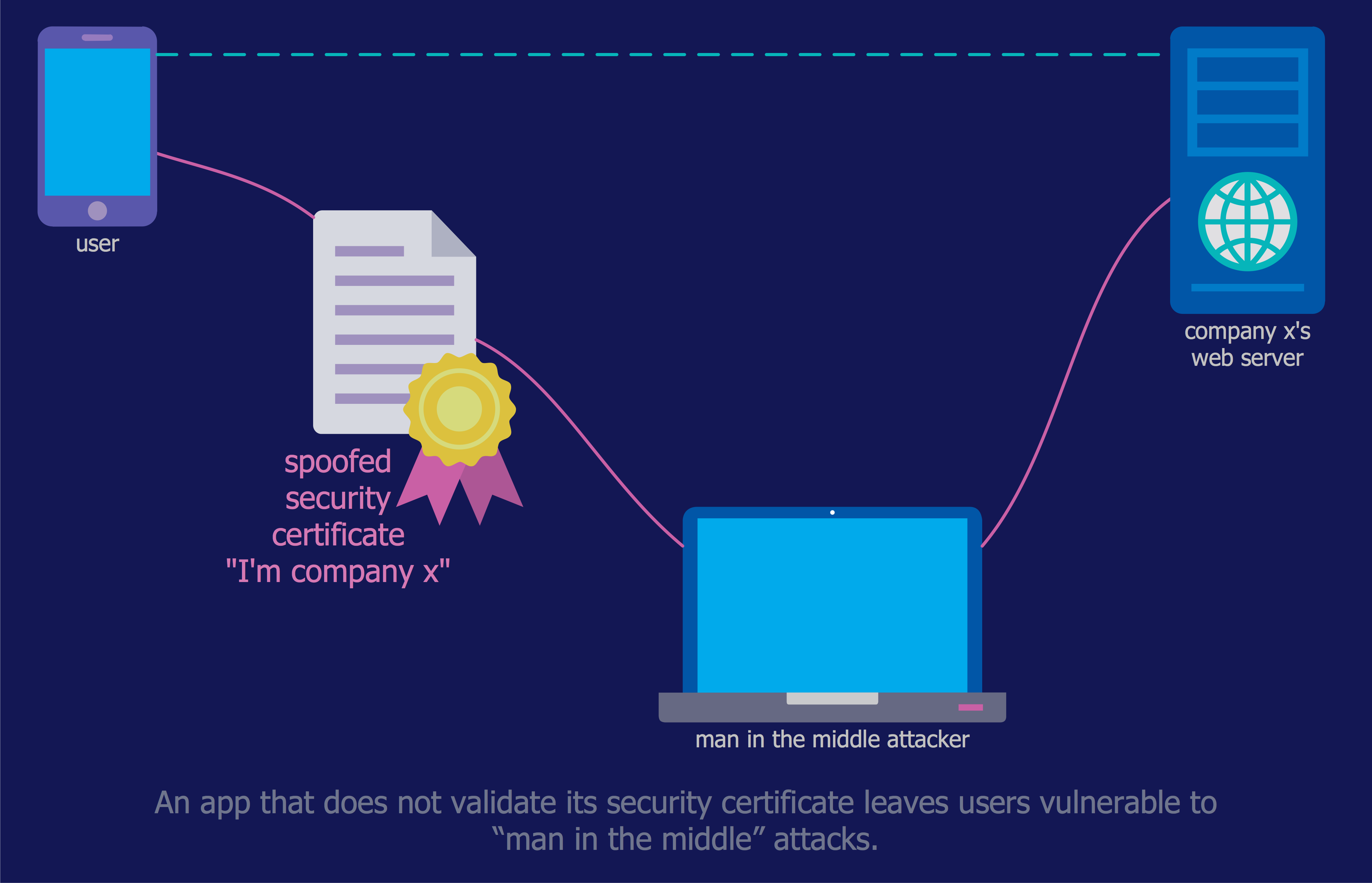
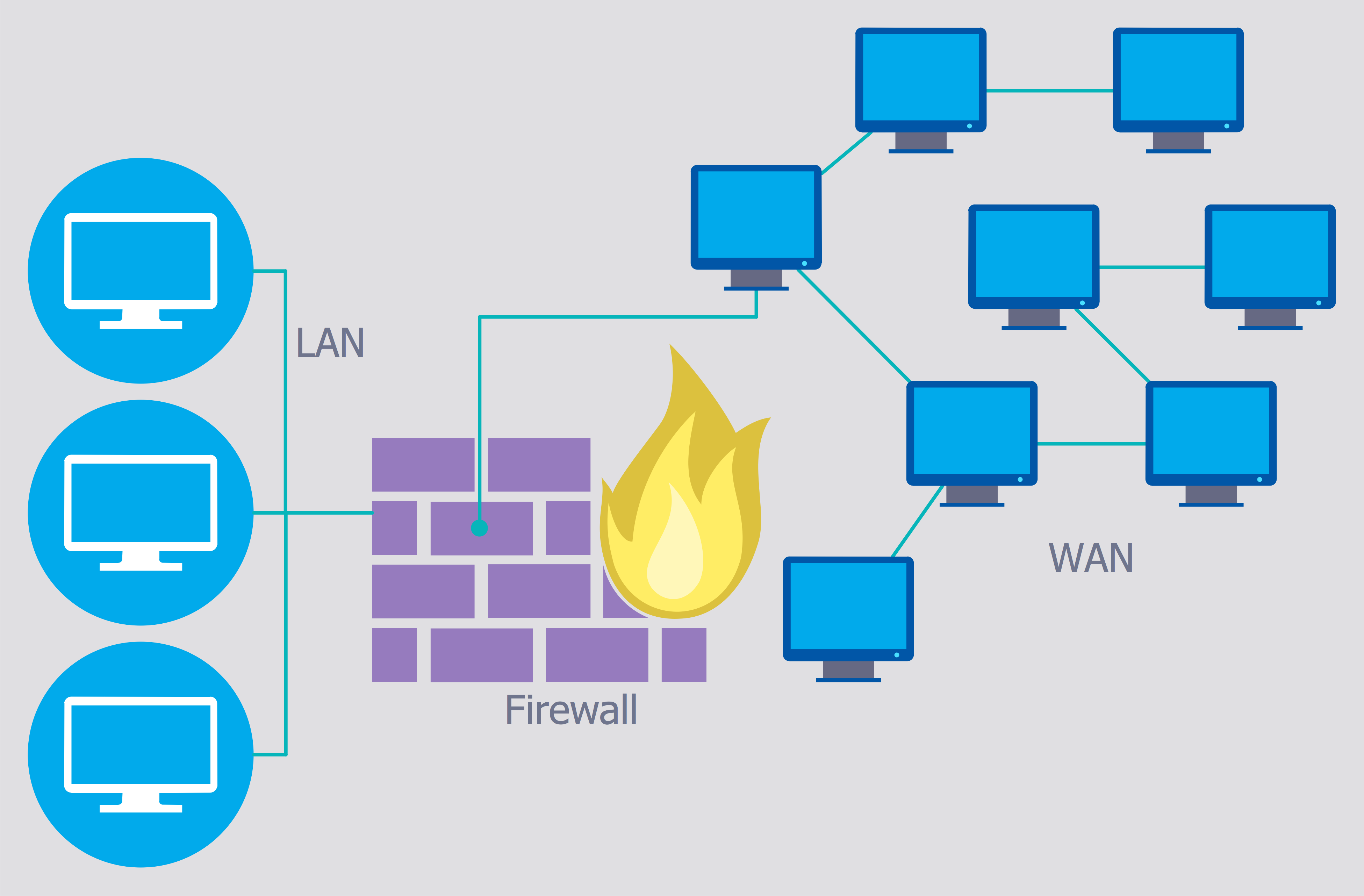
The Internet is a giant computer network which connects computers all over the world. It is integral part of human society and business. But the serious question for network engineers, designers, lawmakers and enforcers is the need for protect the Internet networks from the Internet crimes, hacking and attacks. There are quite a number of hardware, software and physical methods of protection against them. The samples you see on this page were created in ConceptDraw PRO using the tools of Network Security Diagrams Solution for ConceptDraw PRO software. They show protection networks with Firewalls and other network security devices.DES Network. Computer and Network Examples
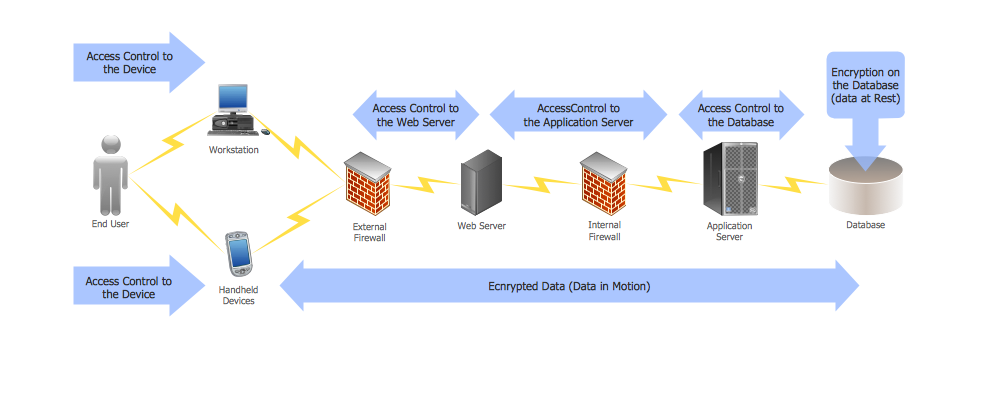
29095The Data Encryption Standard (DES) is a symmetric-key algorithm for the encryption of the electronic data. This diagram was created in ConceptDraw PRO using the Computer and Networks Area of ConceptDraw Solution Park and shows how the encryption and access control work together to secure data.
The vector stencils library "AWS Security, Identity and Compliance" contains 23 Amazon Web Services security, identity and compliance icons.
Use it to draw AWS architecture diagrams with ConceptDraw PRO software.
Amazon Security, Identity and Compliance services includes: "Amazon Cloud Directory (Create flexible cloud-native directories), AWS Identity & Access Management (Manage User Access and Encryption Keys), Amazon Inspector (Analyze Application Security), AWS Certificate Manager (Provision, Manage, and Deploy SSL/ TLS Certificates), AWS CloudHSM (Hardware-based Key Storage for Regulatory Compliance), AWS Directory Service (Host and Manage Active Directory), AWS Key Management Service (Managed Creation and Control of Encryption Keys), AWS Organizations (Policy-based management for multiple AWS accounts), AWS Shield (DDoS Protection), AWS WAF (Filter Malicious Web Traffic)" [aws.amazon.com]
The AWS icons example "Design elements - AWS Security, Identity and Compliance" is included in the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to draw AWS architecture diagrams with ConceptDraw PRO software.
Amazon Security, Identity and Compliance services includes: "Amazon Cloud Directory (Create flexible cloud-native directories), AWS Identity & Access Management (Manage User Access and Encryption Keys), Amazon Inspector (Analyze Application Security), AWS Certificate Manager (Provision, Manage, and Deploy SSL/ TLS Certificates), AWS CloudHSM (Hardware-based Key Storage for Regulatory Compliance), AWS Directory Service (Host and Manage Active Directory), AWS Key Management Service (Managed Creation and Control of Encryption Keys), AWS Organizations (Policy-based management for multiple AWS accounts), AWS Shield (DDoS Protection), AWS WAF (Filter Malicious Web Traffic)" [aws.amazon.com]
The AWS icons example "Design elements - AWS Security, Identity and Compliance" is included in the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.
 Active Directory Diagrams
Active Directory Diagrams
Active Directory Diagrams solution extends ConceptDraw PRO software with samples, templates and libraries of vector stencils for drawing the AD diagrams to visualize the detail structures of the Microsoft Windows networks.
Using Remote Networking Diagrams
Remote Networking - We explain the method most people use to connect to the Internet.
Virtual private networks (VPN). Computer and Network Examples
A Virtual Private Network (VPN) is a network that allows the private networks at a remote location securely connect to the public Internet and provide access only to the intended recipients for transmitting data. VPN is built by creating the virtual point-to-point connection using the dedicated connections, traffic encryption or virtual tunneling protocols. This example was created in ConceptDraw PRO using the Computer and Networks Area of ConceptDraw Solution Park and shows the Virtual Private Network (VPN) diagram.
Cyber Security Degrees
For protection various cyber environments are developed and applied large variety of cyber security standards, techniques, security concepts and approaches with different cyber security degrees. The ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park offers the number of useful tools which will help network security engineers, cyber security specialists, network and computer analysts easily and visually depict the knowledge and skills for research and prevention of intrusions, about protection critical information and analysis of cyber incidents, and for how to assess threats and vulnerabilities.Cisco Products Additional. Cisco icons, shapes, stencils and symbols
The ConceptDraw vector stencils library Cisco Products Additional contains equipment symbols for drawing the computer network diagrams.This vector stencils library contains 184 round icons.
Use it to design cloud computing infographics and diagrams with ConceptDraw PRO software.
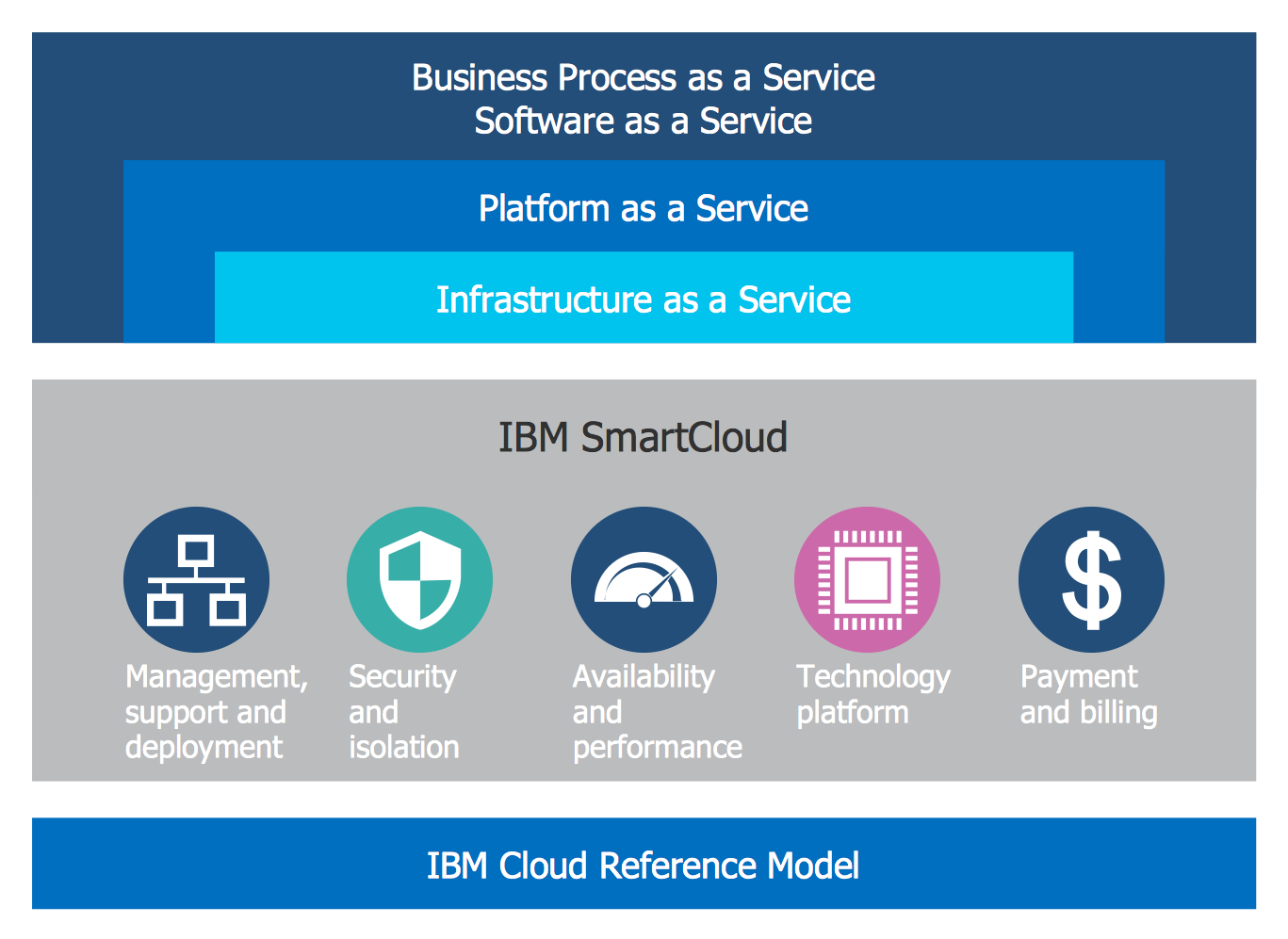
"Though service-oriented architecture advocates "everything as a service" (with the acronyms EaaS or XaaS or simply aas), cloud-computing providers offer their "services" according to different models, which happen to form a stack: infrastructure-, platform- and software-as-a-service.
Infrastructure as a service (IaaS)
In the most basic cloud-service model ... providers of IaaS offer computers — physical or (more often) virtual machines — and other resources. IaaS refers to online services that abstract the user from the details of infrastructure like physical computing resources, location, data partitioning, scaling, security, backup etc.
Platform as a service (PaaS)
PaaS vendors offer a development environment to application developers. The provider typically develops toolkit and standards for development and channels for distribution and payment. In the PaaS models, cloud providers deliver a computing platform, typically including operating system, programming-language execution environment, database, and web server. Application developers can develop and run their software solutions on a cloud platform without the cost and complexity of buying and managing the underlying hardware and software layers.
Software as a service (SaaS)
In the software as a service (SaaS) model, users gain access to application software and databases. Cloud providers manage the infrastructure and platforms that run the applications. SaaS is sometimes referred to as "on-demand software" and is usually priced on a pay-per-use basis or using a subscription fee.
In the SaaS model, cloud providers install and operate application software in the cloud and cloud users access the software from cloud clients. Cloud users do not manage the cloud infrastructure and platform where the application runs. This eliminates the need to install and run the application on the cloud user's own computers, which simplifies maintenance and support. Cloud applications differ from other applications in their scalability — which can be achieved by cloning tasks onto multiple virtual machines at run-time to meet changing work demand." [Cloud computing. Wikipedia]
The vector stencils library "Cloud round icons" is included in the Cloud Computing Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design cloud computing infographics and diagrams with ConceptDraw PRO software.
"Though service-oriented architecture advocates "everything as a service" (with the acronyms EaaS or XaaS or simply aas), cloud-computing providers offer their "services" according to different models, which happen to form a stack: infrastructure-, platform- and software-as-a-service.
Infrastructure as a service (IaaS)
In the most basic cloud-service model ... providers of IaaS offer computers — physical or (more often) virtual machines — and other resources. IaaS refers to online services that abstract the user from the details of infrastructure like physical computing resources, location, data partitioning, scaling, security, backup etc.
Platform as a service (PaaS)
PaaS vendors offer a development environment to application developers. The provider typically develops toolkit and standards for development and channels for distribution and payment. In the PaaS models, cloud providers deliver a computing platform, typically including operating system, programming-language execution environment, database, and web server. Application developers can develop and run their software solutions on a cloud platform without the cost and complexity of buying and managing the underlying hardware and software layers.
Software as a service (SaaS)
In the software as a service (SaaS) model, users gain access to application software and databases. Cloud providers manage the infrastructure and platforms that run the applications. SaaS is sometimes referred to as "on-demand software" and is usually priced on a pay-per-use basis or using a subscription fee.
In the SaaS model, cloud providers install and operate application software in the cloud and cloud users access the software from cloud clients. Cloud users do not manage the cloud infrastructure and platform where the application runs. This eliminates the need to install and run the application on the cloud user's own computers, which simplifies maintenance and support. Cloud applications differ from other applications in their scalability — which can be achieved by cloning tasks onto multiple virtual machines at run-time to meet changing work demand." [Cloud computing. Wikipedia]
The vector stencils library "Cloud round icons" is included in the Cloud Computing Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Cloud Computing Architecture Diagrams
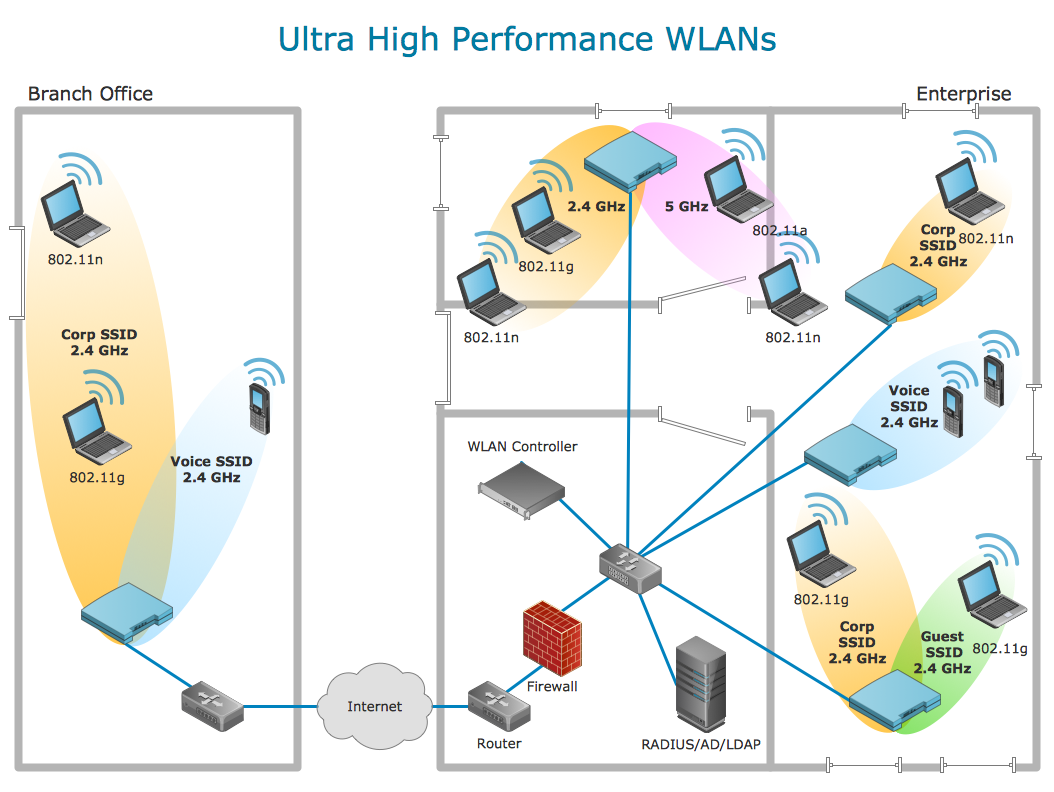
For documenting the Cloud Computing Architecture with a goal to facilitate the communication between stakeholders are successfully used the Cloud Computing Architecture diagrams. It is convenient and easy to draw various Cloud Computing Architecture diagrams in ConceptDraw PRO software with help of tools of the Cloud Computing Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.Secure Wireless Network
Use the ConceptDraw PRO diagramming and vector drawing software enhanced with powerful tools of Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park to effectively visualize the importance of network security and wireless network security, and ways to ensure them, to easily design Network Security Diagrams and Maps, Network Security Model, Secure Wireless Network and Network Security Architecture diagrams.- Active Directory diagram - Asymmetric encryption | Access control ...
- Access Control Diagram
- Testing Under Control In Cloud Computing Diagram
- Design elements - Alarm and access control | Alarm and access ...
- Active Directory diagram - Asymmetric encryption | Network Security ...
- Network Access Control Diagram
- Active Directory diagram - Asymmetric encryption | Active Directory ...
- Identity And Access Management
- Hybrid Encryption Png
- DES Network. Computer and Network Examples | Network ...
- Recommended network architecture for BlackBerry SWS | Firewall ...
- Key Encryption Stencil
- Access Control Visio
- DES Network. Computer and Network Examples | Netflow ...
- Food infogram - Reducing sodium | Organizational chart - National ...
- Network Access Control Cisco Icons Png
- Hotel Network Topology Diagram. Hotel Guesthouse WiFi Network ...
- Constant improvement of key performance indicators | Key ...
- Cloud round icons - Vector stencils library | Account Flowchart ...